IT PORTFOLIO MANAGEMENT
OMB and Agencies Are Not Fully Addressing Selected Statutory Requirements
Report to the Ranking Member, Subcommittee on Cybersecurity, Information Technology, and Government Innovation, Committee on Oversight and Accountability, House of Representatives
November 2024
GAO-25-107041
United States Government Accountability Office
View GAO-25-107041. For more information, contact Kevin Walsh at (202) 512-6151 or walshk@gao.gov.
Highlights of GAO-25-107041, a report to the Ranking Member, Subcommittee on Cybersecurity, Information Technology, and Government Innovation, Committee on Oversight and Accountability, House of Representatives
November 2024
IT PORTFOLIO MANAGEMENT
OMB and Agencies Are Not Fully Addressing Selected Statutory Requirements
Why GAO Did This Study
The executive branch has undertaken numerous initiatives to better manage the more than $100 billion that is annually invested in IT. However, federal IT investments too frequently fail to deliver capabilities in a timely manner. Recognizing the issues related to the government-wide management of IT, in December 2014, Congress enacted federal IT acquisition reform legislation, commonly referred to as FITARA.
GAO was asked to evaluate IT executive reviews. This report evaluates the extent to which OMB and agencies are following requirements for IT portfolio management oversight, including annual IT portfolio and high-risk investment reviews. To do so, GAO identified related requirements from FITARA. GAO then compared agency documentation from OMB and the 24 agencies to the requirements. GAO also interviewed OMB and agency officials regarding their IT portfolio management practices.
What GAO Recommends
GAO is making 10 recommendations to OMB to improve guidance, processes, and reporting; and 36 recommendations to 24 agencies to improve their IT portfolio processes.
OMB did not agree or disagree with its recommendations but stated that it disagreed with parts of the report. As discussed in the report, GAO maintains that the recommendations are warranted. Of the 24 agencies, seven agreed with their recommendations, two agencies neither agreed nor disagreed, and 15 stated that they had no comments.
What GAO Found
The Office of Management and Budget (OMB) is not fully addressing eight key statutory requirements contained in the Federal Information Technology Acquisition Reform Act (FITARA). Specifically, OMB is partially following four of the five requirements on IT portfolio reviews, and not following the three requirements on high-risk IT investments (see table). Until OMB adheres to FITARA’s portfolio management requirements, its oversight of agencies’ IT portfolios, including potentially troubled IT investments, will be limited. As a result, the federal government will continue to expend resources on IT investments that do not meet the needs of the government or the public.
|
Requirement |
Assessment |
|
IT portfolio reviews |
|
|
Implement a process to assist agencies in reviewing their IT portfolios. |
◐ |
|
Develop standardized cost savings/avoidance and performance metrics for agencies to implement the process. |
◐ |
|
Carry out the Federal Chief Information Officer’s (CIO) role in being involved in an annual review of each agencies’ IT portfolio in conjunction with the agency’s CIO and Chief Operating Officer or Deputy Secretary (or equivalent). |
○ |
|
Submit a quarterly report on the cost savings/reductions in duplicative IT investment identified through this review process to key committees in Congress. |
◐ |
|
Submit to Congress a report on the net program performance benefits achieved as a result of major capital investments made by agencies for information systems and how the benefits relate to the accomplishment of the goals of the agencies. |
◐ |
|
High-risk IT investment reviews |
|
|
Carry out consultation responsibilities of the Federal CIO to agency CIOs and program managers of major IT investments that receive high-risk ratings for four consecutive quarters. |
○ |
|
Communicate the results of high-risk IT investment reviews to key committees in Congress. |
○ |
|
Deny any request of additional development, modernization, or enhancement funding for a major investment that has been rated high-risk for a year after the high-risk IT investment review. Additional funding should be denied until the agency CIO determines that the root causes of the risk have been addressed, and there is capability to deliver the remaining increments within the planned cost and schedule.a |
○ |
Legend: ◐ Partially followed = the agency demonstrated that it was following some, but not all, of the requirement; ○ Not followed = the agency did not demonstrate that it was following the requirement.
Source: GAO analysis based on OMB data. | GAO-25-107041
aThis requirement does not apply to investments at the Department of Defense.
Agencies have also not fully addressed FITARA requirements for IT portfolio management. Specifically, none of the 24 agencies fully met the requirements for annual IT portfolio reviews. In addition, eight agencies with major IT investments rated as high-risk for four consecutive quarters did not follow the FITARA requirements for performing high-risk IT investment reviews. Three of the eight agencies performed the reviews, but they did not address the specific requirements in law. The remaining five agencies did not perform the reviews. Not performing these required reviews can permit investments with substantial cost, schedule, and performance problems to continue unabated without necessary corrective actions.
Abbreviations
|
CIO |
chief information officer |
|
DHS |
Department of Homeland Security |
|
FITARA |
Federal Information Technology Acquisition Reform Act |
|
IDC |
Integrated Data Collection |
|
OMB |
Office of Management and Budget |
This is a work of the U.S. government and is not subject to copyright protection in the United States. The published product may be reproduced and distributed in its entirety without further permission from GAO. However, because this work may contain copyrighted images or other material, permission from the copyright holder may be necessary if you wish to reproduce this material separately.
November 14, 2024
The Honorable Gerald E. Connolly
Ranking Member
Subcommittee on Cybersecurity, Information Technology, and Government
Innovation
Committee on Oversight and Accountability
House of Representatives
Dear Mr. Connolly:
The executive branch has undertaken numerous initiatives to better manage the more than $100 billion that is annually invested in IT. However, federal IT investments too frequently fail to deliver capabilities in a timely manner. They also may incur cost overruns or schedule slippages while contributing little to mission-related outcomes. These investments often lack disciplined and effective management in areas such as project planning, requirements definition, and program oversight and governance.
Recognizing the severity of issues related to the government-wide management of IT, in December 2014, Congress enacted federal IT acquisition reform legislation, commonly referred to as the Federal Information Technology Acquisition Reform Act (FITARA).[1] In 2015, we added the government’s management of IT acquisitions and operations to our high-risk list.[2]
You asked us to evaluate executive IT reviews. Our objectives were to determine (1) the extent to which the Office of Management and Budget (OMB) is following statutory requirements for IT portfolio management oversight, including annual IT portfolio reviews and high-risk IT investment reviews; and (2) the extent to which agencies are following statutory requirements for IT portfolio management oversight, including annual IT portfolio reviews and high-risk IT investment reviews. The scope of our review includes OMB and the 24 federal agencies covered by the Chief Financial Officers Act of 1990 that also generally correspond to the agencies covered by FITARA.[3]
To address the first objective, we identified FITARA’s requirements for OMB to conduct and oversee annual IT portfolio reviews and high-risk investment reviews.[4] Based on our review, we identified eight key requirements for OMB.
To determine the extent to which OMB is following these requirements, we obtained and assessed OMB documentation related to annual IT portfolio reviews and high-risk investment reviews. We assessed OMB’s compliance with the FITARA requirements applicable to OMB as follows:
· fully following, if available evidence demonstrated OMB was following all aspects of the requirement;
· partially following, if available evidence demonstrated OMB was following some, but not all, of the requirement; or
· not following, if available evidence did not demonstrate OMB was following any aspect of the requirement.
To determine the extent to which OMB had followed a FITARA requirement on reporting cost savings to Congress, we downloaded the PortfolioStat cost savings from the IT Dashboard for 23 of the 24 agencies.[5] We assessed the reliability of the data by reviewing related documentation, reviewing the data for obvious errors and omissions, and reviewing agency documentation demonstrating how the agency derived these cost savings/avoidances. We determined that the cost saving/avoidance data were not sufficiently reliable and discuss these issues in this report.
To address the second objective, we identified FITARA’s requirements for agencies to conduct annual IT portfolio reviews and high-risk investment reviews. For the annual IT portfolio review requirements, we compared agency documentation to the FITARA requirements. We assessed agencies’ compliance with the FITARA requirements applicable to agencies as follows:
· fully following, if available evidence demonstrated the agency was following all aspects of the requirement;
· partially following, if available evidence demonstrated the agency was following some, but not all, of the requirement; or
· not following, if available evidence did not demonstrate that the agency was following any aspect of the requirement.
To determine the extent to which agencies were following FITARA’s requirements for high-risk IT investment reviews, we reviewed the Chief Information Officer (CIO) ratings on the IT Dashboard. In particular, we identified the ratings of major investments between November 2020 and August 2023 to identify those that received a high-risk rating for at least four consecutive quarters during this time.[6] We determined 17 investments met this criterion. Therefore, agencies were required by FITARA to hold a high-risk IT investment review for these investments.
In addition, we downloaded background information from the IT Dashboard on these investments, such as the investment title and planned expenditures. We assessed the reliability of these data by reviewing related documentation, reviewing the data for obvious errors and omissions, and asking agencies to verify the information. We determined that the data were sufficiently reliable for our purposes of identifying investments that met the FITARA threshold and providing background information on those investments.
We compared agency documentation to FITARA’s requirements on high-risk IT investment reviews. We assessed the agencies as:
· fully following, if available evidence demonstrated the agency was following all aspects of the requirement;
· partially following, if available evidence demonstrated the agency was following some, but not all, of the requirement; or
· not following, if available evidence did not demonstrate that the agency was following any aspect of the requirement.
We also met with relevant officials at OMB and the agencies to obtain additional information on agency efforts to meet FITARA’s IT portfolio management requirements. These officials included staff from OMB’s Office of the Federal CIO and the agencies’ offices of the CIO, such as CIOs and the Deputy Chief Information Security Officer. See appendix I for a more detailed discussion of our objectives, scope, and methodology.
We conducted this performance audit from August 2023 to November 2024 in accordance with generally accepted government auditing standards. Those standards require that we plan and perform the audit to obtain sufficient, appropriate evidence to provide a reasonable basis for our findings and conclusions based on our audit objectives. We believe that the evidence obtained provides a reasonable basis for our findings and conclusions based on our audit objectives.
Background
The Federal Government Has Undertaken Multiple Initiatives to Address IT Issues
The federal government has undertaken multiple initiatives over the years in an attempt to address persistent issues with IT acquisitions and operations. For example:
· Congress enacted the E-Government Act of 2002 to address the challenges of managing federal government programs and services in the information age.[7] The act established the Office of Electronic Government within OMB, to be headed by an Administrator. In March 2009, the President designated this Administrator as the Federal CIO.[8] Among other things, the President assigned the Federal CIO responsibility for directing the policy and strategic planning of federal IT investments, overseeing federal technology spending, and ensuring information security and privacy across the federal government.
· In June 2009, OMB launched the IT Dashboard. It is intended to provide transparency for IT investments to facilitate public monitoring of government operations and accountability for investment performance by the Federal CIO who oversees them. Among other things, agencies are to submit ratings from their CIOs, which, according to OMB’s instructions, should reflect the level of risk facing an investment relative to that investment’s ability to accomplish its goals.[9] These risk ratings are based on a five-point scale where 1 represents the highest risk and 5 represents the lowest risk. The dashboard then translates the agency CIOs’ numerical ratings into a color for depiction on the Dashboard, with green signifying low or moderately low risk (i.e., investments with a 4 or 5), yellow signifying medium risk (i.e., a 3), and red signifying moderately high or high risk (i.e., a 1 or 2).
· In January 2010, OMB began conducting TechStats in an effort to turnaround, halt, or terminate IT projects that were failing or not producing results. OMB envisioned TechStats as face-to-face, evidence-based reviews of an at-risk IT investment. At the time, OMB used CIO ratings from the IT Dashboard, among other sources, to select at-risk investments for the TechStats. OMB conducted TechStats from 2010 through 2011 and subsequently required federal agencies to hold them, too.[10]
To assist agencies, OMB worked with a task force of agency leads to develop, document, and issue a TechStat Toolkit—a guide to holding TechStats at the agency level. According to the toolkit, a TechStat is triggered when an agency’s Office of the CIO determines that a project is underperforming, using data from the IT Dashboard and other sources. In the TechStat session, the CIO, along with other members of the agency’s leadership team, is to meet for 1 hour to review the analysis assembled by the TechStat team, examine program performance data, and explore opportunities for improvement.
In establishing and rolling out the TechStat sessions, OMB stated that it expected that the sessions would help strengthen IT governance, improve line-of-sight between project teams and senior executives, increase the precision of ongoing measurement of IT program health, and boost the quality and timing of interventions to keep projects on track.
· In December 2010, the White House issued a 25-point plan intended to reform federal IT management.[11] Among other things, the document required agencies to reform and strengthen their Investment Review Boards according to the TechStat model and begin holding TechStats at the department and bureau levels.
· In March 2012, recognizing the proliferation of duplicative and low-priority IT investments within the federal government and the need to drive efficiency, OMB launched the PortfolioStat initiative.[12] This required agency CIOs to conduct an annual agency-wide reviews of their IT portfolios to, among other things, assess the current maturity of their IT portfolio management processes, reduce duplication, demonstrate how investments align with the agencies’ missions, and achieve savings by identifying opportunities to consolidate investments or move to shared services. OMB’s 2012 PortfolioStat guidance stated that while a TechStat was to examine IT performance at the specific project or investment level, a PortfolioStat was to examine an agency’s portfolio as a whole, to help identify and eliminate areas of duplication and waste.
· In December 2014, FITARA[13] was enacted and required covered executive branch agencies[14] to ensure CIOs have a significant role in the management, governance, and oversight processes related to their IT portfolios. FITARA includes various requirements for agencies and OMB regarding IT portfolio management. While FITARA does not specifically use the terms “PortfolioStat” and “TechStat,” it codified similar requirements for OMB and agencies on performing annual IT portfolio reviews and high-risk IT investment reviews. We discuss these requirements in-depth later in this report.
· In June 2015, OMB issued guidance that described how agencies are to implement FITARA.[15] Among other things, OMB provided guidance for agencies in implementing FITARA’s requirements for the annual review of agencies’ IT portfolios and reviews of high-risk IT investments.[16] In its guidance, OMB updated the existing PortfolioStat and TechStat processes and requirements. In some cases, OMB’s guidance was more stringent than FITARA, requiring more frequent meetings (e.g., quarterly PortfolioStat sessions rather than annual) or requiring a TechStat sooner (i.e., after only 3 months of consecutive high-risk ratings instead of four consecutive quarters). In other cases, OMB’s guidance was less stringent. For example, OMB’s guidance did not require the agency CIOs to conduct annual reviews in conjunction with the agency’s deputy secretary (or equivalent) as is required in FITARA.
GAO Has Reported on Federal Initiatives to Address IT Acquisition and Operation Issues
Over the last two decades, we have issued many reports on the issues with the federal government’s management of IT acquisitions and operations, as well as the initiatives to address these issues. These reports include:
· Beginning in July 2010, and over several years, we issued a series of reports about the IT Dashboard.[17] These reports noted both the significant steps OMB took to enhance the oversight, transparency, and accountability of federal IT investments by creating the Dashboard, as well as issues with the accuracy and reliability of data. We made a total of 22 recommendations to OMB and the associated agencies. Twenty of the recommendations were implemented and two were closed but not implemented.
· In September 2011, we reported that there were hundreds of investments providing similar functions across the federal government.[18] We made recommendations to OMB to improve its guidance to agencies on categorizing investments and ensuring that their IT investments were not duplicative. OMB has implemented the recommendations.
