CYBERSECURITY
Network Monitoring Program Needs Further Guidance and Actions
Report to Congressional Committees
United States Government Accountability Office
For more information, contact Jennifer R. Franks at franksj@gao.gov.
Highlights of GAO-25-107470, a report to congressional committees
June 2025
CYBERSECURITY
Network Monitoring Program Needs Further Guidance and Actions
Why GAO Did This Study
A key aspect of a rigorous cybersecurity program is continuously monitoring networks and systems to identify and manage risks. Consistent with the FISMA requirement for agency network monitoring, the CISA-led CDM program provides tools to agencies to assist in this effort.
FISMA includes a provision for GAO to periodically report on agencies’ implementation of the act. Among its objectives, this report examines the extent to which the CDM program is (1) meeting its goals, and (2) supporting other federal cybersecurity initiatives.
GAO selected for review the 23 civilian agencies covered in the Chief Financial Officers Act of 1990 (CFO Act). GAO compared CDM program documentation against relevant guidance, and summarized survey results from the 23 civilian CFO Act agencies. GAO also interviewed CISA and OMB officials.
What GAO Recommends
GAO is making four recommendations to DHS and CISA to (1) issue guidance on implementing network security and data protection capabilities, (2) address data quality issues, (3) implement an endpoint solution, and (4) issue updated guidance on cloud asset management. DHS, on behalf of CISA, concurred with the recommendations.
What GAO Found
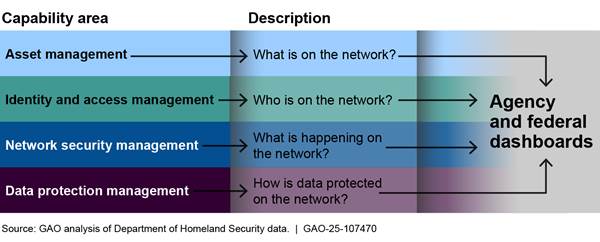
The Department of Homeland Security (DHS) established the Continuous Diagnostics and Mitigation (CDM) program in 2012 to strengthen the cybersecurity of government networks and systems. Its goals are to: (1) reduce exposure to insecure configurations or known vulnerabilities; (2) improve federal cybersecurity response capabilities; (3) increase visibility into the federal cybersecurity posture; and (4) streamline Federal Information Security Modernization Act of 2014 (FISMA) reporting. The Cybersecurity and Infrastructure Security Agency (CISA) manages these goals across four capability areas (see figure). The program is meeting two of its four goals and partially meeting the other two, as discussed below.
CDM has met two goals. First, it is reducing exposure to insecure configurations and known vulnerabilities—22 of 23 agencies reported that the program was helpful in accomplishing this. CDM is also meeting its incident response capability goal.
The program, however, has been less successful in meeting the other two goals.
· Although CISA developed dashboards to visualize and provide insight to the federal cybersecurity posture and the associated capability areas noted above, officials from 21 of 23 agencies stated that they had not yet fully implemented network security and data protection capabilities. Several agencies cited a lack of guidance as contributing to the slow implementation.
· While officials from four agencies stated that CDM helped to automate FISMA reporting, officials from seven other agencies said that data quality issues were adversely affecting efforts to streamline reporting leading to manual updates to correct data errors.
Regarding supporting other initiatives, the Office of Management and Budget (OMB) established expectations that CDM would support federal cybersecurity efforts on zero trust architecture, endpoint detection and response, and cloud asset management. CDM has generally met expectations for the zero trust architecture program. However, CISA had not finalized key activities to support endpoint detection and cloud asset management. CISA’s actions to implement an endpoint solution for all agencies and issue updated guidance on cloud asset management would improve the cybersecurity posture of federal agencies.
Abbreviations
|
CDM |
continuous diagnostics and mitigation |
|
CFO Act |
Chief Financial Officers Act of 1990 |
|
CISA |
Cybersecurity and Infrastructure Security Agency |
|
DHS |
Department of Homeland Security |
|
EDR |
endpoint detection and response |
|
FISMA |
Federal Information Security Modernization Act of 2014 |
|
FY |
fiscal year |
|
GSA |
General Services Administration |
|
IT |
information technology |
|
OMB |
Office of Management and Budget |
|
PAC |
Persistent Access Capability |
|
PMO |
program management office |
|
ZTA |
zero trust architecture |
This is a work of the U.S. government and is not subject to copyright protection in the United States. The published product may be reproduced and distributed in its entirety without further permission from GAO. However, because this work may contain copyrighted images or other material, permission from the copyright holder may be necessary if you wish to reproduce this material separately.
June 11, 2025
The Honorable Rand Paul, M.D.
Chairman
The Honorable Gary C. Peters
Ranking Member
Committee on Homeland Security and Governmental Affairs
United States Senate
The Honorable James Comer
Chairman
The Honorable Stephen F. Lynch
Acting Ranking Member
Committee on Oversight and Government Reform
House of Representatives
Federal agencies rely heavily on information technology systems to carry out their missions, making the security of these systems vital due to the sensitive and essential data they contain. Moreover, these systems face increasing risks, not only from insider threats, but also from external threats of malicious attackers. As such, maintaining rigorous cybersecurity programs that provide timely, relevant, and accurate information is imperative.
