NATIONAL NUCLEAR SECURITY ADMINISTRATION
Reporting on Industrial Base Risks Needs Improvement
Report to Congressional Committees
United States Government Accountability Office
View GAO‑25‑107215. For more information, contact Allison Bawden at (202) 512-3841 or bawdena@gao.gov.
Highlights of GAO‑25‑107215, a report to congressional committees
National Nuclear Security Administration
Reporting on Industrial Base Risks Needs Improvement
Why GAO Did This Study
NNSA relies on contractors to produce or procure thousands of parts and components for the nuclear weapons stockpile. These contractors operate the laboratories and production facilities comprising the NSE. However, NNSA faces risks to its NSE industrial base such as human capital gaps, eroding infrastructure, constrained markets and suppliers, and global events. The FY 2022 NDAA requires NNSA to report on NSE industrial base risks.
A Senate report accompanying a bill for the FY 2023 NDAA includes a provision for GAO to review NNSA’s plans for addressing NSE industrial base risks. This report (1) examines NNSA’s approach to managing risks to the NSE industrial base and (2) assesses the extent to which NNSA has identified NSE industrial base risks and communicated these risks to external stakeholders.
To do this work, GAO reviewed NNSA documentation and interviewed NNSA officials and selected contractor and working group representatives. GAO compared NNSA’s risk reporting to enterprise risk management good practices.
What GAO Recommends
GAO is making two recommendations to NNSA to provide complete and clear information about NSE industrial base risks and resource needs. NNSA agreed with GAO’s recommendations.
What GAO Found
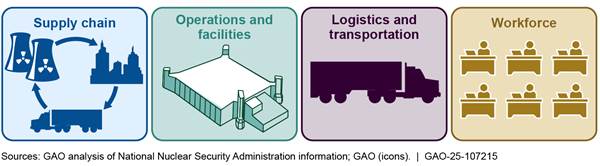
The National Nuclear Security Administration (NNSA) uses a coordinated but decentralized approach to manage risks to the nuclear security enterprise (NSE) industrial base. The NSE industrial base includes four elements—supply chain, operations and facilities, logistics and transportation, and workforce. The Office of Systems Engineering and Integration, within NNSA’s Office of Defense Programs, serves as the focal point for managing NSE industrial base risks at the enterprise level, including by attending working group meetings and participating in interagency processes. Contractors and working groups across the NSE are primarily responsible for managing industrial base risks. They use a variety of tools and processes that are often interlinked and cross-cutting. For example, some working groups use third-party software to identify, assess, and monitor risks.
NNSA has identified several key risks and taken steps to address some of them. For example, to address the insufficient supply of specialized equipment, NNSA established a working group that created two initiatives to expand capacity and increase supply. However, NNSA’s primary method of communicating NSE industrial base risks to external stakeholders—the annual Stockpile Stewardship and Management Plan—does not completely and clearly communicate risk priorities or resource needs. For example,
· The Fiscal Year (FY) 2022 National Defense Authorization Act (NDAA) requires NNSA to report on identified risks and how they are prioritized. However, GAO found that the plan discusses some key risks in limited detail and did not describe any as priorities.
· The FY 2022 NDAA also requires NNSA to report its resource needs to mitigate industrial base risks. NNSA officials said that additional resources or tools would be useful to address some risks. However, the plan did not identify such resources.
Complete and clear information about industrial base risks and resource needs would help inform stakeholders and decision-makers about the status of the NSE industrial base.
Abbreviations
|
DPA |
Defense Production Act |
|
DOD |
Department of Defense |
|
DOE |
Department of Energy |
|
ERM |
Enterprise Risk Management |
|
M&O |
management and operating |
|
NDAA |
National Defense Authorization Act |
|
NNSA |
National Nuclear Security Administration |
|
NSE |
nuclear security enterprise |
|
SSMP |
Stockpile Stewardship and Management Plan |
This is a work of the U.S. government and is not subject to copyright protection in the United States. The published product may be reproduced and distributed in its entirety without further permission from GAO. However, because this work may contain copyrighted images or other material, permission from the copyright holder may be necessary if you wish to reproduce this material separately.
March 14, 2025
Congressional Committees
The National Nuclear Security Administration (NNSA)—a separately organized agency within the Department of Energy (DOE)—is responsible for maintaining a safe, secure, and reliable nuclear weapons stockpile. To fulfill its mission, NNSA relies on management and operating (M&O) contractors to produce or procure thousands of parts and components for the stockpile.[1] These contractors operate the laboratories and production facilities comprising the nuclear security enterprise (NSE). NNSA is unique among federal agencies in that it is both a producer and consumer of manufactured goods. NNSA sources many of these goods from a broad industrial base.
NNSA defines the NSE industrial base as the global industrial capacity and capability that enables research and development, design, production, shipping, sustainment, and modernization of nuclear weapons components, subsystems, and materials to support the U.S. nuclear deterrent. NNSA faces internal and external risks to its industrial base that include human capital gaps, eroding infrastructure, constrained markets and suppliers, and global events.
NNSA has developed a framework for examining the NSE industrial base. This framework includes four interdependent, cross-cutting pillars—supply chain, operations and facilities, logistics and transportation, and workforce.
· NNSA’s supply chain includes procurement of raw materials, commercial off-the-shelf components, and specialized equipment, among other things.
· Operations and facilities include the infrastructure needed to process materials, manufacture and test components, and assemble and disassemble nuclear weapons.
· Logistics and transportation represent NNSA’s ability to handle, transport, and store a range of things, from completed weapons to strategic materials.
· NNSA’s workforce includes the recruitment and retention of personnel with specialized education, skill, training, and experience to work within the NSE.
The William M. (Mac) Thornberry National Defense Authorization Act for Fiscal Year 2021 (FY 2021 NDAA) required NNSA to designate a senior official to be responsible for monitoring the NSE industrial base, tracking issues over time, and identifying gaps or risks relating to the NSE industrial base. The provision also calls for the NNSA Administrator to brief the Senate and House Armed Services Committees annually through 2024 about monitoring gaps in and risks to the NSE industrial base.[2] The National Defense Authorization Act for Fiscal Year 2022 (FY 2022 NDAA) further requires NNSA to submit a report at the same time as each briefing. The report must include information on risks, actions NNSA is taking to address and prioritize these risks along with associated timelines and needed resources, and coordination with other federal agencies.[3]
A Senate report accompanying a bill for the James M. Inhofe National Defense Authorization Act for Fiscal Year 2023 (FY 2023 NDAA) includes a provision for us to review NNSA’s plans for addressing NSE industrial base risks.[4] This report (1) examines NNSA’s approach to managing risks to the NSE industrial base, and (2) assesses the extent to which NNSA has identified NSE industrial base risks and communicated these risks to external stakeholders.
To address our objectives, we reviewed relevant agency documents, including NNSA reports, briefings, and guidance. We also reviewed M&O contractor and working group documents, including risk management presentations and tools, and organization charters. We interviewed officials from NNSA headquarters responsible for managing risks to the NSE industrial base to identify how risks are managed and communicated. In addition, we selected and interviewed representatives from two M&O contractor sites with responsibility over the design and procurement of many of NNSA’s nonnuclear components. We also selected and interviewed NNSA officials and contractor representatives from seven working groups to describe their roles in managing NSE industrial base risks. Finally, we assessed NNSA’s reporting on NSE industrial base risks against statutory requirements and enterprise risk management practices to determine whether the agency effectively communicates its NSE industrial base risks. For additional information on our objectives, scope, and methodology, see appendix I.