· In June 2013, we reported that OMB and selected agencies had held multiple TechStats on IT investments that varied in function, significance, and risk.[19] However, we noted that the number of TechStats that were held were relatively small compared to the number of at-risk investments in the government and at these selected agencies. We also found that while the selected agencies were generally conducting TechStats in accordance with OMB guidance, there was room for improvement. We made recommendations to the agencies to address the weaknesses in their TechStat processes that we identified. We also made recommendations to OMB to improve its oversight of TechStats, such as requiring agencies to conduct TechStats on investments rated with a moderately high- or high-risk rating on the IT Dashboard. Agencies have implemented their recommendations. In addition, with the issuance of its FITARA implementation guidance, M-15-14, OMB implemented its recommendation.
· In November 2013, we reported that agencies had taken actions to implement OMB’s PortfolioStat guidance.[20] However, there were shortcomings in their implementation of selected requirements, such as addressing all required elements of the final PortfolioStat action plan. We made 64 recommendations to OMB and 24 agencies to take steps to improve their PortfolioStat implementation. Agencies have implemented their recommendations.
· After many years of reporting on frequent failures, cost overruns, and schedule slippages of federal IT investments, in February 2015, we added improving the management of IT acquisitions to our high-risk areas for the federal government.[21] We noted that federal IT projects have failed due, in part, to a lack of oversight and governance. We reported that executive-level governance and oversight across the government has often been ineffective, specifically from CIOs. We further reported that not all CIOs have the authority to review and approve the entire agency IT portfolio and that CIOs’ authority was limited. In our 2023 high-risk update, we stated that, while progress had been made, overall, the status of the area had remained unchanged since 2017.[22]
· In June 2016, we reported that selected agencies’ CIO ratings of investments were generally rated lower risk than our assessment of those same investments.[23] As a result, we made 25 recommendations to 15 agencies to improve the quality and frequency of their ratings. Agencies have implemented all of those recommendations.
· In April 2017, we reported on the results of a CIO forum, convened by the Comptroller General on September 14, 2016.[24] The panel explored the challenges and opportunities for CIOs to improve federal IT acquisitions and operations. For example, the panel participants identified key actions related to strengthening FITARA and improving CIO authorities. Panel participants also noted challenges in IT areas such as budget formulation, governance, workforce, operations, and transition planning.
· In August 2018, we reported on critical actions needed by federal agencies to address shortcomings and challenges in implementing CIO responsibilities.[25] In a review of the 24 agencies covered by the Chief Financial Officers Act of 1990, none fully addressed the role of their CIOs consistent with federal laws and guidance. In addition, the majority of the agencies did not address the role of their CIOs in the areas of IT leadership and accountability, IT budgeting, information security, IT investment management, IT strategic planning, and IT workforce. We recommended that agencies fully address the role of their CIOs in policy. As of September 2024, nine agencies had not implemented their recommendations and one agency had partially implemented its recommendation.
· In September 2022, we reported that the responsibilities of the Federal CIO and agency CIOs generally aligned to those of private sector CIOs.[26] However, we noted that the Federal CIO position was not itself established by statute but its main legal authorities were those established for the OMB Administrator for E-government and Information Technology in 2002. As a result, the Federal CIO’s responsibilities were often more limited in key CIO management areas than those of other types of CIOs. We recommended that Congress consider formalizing the Federal CIO position and establishing responsibilities and authorities for government-wide management. We also made recommendations to OMB to increase emphasis on collaboration between CIOs and other executives and consider managerial skills in CIO hiring criteria. As of September 2024, these recommendations have not been implemented.
OMB Is Not Fully Following Key FITARA IT Management Requirements
OMB is not fully following eight FITARA requirements for IT portfolio management oversight. Specifically, OMB is partially following four of the five requirements on IT portfolio reviews and is not following the three requirements on high-risk IT investments. Table 1 summarizes the extent to which OMB is following IT portfolio management requirements in FITARA.[27]
Table 1: Extent to Which the Office of Management and Budget (OMB) Is Following the Federal Information Technology Acquisition Reform Act’s (FITARA) IT Portfolio Management Requirements
|
Requirement |
Assessment |
|
IT portfolio reviews |
|
|
Implement a process to assist agencies in reviewing their IT portfolios to: · identify or develop ways to increase the efficiency and effectiveness of the agency’s IT investments; · identify or develop opportunities to consolidate the acquisition and management of IT services and increase the use of shared-service delivery models; · identify potential duplication and waste; · identify potential cost savings; · develop plans for actions to optimize the IT portfolio, programs, and resources; · develop ways to better align the IT portfolio, programs, and financial resources to any multi-year funding requirements or strategic plans required by law; and · develop a multi-year strategy to identify and reduce duplication and waste within the IT portfolio, including component-level investments, and to identify projected cost savings resulting from such strategy. |
◐ |
|
Develop standardized cost savings/ avoidance and performance metrics for agencies to implement the process, in consultation with agency chief information officers (CIO).a |
◐ |
|
Carry out the Federal CIO’s role of being involved in an annual review of each agency’s IT portfolio that is conducted by the CIO of each agency in conjunction with the Chief Operating Officer or Deputy Secretary (or equivalent) of each agency and the Federal CIO. |
○ |
|
Submit a quarterly report on the cost savings and reductions in duplicative IT investment identified through this review process to specified committees of Congress. |
◐ |
|
Submit to Congress, at the same time that the President submits the budget for a fiscal year, a report on the net program performance benefits achieved as a result of major capital investments made by agencies for information systems and how the benefits relate to the accomplishment of the goals of the agencies.b |
◐ |
|
High-risk IT investment reviews |
|
|
Carry out consultation responsibilities of the Federal CIO to agency CIOs and program managers of major IT investments that receive high-risk ratings for four consecutive quarters. |
○ |
|
Through the Federal CIO, communicate the results of required high-risk IT investment reviews to the Senate Committee on Homeland Security and Governmental Affairs, the House Committee on Oversight and Government Reformc and the House and Senate Appropriations Committees, and the committees of the Senate and House with primary jurisdiction over the agency. |
○ |
|
Ensure that for agencies other than the Department of Defense, if 1 year after the date of completion of the high-risk IT investment review the major IT investment is still rated as high-risk, any request of additional development, modernization, or enhancement funding for the major investment is denied until the date on which the agency CIO determines that the root causes of the high level of risk have been addressed, and there is sufficient capability to deliver the remaining planned increments within the planned cost and schedule. |
○ |
Legend: ◐ Partially followed = documentation demonstrated that the agency was following some, but not all, of the requirement; ○ Not followed = no documentation or documentation demonstrated that the agency was not following the requirement.
Source: FITARA and GAO analysis of OMB documentation. | GAO‑25‑107041
aFITARA uses the term “performance indicators” but we refer to them in this report as metrics for simplicity.
bThis language preceded FITARA in 40 USC 11302 and remained in the relevant section as part of the FITARA revisions.
cThis committee is now called the Committee on Oversight and Accountability.
OMB Established Initial Guidance, but Is No Longer Holding Annual IT Portfolio Reviews with Agencies
FITARA requires OMB to perform five activities related to IT portfolio reviews.[28] Table 2 details FITARA’s requirements for OMB regarding IT portfolio reviews.
Table 2: Federal Information Technology Acquisition Reform Act (FITARA) IT Portfolio Review Requirements for the Office of Management and Budget (OMB)
|
Requirement |
|
Implement a process to assist agencies in reviewing their IT portfolios to: · identify or develop ways to increase the efficiency and effectiveness of the agency’s IT investments; · identify or develop opportunities to consolidate the acquisition and management of IT services and increase the use of shared-service delivery models; · identify potential duplication and waste; · identify potential cost savings; · develop plans for actions to optimize the IT portfolio, programs, and resources; · develop ways to better align the IT portfolio, programs, and financial resources to any multi-year funding requirements or strategic plans required by law; and · develop a multi-year strategy to identify and reduce duplication and waste within the IT portfolio, including component-level investments, and to identify projected cost savings resulting from such strategy. |
|
Develop standardized cost savings/avoidance and performance metrics for agencies to implement the process, in consultation with the agency chief information officers (CIO).a |
|
Carry out the Federal CIO’s role in being involved in an annual review of each agency’s IT portfolio that is conducted by the CIO of each agency in conjunction with the Chief Operating Officer or Deputy Secretary (or equivalent) of each agency and the Federal CIO. |
|
Submit a quarterly report on the cost savings and reductions in duplicative IT investment identified through this review process to key committees in Congress. |
|
Submit to Congress, at the same time that the President submits the budget for a fiscal year, a report on the net program performance benefits achieved as a result of major capital investments made by agencies for information systems and how the benefits relate to the accomplishment of the goals of the agencies. |
Source: GAO analysis of 40 U.S.C 11319. | GAO‑25‑107041
aFITARA uses the term “performance indicators” but we refer to them in this report as metrics for simplicity.
OMB is partially following most of FITARA’s requirements for IT portfolio reviews. Specifically, of the five requirements for IT portfolio reviews, OMB is partially following four and is not following the fifth.
OMB Developed an IT Portfolio Review Process, but the Guidance Is Outdated
FITARA requires OMB to implement a process to assist agencies in reviewing their IT portfolios. As previously noted, in June 2015, OMB issued guidance that outlined a process for agencies to implement for IT portfolio review activities to ensure compliance with FITARA requirements.[29] The guidance addressed all of the elements FITARA required, such as providing a method for agencies to identify potential duplication and waste and plans for action to optimize the IT portfolio.
However, this guidance has not been revised since 2015 and is now outdated. For example, the guidance describes a process that OMB has stated is no longer in use (e.g., quarterly meetings) and includes guidance that is only relevant for fiscal year 2015. In addition, the metrics identified in the guidance reflect priorities from two administrations ago. The guidance also does not reflect changes OMB has made to IT portfolio management and budget terms since 2015 (e.g., the addition of new investment types such as standard and funding transfer investments).[30] Moreover, OMB told us that it is not following the IT portfolio management process laid out in the guidance or ensuring that agencies follow the guidance for IT portfolio reviews.
OMB also pointed to section 55 of its Circular A-11 for additional guidance for agencies’ IT portfolio management processes.[31] Circular A-11 states that it established a foundation for effective IT planning and budgeting and IT portfolio management practices and that by following the guidance, agencies enable OMB to review their IT investment spending and government-wide spending. However, it does not include FITARA’s required elements for this process, including identifying ways for agencies to increase the efficiency and effectiveness of the portfolio, identify potential duplication or waste, or identify potential cost savings.
OMB maintains that it is complying with FITARA’s requirements on IT portfolio reviews through its iterative engagement between agency CIOs and desk officers from the Office of the Federal CIO.[32] Further, OMB indicated that this is to allow the Office of the Federal CIO to balance resource constraints and staffing shortages. OMB stated that administrations have to balance resources, priorities, and staff. As a result, as other areas such as cybersecurity have demanded additional resources, the Office of the Federal CIO has scaled back some activities. Such activities include holding IT portfolio reviews using the process as described in its guidance, M-15-14.
We acknowledge that resource constraints may exist, requiring the prioritization of available resources. However, given that the federal government spends over $100 billion annually on IT, effectively prioritizing the management of this vast portfolio could help ensure that resources are not wasted. Until OMB updates and then enforces the implementation of its updated guidance, the agency will be limited in its insights and oversight of agencies’ IT portfolios. This can lead to duplication, waste, unoptimized or misaligned IT portfolios, and missed cost savings.
OMB Developed Standardized Metrics on Cost Savings/Avoidance, but Not on Performance
FITARA requires OMB to develop standardized cost savings and avoidance and performance metrics for agencies to implement their IT portfolio management processes, in consultation with agency CIOs.[33]
Aside from its initial guidance, OMB reported that the metrics used to measure IT portfolio progress are provided to agencies in three documents: Circular A-11,[34] its guidance on its Integrated Data Collection (IDC) process,[35] and the IT Dashboard’s Frequently Asked Questions.[36] Taken as a whole, these documents provide agencies with standardized cost savings metrics; however, they do not include standardized performance metrics. See table 3 for an overview of the extent to which the documents include cost savings/avoidance and performance metrics.
Table 3: Extent to Which the Office of Management and Budget (OMB) Documentation Includes Standardized Cost Savings/Avoidance and Performance Metrics
|
OMB document |
Includes standardized cost savings/avoidance metrics? |
Includes standardized performance metrics? |
|
Circular A-11 |
No |
No |
|
Integrated Data Collection guidance |
Yes |
No |
|
IT Dashboard Frequently Asked Questions |
No |
No |
Source: GAO analysis of OMB documentation. | GAO‑25‑107041
Specifically, the most recent Circular A-11 issued in August 2023 states that agency IT portfolio submissions should include broad categories of data such as operational analysis data, IT performance data, and performance results data. However, the circular does not provide standardized cost savings/avoidance or performance metrics.
In addition, the IDC instructions do include cost savings and avoidance metrics; however, it does not include those for performance. For example, these instructions require agencies to report the OMB initiative that led to cost savings/avoidances, and the amount realized by the agency, but is silent on specific performance metrics.
Further, the IT Dashboard Frequently Asked Questions asks agencies to identify and provide their own performance metrics, rather than standardized performance metrics. In addition, the document does not include metrics on cost savings/avoidance.
OMB maintained that it is complying with FITARA’s requirements but did not explain the lack of standardized performance metrics. Until OMB develops standardized performance metrics for IT portfolio management, it will be limited in its ability to assess and compare the performance of agencies’ IT portfolios.
OMB Does Not Hold Annual IT Portfolio Review Meetings with the Federal CIO and Agency Leaders
According to FITARA, OMB is to carry out the Federal CIO’s role in being involved in an annual review of each covered agency’s IT portfolio that is conducted by the CIO of each agency in conjunction with the Chief Operating Officer or Deputy Secretary (or equivalent) of each agency and the Federal CIO.[37]
OMB reported that it is not holding, what it called, an annual meeting between the Federal CIO and the agencies to review their IT portfolios. Notably, OMB’s IDC instructions state that PortfolioStat reviews (as described in M-15-14) were discontinued in 2017 and replaced with desk officer reviews. OMB acknowledged that its portfolio reviews have changed over time and, while the agency previously conducted individual meetings called PortfolioStats, it now conducts a number of activities to support the annual review of an agencies’ IT portfolio. In particular, OMB stated that these activities include:
· meetings with desk officers at varying intervals throughout the year,
· strategic reviews led by the OMB Deputy Director for Management,
· reviews of IDC collections and IT Dashboard submissions, and
· annual budget reviews during the budget process.
However, these meetings do not satisfy the FITARA requirements for annual IT portfolio reviews, as the current reviews seem removed from the level of the participants specified in FITARA (including the Federal CIO), nor do they occur on an annual basis.
OMB stated that it believes it is complying with FITARA’s requirements on annual IT portfolio reviews through its iterative engagement between agency CIOs and Office of the Federal CIO desk officers. This allows OMB to balance resource constraints and staff shortages.
Prioritizing the management and oversight of the federal government’s substantial IT portfolio could help ensure that resources are used in an effective manner. Until OMB performs annual IT portfolio reviews as required by FITARA, the agency will be limited in its oversight of agencies’ IT portfolios. Further, without OMB’s comprehensive management and oversight of agencies’ IT portfolios, increasing the efficiency of IT investments and identifying duplication and waste will be more difficult to achieve.
OMB Publicly Reports Some of the FITARA-Required Data, but the Data Are Not Reliable
FITARA requires OMB—through the official now known as the Federal CIO—to submit a quarterly report on the cost savings and reductions in duplicative IT investment identified through this review process to key committees in Congress.
OMB personnel stated that the Office of the Federal CIO does not provide this data specifically to Congress. Instead, OMB uses the public IT Dashboard to display agency-reported cost savings resulting from several OMB initiatives, such as data center optimization and software license management or “PortfolioStat.”[38] However, the IT Dashboard does not provide a report of reductions in duplicative IT investments identified through the portfolio review process.