The Federal Information Security Modernization Act of 2014 (FISMA) requires federal agencies to develop, document, and implement information security programs to protect the information and systems that support the agencies’ operations and assets.[1] As Congress recognized in passing FISMA, one aspect of a rigorous information security program is continuously monitoring networks and systems to identify and manage risks.[2]
The Department of Homeland Security (DHS) developed the Continuous Diagnostics and Mitigation (CDM) program in 2012 to strengthen the cybersecurity of government networks and systems by providing tools to agencies to support continuous monitoring of their networks. The CDM program includes capabilities intended to help agencies identify cybersecurity risks on an ongoing basis, use CDM information to prioritize the risks based on potential impacts, and then mitigate the most significant vulnerabilities first.[3] We previously reported that the estimated program cost through 2031 would be around $10 billion.[4]
FISMA also includes a provision for GAO to periodically report to Congress on agencies’ implementation of the act. Our specific objectives for this review were to determine (1) to what extent the CDM program is meeting its goals; (2) to what extent CDM supports agency implementation of other federal cybersecurity initiatives; and (3) what opportunities exist to strengthen the program.
We selected the 23 civilian agencies covered by the Chief Financial Officers Act of 1990 (CFO Act)[5] for review because they comprise a significant set of CDM contract groups.[6] We also conducted work with the Cybersecurity and Infrastructure Security Agency (CISA) within the Department of Homeland Security because the federal CDM program management office (PMO) resides within CISA. Finally, we included the Office of Management and Budget (OMB) in our review due to its development of government-wide requirements concerning agency implementation of CDM.
To address the first objective, we compared CDM program documentation to the four program goals as specified by CISA. These goals are to (1) reduce the agency threat surface, (2) improve an agency’s ability to respond to cybersecurity incidents, (3) increase visibility into the federal cybersecurity posture, and (4) streamline FISMA reporting.[7] The documentation we analyzed included CDM program descriptions; OMB memoranda on FISMA reporting; the CDM Technical Capabilities Volume 2, version 2.5; prior GAO reports on CDM and related initiatives; and other related and relevant documents.
To further inform this objective, as well as the remaining objectives, we sent a survey to the 23 civilian CFO Act agencies[8] to solicit their experiences and views on their implementations of the CDM program requirements and the goals of the program.[9] Questions addressed topics such as the status of agency implementation of program capabilities, program performance, and opportunities for program improvement. A full list of the survey questions can be found in Appendix I.
The practical difficulties of developing and administering a survey may introduce errors, including how a particular question is interpreted, for example. Therefore, we included steps in developing and administering the questionnaire to minimize such errors. We conducted three pretests of the questionnaire with IT subject matter experts from three agencies to check that (1) the questions were clear and unambiguous, (2) terminology was used correctly, (3) the questionnaire did not place an undue burden on agency officials, (4) the information could be obtained, and (5) the survey was comprehensive and unbiased.
For the second objective, we compared CDM program documentation against requirements associated with other federal cybersecurity initiatives. We selected three initiatives covered by recent OMB directives that CISA and OMB stated they consider CDM to support—zero trust architecture (ZTA),[10] endpoint detection and response (EDR),[11] and cloud asset management.[12] We compared CDM documentation against OMB requirements governing ZTA,[13] EDR,[14] and management of cloud assets.[15] For each initiative, we also interviewed CISA and OMB officials and evaluated CDM program documentation to determine the extent to which the program supports each initiative. In doing so, we considered best practices from GAO guidance on evidence-based policymaking.[16]
To address the third objective, we asked selected agencies about challenges they had experienced in implementing the program in our survey. We also asked selected agencies about any opportunities that existed to strengthen the program. We requested and reviewed documentation from CISA to determine what actions it was taking to address the challenges and opportunities.
Finally, we interviewed officials from the 23 CFO Act agencies regarding their experiences in implementing CDM program requirements. We also interviewed CISA officials regarding program management, and OMB officials regarding program oversight.
We conducted this performance audit from March 2024 through June 2025 in accordance with generally accepted government auditing standards. Those standards require that we plan and perform the audit to obtain sufficient, appropriate evidence to provide a reasonable basis for our findings and conclusions based on our audit objectives. We believe that the evidence obtained provides a reasonable basis for our findings and conclusions based on our audit objectives.
Background
DHS established CDM to support government-wide and agency-specific efforts to provide adequate, risk-based, and cost-effective cybersecurity. The goals of the CDM program are to:
· reduce the agency threat surface,
· improve federal cybersecurity response capabilities,
· increase visibility into the federal cybersecurity posture, and
· streamline FISMA reporting.[17]
The program is intended to allow federal agencies to automate network monitoring, correlate and analyze security-related information, and enhance risk-based decision making at both the individual agency and federal levels. As depicted in figure 1, automated tools send information about hardware devices, including any associated software, connected to an agency’s network to a collection point. That collection point compares the information with expected outcomes, such as whether actual device configuration settings meet agency or federal benchmarks.
The results of these comparisons are then sent to an electronic visual display at an agency, referred to as the agency dashboard. Each agency dashboard is queried by the federal dashboard, which is managed by CISA and provides the agencies with visibility across the entire federal civilian executive branch.