We conducted this performance audit from January 2024 to March 2025 in accordance with generally accepted government auditing standards. These standards require that we plan and perform the audit to obtain sufficient, appropriate evidence to provide a reasonable basis for our findings and conclusions based on our audit objectives. We believe that the evidence obtained provides a reasonable basis for our findings and conclusions based on our audit objectives.
We are separately issuing a controlled unclassified information (CUI) annex to this report that provides additional details on specific NSE industrial base risks.[5] The annex will be available upon request to those with the appropriate and validated need to know.
Background
NNSA Organizational Structure for Industrial Base Management
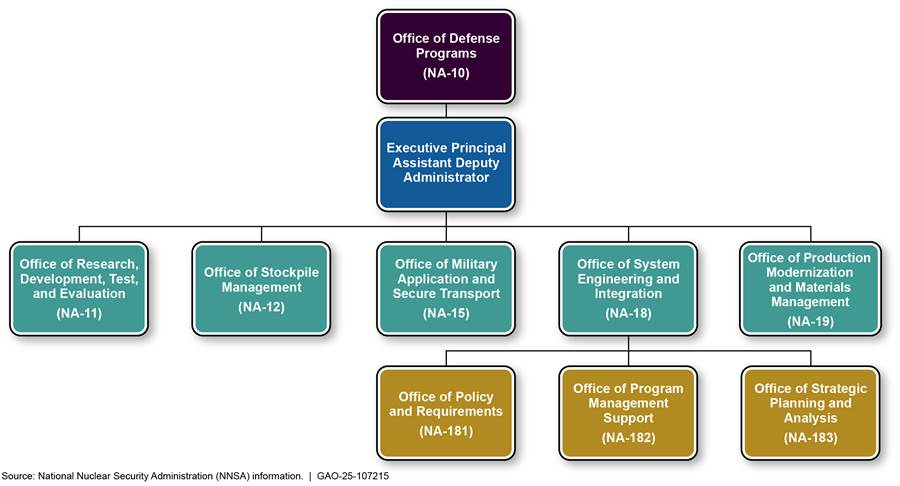
NNSA has designated the Executive Principal Assistant Deputy Administrator within the Office of Defense Programs as the senior official responsible for monitoring the NSE industrial base. In addition, within the Office of Defense Programs, the Office of Systems Engineering and Integration (NA-18) coordinates enterprise-wide industrial base risk management. Specifically, the Office of Strategic Planning and Analysis within NA-18 is responsible for functional tasks related to the NSE industrial base, including reporting and briefing on industrial base risk management. This office also issues the annual Stockpile Stewardship and Management Plan (SSMP) report to Congress, which is the main mechanism that NNSA uses to report on NSE industrial base risks as required by the FY 2022 NDAA. Figure 1 shows NNSA’s organization structure for managing the NSE industrial base.
Figure 1: NNSA’s Organizational Structure for Managing the Nuclear Security Enterprise Industrial Base
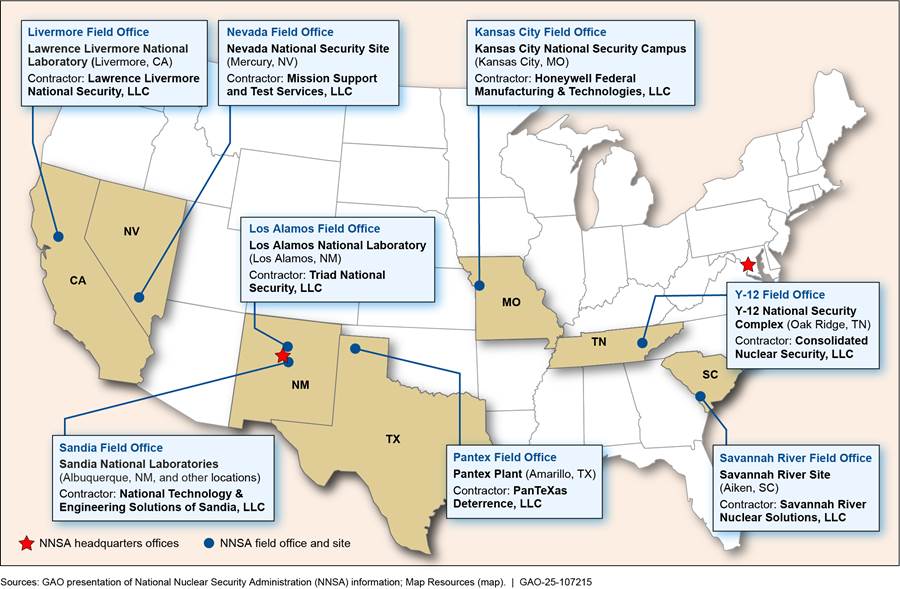
NA-18 relies on a network of at least 80 working groups, programs, and teams to help manage the NSE industrial base.[6] These working groups can be chartered by NNSA, M&O contractors, or other federal agencies to manage specific risks to the NSE industrial base.[7] Generally, working groups involve multiple NNSA sites or programs. M&O contractors are also responsible for industrial base risk management at their sites. See figure 2 for a map of NNSA’s sites and M&O contractors.
Enterprise Risk Management
Enterprise Risk Management (ERM) is a forward-looking management approach that allows agencies to assess threats and opportunities that could affect the achievement of their goals. DOE has established ERM guidance in response to the Office of Management and Budget Circular A-123.[8] DOE uses the Office of Management and Budget’s ERM model, which includes
1. understanding internal and external environments of the organization,
2. initial risk identification,
3. analyzing and evaluating the risks,
4. developing alternative risk responses,
5. responding to risks,
6. monitoring risk response, and
7. conducting continuous risk identification.
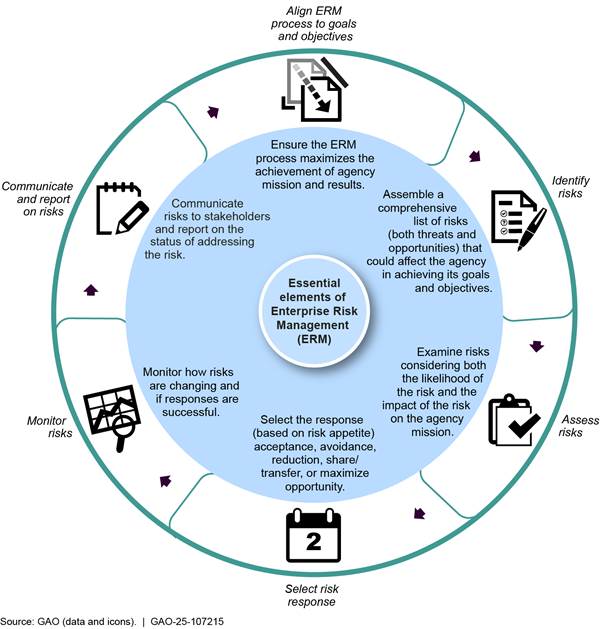
Similarly, we have previously identified a framework of six essential elements to help federal agencies implement ERM, and associated good practices that illustrate these elements.[9] The elements are
1. aligning processes to goals and objectives,
2. identifying risks,
3. assessing risks,
4. selecting risk responses,
5. monitoring risks, and
6. communicating and reporting on risks.