Further, the cost savings/avoidances data reported on the IT Dashboard for annual IT portfolio reviews were unreliable. Specifically, for each agency’s reported cost savings/avoidances, we either identified inaccuracies with the data or were unable to substantiate the savings/avoidances amount or that the savings/avoidances were due to a process other than an annual review of the IT portfolio.
According to IT Dashboard data as of March 2024, between 2012 and 2023, 10 agencies reported $629 million in cost savings or avoidances from these reviews. Table 4 provides the IT portfolio review cost savings for each of the 10 agencies reported between 2012 and 2023.
Table 4: Agency-Reported Cost Savings or Avoidances Attributed to Annual IT Portfolio Reviews from 2012 to 2023, as of March 2024
|
Agency |
2012 |
2013 |
2014 |
2015 |
2016 |
2017 |
2018 |
2019 |
2020 |
2021 |
2022 |
2023 |
Total ($M) |
|
Department of Health and Human Services |
0 |
0.61 |
0.81 |
3.49 |
7.26 |
6.87 |
0 |
0.5 |
0.03 |
2.42 |
0.51 |
0 |
22.5 |
|
Department of Homeland Security |
221.43 |
82.5 |
0 |
0 |
0 |
0 |
0 |
0 |
3.55 |
0 |
0 |
0 |
307.48 |
|
Department of Justice |
2.29 |
2.47 |
5.13 |
12.9 |
5.44 |
7.14 |
3.2 |
0 |
0 |
0 |
0 |
0 |
38.57 |
|
Department of Labor |
1.88 |
5.03 |
3.49 |
4.94 |
8.41 |
34.45 |
23.05 |
22.26 |
21.96 |
16.11 |
11.28 |
2.52 |
155.38 |
|
Department of the Interior |
12.12 |
12.71 |
12.25 |
11.6 |
0.71 |
0.71 |
0.71 |
0.71 |
0.52 |
13.87 |
13.65 |
11.14 |
90.7 |
|
Department of the Treasury |
0 |
0.1 |
0.25 |
0.3 |
0.3 |
0.1 |
0.05 |
0 |
0 |
0 |
0 |
0 |
1.1 |
|
Department of Transportation |
0 |
0 |
0 |
0 |
0 |
0 |
0.03 |
0.03 |
0 |
0 |
0 |
0 |
0.06 |
|
Nuclear Regulatory Commission |
0.04 |
0.29 |
0.01 |
0 |
0 |
0.6 |
0 |
0 |
0 |
0 |
0 |
0 |
0.94a |
|
Social Security Administration |
0 |
1.66 |
1.66 |
2.37 |
0 |
0 |
0 |
0 |
0 |
0 |
0 |
0 |
5.69 |
|
U.S. Agency for International Development |
0.39 |
3.11 |
1.55 |
1.47 |
0 |
0 |
0 |
0 |
0 |
0 |
0 |
0 |
6.52 |
|
Total ($M) |
238.15 |
108.48 |
25.15 |
37.07 |
22.12 |
49.87 |
27.04 |
23.5 |
26.06 |
32.4 |
25.44 |
13.66 |
628.94 |
Source: GAO analysis of IT Dashboard data. | GAO‑25‑107041
aAccording to NRC officials, this amount does not account for the total cost savings/avoidances the agency realized.
However, four agencies (the Departments of Health and Human Services, the Interior, and the Treasury; and the U.S Agency for International Development) reported that their IT portfolio review cost savings were inaccurate when we asked for documentation of their cost savings. For example, Interior stated that it incorrectly attributed about $38 million of the reported $91 million to IT portfolio reviews. In addition, Interior officials stated that it had originally categorized the remaining $53 million to a different OMB initiative. However, in November 2015, OMB recategorized the $53 million to “PortfolioStat,” even though these cost avoidances were not the result of a PortfolioStat review.
In other cases, agencies did not have adequate documentation of the cost savings. For example, several agencies provided us the file they use to report the cost savings to the IT Dashboard or OMB rather than supporting documentation on how the savings were derived.
In addition, the older cost savings and avoidances were difficult for agencies to substantiate because the savings were realized beyond the time period in which agencies typically retain documents. For example, the Social Security Administration last reported savings or avoidances from annual IT portfolio reviews in 2015, and no longer has documentation related to those figures. Officials stated that the Social Security Administration does not keep the pertinent records longer than 7 years (i.e., 2017), unless specifically authorized.
In addition, several agencies reported that they had used a process other than an annual IT portfolio review as the basis for at least some of their reported cost savings/avoidances. Specifically, three agencies (the Departments of Homeland Security (DHS), Justice, and Labor) stated that they used OMB’s IDC process as the basis for their cost savings.[39] However, the collection process is a reporting mechanism, not a portfolio review process. The Department of Justice attributed this change to OMB’s IDC instructions, which stated that PortfolioStat reviews were discontinued in 2017 and replaced with desk officer reviews (as discussed earlier). In another example, the Department of Transportation reported that its savings were derived from multiple processes implemented by the Office of Inspector General. However, the Office of the Inspector General stated that it does not conduct an annual assessment of the program in question and is unsure how the department came up with the calculation of cost savings.
OMB staff stated that it is the agencies’ responsibility to ensure that the data they submit is accurate. Further, the staff noted that OMB does not have the resources to verify all the data entered by agencies.
Since OMB is relying on the IT Dashboard to fulfill its statutory requirement to report to Congress, ensuring the accuracy of the data is of the utmost importance. Further, as previously noted, prioritizing the management and oversight of the federal government’s substantial IT portfolio is critical. Until OMB ensures that it is providing accurate cost savings data on agencies’ reported IT portfolio reviews, it will not be able to determine the extent to which portfolio review initiatives are reducing duplication and generating savings. Further, providing inaccurate data to Congress could over or understate the success of initiatives and limit Congress’ ability to oversee federal IT.
OMB Reports on Anticipated, Rather Than Achieved, Net Performance Benefits of Information Systems
FITARA requires OMB to submit to Congress a report on the net program performance benefits achieved as a result of major capital investments made by agencies for information systems and how the benefits relate to the accomplishment of the goals of the agencies.
OMB’s analytical perspectives section of the President’s fiscal year 2025 budget details anticipated benefits of major capital investments in information systems.[40] For example, the analytical perspectives section discusses the potential benefits of cybersecurity investments in modernizing cybersecurity defenses, improving information sharing, and strengthening the U.S.’s rapid incident responses. In addition, it highlights the anticipated benefits of powering intelligent government operations and citizen services to drive key insights into the decision-making process.
However, the analytical perspectives section does not specify the benefits that have been achieved or how the benefits relate to the accomplishment of the goals of the agencies. OMB staff stated that the office had not reported this information to Congress because it had to prioritize other activities, such as the cybersecurity initiative, over this requirement. OMB staff noted that IT Dashboard captures performance metrics for each agencies’ investments. While the IT Dashboard does provide agency-reported performance metrics, it does not provide the benefits achieved due to the investment nor does it explain how the benefits related to the accomplishment of agencies’ goals.
Until OMB reports to Congress on achieved benefits of major IT investments, the true benefits of federal IT could be over or understated, which limits agencies’ and Congress’s ability to make decisions and provide oversight.
OMB Has Not Followed Requirements for High-Risk IT Investment Reviews
FITARA requires OMB to perform three activities related to high-risk investment reviews.[41] Table 5 provides details on FITARA’s requirements for OMB regarding high-risk investment reviews.
Table 5: The Federal Information Technology Acquisition Reform Act (FITARA) High-Risk IT Investment Review Requirements for the Office of Management and Budget
|
Carry out consultation responsibilities of the Federal Chief Information Officer (CIO) to agency CIOs and program managers of major IT investments that receive high-risk ratings for four consecutive quarters. |
|
Through the Federal CIO, communicate the results of high-risk IT investment reviews to the Senate Committee on Homeland Security and Governmental Affairs, the House Committee on Oversight and Government Reforma and the House and Senate Appropriations Committees, and the committees of the Senate and House with primary jurisdiction over the agency. |
|
Ensure that for agencies other than the Department of Defense, if 1 year after the date of completion of the high-risk IT investment review the investment is still rated as high-risk, any request of additional development, modernization, or enhancement funding for the investment is denied until the date on which the agency CIO determines that the root causes of the high level of risk have been addressed, and there is sufficient capability to deliver the remaining planned increments within the planned cost and schedule. |
Source: GAO analysis of 40 U.S.C 11302. | GAO‑25‑107041
aThis committee is now called the Committee on Oversight and Accountability.
OMB did not follow any of the three statutory requirements for high-risk investment reviews:
· Carry out consultation responsibilities of the Federal CIO to agency CIOs and program managers of major IT investments that receive high-risk ratings for four consecutive quarters. OMB personnel stated that the Federal CIO regularly collaborates with its desk officers and agency CIOs alike on various IT portfolio reviews, including high-risk investments. However, our review of agency documentation of 27 high-risk review sessions shows that the Federal CIO was not consulted for any of them.
· Communicate the results of high-risk IT investment reviews to key committees in Congress. OMB stated it had not reported this information to the required Congressional committees. OMB personnel were unable to assess when such a report could be sent to Congress in the future.
· Deny any request of additional development, modernization, or enhancement funding for a major investment that has been rated high-risk for a year after the high-risk IT investment review. As we discuss further in the next section, of the 17 major investments that were rated high risk for more than 12 consecutive months, agencies performed reviews on nine of them. Three of the investments were only recently reviewed and it is too soon for OMB to have performed this oversight on them. Of the remaining six investments, four improved to medium risk within the year following the agencies’ required review of the investment. However, OMB did not deny requests for additional funding for the other two investments that did meet this criterion: DHS’s Homeland Advanced Recognition Technology investment and the Department of the Interior’s Trust Asset Accounting Management System.
OMB stated that it has not followed the requirements because administrations need to balance resources, priorities, and staff. In this case, the Office of the Federal CIO stated that it must prioritize its resources according to need, with the most critical areas, such as cybersecurity, receiving more resources.
However, prioritizing the oversight of high-risk IT investment reviews better positions the federal government to effectively turn around or terminate troubled IT investments before additional limited resources are wasted. Until OMB follows FITARA’s requirements related to high-risk investment reviews, it will not be able to provide effective oversight of potentially troubled IT investments. As a result, the federal government is likely to expend resources on IT investments that may not fulfill the needs of the government or the public. Furthermore, in OMB not meeting its Congressional reporting requirements, it limits the ability of Congress to provide needed oversight to these at-risk investments.
Agencies Have Not Fully Met Requirements for FITARA-Required IT Reviews
The 24 agencies have not fully followed FITARA requirements for IT portfolio management reviews. In addition, the agencies that had major investments that were considered high risk for four consecutive quarters did not follow the FITARA requirements for performing high-risk investment reviews.
Agencies Did Not Fully Meet Statutory Requirements for Annual IT Portfolio Reviews
FITARA requires an agency CIO to conduct an annual review of the agency’s IT portfolio, in conjunction with the Chief Operating Officer or Deputy Secretary (or equivalent) and the Federal CIO.[42]
As previously discussed, OMB is not holding annual IT portfolio reviews with agencies and instead is using a variety of methods to review portfolios. As a result, all 24 agencies reported using various mechanisms to review their IT portfolios, in an attempt to comply with FITARA requirements. For example, the National Aeronautics and Space Administration reported that it reviews its IT portfolio as part of its budget submission. In addition, the Department of Commerce reported that it conducts annual IT portfolio reviews with its bureau CIOs.
However, none of the 24 agencies’ processes fully followed FITARA’s requirements. For example, 13 agencies were not able to demonstrate that these reviews were conducted by the CIO. In addition, three agencies held these reviews with the Chief Operating Officer or Deputy Secretary (or equivalent). Moreover, some agencies were not able to demonstrate that their reviews occurred on an annual basis or that their reviews covered the entire IT portfolio for the agency. Lastly, as we previously mentioned, since OMB is not holding these annual reviews, agencies were not able to demonstrate that they were held in conjunction with the Federal CIO. However, eight agencies were able to demonstrate that the Federal CIO’s office was involved in their reviews.
Appendix II provides more details on the processes agencies reported using to manage their IT portfolios. Table 6 provides details on the extent to which agencies’ IT portfolio review processes met FITARA’s requirements.
Table 6: Extent to Which Agencies’ Annual IT Portfolio Review Processes Met Requirements in the Federal Information Technology Acquisition Reform Act (FITARA)
|
Agency |
Demonstrated annual IT portfolio review process? |
Conducted by Chief Information Officer (CIO)? |
Held in conjunction with Chief Operating Officer or Deputy Secretary? |
Held in conjunction with the Federal CIO? |
|
Department of Agriculture |
Partiala |
Partialb |
No |
No |
|
Department of Commerce |
Yes |
Yes |
No |
No |
|
Department of Defensec |
Partiala |
No |
No |
No |
|
Department of Education |
Yes |
Yes |
Yes |
No |
|
Department of Energy |
Yes |
Yes |
No |
No |
|
Department of Health and Human Services |
Yes |
Partialb |
No |
No |
|
Department of Homeland Security |
Partiala,d |
No |
No |
No |
|
Department of Housing and Urban Development |
Partiala |
No |
No |
No |
|
Department of Justice |
Partiala |
Partialb |
No |
No |
|
Department of Labor |
Partiala,d |
Partialb |
No |
Partiale |
|
Department of State |
Partiala |
Partialb |
No |
Partiale |
|
Department of the Interior |
Yes |
Yes |
No |
Partiale |
|
Department of the Treasury |
Yesf |
Yesf |
No |
No |
|
Department of Transportation |
Partiala |
Partialb |
No |
Partiale |
|
Department of Veterans Affairs |
No |
No |
No |
No |
|
Environmental Protection Agency |
Partiala |
Yes |
No |
No |
|
General Services Administration |
Partiala |
Yes |
Yes |
No |
|
National Aeronautics and Space Administration |
Partiala |
Partialb |
No |
No |
|
National Science Foundation |
Partiala |
Yes |
No |
No |
|
Nuclear Regulatory Commission |
Yes |
Yes |
Partialg |
Partialh |
|
Office of Personnel Management |
Partiala |
Yes |
Yes |
Partiale |
|
Small Business Administration |
Partiala |
No |
No |
No |
|
Social Security Administration |
Yes |
Yes |
No |
Partiale |
|
U.S. Agency for International Development |
Partiald |
Partialb |
No |
Partiale |
Source: GAO analysis of agency provided data. | GAO‑25‑107041
aThe agency received a partial because it did not provide adequate documentation that it reviewed the IT portfolio annually.
bThe agency received a partial because it did not provide adequate documentation of the CIOs attendance at the review meeting.
cFITARA allows the Department of Defense to use an existing process to fulfill FITARA’s portfolio review requirements, in consultation with the Federal CIO. 40 U.S.C 11319(d)(4).
dThe agency received a partial because its documentation did not demonstrate that the agency’s IT portfolio was reviewed.
eThe agency received a partial because it provided documentation of the Office of Management and Budget’s (OMB) involvement, rather than the Federal CIO being present.
fThere is an apparent lack of consensus between the Department of the Treasury and one of its bureaus, the Office of the Comptroller of the Currency, involving IT annual portfolio reviews. Specifically, Treasury stated that its CIO has attempted to hold an IT annual review with the office, but it asserted that it is independent of these FITARA requirements. The office confirmed its assertion that it is not subject to the Treasury CIO’s annual portfolio review or oversight. Due to a lack of information at this time regarding the efficacy of the office’s assertion, we did not factor this aspect into our findings.
gThe agency received a partial because it did not provide adequate documentation of the Chief Operating Officer or Deputy Secretary’s attendance at the review meeting.
hThe agency received a partial because while it certifies the annual IT portfolio review to OMB, the Federal CIO did not attend.