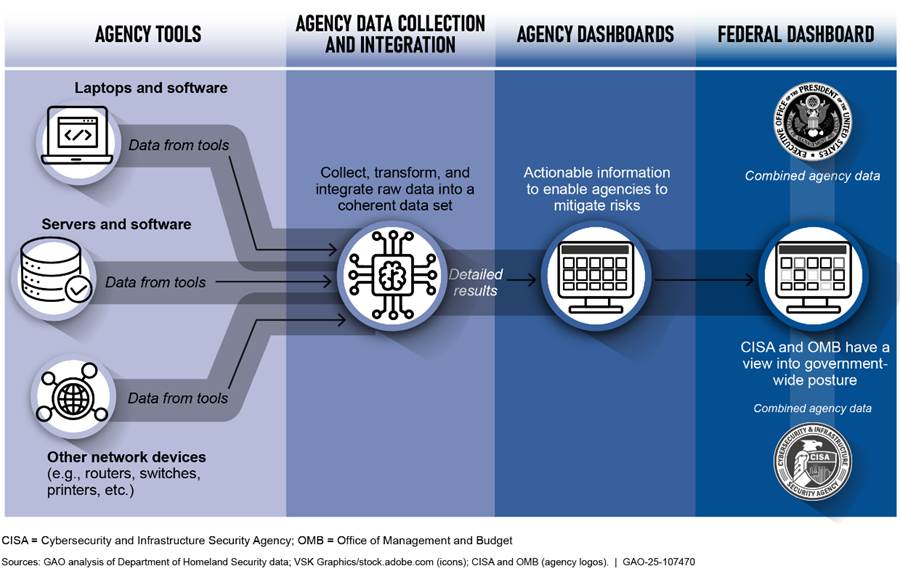
CDM Consists of Capability Areas, Tools, and Dashboards
DHS organized CDM into four capability areas: asset management, identity and access management, network security management, and data protection management. The department further subdivided each capability area into sub-capabilities intended to support each area. Figure 2 depicts the capability areas that support the CDM program.
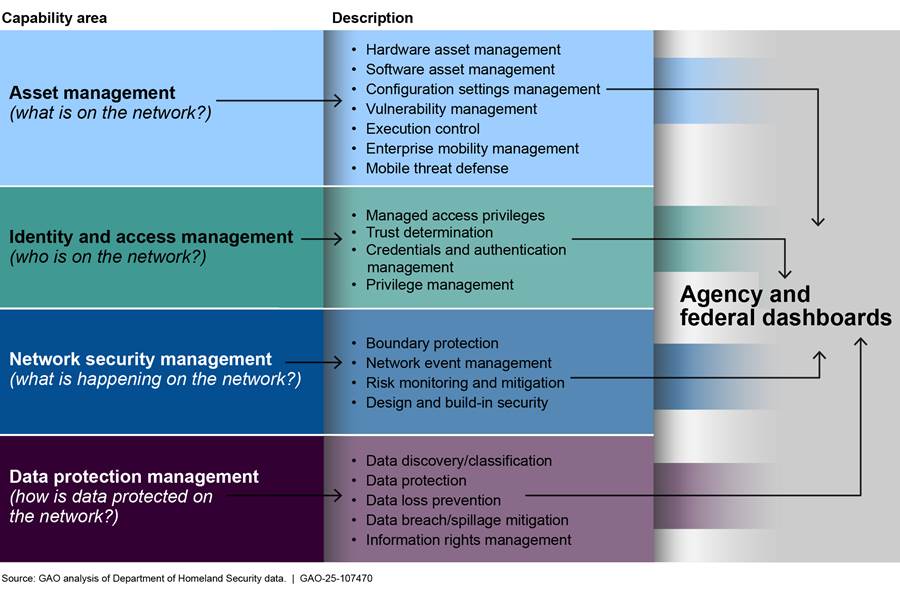
Each of these capability areas uses tools to feed data to agency and federal dashboards.
CDM Tools. The CDM program provides tools to agencies at reduced cost. Specifically, this is because agencies can acquire the tools in groups as opposed to on their own. Nevertheless, agencies have the option to use other tools to meet the program’s requirements at their discretion.
Agency CDM dashboards and the DHS federal CDM dashboard. The CDM program provides each agency with a dashboard that receives, aggregates, and displays information from the CDM tools installed on its network. The agency dashboard is to produce alerts to notify dashboard users of critical issues requiring immediate attention. As noted previously, data within the agency dashboard are available to be queried from the federal dashboard, which is maintained by CISA.
Multiple Stakeholders Are Responsible for Implementing and Overseeing the CDM Program
The CDM program requires coordination among various stakeholders that are responsible for implementing the program. Each stakeholder has specific roles and responsibilities within the program.
DHS: FISMA specifies DHS’s responsibilities for assisting federal agencies with securing their information and systems, including providing operational and technical assistance to agencies and monitoring agencies’ implementation of information security policies and practices. The Federal CDM PMO signs agreements with each agency participating in the program to outline the responsibilities for each in implementing the CDM program requirements. The agreements require the PMO to, among other things, solicit feedback from participating agencies regarding their experiences in implementing the CDM program requirements. As the program’s technical point of contact, the PMO is responsible for ensuring that the integrators—private-sector organizations selected by CISA and the General Services Administration (GSA) to install and configure CDM tools on the agency’s network—perform at an acceptable level.
GSA: GSA partnered with DHS to establish government-wide contracts to provide a consistent government-wide set of information security continuous monitoring tools and services to agencies. GSA is to provide oversight for the acquisition of CDM tools and services.