Throughout this report, we refer to GAO’s six elements as risk management. Figure 3 shows how these essential elements fit together to form a continuous process for managing enterprise risks. While there is no one right way to implement the ERM framework, agencies should include these essential elements in their ERM program.
GAO’s Prior Work on Issues Related to Industrial Base Risks
This report generally focuses on NNSA’s enterprise-wide effort to manage industrial base risks. However, for more than a decade, we have reported on many of the specific industrial base risks that NNSA faces in the context of individual programs or projects. These reports include risks such as sourcing materials and components that are difficult to obtain or from foreign suppliers and are necessary for NNSA’s weapons modernization programs, infrastructure and facility improvement, and workforce challenges. Some of these risks are ongoing, including sourcing electronic parts that can properly function in weapons environments, as we will discuss later in this report.[10]
In 2019, we reported on challenges related to the production of nonnuclear parts at NNSA’s Kansas City National Security Campus.[11] More recently, we reported on the effects of industrial base risks on the manufacturing of high explosives needed for NNSA’s ongoing weapons modernization programs.[12] In addition, we have conducted work addressing the following industrial base risk challenges:
· The domestic supply of uranium and uranium needed to produce tritium used in nuclear weapons
· Infrastructure needs across the enterprise
· Recruitment and retention of a qualified workforce
· The nuclear supply chain using the Enhanced Procurement Authority, which allows NNSA to exclude certain suppliers that may present a significant supply chain risk
· Risk management across the nuclear enterprise[13]
In addition, we have previously reported on the Department of Defense’s (DOD) industrial base risk efforts. Specifically, we identified three DOD investment programs that can be used to help sustain or expand manufacturing and industrial base capabilities.[14] In addition, we reported that DOD’s Office for Industrial Base Policy conducts DOD-wide industrial base risk assessments, coordinates certain industrial base investments, and reports annually on assessments of the defense industrial base and associated risks and mitigation efforts. We recommended that this office develop and use performance measures as well as improve data collection to better manage the defense industrial base.[15] DOD has implemented our recommendations to improve data collection but has not developed industrial base management performance measures.
NNSA and Its Contractors Use a Variety of Processes to Manage Industrial Base Risks
NNSA uses a coordinated but decentralized approach to manage risks to the NSE industrial base. Under this approach, working groups across the NSE and M&O contractors are primarily responsible for identifying, assessing, monitoring, and responding to NSE industrial base risks.[16] NNSA is responsible for facilitating M&O contractors’ and work groups’ efforts and for overseeing and coordinating management of industrial base risk at the enterprise level. According to NNSA officials, this approach—as depicted in figure 4—provides more flexibility, specificity, and responsiveness to emerging and persisting risks.
Figure 4: NNSA’s Enterprise Risk Management (ERM) for the Nuclear Security Enterprise Industrial Base

Working Groups Use a Variety of Tools and Processes to Manage Industrial Base Risks
According to NNSA officials, working groups are one of the primary ways the agency manages risks to the industrial base. Working groups are inherently cross-site and can include representation from M&O contractors, NNSA headquarters, and other agencies such as DOD. NNSA or its M&O contactors can stand up a working group when they identify a category of risk that needs attention. NNSA officials identified at least 80 working groups that address industrial base risks. For example:
· M&O contractors established the Production Integration Collaboration Working Group in 2020 to address production integration risks across the NSE. This working group has several sub-working groups that focus on specific risks, such as the commercial supply chain.
· NNSA and its M&O contractors established the Electronic Parts Program in 2020 to address long-term and ongoing risks that could cause disruption to the supply chains for nonnuclear electronic components.
NNSA’s working groups and M&O contractors we spoke to as part of our review use a variety of tools and processes to identify, assess, respond to, and monitor NSE industrial base risks. These working groups and M&O contractors often use the same tools and processes to identify risks as they use to assess and monitor risks. These tools and processes can also be used to help inform an appropriate risk response. NNSA officials we met with confirmed that these tools and processes are broadly used to manage NSE industrial base risks. Specifically:
Risk identification. Working groups and M&O contractors, including those we spoke with, use several tools and processes to identify risks. For example, NNSA officials told us that they provide M&O contractors with access to third-party software to identify, assess, and monitor risks.[17] This software is used across the entire NSE to help manage risks to the industrial base supply chain. The software tool helps working groups and M&O contractors identify risks and anticipate potential disruptions. Working groups and M&O contractors use this tool to perform routine checks on existing suppliers. According to contactor representatives, the software has been a “huge benefit,” allowing the NSE to be more proactive about risk identification.
Two of the seven working groups we spoke with also use their own risk identification tools to target specific risks in their areas of concern. For example, representatives from one working group told us they maintain a registry focused on material risks. This list uses information from both U.S. government and private industry databases. The working group then enters the registry into third-party software, which enables the group to identify risks to its supply chain. The working group reports information about these material risks to NNSA and the M&O contractors on a quarterly basis, according to contractor representatives.
In addition, working groups and M&O contractors support the interagency body that reviews certain foreign investments in the U.S. to identify risks to national security, known as the Committee on Foreign Investment in the United States. At NA-18’s request, working groups and contractor representatives assess the impact on the NSE of potential foreign acquisitions of U.S. companies, according to working group and contractor representatives we spoke with. These impact assessments may help the Committee on Foreign Investments in the United States identify risks to national security and to enter into legal agreements with the companies involved to mitigate such risks.
Separately from working groups, M&O contractor representatives we spoke with said they also identify NSE industrial base risks. Specifically, one M&O contractor focused on addressing distressed suppliers in its supply chain—suppliers that cannot meet the contractor’s production demands. M&O contractors can also embed risk analysts in programs. These analysts work with programs to identify risks and whether other programs share these risks, enabling the M&O contractor to systematically respond to certain risks.
Risk assessment. Five of the nine working groups and M&O contractors we spoke to as part of our review use many of the same tools to assess risks as they do to identify them. For example, according to working group representatives, working groups can use functions within risk management software to track changes in the market availability of the materials that the NSE uses. In one case, if the software identifies a chemical as being subject to a regulation that might affect its availability, the working group can use the software to identify which materials used by the NSE include that chemical in their supply chains.
Working groups also track risks over time and identify trends. According to representatives from one working group, they do this quarterly to assess the impact of risks over time. This enables them to identify if a risk is transient or long term. If a risk continues to appear, the group can assess it as a long-term risk that M&O contractors or their suppliers need to address.
According to representatives from one working group, they also use risk modeling to forecast potential risks. These representatives said that they use risk modeling to analyze material inventories and equipment capacities for current and future programs. These models can also be used to quantify the impacts of realized risks, including when a mission demand cannot be achieved. The goal, according to these working group representatives, is to inform investments that are needed to ensure the NSE can achieve mission requirements over the long term.
M&O contractors develop risk matrixes to identify, assess, and communicate the likelihood that a risk may have an impact on the NSE. According to contractor documentation, these risk matrices rely on a common set of risk “lenses” that NNSA developed.[18] The matrixes produce an aggregate score of the severity of impact and likelihood of occurrence, which helps M&O contractors identify risk areas on which they need to focus. This in turn informs actions that NNSA or the contractors could take. In addition, contractors regularly update this score as conditions change.
Risk response. According to NNSA’s internal risk management guidance, risks can be mitigated, avoided, transferred, escalated, or accepted.[19] M&O contractors are the first to respond to industrial base risks.