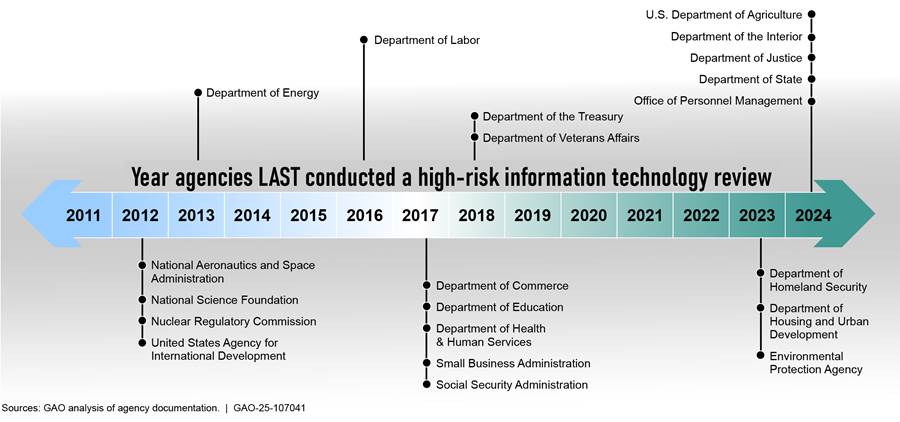
Agencies provided several reasons for not following FITARA’s annual IT portfolio review requirements. The primary reason for agencies’ noncompliance is that, as previously noted, OMB is no longer holding annual reviews that meet FITARA’s requirements. Specifically,15 agencies reported that OMB’s lack of involvement was an issue for them in holding these reviews.[43] In addition, five agencies (the Departments of Commerce, Labor, State, and Veterans Affairs; and the Nuclear Regulatory Commission) cited various issues with OMB’s guidance on holding annual IT portfolio reviews as laid out in FITARA, including that the guidance is out of date and should be updated and enforced.
Further, three agencies (the Departments of Commerce and Veterans Affairs; and the Small Business Administration) cited resource constraints as another reason they have not held annual IT portfolio reviews. For example, the Department of Commerce and the Small Business Administration reported that staff attrition and funding constraints have impacted their IT portfolio review processes.
Finally, eight agencies (the Departments of Health and Human Services, Homeland Security, Housing and Urban Development, and the Treasury; Environmental Protection Agency; General Services Administration; Office of Personnel Management; and the U.S. Agency for International Development) did not provide a reason for not following FITARA’s requirements. Instead, they stated that they use an alternative process to review their IT portfolios.
Annual IT portfolio reviews are crucial for assessing the performance, cost-effectiveness, and alignment of IT investments with agency missions and goals. By conducting such reviews, agencies can identify areas of duplication within their IT portfolios and develop strategies to streamline operations and optimize resource allocation. Furthermore, these sessions enable agencies to project and quantify potential cost savings resulting from the implementation of such strategies, thereby ensuring efficient use of taxpayer funds, and maximizing their value derived from IT investments. Lastly, the annual IT portfolio review is necessary for Congressional oversight because FITARA requires that the Federal CIO submit a quarterly report on the cost savings and reductions in duplicative IT investments identified through this process. [44] Not performing these annual IT portfolio reviews can result in a lack of transparency, hindered decision-making, and reduced accountability in managing IT resources.
Agencies Did Not Fully Meet Requirements for High-Risk IT Investment Reviews
FITARA includes three requirements for agency CIOs related to high-risk IT investment reviews.[45] Specifically, the CIO of each agency and the project manager of the investment in question are to:
· review a major IT investment when it has received a high-risk rating for four consecutive quarters;
· consult the Federal CIO on the review; and
· document (1) a root cause analysis of the high level of risk, (2) the extent to which these causes can be addressed, and (3) the probability of future successes.[46]
Between November 2020 and August 2023, eight agencies had a total of 17 major investments that were rated high risk for four consecutive quarters. (See appendix III for more information on the major investments that were high risk for four consecutive quarters.) Agencies planned to spend a total of $296 million on these 17 investments in fiscal year 2024.
However, none of the eight agencies fully met the related FITARA requirements.[47] Specifically, three agencies (DHS, the Interior, and State) conducted reviews of all of their applicable high-risk investments and five agencies (the Departments of Housing and Urban Development and Labor, Small Business Administration, Office of Personnel Management, and U.S. Agency for International Development) did not hold a high-risk investment review similar to that required by FITARA for any of their applicable investments. See figure 1 for a depiction of the extent to which agencies reviewed their high-risk IT investments, as of April 2024.
Figure 1: Extent to Which Agencies Performed Required High-Risk IT Investment Reviews, as of April 2024
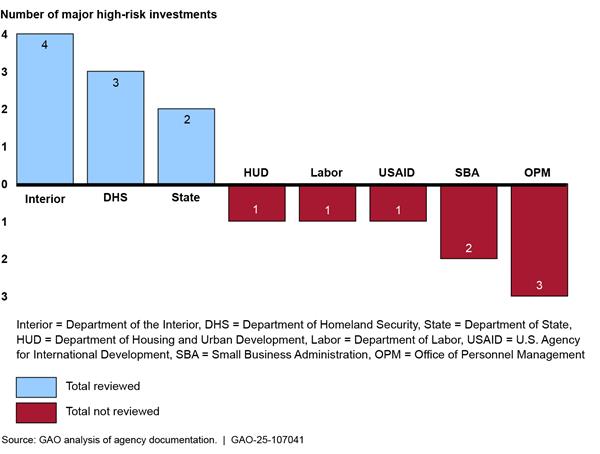
Further, the agencies that conducted reviews of high-risk investments (DHS, the Interior, and State) did not meet the requirements for a high-risk investment review. For example, while DHS documented root cause, action items and an outcome in its review of one investment, the Federal CIO was not consulted, as required by FITARA.
Table 7 details the extent to which the three agencies followed FITARA requirements for their high-risk investment reviews.
Table 7: Extent to Which Three Agencies Followed the Federal Information Technology Acquisition Reform Act (FITARA) Requirements for High-Risk Investment Reviews
|
Agency |
Investment name |
Conducted by Chief Information Officer (CIO) and program manager? |
Federal CIO consulted? |
Documented a root cause, action items and due dates, and an outcome? |
|
Department of Homeland Security (DHS) |
Biometric Entry-Exit |
Noa |
No |
Yes |
|
Financial Systems Modernization – Trio |
Noa |
No |
Partial – While DHS documented a root cause, it did not document action items and due dates or outcomes. |
|
|
Homeland Advanced Recognition Technology |
Noa |
No |
Partial – While DHS documented a root cause, it did not document action items and due dates or outcomes. |
|
|
Department of State |
Global Foreign Affairs Compensation System |
Yes |
No |
Partial - While State documented action items and due dates, it did not document a root cause or outcomes. |
|
Foreign Assistance Coordination and Tracking System |
Yes |
No |
Partial - While State documented action items and due dates, it did not document a root cause or outcomes. |
|
|
Department of the Interior |
Trust Asset Accounting Management System |
Yes |
Partial - The agency had attendees from the Office of the Federal CIO, but the Federal CIO was not consulted. |
Partial - While Interior documented root causes, action items and an outcome, it did not document due dates for implementing corrective actions. |
|
Incident Management, Analysis, and Reporting System |
Yes |
No |
Partial - While Interior documented root causes, action items and an outcome, it did not fully document due dates for implementing corrective actions. |
|
|
Law Enforcement Management Information System |
Yes |
No |
Partial - While Interior documented root causes, action items and an outcome, it did not fully document due dates for implementing corrective actions. |
|
|
Accounting Reconciliation Tool |
Yes |
No |
Yes |
Source: GAO analysis of agency provided data. | GAO‑25‑107041
aAgency provided evidence that its CIO delegated conducting high-risk investment review to the Chief Technology Officer. While the agency stated that the Chief Technology Officer and the program manager conducted the review, the agency did not provide evidence to support that.
The five agencies that did not hold the required high-risk investment reviews provided a variety of reasons for not doing so.[48]
· All five agencies (the Department of Housing and Urban Development, the Department of Labor, Office of Personnel Management, Small Business Administration, and U.S. Agency for International Development) stated that they chose to mitigate the risks associated with these high-risk investments using an alternative internal process. However, when agencies use alternative processes, the processes may not meet FITARA’s requirements, such as having the appropriate people involved or including required elements. For example, the Department of Housing and Urban Development stated that it used its monthly program health assessments to monitor investments; however, this process was not led by the CIO.
· The Small Business Administration noted it faced workload surges and resource availability issues within its Office of the CIO in managing and implementing reviews.
· The Department of Labor stated that the review process is a costly and time and labor-intensive process, often resulting from an issue that has already occurred.
DHS, the Interior, and State provided reasons for their high-risk investment reviews not addressing the requirements of FITARA.
· DHS stated that its CIO delegated this responsibility to the Chief Technology Officer. DHS also stated that the program manager was present for the review. However, DHS did not provide a reason for not being able to provide documentation that showed the presence of either attendee.
· Regarding consulting the Federal CIO, Interior stated that instead it consults with OMB’s Office of the Federal CIO via OMB’s desk officers. DHS stated that OMB’s guidance on holding these reviews does not require consultation with the Federal CIO. DHS further stated that while the CIO does not attend every high-risk review, the CIO has consulted with the Federal CIO on high-risk investments outside of these meetings. State responded that its investment reviews are internal CIO-led investment reviews that did not include OMB.
· Regarding the high-risk investment reviews that were missing elements, DHS stated that those investments were being moderated by its Acquisition Review Board and breach remediation proceedings. While the acquisition review process may have oversight of acquisitions, the purpose of a high-risk IT investment review is to be able to get in front of troubled investments to turn them around before a breach occurs. Interior stated that while no due dates were assigned, all action items were closed out, removing the need to assign due dates. In addition, State declined to provide a reason for the absence of those required elements.
In addition to the above reasons, it is likely that agencies do not adhere to FITARA’s requirements on high-risk IT investment reviews because OMB’s guidance on these reviews is outdated. Specifically, OMB’s original guidance on this type of review is from 2011, predating the enactment of FITARA, and has not been updated since then.[49] OMB’s FITARA implementation guidance references these reviews and builds upon the requirements, but also points to the 2011 guidance on how to conduct these reviews.[50] Several agencies noted that that the guidance was outdated, included links to websites that did not work, and was unclear.
Agency high-risk investment reviews are necessary to determine the root cause for issues affecting an investment and to establish action plans to reduce the risk of the investment. In addition, these reviews are a tool for getting ahead of critical problems in an investment, turning around underperforming investments, or terminating investments if appropriate. In not properly holding these reviews, agencies are not following the law, and are at risk of not being able to properly manage their IT cost, schedule, performance, and security. Further, the lack of these reviews puts hundreds of millions of dollars at risk.
Conclusions
Although OMB took steps to fulfill FITARA’s IT portfolio management requirements in the first few years after the law was enacted, it has not followed through on performing annual IT reviews or reviewing high-risk investments, particularly at the executive level contemplated by FITARA. Until OMB reinstates its efforts to meet the FITARA requirements for reviewing IT investments, the federal government will continue to expend resources on IT investments that could be duplicative or not fulfill the needs of the government or the public.
The lack of annual IT portfolio reviews and high-risk investment review guidance from OMB has directly resulted in agencies’ inability to fulfill their FITARA portfolio review requirements. Until agencies perform required annual reviews, they will not fully identify areas of duplication within their IT portfolios and develop strategies to streamline operations and optimize resource allocation. In addition, the lack of high-risk IT reviews puts hundreds of millions of dollars at risk. Further, agencies not consulting with the Federal CIO hinders the Federal CIO from conducting its statutory FITARA requirements, including communicating the results of the high-risk investment reviews to Congress.
Recommendations for Executive Action
We are making a total of 46 recommendations to 25 agencies, including OMB.