Integrators: As previously noted, integrators are private-sector organizations selected by CISA and GSA to install and configure tools on an agency’s network. Each integrator is to develop an implementation solution (in consultation with each participating federal agency and DHS) that supports the CDM capability areas. The integrator is responsible for troubleshooting problems with the data that the tools send to the agency’s CDM dashboard and the federal CDM dashboard.
Office of Management and Budget (OMB): OMB is to provide oversight by using the CDM federal dashboard to monitor agency cybersecurity posture government-wide.
Participating agencies:[18] The PMO emphasizes the importance of agency staff working closely with DHS and the integrators to ensure that CDM capabilities are properly implemented and achieve intended objectives. Each agency is required to evaluate integrator implementation plans and operate and maintain the CDM tools once the integrator has installed and configured them. While DHS covers the initial funding for implementation of the tools supporting the capabilities, agencies are responsible for funding the ongoing operations and maintenance of the tools.[19]
Federal Agencies Have Established Requirements for the CDM Program
In 2023, CISA published an update to its set of functional requirements to govern the CDM program in its CDM Technical Capabilities Volume 2, version 2.5.[20] This document is intended to be an engineering baseline, provided to agencies and CDM integrators, for use during CDM solution development within contract activities. Integrators are to use the functional requirements to develop a full set of system-level requirements, inclusive of additional deployment considerations such as agency needs, policies, and/or environmental constraints.
In addition, OMB has incorporated CDM into government-wide guidance on FISMA reporting and cybersecurity. For example:
· Guidance on Federal Information Security and Privacy Management Requirements.[21] Agencies are to report at least 90 percent of government-furnished equipment through the CDM program. Agencies must continue to provide data on assets in an automated manner to the maximum extent feasible.
· Federal Zero Trust Strategy.[22] Agencies must create reliable asset inventories through participation in the CDM program. In addition, CISA will design the CDM program to better support a cloud-oriented federal architecture.
· Guidance on Endpoint Detection and Response (EDR).[23] Within 90 days of publication of the guidance, agencies were to provide CISA access to current enterprise EDR deployments or engage with CISA to identify future state options. Further, CISA was to develop a process for continuous performance monitoring to help agencies ensure that EDR solutions are deployed and operate in a manner that will detect and respond to common threats.
GAO Has Made Recommendations to Improve CDM
In August 2020, we reported that three selected agencies had generally deployed tools intended to provide cybersecurity data to support the CDM program.[24] However, none of the three agencies had effectively implemented all key CDM program requirements associated with the asset management program capability.
We made six recommendations to DHS, including to ensure that contractors provide unique hardware identifiers; and three recommendations each to the Federal Aviation Administration, Indian Health Service, and Small Business Administration, including to compare configurations to benchmarks. DHS has implemented all six of the recommendations and the Federal Aviation Administration and Small Business Administration have implemented three recommendations each.
As of May 2025, the Indian Health Service was still in the process of addressing two of three recommendations we made to it. These remaining recommendations included documenting hardware inventory information and comparing configuration settings against federal benchmarks. According to the Department of Health and Human Services, the Indian Health Service is on track to address the remaining recommendations before the end of the year.
CDM Is Meeting Two Goals and Partially Meeting Two Others
According to CISA, the goals of the CDM program are to
· reduce agency threat surface;
· improve federal cybersecurity response capabilities;
· increase visibility into the federal cybersecurity posture; and
· streamline FISMA reporting.
CDM is meeting two of these goals on reducing agencies’ threat surfaces and improving cybersecurity response capabilities while partially meeting the remaining two goals. Further efforts can lead to meeting all four goals and lessening the cybersecurity risks faced by federal agencies.
CDM Has Reduced Agency Threat Surface
CDM is meeting the goal of reducing agency threat surfaces. The CDM program has provided the procurement and deployment of monitoring equipment, sensors and tools, dashboards, and cyber operations services. When combined, these elements have generated the ability to identify and prioritize cybersecurity risk on a continuous basis while enabling cybersecurity professionals to manage and mitigate risks to government data and networks. This is turn allows agencies to reduce their exposure to compromise.
Agency CDM officials generally agreed that the program was meeting this goal. Specifically, officials from 22 out of 23 agencies agreed that the CDM program has been helpful in reducing the threat surface of their agency. For example, officials from four agencies stated that while all potential threat vectors continue to exist, their agencies have more capabilities to detect and respond to threats.
CDM Has Improved Federal Cybersecurity Response Capabilities
CDM is meeting the goal of improving federal cybersecurity response capabilities. The program developed operational requirements to allow real-time prioritization of remediation activities and resources.
Officials from 14 of 23 agencies agreed that the CDM program improved their agencies’ cybersecurity incident response capabilities at least at a somewhat improved level. For example, officials from four out of the 14 agencies stated that the CDM program enhanced agency incident response by providing real-time monitoring and automated threat detection.
Officials from four of the remaining nine agencies told us that, as permitted by the CDM program, they were using their own alternative response capabilities. Officials with three agencies may also be using their own response capabilities but they did not provide us with information on this. The two remaining agencies did not share their opinions on incident response improvement.
CDM Has Partially Increased Visibility into Cybersecurity Posture
CDM has partially met the goal of enhancing cybersecurity visibility. CISA developed a dashboard for use by participating agencies intended to consolidate and visualize information collected from CDM tools. The program also developed a federal dashboard, which enables CISA and OMB to see a government-wide view of agency cybersecurity information as collected through the program. The dashboards are intended to visualize information from each of the capability areas, providing insight into the cybersecurity posture associated with assets, users, networks, and data.