· First, M&O contractors can mitigate a risk by taking action to limit the impact of a risk. For example, according to contractor representatives, they can adjust procurement schedules to meet suppliers’ capacity or help suppliers expand their capabilities.
· Second, M&O contractors can avoid a risk. For example, representatives from one contractor said they prefer to work with low-risk suppliers. If they assess the risk of a supplier and determine that the supplier is excessively risky, they may opt to find a different supplier.
· Third, M&O contractors can transfer a risk. Transferring risk can take place when M&O contractors or NNSA shift a risk to another entity. For example, NNSA relies on the Office of Management and Budget’s Made in America Office to make waiver determinations under Made in America laws.[20] However, many of NNSA’s risks are not transferable.
· Fourth, M&O contractors can elevate a risk. For example, a contractor may determine that a risk is shared across multiple NSE sites. This risk may be elevated to NA-18 so that it can be addressed at an enterprise-wide level.
· Lastly, M&O contractors can accept a risk. For instance, if a component is produced by only one producer or if it is only available in small amounts, an M&O contractor (in consultation with NNSA) may decide to accept the risk if the component is mission critical.
Risk monitoring. M&O contractors and the working groups in our review monitor industrial base risks using many of the same tools they use to identify and assess risks. For instance, according to working group and contractor representatives, software for industrial base monitoring enables them to monitor changes in the supply chain over time. According to contractor representatives, much of this monitoring takes place concurrently with identification and assessment but differs in that it is an ongoing and iterative process.
In addition, one of the M&O contractors we spoke to said they can monitor identified risks by communicating with suppliers. For example, representatives from one M&O contractor told us they monitor supplier health using a system of score cards. The M&O contractor shares these scores with suppliers and identifies weaknesses the suppliers need to address. The contractor continues to monitor the suppliers’ progress in addressing these risks. Table 1 summarizes examples of tools and processes that NNSA and its M&O contractors told us they use or rely on to carry out activities to manage industrial base risk.
Table 1: Examples of Tools and Processes Used to Manage Nuclear Security Enterprise (NSE) Industrial Base Risks
|
Tool and processes |
Identification |
Assessment |
Response |
Monitoring |
|
Third-party software |
● |
● |
|
● |
|
Information sharing across the NSE |
● |
|
● |
● |
|
Risk modeling |
● |
● |
|
● |
|
Committee on Foreign Investment in the United States process |
● |
● |
● |
● |
|
Embedded risk analysts |
● |
● |
● |
● |
|
Distressed vendor analysis |
● |
● |
● |
● |
|
Trend reporting |
|
● |
|
● |
|
Common risk lenses |
● |
● |
|
● |
|
Internal risk assessment |
|
● |
● |
● |
Source: GAO analysis of National Nuclear Security Administration (NNSA) information. | GAO‑25‑107215
Note: We identified these tools and processes through interviews with members of seven of the approximately 80 working groups responsible for managing specific risks to the industrial base. We also met with representatives from two management and operating contractors with responsibility over the design and procurement of many of NNSA’s nonnuclear components. NNSA officials confirmed that our assessment was accurate describing the use of these tools and processes more broadly for its overall efforts to manage industrial base risk.
NNSA Oversees and Coordinates Industrial Base Risk Management at the Enterprise Level
NNSA oversees NSE industrial base risk management at an enterprise-level. The NA-18 office serves as the focal point for managing these risks. According to NA-18 officials, they regularly attend working group meetings, which allows the working groups to share information across the NSE and provides an enterprise-wide perspective. NA-18 can also establish working groups to address identified enterprise-wide risks, such as the Transportation and Shipping Integrated Project Team. This team was established to manage risks associated with implementing new shipping capabilities. NA-18 also spearheads certain interagency processes. For example, NNSA officials said that NA-18 leads collaboration efforts with other federal entities, such as DOD and the Committee on Foreign Investments in the United States. NA-18 also facilitates interagency comments related to proposed regulations that could affect supply chains.
NA-18 officials said that NNSA does not independently rank or prioritize NSE industrial base risks at the enterprise level.[21] To understand whether a risk is significant or will affect the NSE broadly, NNSA officials said they rely on M&O contractors’ risk assessments. NNSA officials expressed confidence in these risk assessments and the subject matter expertise of M&O contractors. However, they said that they are developing a prioritization system to take a more quantitative approach to ranking risks at the enterprise level. In the meantime, officials described using qualitative criteria to inform discussions about key risks, including the breadth of the impact, the depth of the impact, and the time until the impact (see table 2). As of August 2024, these criteria were being incorporated into new standard operating procedures for NSE industrial base monitoring, according to NNSA officials.
Table 2: Qualitative Criteria NNSA Uses to Characterize Risks to the Nuclear Security Enterprise (NSE)
|
Criteria |
Description |
|
Impact breadth |
The number of organizations that will be directly impacted by an industrial base issue. Intended to be a measure of how many organizations may be affected by an issue, but also serves to understand who needs to be informed. |
|
Impact depth |
The degree of disruption expected if the issue is actualized, or the degree of disruption that is currently being experienced because of the issue. |
|
Time to impact |
The amount of time until the issue causes disruptions to the NSE industrial base. |
|
Existing mitigations |
The degree to which an issue is already being addressed by another entity or organization. Must include a description of the measures being taken. |
|
Probability |
The likelihood of the event occurring. |
|
Leadership priority |
Whether the issue was explicitly stated as a concern by NNSA leadership, via direct guidance by NNSA leadership or in key strategic priority documents. |
Source: National Nuclear Security Administration (NNSA). | GAO‑25‑107215
NNSA Does Not Effectively Communicate Key Industrial Base Risks or Associated Resource Needs to Mitigate Them
NNSA has identified several key risks to the NSE industrial base, including the availability of certain equipment and materials, regulatory changes, and reliance on foreign sources of critical minerals and materials. NNSA and its M&O contractors have taken some steps to address industrial base risks. However, the SSMP, which is the agency’s primary method of communicating industrial base risks to Congress, is deficient in two main areas based on risk management guidance and statutory industrial base reporting requirements. First, it does not effectively identify key NSE industrial base risks or describe how NNSA prioritizes such risks. Second, it does not describe the resources that NNSA needs to address industrial base risks.
NNSA Does Not Communicate Complete and Clear Information about Industrial Base Risk Priorities to Congress
According to NNSA officials we interviewed, NNSA currently faces several key risks to the NSE industrial base. While new risks regularly emerge, as of August 2024, these included risks related to the availability of certain equipment and materials, regulatory changes, and reliance on foreign sources of critical minerals and materials.[22]
NNSA officials said that they use the SSMP and congressional briefings to communicate NSE industrial base risks to Congress, including to meet the industrial base reporting requirement established by the FY 2021 and FY 2022 NDAAs.[23] NNSA has included a section on the NSE industrial base in the SSMP since its FY 2023 report. While NNSA is not required to report publicly on the NSE industrial base, the SSMP is a public document. NNSA also provided annual briefings to Congress from 2021 to 2024. According to officials, these briefings focused on key issues related to the NSE industrial base rather than covering the entire NSE industrial base. NNSA also briefs Congress on an as-needed basis, such as to provide updates on evolving risks. While NNSA was only required to report on the NSE industrial base through 2024, officials said that they plan to continue using the SSMP to report on risks to the industrial base and offering annual briefings to Congress.
|
Department of Defense (DOD) Industrial Base Reporting DOD issues stand-alone defense industrial base reports in response to a statutory requirement. Past reports have provided assessments of industrial base gaps, vulnerabilities, and developments, as well as a priority list of defense sectors and recommended actions and investments to address specific risks. In 2023, DOD also released a National Defense Industrial Strategy, which outlines DOD’s industrial base priorities, including resilient supply chains and workforce readiness. Source: GAO analysis of DOD information. | GAO‑25‑107215 |
The need for NNSA to communicate complete information—including information about identified risks and how they are prioritized—to stakeholders is reflected in several sources of requirements and guidance. Specifically:
· Statutory reporting requirements. According to the FY 2022 NDAA, NNSA’s report on the NSE industrial base should, among other things, identify risks and describe how NNSA prioritizes risks.[24]
· DOE guidance on information quality. DOE’s guidance on information quality states that information disseminated to the public by DOE elements—including NNSA—should meet a basic level of quality.[25] For example, one measure of quality is the usefulness of the information.