· The Director of OMB should update existing guidance or issue new guidance to agencies to implement a process to assist agencies in reviewing their IT portfolios that includes the requirements provided in FITARA. (Recommendation 1)
· The Director of OMB should develop standardized performance metrics for agencies to implement the IT portfolio review process, as prescribed by FITARA. (Recommendation 2)
· The Director of OMB should ensure that the Federal CIO carries out its role in annually reviewing each agency’s IT portfolio that is conducted by each agency’s CIO in conjunction with the Chief Operating Officer or Deputy Secretary (or equivalent) and the Federal CIO, as prescribed by FITARA. (Recommendation 3)
· The Director of OMB should direct the Federal CIO to submit a quarterly report to the FITARA-identified committees in Congress on the cost savings and reductions in duplicative IT investments identified through the IT portfolio review process, as prescribed by FITARA. (Recommendation 4)
· The Director of OMB should direct the Federal CIO to ensure that the agency cost savings on the IT Dashboard that are being used to fulfill statutory requirements to report to Congress are accurate and correctly attributed to IT portfolio review. (Recommendation 5)
· The Director of OMB should submit to Congress a report on the net program performance benefits achieved as a result of major capital investments made by agencies for information systems and how the benefits relate to the accomplishment of the goals of the agencies, as prescribed by FITARA. (Recommendation 6)
· The Director of OMB should ensure that the Federal CIO carries out the consultation responsibilities of the Federal CIO to agency CIOs and program managers of major IT investments that receive high-risk ratings for four consecutive quarters, as prescribed by FITARA. (Recommendation 7)
· The Director of OMB should direct the Federal CIO to communicate the results of high-risk IT investment reviews to committees in Congress, as prescribed by FITARA. (Recommendation 8)
· The Director of OMB should deny any request of additional development, modernization, or enhancement funding for a major investment that has been rated high risk for a year after the high-risk IT investment review, as prescribed by FITARA. (Recommendation 9)
· The Director of OMB should direct the Federal CIO to update existing guidance or issue new guidance to direct agencies’ efforts on holding high-risk IT investment reviews in accordance with FITARA’s requirements. (Recommendation 10)
· The Secretary of Agriculture should direct the department CIO to work with OMB to ensure that annual reviews of their IT portfolio are conducted in conjunction with the Federal CIO and the Chief Operating Officer or Deputy Secretary (or equivalent), as prescribed by FITARA. (Recommendation 11)
· The Secretary of Commerce should direct the department CIO to work with OMB to ensure that annual reviews of their IT portfolio are conducted in conjunction with the Federal CIO and the Chief Operating Officer or Deputy Secretary (or equivalent), as prescribed by FITARA. (Recommendation 12)
· The Secretary of Defense should direct the department CIO to work with OMB to ensure that annual reviews of their IT portfolio are conducted in conjunction with the Federal CIO and the Chief Operating Officer or Deputy Secretary (or equivalent), as prescribed by FITARA. (Recommendation 13)
· The Secretary of Education should direct the department CIO to work with OMB to ensure that annual reviews of their IT portfolio are conducted in conjunction with the Federal CIO, as prescribed by FITARA. (Recommendation 14)
· The Secretary of Energy should direct the department CIO to work with OMB to ensure that annual reviews of their IT portfolio are conducted in conjunction with the Federal CIO and the Chief Operating Officer or Deputy Secretary (or equivalent), as prescribed by FITARA. (Recommendation 15)
· The Secretary of Health and Human Services should direct the department CIO to work with OMB to ensure that annual reviews of their IT portfolio are conducted in conjunction with the Federal CIO and the Chief Operating Officer or Deputy Secretary (or equivalent), as prescribed by FITARA. (Recommendation 16)
· The Secretary of Homeland Security should direct the department CIO to work with OMB to ensure that annual reviews of their IT portfolio are conducted in conjunction with the Federal CIO and the Chief Operating Officer or Deputy Secretary (or equivalent), as prescribed by FITARA. (Recommendation 17)
· The Secretary of Homeland Security should direct the department CIO to ensure that the Federal CIO is consulted in performing high-risk IT investment reviews, as prescribed by FITARA. (Recommendation 18)
· The Secretary of Homeland Security should direct the department CIO, in conjunction with the project manager, to conduct high-risk IT investment reviews, as prescribed by FITARA. (Recommendation 19)
· The Secretary of Homeland Security should direct the department CIO to work with OMB to ensure that its high-risk IT investment reviews include the extent to which these causes can be addressed (e.g., action items and due dates) and the probability of future successes (e.g., outcomes), as prescribed by FITARA. (Recommendation 20)
· The Secretary of Housing and Urban Development should direct the department CIO to work with OMB to ensure that annual reviews of their IT portfolio are conducted in conjunction with the Federal CIO and the Chief Operating Officer or Deputy Secretary (or equivalent), as prescribed by FITARA. (Recommendation 21)
· The Secretary of Housing and Urban Development should direct the department CIO to ensure they conduct a review in conjunction with the investment’s program manager and in consultation with the Federal CIO, for major IT investments that have been designated as high risk for four consecutive quarters, as prescribed by FITARA, including identifying (1) the root causes of the high level of risk of the investment; (2) the extent to which these causes can be addressed (e.g., action items and due dates); and (3) the probability of future success (e.g., outcomes). (Recommendation 22)
· The Attorney General should direct the CIO of the Department of Justice to work with OMB to ensure that annual reviews of their IT portfolio are conducted in conjunction with the Federal CIO and the Chief Operating Officer or Deputy Secretary (or equivalent), as prescribed by FITARA. (Recommendation 23)
· The Secretary of Labor should direct the department CIO to work with OMB to ensure that annual reviews of their IT portfolio are conducted in conjunction with the Federal CIO and the Chief Operating Officer or Deputy Secretary (or equivalent), as prescribed by FITARA. (Recommendation 24)
· The Secretary of Labor should direct the department CIO to work with OMB to ensure they conduct a review in conjunction with the investment’s program manager and in consultation with the Federal CIO, for major IT investments that have been designated as high risk for four consecutive quarters, as prescribed by FITARA, including identifying (1) the root causes of the high level of risk of the investment; (2) the extent to which these causes can be addressed (e.g., action items and due dates); and (3) the probability of future success (e.g., outcomes). (Recommendation 25)
· The Secretary of State should direct the department CIO to work with OMB to work with OMB to ensure that annual reviews of their IT portfolio are conducted in conjunction with the Federal CIO and the Chief Operating Officer or Deputy Secretary (or equivalent), as prescribed by FITARA. (Recommendation 26)
· The Secretary of State should direct the department CIO to work with OMB to ensure that the Federal CIO is consulted in performing high-risk IT investment reviews, as prescribed by FITARA. (Recommendation 27)
· The Secretary of State should direct the department CIO to work with OMB to ensure that its high-risk IT investment reviews include a root cause analysis of the high level of risk and the probability of future successes (e.g., outcomes), as prescribed by FITARA. (Recommendation 28)
· The Secretary of the Interior should direct the department CIO to work with OMB to ensure that annual reviews of their IT portfolio are conducted in conjunction with the Federal CIO and the Chief Operating Officer or Deputy Secretary (or equivalent), as prescribed by FITARA. (Recommendation 29)
· The Secretary of the Interior should direct the department CIO to ensure that the Federal CIO is consulted in performing high-risk IT investment reviews, as prescribed by FITARA. (Recommendation 30)
· The Secretary of the Interior should direct the department CIO to ensure that its high-risk IT investment reviews document the extent to which these causes can be addressed (e.g., action items with due dates), as prescribed by FITARA. (Recommendation 31)
· The Secretary of the Treasury should direct the department CIO to work with OMB to ensure that annual reviews of their IT portfolio are conducted in conjunction with the Federal CIO and the Chief Operating Officer or Deputy Secretary (or equivalent), as prescribed by FITARA. (Recommendation 32)
· The Secretary of Transportation should direct the department CIO to work with OMB to ensure that annual reviews of their IT portfolio are conducted in conjunction with the Federal CIO and the Chief Operating Officer or Deputy Secretary (or equivalent), as prescribed by FITARA. (Recommendation 33)
· The Secretary of Veterans Affairs should direct the department CIO to work with OMB to ensure that annual reviews of their IT portfolio are conducted in conjunction with the Federal CIO and the Chief Operating Officer or Deputy Secretary (or equivalent), as prescribed by FITARA. (Recommendation 34)
· The Administrator of the Environmental Protection Agency should direct its agency CIO to work with OMB to ensure that annual reviews of their IT portfolio are conducted in conjunction with the Federal CIO and the Chief Operating Officer or Deputy Secretary (or equivalent), as prescribed by FITARA. (Recommendation 35)
· The Administrator of the General Services Administration should direct its agency CIO to work with OMB to ensure that annual reviews of their IT portfolio are conducted in conjunction with the Federal CIO, as prescribed by FITARA. (Recommendation 36)
· The Administrator of the National Aeronautics and Space Administration should direct its agency CIO to work with OMB to ensure that annual reviews of their IT portfolio are conducted in conjunction with the Federal CIO and the Chief Operating Officer or Deputy Secretary (or equivalent), as prescribed by FITARA. (Recommendation 37)
· The Director of the National Science Foundation should direct its agency CIO to work with OMB to ensure that annual reviews of their IT portfolio are conducted in conjunction with the Federal CIO and the Chief Operating Officer or Deputy Secretary (or equivalent), as prescribed by FITARA. (Recommendation 38)
· The Chairman of the Nuclear Regulatory Commission should direct its agency CIO to work with OMB to ensure that annual reviews of their IT portfolio are conducted in conjunction with the Federal CIO and the Chief Operating Officer or Deputy Secretary (or equivalent), as prescribed by FITARA. (Recommendation 39)
· The Director of the Office of Personnel Management should direct its agency CIO to work with OMB to ensure that annual reviews of their IT portfolio are conducted in conjunction with the Federal CIO, as prescribed by FITARA. (Recommendation 40)
· The Director of the Office of Personnel Management should direct its agency CIO to ensure they conduct a review in conjunction with the investment’s program manager and in consultation with the Federal CIO, for major IT investments that have been designated as high risk for four consecutive quarters, as prescribed by FITARA, including identifying (1) the root causes of the high level of risk of the investment; (2) the extent to which these causes can be addressed (e.g., action items and due dates); and (3) the probability of future success (e.g., outcomes). (Recommendation 41)
· The Administrator of the Small Business Administration should direct its agency CIO to work with OMB to ensure that annual reviews of their IT portfolio are conducted in conjunction with the Federal CIO and the Chief Operating Officer or Deputy Secretary (or equivalent), as prescribed by FITARA. (Recommendation 42)
· The Administrator of the Small Business Administration should direct its agency CIO to ensure they conduct a review in conjunction with the investment’s program manager and in consultation with the Federal CIO, for major IT investments that have been designated as high risk for four consecutive quarters, as prescribed by FITARA, including identifying (1) the root causes of the high level of risk of the investment; (2) the extent to which these causes can be addressed (e.g., action items and due dates); and (3) the probability of future success (e.g., outcomes). (Recommendation 43)
· The Commissioner of the Social Security Administration should direct its agency CIO to work with OMB to ensure that annual reviews of their IT portfolio are conducted in conjunction with the Federal CIO and the Chief Operating Officer or Deputy Secretary (or equivalent), as prescribed by FITARA. (Recommendation 44)
· The Administrator of the U.S. Agency for International Development should direct its agency CIO to work with OMB to ensure that annual reviews of their IT portfolio are conducted in conjunction with the Federal CIO and the Chief Operating Officer or Deputy Secretary (or equivalent), as prescribed by FITARA. (Recommendation 45)
· The Administrator of the U.S. Agency for International Development should direct its agency CIO to ensure they conduct a review in conjunction with the investment’s program manager and in consultation with the Federal CIO, for major IT investments that have been designated as high risk for four consecutive quarters, as prescribed by FITARA, including identifying (1) the root causes of the high level of risk of the investment; (2) the extent to which these causes can be addressed (e.g., action items and due dates); and (3) the probability of future success (e.g., outcomes). (Recommendation 46)
Agency Comments and Our Evaluation
We provided a draft of the report to the 24 Chief Financial Officers Act agencies, as well as OMB, for their review and comment. OMB provided written comments, reprinted in appendix V, and neither agreed nor disagreed with our recommendations. OMB responded on behalf of all the agencies to whom we made recommendations but noted that some agencies might respond to address their own circumstances. Of the 24 agencies, six agencies agreed with our recommendations, two neither agreed or disagreed with the recommendations in their comments, 12 deferred to OMB to provide a response, three agencies stated that they had no comments, and one agency provided comments too late to be included in the report but agreed with its recommendations.
In general, OMB stated that it believes that a number of our assertions—discussed below—are based on incorrect interpretations and applications of FITARA, resulting in incorrect conclusions regarding the obligations of OMB and other agencies. However, OMB acknowledged the merit of some of our recommendations and agreed that improvements are needed in the management of federal IT investments.
Regarding our findings on annual IT portfolio reviews,
· OMB acknowledged that it no longer uses the approach described in its memorandum M-15-14 (i.e., quarterly reviews of each agency’s IT portfolio with OMB, the agency CIO, and other personnel). OMB explained that the memorandum reflects priorities and expectations that existed before a “sea change” in federal IT where OMB and agencies had to contend with ever-evolving technology landscapes along with, in some cases, contracting budgets. To illustrate, OMB stated that its Office of the Federal CIO supports the implementation of more than 30 laws but experienced a $5.7 million reduction in its IT oversight and reform appropriation in fiscal year 2024. While we recognize that OMB and agencies may face resource limitations, the federal government spends over $100 billion annually on IT, and effective prioritization of the management of this portfolio could help prevent waste. Further, as we recommend in this report, OMB should update the IT portfolio review guidance to reflect the process it requires agencies to follow.
· OMB reported that it had adopted “more efficient means” of meeting FITARA’s requirements due to budget constraints and increased workload. Specifically, rather than holding a single (or quarterly) session every year with the CIO of each CFO Act agency, as it did when its guidance was first issued, OMB stated that it has integrated agency IT portfolio reviews into the agencies’ budget and reporting processes. As a part of this, agencies are required to submit their IT budget and investment information to OMB via the IT Dashboard. OMB’s Office of the Federal CIO uses this information during engagements with agencies to address any IT issues and inform the budget formulation process. OMB stated that this approach allows for ongoing review of an agency’s IT portfolio. Additionally, OMB stated that this facilitates more frequent interactions between OMB and agencies to address issues dynamically rather than through a single, rigid review session. We acknowledge that IT portfolio reviews can be iterative in nature. However, we reviewed agencies’ documentation of these interactions, and as we discuss in the report, these interactions did not fully meet FITARA’s requirements.
· OMB stated that our report assumes that the Federal CIO should be personally involved with the IT portfolio review by meeting with the agency CIO once a year. OMB further stated that because an agency official may act through their subordinates, it is OMB’s position that the Federal CIO is not required to participate in each of those engagements personally but may instead supervise and coordinate participation by staff members.
However, as previously stated, FITARA requires that the agency CIO, along with the agency Chief Operating Officer or Deputy Secretary (or equivalent) and the Federal CIO, conduct an annual IT portfolio review. While FITARA does not explicitly address delegation by the Federal CIO, it clearly requires visibility and interaction between high-level officials. This includes agency CIOs, whose involvement in some specified areas of IT oversight is generally nondelegable under 40 U.S.C. 11319(b)(C)(ii), and the Federal CIO. As such, FITARA contemplates that high-level officials should be involved in the oversight of the IT portfolio. This is bolstered by FITARA specifically requiring the Federal CIO to submit a quarterly report to Congress on the cost savings and reductions in duplicative information technology investments identified through the annual review; an oversight mechanism that the Federal CIO failed to comply with. The Federal CIO has not submitted these required quarterly reports. Moreover, OMB has not provided documentation to demonstrate such delegation of duties or the Federal CIO's involvement in the portfolio review process, which further limits FITARA's intended oversight function.
Regardless of these disagreements, OMB stated that it will continue to assess potential adjustments to the annual IT portfolio review process and indicated that it will evaluate our recommendations on how to further strengthen the review of agency IT portfolios. Given the approximately $100 billion spent annually on IT, it is critical that OMB ensure comprehensive reviews of each agency's IT portfolio, as we recommend.
Regarding our findings on high-risk IT investment reviews,
· OMB disagreed with our methodology of identifying high-risk IT investments and stated that it considers a risk rating of “1” to be the trigger for a high-risk review under FITARA. However, as we note in our report and OMB acknowledges in its comments, OMB’s FITARA implementation guidance, M-15-14, equates a high-risk rating with a rating that is “red” on the IT Dashboard. As a result, we identified those IT investments that received a red rating (i.e., a “1” or a “2”) on the dashboard for four consecutive quarters.
· OMB stated that it no longer uses that methodology to categorize risk and is taking steps to make that clear. While we agree that clarification of the outdated policy is warranted, we believe that FITARA’s intent is for agency CIOs, in conjunction with the Federal CIO, to review persistently high-risk IT investments to identify the root causes of the high level of risk and the extent to which these causes can be addressed. OMB’s Circular A-11 defines levels “1” and “2” on the IT Dashboard as high risk and moderately high risk—both categories of high risk. Therefore, we believe there is merit in investigating the causes of high risk and attempting to address the cause of any IT investment that is considered any level of high risk for 12 consecutive months or more.
In addition, including those rated moderately high risk (i.e. a “2” rating) could allow the government to proactively address issues, rather than reacting. Further, if OMB restricts the high-risk IT investment reviews to only those at the highest level of high risk, it may miss insights into other risky IT investments. Moreover, restricting the high-risk IT investments to only the highest level of risk may encourage agencies to understate the risk levels of their IT investments.
Regarding our findings on OMB’s statutory requirements to report to Congress, OMB indicated that it had plans to address this finding. Specifically, OMB stated that it will seek to add fields to the IT Dashboard to collect information on reduced duplication and net program benefits achieved as a result of major capital investments from agencies. This will make it accessible to Congress. We agree that this approach could fulfill the intent of FITARA and address our recommendation.
Lastly, OMB stated that the process-oriented requirements in FITARA can be useful tools but noted that it is important not to adopt such a rigid interpretation of those requirements that they crowd out what really matters—substantive results. OMB also stated that the efforts of OMB and agencies in recent years have yielded significant success.
While we recognize that there have been some successes in IT management, as this report demonstrates there is more to be done to effectively manage the government’s vast IT portfolio. FITARA was intended to provide the Federal CIO and agency CIOs with the tools needed to successfully manage their agencies’ IT portfolios. The FITARA-required activities of annual portfolio reviews and high-risk investment reviews are foundational to managing and providing oversight to the over $100 billion spent on IT every year. As a result, we believe that our findings and recommendations are warranted.