However, officials from 21 of the 23 civilian CFO Act agencies stated that they had not fully implemented capabilities within the network security management and data protection management areas. According to officials from several agencies, they are awaiting additional guidance from CISA regarding these capabilities. Figure 3 shows how many selected agencies consider their implementations of the CDM capability areas to be in the operations and maintenance phase of implementation.[25]
Figure 3: Continuous Diagnostics and Mitigation Capabilities in Operations and Maintenance Phase at 23 Civilian Chief Financial Officers Act Agencies
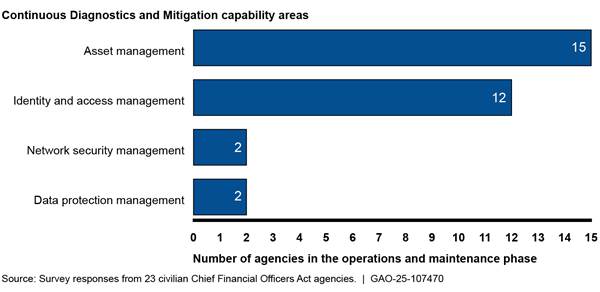
According to CISA, the federal CDM PMO intends to reprioritize and revamp the network security management and data protection management capability areas in fiscal year (FY) 2025. This will include the reassessment of the program’s current cyber marketplace and offerings within that marketplace, as well as revising the CDM capability catalog with appropriate security technologies that align with government priorities, such as zero trust. CISA plans to initiate pilots with ready and willing agencies as early as FY 2025, but the agency has not committed to a specific timeframe for doing so.[26]
Until CISA issues further guidance to prioritize the implementation of the network security management and data protection management capabilities of the program, agencies run the risk of having meaningful visibility gaps within their CDM solutions.
CDM Has Partially Streamlined FISMA Reporting Requirements
The data collection and visualization capabilities offered by the CDM program provide agencies with the ability to collect and report required data in an automated fashion. As such, CDM offers the opportunity to streamline once-manual processes into automated processes for FISMA reporting.
A few agencies reported that CDM had streamlined FISMA reporting. For example, officials from four agencies reported that the CDM program helps the agency to automate aspects of the agency’s FISMA reporting requirements.
However, officials from seven of the selected agencies reported that they had to manually edit incorrect data for FISMA reporting. Specifically, officials from three of the agencies reported that they had to correct data 100 percent of the time. Officials from the remaining four agencies reported having to make changes 20 to 50 percent of the time.
To help address data quality concerns, the federal CDM PMO updated a Data Quality Management Plan, which is intended to help mitigate some data quality issues. In addition, due to the inherent complexity stemming from the high level of interoperability required for the CDM solution to operate nominally, the PMO also developed a new set of activities with discrete tasks and resources directly focused on data-related issues.[27] CISA’s FY 2025 Data Quality Management Plan states that the CDM Data Management Team shall report data quality assessment results to CDM leadership and OMB. In addition, this team will analyze and implement new data analysis tools for the team to use in the data quality assessment process (e.g., anomaly detection and visualization).
However, such issues have persisted since at least 2020.[28] Although CISA has developed a Data Quality Management Plan that includes quality thresholds, the plan does not include milestones for addressing data quality. Until CISA establishes milestones to address data quality problems on an ongoing basis, the CDM program will not be able to fully meet its goal for streamlining FISMA reporting.
CDM Support of Additional Federal Cybersecurity Initiatives Varies
CISA and OMB stated that CDM is intended to support additional government-wide cybersecurity initiatives. These include ZTA, EDR, and cloud asset management. CDM generally supports ZTA implementation, and partially supports EDR initiatives and the management of agency assets in the cloud.
CDM Generally Supports Agency ZTA Implementation
ZTA requires agencies to have a complete understanding of the devices, users, and systems interacting within their IT environment.[29] For most enterprises, creating and maintaining a complete inventory over time requires tools that can support the dynamic discovery and cataloging of assets. OMB’s Zero Trust Strategy necessitates ongoing, reliable, and complete asset inventories, including by leveraging the CDM program.
The asset management program area of CDM, if implemented effectively, should enable agencies to create ongoing, reliable, and complete asset inventories. Elements of the program should support agency implementation of zero trust principles. For example:
· Considered to be a foundational capability of the CDM program, the asset management capability provides the ability for agencies to create inventories of the assets that connect to their networks. In doing so, CDM can help agencies understand the devices and systems that interact with their networks. Through the CDM dashboard, each agency also has the ability to dynamically discover and catalog its IT assets.
· Further, the identity and access management capability of the CDM program is intended to enable agencies to manage access privileges, determine trust, manage credentials and authentication management, and implement security-related behavioral training. In this manner, CDM is architected to help agencies understand who the users are on the network.
Further, CDM PMO officials stated that they are working to align CDM program requirements with zero trust initiatives. Specifically, officials stated that they will strive to align program requirements to relevant OMB memoranda where there is applicability to CDM.