· ERM framework. DOE’s ERM guidance does not include a communication or reporting requirement. However, an essential element of GAO’s ERM framework includes communicating and reporting on risks. According to GAO’s ERM framework, agencies should communicate identified risks with stakeholders and report on the status of addressing risks.[26] Effective reporting and communication are vital for an agency to achieve its objectives.
However, we found that NNSA’s communication with Congress and the public via the SSMP is not complete because it does not fully identify key NSE industrial base risks nor describe how NNSA prioritizes risks, as required. Specifically, we conducted an in-depth review of the FY 2024 and FY 2025 SSMPs.[27] We found that both documents contain examples of industrial base risks within a short appendix, including managing glovebox fabrication and deliveries; managing material obsolescence and vendor risks; issues stemming from outdated and aging infrastructure; and the need to hire, train, qualify, and retain personnel for a specific production effort. However, the documents present these risks as examples and do not identify any as priority risks. Further, the FY 2024 and FY 2025 SSMPs do not describe the process NNSA uses to prioritize industrial base risks.
We also found that the FY 2024 and FY 2025 SSMPs do not fully identify key risks to the NSE industrial base. The FY 2024 SSMP identifies four of eight risks that NNSA officials described to us as priorities.[28] The FY 2025 SSMP identifies seven of the eight priority risks. However, the report discusses some of the risks in limited detail, and none are described as priorities. Further, the FY 2025 SSMP includes mitigation strategies for three of the seven risks it identifies.
The SSMP does not clearly communicate key risks to the NSE industrial base in part because it is not well organized for summarizing this information and identifying priorities. For example:
· NNSA uses the SSMP to respond to at least 10 statutory requirements and congressional requests. As a result, the SSMP contains a wide range of information.
· Both the FY 2024 and FY 2025 SSMPs include an appendix specifically focused on the NSE industrial base. However, this appendix is less than four pages in length and states that information about NSE industrial base risks is spread across the full report. Both the FY 2024 and FY 2025 SSMPs are over 200 pages in length, which makes it challenging for readers, including congressional stakeholders, to identify what information is related to the NSE industrial base, as well as what NNSA’s industrial base priorities are.
NNSA officials said that reporting on the NSE industrial base in the SSMP will continue to evolve as the agency identifies strategic risks. However, they said that they do not anticipate issuing a stand-alone industrial base report in the future because they view it as important to report all risks—not just industrial base risks—together in a single document.
DOE’s guidance on information quality states that information disseminated to the public should meet a basic level of quality, measured in part by the usefulness of the information to intended users. In addition, according to GAO’s ERM framework, clear communication assures stakeholders, including Congress, that agency leaders are effectively managing risk. By improving its communication about risks to the NSE industrial base—particularly about priority risks—in the SSMP or another reporting tool, NNSA could provide clearer information that is more useful to stakeholders. This information could better assure them that NNSA is effectively managing risks to the NSE industrial base. By mandating, in law, reports on risks to the industrial base, Congress has indicated it wants this information.
If NNSA has concerns about including information about specific NSE industrial base risks, risk priorities, or mitigation strategies in the public SSMP, GAO’s ERM framework states that agencies can establish safeguards, such as communicating risk information only to appropriate parties. For example, the public version of the SSMP is accompanied by a classified annex available to appropriately cleared individuals with need to know, including members of Congress.[29]
NNSA Does Not Describe Industrial Base Resource Needs in Its Report to Congress
According to NNSA officials we interviewed, NNSA and its M&O contractors have taken some steps to address key risks to the NSE industrial base.[30] For example, NNSA established a working group, which includes representatives from NNSA headquarters and M&O contractors, to oversee an NNSA-wide strategy to ensure a sufficient supply of certain equipment. The agency also established initiatives to increase the number and capacity of suppliers of the equipment. In addition, related to the supply of materials affected by supplier manufacturing decisions, M&O contractors completed bulk buys of some materials and identified potential new vendors of these materials in the short term. In the long term, M&O contractors are working to identify, develop, and qualify alternatives for affected materials.
According to the FY 2022 NDAA, NNSA’s reports on the NSE industrial base should include the resources needed to address industrial base risks. Additionally, according to DOE’s ERM guidance, agencies should take an enterprise-wide approach to risk management, which includes developing alternative risk responses and responding to risks by deciding on the best course of action. By following this approach, agencies can determine if additional resources are needed to mitigate a risk.
However, in reviewing the FY 2024 and FY 2025 SSMPs, we found that the documents did not describe the resources NNSA needs to address NSE industrial base risks Specifically, we found that the FY 2024 and FY 2025 SSMPs provided information about the resources needed to address some, but not all, of the examples of industrial base risks described in the industrial base appendix. NNSA officials told us that they do not view the SSMP as a place to outline the need for additional tools or resources—such as those used by DOD.
Nonetheless, NNSA officials told us that additional resources or tools would be useful to address enterprise risks to the NSE industrial base. However, NNSA faces challenges leveraging or cannot leverage some of these resources. For example:
· Access to Defense Production Act funding. While NNSA is able to access and use certain funding under the Defense Production Act of 1950 (DPA) to address risks to the NSE industrial base, officials said that administrative barriers prevent it from fully leveraging these authorities. The DPA gives the President a broad set of authorities to influence domestic industry in the interest of national defense.[31] NNSA officials said that they view both DPA Title I and Title III authorities as tools to address risks to the NSE industrial base.[32] NNSA officials said Title I authorities have been a helpful tool to support the industrial base. In FY 2023, NNSA used these authorities to prioritize over 100,000 purchase orders valued at over $4 billion. Officials noted that these authorities are used only when necessary and appropriate; they are not applied to all purchase orders. However, officials said that the agency currently does not have DPA Title III funding and that it is challenging and administratively burdensome to obtain this funding.[33] One official said that NNSA has requested Title III funds through DOE, but that DOE does not have established processes to request Title III funds.
· Access to dedicated industrial base funding. NNSA does not have investment programs that enable it to leverage dedicated funding to mitigate risks to the industrial base. DOD has two such programs focused on mitigating risks to the industrial base. The Industrial Base Analysis and Sustainment program seeks to maintain or improve the health of essential parts of the defense industry by investing in critical capabilities, including preserving critical manufacturing skills and supporting and expanding reliable sources.[34] The Manufacturing Technology program seeks to anticipate and respond to capability gaps by investing in the development of advanced manufacturing processes, techniques, and equipment to develop, produce, and sustain weapon systems.[35] However, NNSA officials told us NNSA does not have comparable programs.