The 24 Chief Financial Officers Act agencies responded as follows:
· six agencies (the Departments of Agriculture, Defense, Homeland Security, and Veterans Affairs; the National Aeronautics and Space Administration, and U.S. Agency for International Development) agreed with our recommendations;
· two agencies (Departments of Justice and the Treasury) neither agreed nor disagreed with the recommendations in their comments;
· 12 agencies (the Departments of Commerce, Education, Energy, Health and Human Services, Housing and Urban Development, the Interior, and State; the Environmental Protection Agency; General Services Administration; National Science Foundation; Nuclear Regulatory Commission; and Social Security Administration) deferred to OMB to provide a response on behalf of the agency;
· three agencies (Departments of Labor and Transportation and the Small Business Administration) stated that they had no comments on the report; and
· one agency (the Office of Personnel Management) provided comments too late to be included in the report, but agreed with its recommendations.
The following six agencies agreed with our recommendations:
· In comments provided via email on September 18, 2024, the Department of Agriculture’s Audit Liaison stated that Agriculture generally concurred with the findings and recommendations in the report.
· The Department of Defense provided written comments stating that it concurred with the recommendation. The department further stated if OMB issues updated or new annual IT portfolio review guidance, the department’s CIO will review the guidance to ensure compliance. This will include attending and participating in scheduled OMB annual reviews of their IT portfolio. The department’s comments are reprinted in appendix VI.
· DHS provided written comments stating that it concurs with the recommendations and provided details on how it intends to implement them. Regarding the recommendation on conducting annual reviews of the IT portfolio, the department plans to create a standard operating procedure revising its current processes, as appropriate, to ensure an annual review with the necessary stakeholders is conducted. It estimated that it would be completed by September 30, 2025.
Regarding the recommendation on consulting the Federal CIO in performing high-risk IT investment reviews, the department stated they will engage with the Federal CIO for all future high-risk IT investments and ensure a copy of the outcome of each review is provided upon completion. It estimated that it would be completed by December 31, 2024.
Regarding the recommendation on conducting high-risk IT investment reviews with the project manager, the department stated that it will update policy and guidance requiring all future reviews to be held in conjunction with the project manager and estimated that it would be updated by September 30, 2025. In response to our recommendation on ensuring that high-risk IT investment reviews include action items, due dates, and outcomes, the department stated that it will update policy and estimated that this would be completed by September 30, 2025.
The department expressed disagreement with our interpretation of certain FITARA requirements and how the department was meeting them. Specifically, the department stated that there is no explicit requirement in FITARA that the consultation between the agency CIO and the Federal CIO must occur during a TechStat meeting. The department also added that while the CIO does not attend every high-risk IT investment review, the CIO does consult with the Federal CIO outside of these meetings, and the department believes that this as-needed consultation fulfills the intent of FITARA. However, FITARA requires consultation between the agency CIO and the Federal CIO for high-risk IT investment reviews. The department did not provide documentation that these consultations occurred for its high-risk investments under review, whether during TechStat sessions or through other means. DHS’s comments are reprinted in appendix VII. The department also provided technical comments which we incorporated as appropriate.
· The Department of Veterans Affairs provided written comments stating that it concurs with the recommendation. The department stated that it deferred to OMB’s response to our recommendation regarding the review of agencies' IT portfolios and intends to work with OMB to ensure that all requirements are fulfilled. The department’s comments are reprinted in appendix VIII.
· The National Aeronautics and Space Administration provided written comments stating that it concurs with the recommendation and plans to update its existing IT portfolio review process to ensure an annual review is conducted with the agency CIO, Chief Operating Officer, and the Federal CIO. The agency estimated that it would be completed by December 31, 2025. The agency’s comments are reprinted in appendix IX.
· The U.S. Agency for International Development provided written comments stating that it concurs with its recommendations. Regarding the recommendation on conducting annual reviews of the IT portfolio, the agency stated that it plans to revise its current processes to ensure engagement with the necessary stakeholders. The agency estimated that it would complete this action by December 31, 2024. In response to our recommendation on high-risk IT investment reviews, the agency stated that it plans to incorporate steps into its processes to ensure that major investments that are designated as high risk for four consecutive quarters are reviewed, as required by FITARA. The agency estimated that it will complete this action by December 31, 2024. The agency’s comments are reprinted in appendix X.
Two agencies did not state whether they agreed or disagreed with our recommendations:
· In comments provided via email on October 11, 2024, a Management and Program Analyst with the Department of Justice’s Audit Liaison Group did not agree or disagree with the recommendations.
· The Department of the Treasury provided written comments that did not state whether the agency agreed or disagreed with our recommendation but had comments regarding a partial rating regarding its compliance with the CIO’s attendance at its annual IT portfolio reviews in our draft report. Treasury stated that it provided documentation confirming that its CIO conducted IT annual portfolio reviews with all bureaus and components except for the Office of the Comptroller of the Currency. Treasury also stated that the CIO has attempted to hold a review with that office, but the office claimed that it is independent of FITARA requirements. Treasury submitted documentation of that office’s assertion. Treasury and the Office of the Comptroller of the Currency apparently lack consensus on whether or not the office should be part of the department’s FITARA reviews. Due to a lack of information regarding the efficacy of the office’s assertion, we decided to not factor this aspect into our findings. As a result, we made an update to the report language to make that clear and provide Treasury with full credit for the CIO performing annual reviews of its portfolio. However, since Treasury’s annual IT portfolio review did not include the Deputy Secretary or the Federal CIO, we believe the associated recommendation stands. Treasury’s comments are reprinted in appendix XI.
The following 12 agencies did not provide any comments and deferred to OMB’s response:
· In comments provided via email on October 11, 2024, Commerce’s GAO/OIG Audit Liaison stated that the department did not have any comments as OMB’s response aligned with their planned response.
· In comments provided via email on October 11, 2024, a representative from the Department of Education’s Office of the Secretary stated that the department would defer to OMB’s response. The department also provided technical comments which we incorporated as appropriate.
· In comments provided via email on October 3, 2024, a representative from the Department of Energy’s Office of the Chief Financial Officer’s Office of Financial Policy and Audit Resolution stated that Energy would defer to OMB’s response to the report.
· In comments provided via email on September 24, 2024, a Management Analyst/Audit Liaison from the Department of Health and Human Services stated that the department did not have any comments due to OMB’s response to the report.
· In comments provided via email on October 1, 2024, an Audit Liaison Officer from the Department of Housing and Urban Development stated that the department would defer to OMB’s response to the report.
· In comments provided via email on October 10, 2024, the Office of the Chief Information Officer Audit Liaison Lead from the Department of the Interior stated that the department would defer to OMB’s response to the report.
· In comments provided via email on October 9, 2024, a Senior Management Analyst within the Department of State’s GAO Liaison Office stated that the department would defer to OMB’s response to the report.
· In comments provided via email on October 9, 2024, the Audit Follow-up Coordinator from the Environmental Protection Agency’s Office of Missions Support stated that the agency would defer to OMB’s response to the report.
· In comments provided via email on September 30, 2024, a Program Analyst from the General Services Administration’s Office of Audit Management and Accountability stated that the agency would defer to OMB’s response to the report.
· In comments provided via email on October 8, 2024, an Analyst from the National Science Foundation’s Policy, Audit and Enterprise Risk Management office stated that the agency would defer to OMB’s response to the report.
· In comments provided via email on October 4, 2024, an Executive Technical Assistant within the Nuclear Regulatory Commission’s Office of the Executive Director for Operations stated that the agency would defer to OMB’s response to the report and will respond to agency specific recommendations as required.
· The Social Security Administration provided written comments stating that it deferred to OMB’s response to the report. The agency’s comments are reprinted in appendix XII. The Social Security Administration also provided technical comments which we incorporated as appropriate.
The following three agencies did not have comments on our report:
· In comments provided via email on October 3, 2024, a representative from the Department of Labor’s Office of the Assistant Secretary for Policy stated that the department did not have any comments on the report.
· In comments provided via email on October 3, 2024, the Deputy Director of the Department of Transportation’s Audit Relations and Program Improvement office stated that Transportation would not be providing a written management response and did not have any technical comments on the report.
· In comments provided via email on October 16, 2024, the GAO Liaison from the Small Business Administration stated that the agency had no comments on the report.
We are sending copies of this report to the appropriate congressional committees, the Director of the Office of Management and Budget, and the secretaries and heads of the departments and agencies addressed in this report. In addition, the report is available at no charge on the GAO website at http://www.gao.gov.
If you or your staff have any questions about this report, please contact Kevin Walsh at (202) 512-6151 or WalshK@gao.gov. Contact points for our Offices of Congressional Relations and Public Affairs may be found on the last page of this report. GAO staff who made key contributions to this report are listed in appendix XIII.
Sincerely,
Kevin Walsh
Director, Information Technology and Cybersecurity
Our objectives were to (1) assess the extent to which the Office of Management and Budget (OMB) is following statutory requirements for IT portfolio management oversight, including annual IT portfolio reviews and high-risk IT investment reviews, and (2) assess the extent to which agencies are following statutory requirements for IT portfolio management oversight, including annual IT portfolio reviews and high-risk IT investment reviews. The scope of our review includes OMB and the 24 federal agencies covered by the Chief Financial Officers Act of 1990 that also generally correspond to the agencies covered by FITARA.[51]
To address the first objective, we identified the Federal Information Technology Acquisition Reform Act’s (FITARA)[52] requirements for OMB to conduct and oversee annual IT portfolio reviews and high-risk investment reviews.[53] Based on our review, we identified eight requirements for OMB. Table 8 provides a summary of those requirements.
Table 8: Summary of Selected Federal Information Technology Acquisition Reform Act Requirements for the Office of Management and Budget
|
Requirement |
Source |
|
IT portfolio reviews |
|
|
Implement a process to assist agencies in reviewing their IT portfolios to: · identify or develop ways to increase the efficiency and effectiveness of the agency’s IT investments; · identify or develop opportunities to consolidate the acquisition and management of IT services and increase the use of shared-service delivery models; · identify potential duplication and waste; · identify potential cost savings; · develop plans for actions to optimize the IT portfolio, programs, and resources; · develop ways to better align the IT portfolio, programs, and financial resources to any multi-year funding requirements or strategic plans required by law; and · develop a multi-year strategy to identify and reduce duplication and waste within the IT portfolio, including component-level investments, and to identify projected cost savings resulting from such strategy. |
40 U.S.C. 11319(d)(1) |
|
Develop standardized cost savings/avoidance and performance metrics for agencies to implement the process, in consultation with agency chief information officers (CIO).a |
40 U.S.C. 11319(d)(2) |
|
Carry out the Federal CIO’s role in an annual review of each agency’s IT portfolio that is conducted by the CIO of each agency in conjunction with the Chief Operating Officer or Deputy Secretary (or equivalent) of each agency and the Federal CIO. |
40 U.S.C. 11319(d)(3) |
|
Submit a quarterly report on the cost savings and reductions in duplicative IT investment identified through this review process to the Senate Committee on Homeland Security and Governmental Affairs and the Committee on Appropriations, the House Committee on Oversight and Government Reformb and the Committee on Appropriations, and upon request by any committee of Congress. |
40 U.S.C. 11319(d)(5) |
|
Submit to Congress, at the same time that the President submits the budget for a fiscal year, a report on the net program performance benefits achieved as a result of major capital investments made by agencies for information systems and how the benefits relate to the accomplishment of the goals of the agencies. |
40 U.S.C. 11302(c)(5) |
|
High-risk IT investment reviews |
|
|
Carry out consultation responsibilities of the Federal CIO to agency CIOs and program managers of major IT investments that receive high-risk ratings for four consecutive quarters. |
40 U.S.C. 11302(c)(4)(A) |
|
Through the Federal CIO, communicate the results of required high-risk IT investment reviews to the Senate Committee on Homeland Security and Governmental Affairs, the House Committee on Oversight and Government Reformb and the House and Senate Appropriations Committees, and the committees of the Senate and House with primary jurisdiction over the agency. |
40 U.S.C. 11302(c)(4)(B) |
|
Ensure that, for agencies other than the Department of Defense, if 1 year after the date of completion of the high-risk IT investment review the major IT investment is still rated as high-risk, any request of additional development, modernization, or enhancement funding for the major investment is denied until the date on which the agency CIO determines that the root causes of the high level of risk have been addressed, and there is sufficient capability to deliver the remaining planned increments within the planned cost and schedule. |
40 U.S.C. 11302(c)(4)(D) |
Source: The Federal Information Technology Acquisition Reform Act (FITARA) provisions of the Carl Levin and Howard P. “Buck” McKeon National Defense Authorization Act for Fiscal Year 2015, Pub. L. No. 113-291, division A, title VIII, subtitle D, 128 Stat. 3292, 3438-3450 (Dec. 19, 2014). | GAO‑25‑107041
aFITARA uses the term “performance indicators” but we refer to them in this report as metrics for simplicity.
bThis committee is now called the Committee on Oversight and Accountability.
To determine the extent to which OMB was following these requirements, we obtained and assessed OMB documentation related to annual IT portfolio reviews and high-risk investment reviews, such as OMB guidance and information found on the IT Dashboard.
We assessed OMB’s compliance with the FITARA requirements applicable to OMB as follows:
· fully following, if available evidence demonstrated OMB is following all aspects of the requirement;
· partially following, if available evidence demonstrated OMB is following some, but not all, of the requirement; or
· not following, if available evidence did not demonstrate OMB is following any aspect of the requirement.
To determine the extent to which OMB had followed a FITARA requirement on reporting cost savings to Congress, we downloaded the cost savings from the IT Dashboard for 23 of the 24 agencies.[54] We compiled the data from each agency into a single file and isolated those cost savings that were attributed to holding PortfolioStats. In order to assess the reliability of this data, we (1) reviewed related documentation such as documentation on OMB’s Integrated Data Collection and the IT Dashboard; (2) assessed the data for obvious outliers, errors, or missing data; and (3) reviewed agency documentation and written responses demonstrating how the agency derived these cost savings/avoidances. We determined that the cost saving/avoidance data were not sufficiently reliable and discuss these issues in this report.
To address the second objective, we identified FITARA’s requirements for agencies to conduct annual IT portfolio reviews and high-risk investment reviews. Based on our review, we identified one requirement on annual IT portfolio reviews for agencies. Specifically, FITARA requires agency CIOs to conduct an annual review of the agency’s IT portfolio, in conjunction with the Chief Operating Officer or Deputy Secretary (or equivalent) and the Federal CIO.[55]
We also identified three requirements for agencies on high-risk investment reviews. Specifically:
· The agency CIO and the program manager of the investment are to conduct a review on a major IT investment when it has received a high-risk rating for four consecutive quarters;
· The agency CIO and program manager shall consult with the Federal CIO on the review; and
· The agency CIO and program manager shall include in the reviews root cause analysis of the high level of risk, extent to which these causes can be addressed, and probability of future successes.[56]
For the requirements on annual IT portfolio reviews, we compared agency documentation, including portfolio review meeting minutes, slides, and memorandums, to the FITARA requirements. We assessed agencies’ compliance with the FITARA requirements applicable to agencies as follows:
· fully following, if available evidence demonstrated the agency was following all aspects of the requirement;
· partially following, if available evidence demonstrated the agency was following some, but not all, of the requirement; or
· not following, if available evidence did not demonstrate that the agency was following any aspect of the requirement.