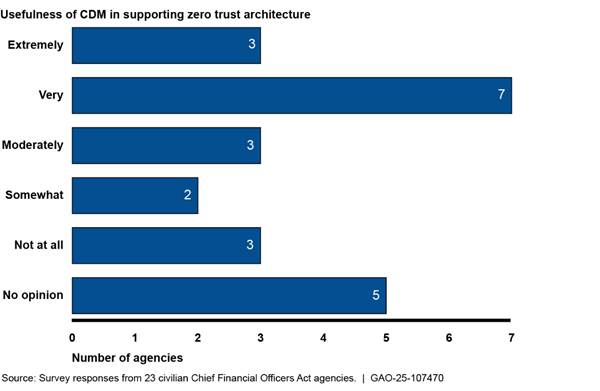
Many selected agencies stated that CDM is generally helpful in supporting their implementation of their ZTA. Specifically, 15 agencies found CDM to be at least somewhat helpful in supporting their ZTA efforts.[30] Figure 4 shows how helpful officials from each of the selected agencies found CDM in supporting their ZTA deployments.
Figure 4: Usefulness of the Continuous Diagnostics and Mitigation (CDM) Program in Supporting Zero Trust Architecture Initiatives
CDM Partially Supports Agency EDR
Endpoint detection and response (EDR) provide cybersecurity monitoring and control of endpoint devices. EDR is a sub-capability in the network security management capability area of the CDM program.[31]
OMB guidance requires CISA to work with agencies to help improve government-wide endpoint detection and response capabilities.[32] Specifically:
· Through a collective effort, the federal government is to achieve government-wide visibility through a centrally located EDR initiative, implemented by CISA, to support host-level visibility, attribution, and response across federal information systems.
· Agencies shall provide CISA with access to their current and future EDR solutions to enable proactive threat hunting activities and a coordinated response to advanced threats. This should also facilitate, as appropriate, network access to CISA personnel and contractors supporting the implementation of the EDR initiative.
In line with OMB requirements, CISA developed the Persistent Access Capability (PAC). The program is intended to provide CISA with increased visibility into agency EDR solutions. Specifically, PAC would allow CISA to better support cyber threat hunt engagements, plus detection and response activities that CISA or their agency partners are leading. If implemented effectively, the program would help to achieve government-wide visibility through a centrally located EDR initiative.
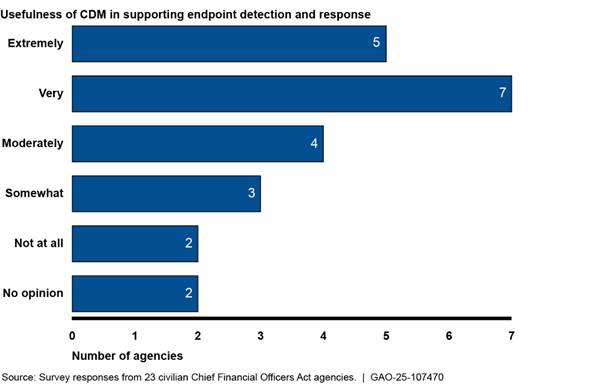
In addition, a majority of selected agencies found CDM supportive of their EDR initiatives. Figure 5 shows how helpful agency CDM officials found CDM in supporting their EDR initiatives.
Figure 5: Usefulness of the Continuous Diagnostics and Mitigation (CDM) Program in Supporting Endpoint Detection and Response Initiatives
However, CISA has not fully achieved government-wide visibility into agency EDR solutions. CISA officials stated that, as of March 2025, not all agencies had been onboarded to PAC. Specifically, according to CISA officials, five CFO Act agencies have been fully onboarded, and another five CFO Act agencies have been partially onboarded in PAC. The officials stressed that onboarding is a priority but stated that agencies must be willing to participate in the program. Until CISA onboards selected agencies into the PAC program, CISA will not have a comprehensive view of endpoint security government-wide.
CDM Partially Supports Management of Agency Assets in the Cloud
Cloud computing provides agencies with potential opportunities to obtain IT services more efficiently. If not effectively implemented, it also poses cybersecurity risks.
OMB required CISA to update the CDM program to better support a cloud-oriented federal architecture.[33] CISA officials stated that the agency is developing a solution intended to assist agencies in inventorying and securing cloud assets within agency environments. Officials also explained that the initiative would incorporate, for example, capabilities to better account for the provisioning of cloud resources, as well as how those resources are inventoried and secured. Further, the officials stated that the initiative will also include compliance management, vulnerability management, and real-time threat detection of cloud workloads.
In addition, CDM PMO officials explained that CISA is developing its solution in line with OMB requirements. The officials stated that the program is slated to begin in fiscal year 2025. If implemented effectively, the program could enhance CDM’s offerings to manage assets in the cloud.
GAO guidance on evidence-based policymaking states that, among other things, agencies should identify strategies along with related resources to achieve objectives. However, as of December 2024, CDM PMO officials stated that CISA’s plan for additional cloud activities was under active revision to adjust the agency’s current strategy and more effectively align resources to enhance CDM’s cloud offering. In May 2025, CISA provided us with a high-level strategy, but it did not identify resources needed to achieve its objectives.
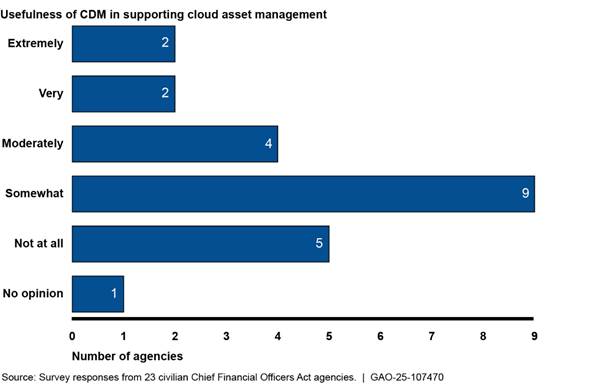
While CISA officials stated that additional cloud activities are a priority, five of the selected agencies considered CDM to be not helpful at all in supporting the management of cloud assets. Figure 6 shows how helpful officials from selected agencies found CDM in supporting the management of their cloud assets.