According to NNSA officials, a separate industrial base fund or an NNSA-specific funding line through DPA Title III could be helpful if the fund represents new funding rather than shifting it from other NNSA programs. A contractor representative said that this type of program-agnostic fund could be used to address risks that occur throughout program lifecycles and ideally should be an emergency fund that NNSA can quickly access. Such a fund could also help NNSA build the NSE industrial base. For example, it could be used to invest in a company that wants to make needed equipment that is deemed a risk but that does not have the necessary capability.
In the absence of dedicated industrial base funding, NNSA can address NSE industrial base risks by reprogramming funding from existing activities. As an example, NNSA officials said that the agency requested DPA Title III funds to address the insufficient supply of a critical type of needed equipment but was unable to access funding under this authority. Instead, agency officials told us they reprogrammed funds from existing programs or projects to offer grants under two initiatives aimed at expanding domestic fabrication capacity for this equipment.[36]
However, reprogramming funds also poses challenges. According to a senior NNSA official, NNSA has limited flexibility to reprogram funds to address industrial base risks. Specifically, NNSA can only reprogram the lesser of $5 million or 10 percent of any program, project, or activity within an appropriation without specific congressional notification and a 30-day waiting period, which can cause delays.[37] According to the senior official, this requires a significant investment of time and effort and places an administrative burden on the agency. To reprogram funds to support two initiatives, officials said it took several months to identify funds that could be reprogrammed. Finally, they had to inform Congress about their intention to reprogram the funds. A senior official said that if a separate NNSA industrial base fund is not possible, additional flexibility to reprogram funds to address NSE industrial base risks would be a helpful tool. This would require legislative change, but the agency has not pursued a legislative proposal on this topic with Congress to date.
According to NNSA officials, they have not used the SSMP to identify additional tools or resources to address enterprise industrial base risks because they see it as a mechanism to update Congress rather than to identify a need for funding. However, they said that they are open to looking into using the report to identify additional industrial base resources, such as a separate funding line to address enterprise-wide risks. Additionally, officials said that they had internal discussions in the past about an NNSA-specific funding line through DPA Title III, as well as discussions with congressional stakeholders. However, these discussions did not result in a formal request to Congress for an NNSA-specific funding line.
According to the FY 2022 NDAA, NNSA’s report on risks to the NSE industrial base should include the resources needed to address industrial base risks. By communicating, in the SSMP or another reporting tool, whether NNSA has the necessary resources to address NSE industrial base risks, NNSA could better inform Congress about what it needs to address these risks. Obtaining such NNSA-specific resources and tools could reduce administrative burden and help NNSA more effectively manage industrial base risks.
Conclusions
NNSA faces risks to its industrial base that include human capital gaps, eroding infrastructure, constrained markets and suppliers, and global events. NNSA has reported on these risks since 2023, including risks to supply chains, operations and facilities, logistics and transportation, and workforce. However, we found that these reports do not contain complete information about key industrial base risks, risk priorities, and the resources needed to address risks, as required by statute. Effective enterprise risk management requires NNSA to effectively communicate useful information about the NSE industrial base. This information should include clearly identifying risks and the resources needed to address risks in its industrial base reports or legislative proposals. By ensuring that industrial base reporting includes complete and clear information on key risks and resource needs, NNSA can better inform stakeholders about the NSE industrial base and assure them that the agency is effectively managing risks.
Recommendations for Executive Action
We are making the following two recommendations to NNSA:
The NNSA Administrator should ensure that the agency’s reporting on risks to the NSE industrial base includes complete and clear information on key industrial base risks. (Recommendation 1)
The NNSA Administrator should ensure that the agency’s reporting on risks to the NSE industrial base includes an assessment of whether additional resources, tools, or legislative proposals are needed to address these risks. (Recommendation 2)
Agency Comments and Our Evaluation
We provided a draft of this report to NNSA for review and comment. In its written comments, reproduced in appendix II, NNSA concurred in principle with our first recommendation and concurred with our second recommendation. NNSA also provided technical comments, which we incorporated as appropriate.
Regarding our first recommendation, NNSA stated that it plans to describe the actions being taken to prioritize NSE industrial base risks in the FY 2026 SSMP classified appendix to enhance the clarity and completeness of reporting and more fully meet the FY 2022 NDAA requirements. However, NNSA also stated that the FY 2022 NDAA does not require a specific prioritization or reporting of risks as “key” but instead requires a description of actions taken to prioritize those risks included in the report.
The FY 2022 NDAA requires NNSA to describe the actions it takes to assess, characterize, and prioritize risks. We interpret this direction to include a description of how NNSA prioritizes risk. In addition, the FY 2022 NDAA does not specifically require the reporting of “key” risks but requires the identification of risks generally, which would include key risks. As we state in our report, NNSA officials identified certain risks as “key” in interviews with us, but we found that NNSA’s reporting did not include all those risks. As a result, we continue to believe that the agency’s reporting on risks to the NSE industrial base should include complete and clear information on key industrial base risks.
We are sending copies of this report to the appropriate congressional committees, the Administrator of NNSA, and other interested parties. In addition, this report is available at no charge on the GAO website at http://www.gao.gov.
If you or your staff have any questions about this report, please contact me at (202) 512-3841 or bawdena@gao.gov. Contact points for our Offices of Congressional Relations and Public Affairs may be found on the last page of this report. GAO staff who made significant contributions to this report are listed in appendix III.

Allison Bawden
Director, Natural Resources and Environment
List of Committees
The Honorable Roger F. Wicker
Chairman
The Honorable Jack Reed
Ranking Member
Committee on Armed Services
United States Senate
The Honorable John Kennedy
Chair
The Honorable Patty Murray
Ranking Member
Subcommittee on Energy and Water Development
Committee on Appropriations
United States Senate
The Honorable Mike Rogers
Chairman
The Honorable Adam Smith
Ranking Member
Committee on Armed Services
House of Representatives
The Honorable Chuck Fleischmann
Chairman
The Honorable Marcy Kaptur
Ranking Member
Subcommittee on Energy and Water Development, and Related Agencies
Committee on Appropriations
House of Representatives
This report (1) examines the National Nuclear Security Administration’s (NNSA) approach to managing risks to the nuclear security enterprise (NSE) industrial base, and (2) assesses the extent to which NNSA has identified NSE industrial base risks and communicated these risks to external stakeholders.
For our first objective, we selected a nongeneralizable sample of seven organizations from a population of more than 80 working groups, programs, and teams that help manage the NSE industrial base.[38] To select the working groups for our review, we determined whether they: represented at least one of NNSA’s industrial base pillars; were present in congressional briefings; were discussed by agency officials; and were present in an NNSA-provided list of working groups. Specifically, we identified at least one working group from each of NNSA’s four industrial base pillars—supply chain, facilities and operations, logistics and transportation, and workforce. We then reviewed agency documentation to identify working groups that addressed key risks that NNSA officials identified.
We conducted semi-structured interviews with representatives from the seven working groups to identify their roles in managing the NSE industrial base. Specifically, we discussed the tools and processes these working groups use to identify, assess, respond to, and monitor industrial base risks. In addition, we interviewed representatives from two selected NNSA management and operating (M&O) contractor sites—Sandia National Laboratories and Kansas City National Security Campus—to discuss their roles in industrial base risk management. These sites were selected based on their roles in designing and procuring many of the nonnuclear components used across the NSE. The views of these M&O contractor representatives are not generalizable, but NNSA officials confirmed their views are broadly representative of industrial base risk management in the NSE. Finally, we interviewed NNSA officials to identify the approach the agency takes to manage industrial base risk. Specifically, we discussed how NNSA coordinates industrial base risk management across the NSE through the working groups and M&O contractors.