To determine the extent to which agencies were following FITARA’s requirements for high-risk IT investment reviews, in August 2023, we downloaded the “CIO Evaluation History” from the IT Dashboard.[57] FITARA states that a “high-risk rating” shall be categorized in accordance with guidance from OMB.[58] OMB’s FITARA implementation guidance equates a high-risk rating with a rating that is red (i.e., a risk rating of 1 or 2) on the IT Dashboard.[59] As a result, we reviewed the CIO ratings for major investments between November 2020 and August 2023 to identify those that received a high-risk rating for at least four consecutive quarters. We determined 17 investments met this criterion and, therefore, agencies were required to hold a high-risk IT investment review for these investments. See appendix II for this list of these investments.
We requested information from the agencies regarding the reviews held on these 17 investments, as applicable. We compared agency documentation, including meeting minutes and memorandums, to FITARA’s requirements on high-risk IT investment reviews. We assessed the FITARA requirements for agencies as:
· fully following, if available evidence demonstrated the agency was following all aspects of the requirement;
· partially following, if available evidence demonstrated the agency was following some, but not all, of the requirement; or
· not following, if available evidence did not demonstrate that the agency was following any aspect of the requirement.
In addition, we downloaded background information from the IT Dashboard on these investments, such as the investment title and planned expenditures. In order to determine the reliability of this data, as well as the aforementioned CIO evaluation data, we (1) reviewed related documentation, such as the IT Dashboard Frequently Asked Questions; (2) assessed the data for obvious outliers, errors, or missing data; and (3) reviewed agency documentation and written responses verifying this information. We determined that the data were sufficiently reliable for our purposes of identifying investments that met the FITARA threshold and providing background information on those investments.
We also collected information from agencies on the number of high-risk IT investment reviews they have held since 2010 and the year the last review took place.
For both of the objectives, we met with relevant officials at OMB and the agencies to obtain additional information on agency efforts to meet FITARA’s IT portfolio management requirements. These officials included staff from OMB’s Office of the Federal CIO and the agencies’ offices of the CIO, such as CIOs and the Deputy Chief Information Security Officers.
We conducted this performance audit from August 2023 to November 2024 in accordance with generally accepted government auditing standards. Those standards require that we plan and perform the audit to obtain sufficient, appropriate evidence to provide a reasonable basis for our findings and conclusions based on our audit objectives. We believe that the evidence obtained provides a reasonable basis for our findings and conclusions based on our audit objectives.
Agencies reported using a variety of mechanisms to fulfill the Federal Information Technology Acquisition Reform Act requirements. Table 9 provides details of agencies’ reported processes.
|
Agency |
Portfolio review mechanisms |
|
Department of Agriculture (USDA) |
USDA reported holding quarterly customer profile reviews with its mission areas. USDA officials stated that these reviews resemble PortfolioStats, employing a data-driven approach alongside Chief Information Officer (CIO) rating criteria and their Enterprise Governance process to assess USDA’s IT portfolio. In addition, the CIO has given authority to the Assistant CIOs to conduct their own annual IT portfolio reviews for their mission areas. |
|
Department of Commerce (Commerce) |
Commerce reported conducting annual IT Portfolio reviews and monthly CIO Council meetings with bureau CIOs. Commerce officials also stated that the CIO participates with the Deputy Secretary in the comprehensive annual bureau budget review which includes the IT portfolio. In addition, officials mentioned having ad hoc meetings with the Office of Management and Budget’s (OMB) desk officer to discuss IT portfolio topics. |
|
Department of Defense (DOD)a |
DOD officials reported that the agency held a high-level IT portfolio review, per its CIO Risk Rating Process guidance, that was provided to OMB. This review described DOD’s IT priorities and funding. |
|
Department of Education (Education) |
Education reported conducting an annual review of its IT portfolio through its Investment Review Board that is co-chaired by the Deputy Secretary and their CIO. Additionally, officials from Education mentioned their participation in OMB desk officer review sessions. |
|
Department of Energy (Energy) |
Energy officials reported that their CIO regularly meets with OMB desk officers to review budget and IT portfolio priorities. In addition, Energy stated that its CIO reviews IT budgets with its components during an IT Dashboard data call. In addition, Energy submits information including performance metrics on IT investments through the Federal IT Dashboard. |
|
Department of Health and Human Services (HHS) |
HHS reported conducting annual IT portfolio reviews with the agency’s operating divisions. In addition, HHS officials stated that the CIO attends monthly OMB desk officer meetings. |
|
Department of Homeland Security (DHS) |
DHS reported using its monthly desk officer meetings with OMB to fulfill the Federal Information Technology Acquisition Reform Act (FITARA) requirements on conducting annual IT portfolio reviews. |
|
Department of Housing and Urban Development (HUD) |
HUD officials reported using its desk officer meetings with OMB to review its IT portfolio. In addition, HUD reported holding annual budget reviews with OMB for its appropriated IT fund, which includes both enterprise infrastructure and mission supporting applications. |
|
Department of Justice (Justice) |
Justice reported that its CIO holds monthly meetings with an OMB desk officer and the Office of the Chief Information Officer (OCIO) participates in monthly Federal CIO Council meetings to fulfill FITARA requirements. |
|
Department of Labor (Labor) |
Labor reported holding monthly meetings with an OMB desk officer, monthly meetings with the CIO Council with the Federal CIO present, and meetings on Labor’s Technology Modernization Fund Project Portfolio to review the IT portfolio and fulfill FITARA requirements. |
|
Department of State (State) |
State reported that its CIO meets with an OMB desk officer monthly to fulfill FITARA requirements. Furthermore, the CIO conducts quarterly briefings with the Under Secretary for Management and the Deputy Secretary for Management and Resources regarding the agency’s IT portfolio and high-risk investments. |
|
Department of the Interior (Interior) |
Interior reported that its Deputy CIO of Program Management holds weekly meetings with an OMB desk officer and the CIO meets with the OMB desk officer at least twice a year to fulfill FITARA requirements. Interior also reported holding IT portfolio reviews three times per year with the agency CIO, bureau and office Associate CIOs, bureau deputy directors, bureau budget officers, and other stakeholders with significant responsibility over IT. Further, the department stated that the Interior CIO is an active participant in the Federal CIO Council. |
|
Department of the Treasury (Treasury) |
Treasury reported conducting annual IT portfolio reviews with bureau CIOs and meetings with OMB’s Office of the Federal CIO. |
|
Department of Transportation (Transportation) |
Transportation reported that it holds regular meetings with its assigned OMB desk officer, as well as internal reviews of its IT portfolio to fulfill FITARA requirements. |
|
Department of Veterans Affairs (VA) |
VA officials reported that while they have not held an annual review with the Federal CIO in the past 2 years, it does hold regular and recurring internal portfolio reviews with the agency CIO. |
|
Environmental Protection Agency (EPA) |
EPA officials reported that it conducts IT portfolio reviews internally through governance processes, working with all major programs and regions. In addition, EPA conducts annual reviews and obtains approval of its IT portfolio through its CIO-Senior Advisory Council, consisting of the agency CIO in partnership with agency Senior Information Officials representing EPA’s programs and regions. |
|
General Services Administration (GSA) |
GSA officials reported their last annual IT portfolio review took place in 2018. However, GSA stated that the agency CIO holds weekly meetings with their Deputy Administrator to meet the FITARA requirement for an annual IT portfolio review. |
|
National Aeronautics and Space Administration (NASA) |
NASA officials stated to meet the FITARA requirements for annual IT portfolio reviews, the agency reviews its IT portfolio as part of the agency budget request submission to OMB. This submission is reviewed and approved by the agency Chief Financial Officer and the NASA Executive Council prior to submission to OMB.b |
|
National Science Foundation (NSF) |
NSF officials stated that its CIO continually reviews the IT portfolio as part of the agency’s IT governance process. According to the agency, specific mechanisms for this process include annual budget planning, formulation, and execution processes, including quarterly IT Capital Planning and Investment Control meetings, CIO concurrence with the agency’s annual budget submission, and regular IT compliance mechanisms including the quarterly Information Data Collection (IDC), monthly IT Dashboard reviews, and coordinated reviews of all agency IT acquisitions. NSF officials were able to provide documentation demonstrating that the IT portfolio is reviewed during this process. |
|
Nuclear Regulatory Commission (NRC) |
NRC officials reported conducting semiannual FITARA briefings with NRC’s Executive Director for Operations and Deputy Executive Director for Operations, as well as reviews for all the major IT Investments. NRC regularly reviews the IT portfolio as part of the agency’s IT governance process. Specific mechanisms include annual budget planning, formulation, and execution processes, including quarterly IT Capital Planning and Investment Control meetings, CIO concurrence with the agency’s annual budget submission, leveraging the Information Technology/Information Management Portfolio Executive Council to review and align on modernization goals, and explore shared solutions through GSA’s IT Vendor Management Office. The CIO also conducts semiannual FITARA briefings with NRC’s Executive Director for Operations and Deputy Executive Director for Operations, and regularly reviews the quarterly IDC, monthly IT Dashboard, and agency IT acquisitions as part of routine IT portfolio maintenance. Further, the CIO utilizes informal interactions with system owners and Contracting Officer Representatives/Contracting Officer Technical Representatives to supplement formal IT portfolio review. |
|
Office of Personnel Management (OPM) |
OPM officials reported holding monthly meetings between OMB and the OPM CIO. The monthly meeting is the mechanism for the CIO and other stakeholders, including the Office of the Director, Chief Management Officer, and the Chief Financial Officer, to discuss current IT projects and priorities including the IT budget. In addition, OPM’s OCIO holds monthly desk officer meetings with OMB. |
|
Small Business Administration (SBA) |
SBA officials reported conducting one annual IT portfolio review in 2021. In addition, SBA stated that it conducts monthly investment review meetings of its major IT investments to include milestone reviews, operational analysis, CIO ratings, and risk management. |
|
Social Security Administration (SSA) |
SSA officials reported conducting a review of its IT portfolio annually. |
|
U.S. Agency for International Development (USAID) |
USAID officials reported the agency CIO holds regular meetings with the agency Chief Operating Officer and Deputy Administrator for management and resources, as well as regularly scheduled meetings with OMB desk officers. In addition, the portfolio is reviewed through its risk management process, Project Management Office on a biweekly bases, and continuous monitoring. |
Source: GAO analysis of agency provided data. | GAO‑25‑107041
aAccording to FITARA, DOD may use an existing investment or review process for its IT portfolio reviews.
bAccording to NASA officials, the Executive Council includes the NASA Administrator, Deputy Administrator, and Associate Administrator.
Appendix III: List of Major IT Investments Rated as High Risk for Four Consecutive Quarters between November 2020 and August 2023
Table 10 provides details on the 17 major investments that were rated as high risk for at least four consecutive quarters between November 2020 and August 2023, the number of months designated as high risk, whether a review was held on the investment, and the planned expenditures for fiscal year 2024.
|
Agency |
Investment |
Number of months rated high risk |
Required review held? |
Planned expenditures for fiscal year 2024, in millions |
|
Department of Homeland Security |
Financial Systems Modernization - Trio |
12 |
Yes |
59.0 |
|
Homeland Advanced Recognition Technology |
26 |
Yes |
39.7 |
|
|
Customs and Border Protection - Biometric Entry-Exit |
19 |
Yes |
21.4 |
|
|
Department of Housing and Urban Development |
Single Family Housing |
12 |
No |
47.5 |
|
Department of Labor |
Employment and Training Administration Unemployment Insurance State Support Services |
15 |
No |
24.9 |
|
Department of State |
Global Foreign Affairs Compensation System |
24 |
Yes |
30.2 |
|
Foreign Assistance Coordination and Tracking System |
24 |
Yes |
4.7a |
|
|
Department of the Interior |
Bureau of Indian Affairs - Trust Asset Accounting Management System |
12 |
Yes |
15.7 |
|
Incident Management, Analysis, and Reporting System |
16 |
Yes |
8.0 |
|
|
Fish and Wildlife Service - Law Enforcement Management Information System |
16 |
Yes |
1.2 |
|
|
Bureau of Trust. Funds Administration - Accounting Reconciliation Tool |
31 |
Yes |
0.8 |
|
|
Office of Personnel Management |
Retirement Benefits Services |
24 |
No |
16.1 |
|
Merit System Audit and Compliance - Combined Federal Campaign Central Campaign Administrator Systems |
16 |
No |
0.3 |
|
|
Chief Information Officer – myPayc |
19 |
No |
0.0b |
|
|
Small Business Administration |
(Office of Government Contracting and Business Development) Certify.SBA.GOV |
28 |
No |
8.9 |
|
(Office of Chief Information Officer) SBA.gov |
27 |
No |
2.6 |
|
|
U.S. Agency for International Development |
Bureau for Management, Office of Chief Information Officer (M/CIO) - Development Information Solution |
27 |
No |
14.7 |
Source: GAO analysis of agency provided data. | GAO‑25‑107041
aInvestment’s total planned expenditure for fiscal year 2024 is $9.9 million, when $5.2 million in other agency contributions is factored in.
bInvestment’s total planned expenditure for calendar year 2024 is $5.0 million, when $5.0 million in other agency contributions is factored in.
cChief Information Officer – myPay is managed by the Department of Defense’s Defense Finance and Accounting Service Project Office; however, the system is hosted, developed, and maintained by OPM’s Office of the Chief Information Officer. OPM’s Chief Information Officer rated this investment as high-risk.
Most agencies reported holding various reviews of high-risk investments over the last 13 years. Specifically, 21 of the 24 agencies reported that they conducted a total of 389 reviews of high-risk IT investments from 2010 to May 2024. Three agencies reported that they did not conduct any high-risk IT investment reviews during this time and 13 agencies’ last reported review was more than 5 years ago. Table 11 demonstrates the number of high-risk IT investment reviews agencies reported holding between 2010 and May 2024, as well as the year of the last review.
|
Agency |
Number of reviews |
Year of last review |
|
Department of Agriculture |
126 |
2024 |
|
Department of Commerce |
17 |
2017 |
|
Department of Defense |
0 |
N/Ab |
|
Department of Education |
6 |
2017 |
|
Department of Energy |
5 |
2013 |
|
Department of Health and Human Services |
5 |
2017 |
|
Department of Homeland Security |
12 |
2023 |
|
Department of Housing and Urban Development |
3 |
2023 |
|
Department of Justice |
89 |
2024 |
|
Department of Labor |
1 |
2016 |
|
Department of State |
8 |
2024 |
|
Department of the Interior |
10 |
2024 |
|
Department of the Treasury |
21 |
2018 |
|
Department of Transportation |
0 |
N/Aa |
|
Department of Veterans Affairs |
46 |
2018 |
|
Environmental Protection Agency |
4 |
2023 |
|
General Services Administration |
0 |
N/Aa |
|
National Aeronautics and Space Administration |
3 |
2012 |
|
National Science Foundation |
3 |
2012 |
|
Nuclear Regulatory Commission |
5 |
2012 |
|
Office of Personnel Management |
8 |
2024 |
|
Small Business Administration |
6 |
2017 |
|
Social Security Administration |
10 |
2017 |
|
U.S. Agency for International Development |
1 |
2012 |
|
Total |
389 |
n/a |
Source: GAO analysis of agency-provided data. | GAO‑25‑107041
aThis table does not account for the number of reviews the agency should have had over this time period.
bAccording to officials at the Departments of
Defense and Transportation and the General Services Administration, their
respective agencies have not had an investment that has received a high-risk
rating for four consecutive quarters, and therefore, did not require a review.
Figure 2 illustrates the timeline of the last year each agency reported conducting their last high-risk IT investment reviews between 2010 and 2024.


