Figure 6: Usefulness of the Continuous Diagnostics and Mitigation (CDM) Program in Supporting Cloud Asset Management
CISA officials explained that uncertainty surrounding funding has made it difficult to determine time frames for additional cloud-related efforts. Nevertheless, until the CDM program updates its strategy to include required resources, as well as implements it and provides further guidance to agencies, the program will have less assurance that cloud assets will be secure.
CISA Is Addressing Opportunities to Strengthen the Program
CISA is working to address challenges agencies faced in implementing CDM. The agency is also working to address additional opportunities to improve the program.
CISA Is Addressing Challenges
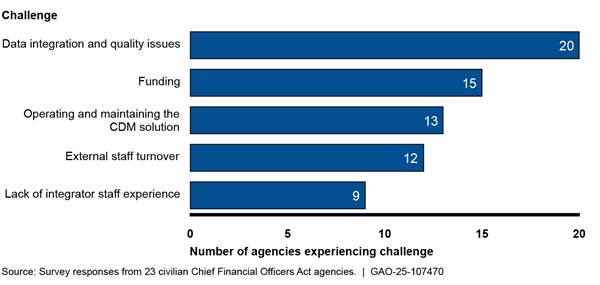
Agencies reported challenges in implementing the CDM program. Figure 7 provides a list of the challenges.
Figure 7: Challenges in Implementing Continuous Diagnostics and Mitigation (CDM) Program Requirements
CISA is taking actions to address the challenges. These include:
· Data integration and quality. Twenty of 23 selected agencies reported that they face issues with data integration and data quality. Data integration issues include, for example, a need to integrate additional data sources into the CDM dashboard. Agencies also reported data quality issues, such as differences in how individual agencies and CISA use data to support FISMA metrics. Further, 16 of 23 selected agencies reported issues involving their hardware inventories, such as duplication of devices.
To address these challenges, CISA officials stated that CISA has robust relationships with most agencies regarding ongoing data quality monitoring. The officials added that they use a Data Quality Management Plan as a framework to evaluate the quality of datasets within both agency dashboards as well as the federal dashboard. Further, officials explained that the PMO helps agencies in triaging and troubleshooting data issues. However, as discussed earlier, until CISA establishes milestones for addressing issues with data quality on an ongoing basis, the issue runs the risk of persisting and negatively impacting agencies’ ability to streamline FISMA reporting.
· Funding and ongoing operations and maintenance expenses. Fifteen of 23 selected agencies reported challenges with ongoing operations and maintenance expenses. For example, challenges included difficulty transitioning to providing funding for CDM tools, license renewals that are misaligned with government funding cycles, and budgeting teams that do not understand all the technical details of CDM. Thirteen of 23 selected agencies specifically cited challenges in the rising costs of operating and maintaining the CDM solution.
To address this challenge, CISA is working to reduce licensing costs by, for example, consolidating existing tools and licenses, reducing duplication, and assisting agencies in developing proposals. Officials also stated that CISA has ongoing discussion with agencies to provide greater visibility into funding processes.
· Staff turnover and a decline in integrator experience. Twelve of 23 selected agencies reported challenges in external staff turnover (e.g., at CISA or the integrator). One agency cited, for example, being responsible to train new integrator staff on internal agency processes created a burden.
CISA is aware of this challenge and is taking actions to address it. For example, officials stated that the next generation of CDM contracts will increase standardization in areas requiring the most process knowledge, which may reduce impact when staff turnover occurs. Further, CISA officials stated that they continually request feedback from agencies about integrator performance and that all CDM contracts contain requirements and incentives for the retention of key personnel.
Although agencies face challenges in implementing program requirements, they are generally satisfied by the ways in which the federal CDM PMO responds to issues that agencies have identified. Specifically, 19 out of 21 selected agencies are somewhat satisfied or very satisfied by the receptiveness of the PMO to issues raised by agencies.[34] In addition, 17 of 21 selected agencies are either somewhat satisfied or very satisfied by the PMO’s resolution of issues raised by agencies. With continued responsiveness and resolution efforts, CISA’s actions should help mitigate challenges associated with funding and ongoing operations and maintenance expenses, and staff turnover and a decline in integrator experience.
CISA Is Working to Address Additional Opportunities to Improve the Program
Agencies identified additional opportunities to improve the CDM program, and CISA is working to address them. For example:
· Enhancing the procurement model. Selected agencies shared several opportunities to improve the procurement model, such as aligning license renewal dates with government funding cycles, negotiating pricing on behalf of all agencies, and enhancing visibility into the procurement process. CISA has acknowledged that the existing primary funding model can at times present challenges for capability implementation and sustainment and intends to revamp the model through a new program known as Strategic Cybersecurity Acquisition & Buying Services, which officials stated will expand CISA’s buying power and centralize IT procurements. However, CISA officials noted that the program is mindful of both up-front and long-term costs and takes these into account during its procurement process. Further, the officials stated that CISA involves participating agencies in acquisition discussions to aid in visibility.