In addition, to examine NNSA’s approach to managing risks to the industrial base, we reviewed working group charters for the working groups we selected. Specifically, we reviewed charter documentation to determine which NNSA organizations participated in each working group, the topic areas they cover, and which organization chartered the group. We also reviewed contractors’ risk management presentations and tools documentation. In addition, we reviewed NNSA documentation to understand the organizational structure NNSA has in place to manage the NSE industrial base. Specifically, we reviewed the annual Stockpile Stewardship and Management Plan (SSMP) for fiscal years (FY) 2024 and 2025 to define the NSE industrial base. We also reviewed NNSA briefings and presentations to understand NNSA’s approach to industrial base risk management. Finally, we applied GAO’s Enterprise Risk Management framework of essential elements of risk management to NNSA’s approach.
For our second objective, we reviewed the FY 2021 and FY 2022 National Defense Authorization Acts (NDAA) to identify NNSA’s industrial base reporting requirements. We then undertook a multistep analysis to determine the key risks that the NSE industrial base is currently facing and the extent to which these risks are communicated to stakeholders, including Congress, via the FY 2024 and 2025 SSMPs and annual congressional briefings. We identified eight key risks to the NSE industrial base, based on information NNSA officials provided to us. We then developed a list of search terms associated with each key risk. Next, we searched the FY 2024 and 2025 SSMPs and the 2021 through 2024 congressional briefings for these keywords to identify whether the risk was mentioned in each document. Finally, if the risk was mentioned in the SSMP or in a briefing, we analyzed the extent to which it was discussed, including whether it was identified and characterized, whether it was described as a priority, and the actions being taken to mitigate the risk.
We further reviewed the FY 2024 and 2025 SSMPs to determine whether NNSA identified resources needed to address NSE industrial base risks. In addition to the statutory requirements, we assessed whether NNSA reporting adhered to the Department of Energy’s Enterprise Risk Guidance and met good practices identified in GAO’s Enterprise Risk Management framework to determine whether the agency effectively communicated its NSE industrial base risks and resource needs.
We also interviewed NNSA officials to gain their perspective on the agency’s reporting on NSE industrial base risks and resources needs. Specifically, we discussed the agency’s priority risks and how industrial base risks are communicated to stakeholders. We also discussed whether alternative reporting mechanisms were necessary. In addition, we met with NNSA officials to determine whether additional resources would be helpful in addressing NSE industrial base risks.
We conducted this performance audit from January 2024 to March 2025 in accordance with generally accepted government auditing standards. These standards require that we plan and perform the audit to obtain sufficient, appropriate evidence to provide a reasonable basis for our findings and conclusions based on our audit objectives. We believe that the evidence obtained provides a reasonable basis for our findings and conclusions based on our audit objectives.
We are separately issuing a controlled unclassified information (CUI) annex to this report that provides additional details on specific NSE industrial base risks.[39] The annex will be available upon request to those with the appropriate and validated need to know.


GAO Contacts
Allison Bawden at (202) 512-3841 or BawdenA@gao.gov.
Staff Acknowledgements
In addition to the contact named above, Jason Holliday (Assistant Director), John Hocker (Analyst in Charge), Cherly Andrews, Antoinette Capaccio, Rebecca Conway, Cindy Gilbert, Caroline Johnson, Mae Jones, Rohan Krishnamoorthy, and Danny Royer made key contributions to this report.
The Government Accountability Office, the audit, evaluation, and investigative arm of Congress, exists to support Congress in meeting its constitutional responsibilities and to help improve the performance and accountability of the federal government for the American people. GAO examines the use of public funds; evaluates federal programs and policies; and provides analyses, recommendations, and other assistance to help Congress make informed oversight, policy, and funding decisions. GAO’s commitment to good government is reflected in its core values of accountability, integrity, and reliability.
Obtaining Copies of GAO Reports and Testimony
The fastest and easiest way to obtain copies of GAO documents at no cost is through our website. Each weekday afternoon, GAO posts on its website newly released reports, testimony, and correspondence. You can also subscribe to GAO’s email updates to receive notification of newly posted products.
Order by Phone
The price of each GAO publication reflects GAO’s actual cost of production and distribution and depends on the number of pages in the publication and whether the publication is printed in color or black and white. Pricing and ordering information is posted on GAO’s website, https://www.gao.gov/ordering.htm.
Place orders by calling (202) 512-6000, toll free (866) 801-7077,
or
TDD (202) 512-2537.
Orders may be paid for using American Express, Discover Card, MasterCard, Visa, check, or money order. Call for additional information.
Connect with GAO
Connect with GAO on Facebook, Flickr, X, and YouTube.
Subscribe to our RSS Feeds or Email Updates. Listen to our Podcasts.
Visit GAO on the web at https://www.gao.gov.
To Report Fraud, Waste, and Abuse in Federal Programs
Contact FraudNet:
Website: https://www.gao.gov/about/what-gao-does/fraudnet
Automated answering system: (800) 424-5454 or (202) 512-7700
Congressional Relations
A. Nicole Clowers, Managing Director, ClowersA@gao.gov, (202) 512-4400, U.S. Government Accountability Office, 441 G Street NW, Room 7125, Washington, DC 20548
Public Affairs
Sarah Kaczmarek, Managing Director, KaczmarekS@gao.gov, (202) 512-4800, U.S.
Government Accountability Office, 441 G Street NW, Room 7149
Washington, DC 20548
Strategic Planning and External Liaison
Stephen J. Sanford, Managing
Director, spel@gao.gov, (202) 512-4707
U.S. Government Accountability Office, 441 G Street NW, Room 7814, Washington,
DC 20548
[1]The Federal Acquisition Regulation defines management and operating contracts as agreements under which the government contracts for the operation, maintenance, or support, on its behalf, of a government-owned or -controlled research, development, special production, or testing establishment wholly or principally devoted to one or more of the major programs of the contracting federal agency. 48 C.F.R. § 17.601. These contracts originated from the Manhattan Project during World War II.
[2]William M. (Mac) Thornberry National Defense Authorization Act for Fiscal Year 2021, Pub. L, No. 116-283, § 3113, 134 Stat. 3388, 4378.
[3]National Defense Authorization Act for Fiscal Year 2022, Pub. L. No. 117-81, § 3135, 135 Stat. 1541, 2231 (2021).
[4]S. Rep. No. 117-130, at 370 (2022).
[5]See GAO, Controlled Unclassified Information Annex for GAO‑25‑107215: Details on Specific Nuclear Weapons Industrial Base Risks, GAO‑25‑108000SU (Washington D.C., Mar. 14, 2025).
[6]For purposes of this report, we collectively refer to these working groups, programs, and teams as “working groups.”
[7]Other agencies, such as the Department of Defense (DOD), may charter working groups to address industrial base risks they share with NNSA.
[8]Department of Energy, Fiscal Year 20224 Enterprise Risk Management Guidance, (Washington D.C.: Dec. 28, 2023); and Office of Management and Budget, Management's Responsibility for Enterprise Risk Management and Internal Control, Circular No. A-123 (Washington, D.C.: July 15, 2016).