GAO Contact
Kevin Walsh at (202) 512-6151 or WalshK@gao.gov
Staff Acknowledgments
In addition to the individual named above, principal contributors to this report were Jessica Steele (Assistant Director), Ash Huda (Analyst-in-Charge), Chris Businsky, Rebecca Eyler, Sami Ghusn, Colin Jenkins, Michael Lebowitz, Nathan Nguyen, and Andrew Weiss.
GAO’s Mission
The Government Accountability Office, the audit, evaluation, and investigative arm of Congress, exists to support Congress in meeting its constitutional responsibilities and to help improve the performance and accountability of the federal government for the American people. GAO examines the use of public funds; evaluates federal programs and policies; and provides analyses, recommendations, and other assistance to help Congress make informed oversight, policy, and funding decisions. GAO’s commitment to good government is reflected in its core values of accountability, integrity, and reliability.
Obtaining Copies of GAO Reports and Testimony
The fastest and easiest way to obtain copies of GAO documents at no cost is through our website. Each weekday afternoon, GAO posts on its website newly released reports, testimony, and correspondence. You can also subscribe to GAO’s email updates to receive notification of newly posted products.
Order by Phone
The price of each GAO publication reflects GAO’s actual cost of production and distribution and depends on the number of pages in the publication and whether the publication is printed in color or black and white. Pricing and ordering information is posted on GAO’s website, https://www.gao.gov/ordering.htm.
Place orders by calling (202) 512-6000, toll free (866) 801-7077,
or
TDD (202) 512-2537.
Orders may be paid for using American Express, Discover Card, MasterCard, Visa, check, or money order. Call for additional information.
Connect with GAO
Connect with GAO on Facebook, Flickr, X, and YouTube.
Subscribe to our RSS Feeds or Email Updates. Listen to our Podcasts.
Visit GAO on the web at https://www.gao.gov.
To Report Fraud, Waste, and Abuse in Federal Programs
Contact FraudNet:
Website: https://www.gao.gov/about/what-gao-does/fraudnet
Automated answering system: (800) 424-5454 or (202) 512-7700
Congressional Relations
A. Nicole Clowers, Managing Director, ClowersA@gao.gov, (202) 512-4400, U.S. Government Accountability Office, 441 G Street NW, Room 7125, Washington, DC 20548
Public Affairs
Sarah Kaczmarek, Managing Director, KaczmarekS@gao.gov, (202) 512-4800, U.S.
Government Accountability Office, 441 G Street NW, Room 7149
Washington, DC 20548
Strategic Planning and External Liaison
Stephen J. Sanford, Managing
Director, spel@gao.gov, (202) 512-4707
U.S. Government Accountability Office, 441 G Street NW, Room 7814, Washington,
DC 20548
[1]Federal Information Technology Acquisition Reform provisions of the Carl Levin and Howard P. “Buck” McKeon National Defense Authorization Act for Fiscal Year 2015, Pub. L. No. 113-291, div A, title VIII, subtitle D, 128 Stat. 3292, 3438-3450 (Dec. 19, 2014).
[2]GAO, High-Risk Series: An Update, GAO‑15‑290 (Washington, D.C.: Feb. 11, 2015). GAO’s high-risk program identifies government operations with vulnerabilities to fraud, waste, abuse, and mismanagement, or in need of transformation to address economy, efficiency, or effectiveness challenges. Every 2 years, we issue an update that describes the status of these high-risk areas and actions that are still needed to assure further progress and identifies new high-risk areas needing attention by Congress and the executive branch.
[3]The 24 federal agencies covered by the Chief Financial Officers Act of 1990 are the Departments of Agriculture, Commerce, Defense, Education, Energy, Health and Human Services, Homeland Security, Housing and Urban Development, the Interior, Justice, Labor, State, Transportation, the Treasury, and Veterans Affairs; Environmental Protection Agency; General Services Administration; National Aeronautics and Space Administration; National Science Foundation; Nuclear Regulatory Commission; Office of Personnel Management; Small Business Administration; Social Security Administration; and U.S. Agency for International Development.
[4]This report uses “annual IT portfolio review” to refer to any IT portfolio review, including those referred to as PortfolioStat sessions and uses “high-risk investment review” to refer to any review of high-risk investments, including those referred to as TechStat sessions. PortfolioStat and TechStat were terms in use by OMB to describe these sessions when FITARA was enacted. However, since FITARA does not use the terms PortfolioStat and TechStat and those terms are not used consistently throughout the government, we use different terms to describe these reviews. We only refer to “PortfolioStat” and “TechStat” when those are the specifically cited terms.
[5]OMB’s IT Dashboard is intended to provide transparency for IT investments to facilitate public monitoring of government operations and accountability for investment performance by the Federal CIO who oversees them. Among other things, it provides agency-reported cost savings by OMB initiative. The Department of Defense does not report these data on the IT Dashboard. See IT Dashboard, https://itdashboard.gov/cost-savings (accessed September 10, 2024).
[6]FITARA states that a “high risk rating” shall be categorized in accordance with guidance from OMB. 40 U.S.C § 11302(c)(4) and 11302(c)(3)(C). OMB’s FITARA implementation guidance, M-15-14, equates a high-risk rating with a rating that is red on the IT Dashboard. As a result, we identified those that received a “red” rating (i.e., a “1” or a “2”) on the dashboard for four consecutive quarters.
[7]Pub. L. No. 107-347, 116 Stat. 2899 (Dec. 17, 2002).
[8]OMB now refers to the Office of the Electronic Government as the Office of the Federal CIO.
[9]According to the IT Dashboard, each agency CIO is to rate investments based on their best judgment, using a set of pre-established criteria, including risk management, requirements management, contractor oversight, historical performance, human capital, and any other factors the CIO deems important to forecasting future success.
[10]The White House, 25 Point Implementation Plan to Reform Federal Information Technology Management (Washington, D.C.: Dec. 9, 2010) and Chief Information Officer Authorities M-11-29 (Washington, D.C.: Aug. 8, 2011). OMB’s M-11-29 was rescinded by M-17-26 on June 15, 2017.
[11]The White House, 25 Point Implementation Plan to Reform Federal Information Technology Management, (Washington, D.C.: Dec. 9, 2010).
[12]OMB, Implementing PortfolioStat, M-12-10 (Washington, D.C.: Mar. 30, 2012).
[13]Federal Information Technology Acquisition Reform provisions of the Carl Levin and Howard P. ‘Buck’ McKeon National Defense Authorization Act for Fiscal Year 2015, Pub. L. No. 113-291, div. A, title VIII, subtitle D, 128 Stat. 3292, 3438-3450 (Dec. 19, 2014).
[14]The covered executive branch agencies correspond to the 24 agencies covered by the Chief Financial Officers Act, with certain exceptions for the Department of Defense.
[15]OMB, Management and Oversight of Information Technology, M-15-14 (Washington, D.C.: June 10, 2015).
[16]Since FITARA does not use the terms PortfolioStat and TechStat and those terms are not used consistently throughout the government, we chose broad terms to describe these reviews. This report generally uses “annual IT portfolio review,” which is a broad term that includes PortfolioStat sessions, and “high-risk investment review,” which is a broad term that includes TechStat sessions. We only refer to “PortfolioStat” and “TechStat” when those are the specifically cited terms.
[17]GAO, Information Technology: OMB’s Dashboard Has Increased Transparency and Oversight, but Improvements Needed, GAO‑10‑701 (Washington, D.C.: July 16, 2010); Information Technology: OMB Has Made Improvements to Its Dashboard, but Further Work Is Needed by Agencies and OMB to Ensure Data Accuracy, GAO‑11‑262 (Washington, D.C.: Mar. 15, 2011); IT Dashboard: Accuracy Has Improved, and Additional Efforts Are Under Way to Better Inform Decision Making, GAO‑12‑210 (Washington, D.C.: Nov. 7, 2011); Information Technology Dashboard: Opportunities Exist to Improve Transparency and Oversight of Investment Risk at Select Agencies, GAO‑13‑98 (Washington, D.C.: Oct. 16, 2012); and IT Dashboard: Agencies Are Managing Investment Risk, but Related Ratings Need to Be More Accurate and Available, GAO‑14‑64 (Washington, D.C.: Dec. 12, 2013).
[18]GAO, Information Technology: OMB Needs to Improve Its Guidance on IT Investments, GAO‑11‑826 (Washington, D.C.: Sept. 29, 2011).
[19]GAO, Information Technology: Additional Executive Review Sessions Needed to Address Troubled Projects, GAO‑13‑524 (Washington, D.C.: June 13, 2013).
[20]GAO, Information Technology: Additional OMB and Agency Actions Are Needed to Achieve Portfolio Savings, GAO‑14‑65 (Washington, D.C.: Nov. 6, 2013).
[21]GAO, High-Risk Series: An Update, GAO‑15‑290 (Washington, D.C.: Feb. 11, 2015).
[22]GAO, High-Risk Series: Efforts Made to Achieve Progress Need to Be Maintained and Expanded to Fully Address All Areas, GAO‑23‑106203 (Washington, D.C.: Apr. 20, 2023).
[23]GAO, IT Dashboard: Agencies Need to Fully Consider Risks When Rating Their Major Investments, GAO‑16‑494 (Washington, D.C.: June 2, 2016).
[24]GAO, Information Technology: Opportunities for Improving Acquisitions and Operations, GAO‑17‑251SP (Washington, D.C.: Apr. 11, 2017).
[25]GAO, Federal Chief Information Officers: Critical Actions Needed to Address Shortcomings and Challenges in Implementing Responsibilities, GAO‑18‑93 (Washington, D.C.: Aug. 2, 2018).
[26]GAO, Chief Information Officers: Private Sector Practices Can Inform Government Roles, GAO‑22‑104603 (Washington, D.C.: Sept. 15, 2022).
[27]Sunset provisions relevant to FITARA’s sections on capital planning and investment control (40 U.S.C. § 11302) and resources, planning, and portfolio management (40 U.S.C. § 11319) were removed through amendments to FITARA in 2017.
[28]40 U.S.C § 11319(d).
[29]OMB, Management and Oversight of Information Technology, M-15-14 (Washington, D.C.: June 10, 2015).
[30]In preparation for the fiscal year 2018 IT budget, OMB provided updated Capital Planning Guidance that introduced Standard IT Investments—investments in IT infrastructure, security, and management, among others—as a type of IT investment. Likewise, for fiscal year 2020, OMB provided updated Capital Planning Guidance that introduced funding transfer investments—used to indicate the partner contribution to an investment in another agency’s portfolio.
[31]OMB, Preparation, Submission, and Execution of the Budget, Circular No. A-11, section 55, (Washington, D.C.: Aug. 11, 2023).
[32]According to OMB, desk officers provide oversight of an agency’s progress addressing statutory requirements and serve as liaisons between OMB staff and agency officials.
[33]FITARA uses the term “performance indicators” but we refer to them in this report as metrics for simplicity. 40 U.S.C. § 11319(d)(2).
[34]OMB, Preparation, Submission, and Execution of the Budget, Circular No. A-11 (Washington, D.C.: August 2023).
[35]The IDC process is intended to be a consolidated approach for agencies to comply with OMB’s reporting requirements. OMB provides IDC instructions quarterly to agencies dictating how to report required data to OMB.
[36]IT Dashboard, https://itdashboard.gov/faq (accessed February 21, 2024).
[37]According to 44 U.S.C. 3602(c), the Federal CIO (referred to as the Administrator of the Office of Electronic Government in the statute) shall assist the OMB Director in carrying out various functions that include the IT management provisions of Title 40, U.S. Code. These provisions have been amended to encompass relevant portions of FITARA.
[38]As previously stated, the PortfolioStat term is not used consistently throughout the government, nor does FITARA specifically use that term. As a result, we use a broader term, “annual IT portfolio reviews” here.
[39]The IDC is the OMB Office of the Federal CIO’s quarterly reporting mechanism to capture data and information related to PortfolioStat, Data Center Optimization Initiative, and other initiatives.
[40]OMB, Analytical Perspectives, Budget of the United States Government, Fiscal Year 2025 (Washington, D.C.: Mar. 11, 2024).
[41]40 U.S.C § 11302.
[42]40 U.S.C § 11319(d)(3). FITARA allows the Department of Defense to use an existing process to fulfill this requirement, in consultation with the Federal CIO. 40 U.S.C § 11319(d)(4).
[43]The 15 agencies are: the Departments of Agriculture, Commerce, Defense, Education, Energy, the Interior, Justice, Labor, Transportation, and Veterans Affairs; National Aeronautics and Space Administration; National Science Foundation; Nuclear Regulatory Commission; Small Business Administration; and Social Security Administration.
[44]40 U.S.C. § 11319(d)(5).
[45]FITARA allows the Department of Defense to use an existing process to fulfill the requirement, provided that the results of the review are provided to the Federal CIO upon request and to specified committees of Congress. 40 U.S.C § 11302(c)(4)(C).
[46]Using OMB’s FITARA implementation guidance, M-15-14, we interpreted “the extent to which these causes can be addressed” to be demonstrated by the agency identifying action items and due dates. Likewise, we interpreted “the probability of future successes” to be demonstrated by the agency identifying outcomes.
[47]Agencies reported holding various reviews of high-risk IT investments over the last 13 years. See appendix IV for details on the number of reviews and the date of the last review held by each agency.
[48]Some agencies reported multiple reasons for not holding high-risk investment reviews.
[49]TechStat Toolkit, https://www.cio.gov/assets/resources/TechstatToolkit.zip (accessed July 22, 2024).
[50]M-15-14.
[51]The 24 federal agencies covered by the Chief Financial Officers Act of 1990 are the Departments of Agriculture, Commerce, Defense, Education, Energy, Health and Human Services, Homeland Security, Housing and Urban Development, the Interior, Justice, Labor, State, Transportation, the Treasury, and Veterans Affairs; Environmental Protection Agency; General Services Administration; National Aeronautics and Space Administration; National Science Foundation; Nuclear Regulatory Commission; Office of Personnel Management; Small Business Administration; Social Security Administration; and U.S. Agency for International Development.
[52]Federal Information Technology Acquisition Reform provisions of the Carl Levin and Howard P. ‘Buck’ McKeon National Defense Authorization Act for Fiscal Year 2015, Pub. L. No. 113-291, div. A, title VIII, subtitle D, 128 Stat. 3292, 3438-3450 (Dec. 19, 2014).
[53]This report uses “annual IT portfolio review” to refer to any IT portfolio review, including those referred to as PortfolioStat sessions and “high-risk investment review” to refer to any review of high-risk investments, including those referred to as TechStat sessions. PortfolioStat and TechStat were terms in use by OMB to describe these sessions when FITARA was enacted. However, since FITARA does not use the terms PortfolioStat and TechStat and those terms are not used consistently throughout the government, we use different terms to describe these reviews. We only refer to “PortfolioStat” and “TechStat” when those are the specifically cited terms.
[54]The Department of Defense does not report these data on the IT Dashboard. IT Dashboard, https://itdashboard.gov/cost-savings (accessed March 10, 2024).
[55]40 U.S.C § 11319(d)(3).
[56]40 U.S.C. § 11302(c)(4)(A). Using OMB’s FITARA implementation guidance, M-15-14, we interpreted “the extent to which these causes can be addressed” to be demonstrated by the agency identifying action items and due dates. Likewise, we interpreted “the probability of future successes” to be demonstrated by the agency identifying outcomes.
[57]IT Dashboard, https://itdashboard.gov/data-feeds (accessed August 29, 2024).
[58]40 U.S.C. § 11302(c)(4) and 11302(c)(3)(C).
[59]Office of Management and Budget, Management and Oversight of Federal Information Technology, M-15-14 (Washington, D.C.: June 10, 2015).