[9]GAO, Enterprise Risk Management: Selected Agencies’ Experiences Illustrate Good Practices in Managing Risk, GAO‑17‑63 (Washington, D.C.: Dec. 1, 2016).
[10]GAO, Nuclear Weapons: NNSA Needs to Incorporate Additional Management Controls Over Its Microelectronic Activities, GAO‑20‑357 (Washington, D.C.: June 9, 2020).
[11]GAO, Modernizing the Nuclear Security Enterprise: NNSA is Taking Action to Manage Increased Workload at Kansas City National Security Campus, GAO‑19‑126 (Washington, D.C.: Apr. 12, 2019).
[12]GAO, National Nuclear Security Administration: Explosives Program Is Mitigating Some Supply Chain Risks but Should Take Additional Actions to Enhance Resiliency, GAO‑25‑107016 (Washington, D.C.: Mar. 12, 2025).
[13]GAO, Uranium Management: Actions to Mitigate Risks to Domestic Supply Chain Could Be Better Planned and Coordinated, GAO‑21‑28 (Washington, D.C.: Dec. 10, 2020); National Nuclear Security Administration: Assessments of Major Projects, GAO‑23‑104402 (Washington, D.C.: Aug. 17, 2023); National Nuclear Security Administration: Actions to Recruit and Retain Federal Staff Could Be Improved, GAO‑24‑106167 (Washington, D.C.: May 29, 2024); National Nuclear Security Administration: Improvements Needed for Overseeing Contractor Workforce Recruitment and Retention Efforts, GAO‑24‑106861 (Washington, D.C.: May 29, 2024); Nuclear Supply Chain: NNSA Should Notify Congress of Its Recommendations to Improve the Enhanced Procurement Authority, GAO‑19‑606R (Washington, D.C.: Aug. 8, 2019); Nuclear Supply Chain: DOE Should Assess Circumstances for Using Enhanced Procurement Authority to Manage Risk, GAO‑16‑710 (Washington, D.C.: Aug. 11, 2016); and Nuclear Enterprise: DOD and NNSA Could Further Enhance How They Manage Risk and Prioritize Efforts, GAO‑22‑104061 (Washington, D.C.: Jan. 20, 2022).
[14]GAO, Defense Industrial Base: DOD Should Take Actions to Strengthen Its Risk Mitigation Approach, GAO‑22‑104154 (Washington, D.C.: July 7, 2022).
[15]GAO‑22‑104154 and GAO, Defense Industrial Base: Integrating Existing Supplier Data and Addressing Workforce Challenges Could Improve Risk Analysis, GAO‑18‑435 (Washington, D.C.: June 13, 2018).
[16]These are the four essential elements of risk management for which working groups and M&O contractors are responsible. NNSA is responsible for the other two: aligning its goals and communicating risks to external stakeholders. We discuss these in our second objective.
[17]This software allows users to gain visibility into their supply chain and help identify risks such as sanctions on multiple tiers of suppliers. According to NNSA officials, the software used is the industry standard for supply chain management.
[18]These risk lenses create a common approach to risk assessment and prioritization across the NSE.
[19]NNSA, Risk Management Guide for Defense Programs (Washington D.C.: March 2022).
[20]The Made in America Office ensures that any waivers from Made in America laws are applied clearly, consistently, and transparently across federal agencies. Made in America laws include three waiver types—nonavailability, unreasonable cost, and public interest.
[21]However, NNSA officials said that in general, NNSA senior leadership identify, assess, and address significant enterprise-level risks.
[22]Information about specific key risks is considered CUI and is included in a separate CUI annex. GAO‑25‑108000SU.
[23]NNSA publishes the SSMP annually, either as a detailed report or summary, in response to a statutory requirement to develop and annually update a plan for sustaining the nuclear weapons stockpile. 50 U.S.C. § 2523(a).
[24]The FY 2021 and FY 2022 NDAAs required NNSA to report on the NSE industrial base through 2024. NNSA no longer has a reporting obligation but should have identified and prioritized risks in past industrial base reports.
[25]DOE, Information Quality Guidelines (Washington, D.C.: 2019). Quality is measured by utility, objectivity, and integrity. Utility refers to the usefulness of the information to intended users. Objectivity refers to whether information is being presented in an accurate, clear, complete, and unbiased manner. Integrity refers to the protection of information from unauthorized access or revision.
[27]DOE, Fiscal Year 2024 Stockpile Stewardship and Management Plan, Report to Congress (Washington, D.C.: November 2023). DOE, Fiscal Year 2025 Stockpile Stewardship and Management Plan, Report to Congress (Washington, D.C.: September 2024). The FY 2024 SSMP (released in 2023) is a detailed report, as statutorily required in odd-numbered years. See 50 U.S.C. § 2523(b)(2). The FY 2025 SSMP (released in 2024) is a summary report, as statutorily required in even-numbered years. See 50 U.S.C. § 2523(b)(1).
[28]Information about specific key risks is included in a CUI annex. GAO‑25‑108000SU.
[29]We reviewed the classified appendixes to the FY 2024 SSMP and did not identify additional information on NSE industrial base risks.
[30]Information about specific key risks and steps to address these risks are included in a CUI annex. GAO‑25‑108000SU.
[31]Pub. L. No. 81-774, 64 Stat. 798.
[32]DPA Title I allows the federal government to receive priority access to private materials, facilities, and services in the interest of national defense. DPA Title III allows the federal government to create, maintain, protect, expand, or restore domestic industrial base capabilities essential for the national defense through actions such as making purchases and purchase commitments; encouraging exploration, development, and mining of critical and strategic materials and other materials; and developing production capabilities.
[33]To use these DPA Title III authorities, the President must meet three specific criteria: (1) the industrial resource is essential to national defense; (2) without Presidential action, the industry cannot reasonably be expected to provide the capability in a timely manner; and (3) the action is the most cost-effective, expedient, and practical method for meeting the need. These authorities cannot be delegated.
[34]DOD’s Industrial Base Analysis and Sustainment program implements the Industrial Base Fund established by 10 U.S.C. 4817. The program invests in six priorities: (1) submarine and shipbuilding workforce; (2) kinetic weapons; (3) microelectronics; (4) critical chemicals; (5) casting and forgings; and (6) energy storage and batteries.
[35]DOD focuses on a diverse set of identified joint, defense-critical, and sometimes high-risk manufacturing technology areas. The portfolio works on cross-cutting national security manufacturing needs to stimulate the early development of manufacturing processes concurrent with technology development and workforce training.
[36]An appropriations account covers one or more specific purposes. Reprogramming is when an agency shifts funds within an appropriations account to use them for a purpose other than what was contemplated at the time of appropriation. According to NNSA officials, one initiative was funded using operating funds from the Plutonium Modernization Program, and one was funded using “other project costs” funding from the Savannah River Plutonium Processing Facility project.
[37]Limits on reprogramming are included in annual appropriation acts. For the current limit, see Consolidated Appropriations Act, 2024, Pub. L. No. 118-42, div. D, tit. III, § 301(e), 138 Stat. 25, 206, as continued by Continued Appropriations and Extensions Act, 2025, Pub. L. No. 118-83, 138 Stat. 1524 (2024).
[38]For purposes of this report, we collectively refer to these more than 80 organizations as working groups.
[39]See GAO, Controlled Unclassified Information Annex for GAO‑25‑107215: Details on Specific Nuclear Weapons Industrial Base Risks, GAO‑25‑108000SU (Washington D.C., Mar. 14, 2025).