· Implementing artificial intelligence (AI) tools. Selected agencies were interested in leveraging AI to, for example, improve threat prediction capabilities. According to CISA officials, the agency is exploring ways in which AI can be strategically and responsibly incorporated into CDM. They added that the program plans to pilot an AI solution with an agency participating in the program in the second quarter of FY 2025.
· Adding additional features to the CDM dashboards. Selected agencies stated that they were interested in adding additional features to the agency dashboard, such as custom visualizations and additional data sources. CISA officials stated that the PMO has continually sought solutions to provide maximum flexibility for agencies regarding data types and sources that can be integrated into CDM. In addition, CISA officials stated that the agency had periodically updated the CDM dashboard to make it more operationally relevant to agencies, and to allow agencies to implement custom data fields and visualizations, in keeping up with evolving federal priorities.
Conclusions
The CDM program is meeting two of its goals and is partially meeting two others. However, for the visibility goal, additional guidance could significantly improve the implementation of the network security management and data protection management capabilities. In addition, although the CDM PMO has developed a plan to address data quality issues, it lacks milestones to ensure that problems are addressed on an ongoing basis. Mitigating these problems would help the program meet its goal of streamlining FISMA reporting.
Regarding agencies participating in the CDM program’s Persistent Access Capability (PAC), CISA did not have government-wide visibility into agency endpoint detection and response capabilities. In addition, because the CDM PMO had not updated and implemented its strategy concerning the management of cloud assets within the program, agencies had less assurance that their cloud assets would be protected. By onboarding agencies to the PAC, and providing updated cloud guidance, CISA can enable agencies to enhance government-wide endpoint detection and response and cloud asset management.
Recommendations
We are making four recommendations to the Department of Homeland Security concerning the CDM program. Specifically:
The Secretary of Homeland Security should direct the Director of the Cybersecurity and Infrastructure Security Agency to issue guidance to help facilitate agencies’ implementation of the network security management and data protection management capabilities within the CDM program. (Recommendation 1)
The Secretary of Homeland Security should direct the Director of the Cybersecurity and Infrastructure Security Agency to develop milestones for addressing data quality issues on an ongoing basis. (Recommendation 2)
The Secretary of Homeland Security should direct the Director of the Cybersecurity and Infrastructure Security Agency to work with the 23 civilian Chief Financial Officers Act agencies to ensure that willing agencies are onboarded to the Persistent Access Capability. (Recommendation 3)
The Secretary of Homeland Security should direct the Director of the Cybersecurity and Infrastructure Security Agency to update the agency’s strategy associated with its cloud asset management activities to include required resources, provide the strategy to agencies, and implement the strategy. (Recommendation 4)
Agency Comments and Our Evaluation
We requested comments on a draft of this report from the Cybersecurity and Infrastructure Security Agency (CISA), the agency to which we made the recommendations. We also requested comments from 22 other agencies we selected for our review and the Office of Management and Budget (OMB).
In written comments, which are reprinted in Appendix II, the Department of Homeland Security (DHS), on behalf of CISA, stated that CISA concurred with our four recommendations. The department stated that CISA remains committed to partnering with all agencies participating in CDM to strengthen its operational use and expand its implementation. Regarding program guidance, the department stated that the program will author and provide agencies with strategies regarding how CDM participants can collaborate and tailor agency priorities to facilitate implementation of the network security management and data protection management capabilities. The department estimates that CISA will complete this effort by June 30, 2026.
In addition, by December 31, 2026, CISA plans to provide a roadmap for implementing the capabilities. If effectively implemented, providing strategies and a roadmap should help (1) prioritize the implementation of the network security management and data protection management capabilities of the program and (2) reduce the risk that agencies may have meaningful visibility gaps within their CDM solutions.
Regarding data quality, DHS stated that the program will continue to update its Data Quality Management Plan on an annual basis, provide it to agencies, and execute its quality control processes. The department estimates that CISA will complete these efforts by April 30, 2026. The department stated that data quality improvements are not milestone-driven activities but are an ongoing responsibility for day-to-day sustainment of operational solutions shared between agencies and CISA. As discussed in our report, addressing data quality problems on an ongoing basis would help the program meet its goal for streamlining FISMA reporting.
Regarding the Persistent Access Capability (PAC), DHS stated that CISA’s Cybersecurity Division will continue to work to make the PAC available to all agencies’ endpoint detection and response solutions. Once ready, CISA will formally offer to onboard all willing and still outstanding CFO Act agencies to PAC. The department reiterated that CISA currently does not have the authority to mandate that an agency onboard to the PAC, but that CISA will continue to make PAC available to all agencies and partner with them to work through any onboarding constraints, as appropriate. The department estimates that CISA will complete these activities by January 30, 2026. As discussed in our report, by onboarding agencies to PAC, CISA can enable agencies to enhance government-wide endpoint detection and response.
Regarding cloud asset management, DHS stated that the program will update its strategy to include anticipated resources required to successfully execute its activities and will formally share it with CDM-participating agencies. CISA will also implement the strategy subject to adequate resourcing through appropriations and staffing. The department estimates that CISA will complete these activities by April 30, 2026. By updating its strategy to include required resources, as well as implementing it and providing further guidance to agencies, the program will have more assurance that cloud assets will be secure. Officials from CISA also provided technical comments on the report, which we addressed as appropriate.
Of the remaining 23 agencies, the Department of Transportation, the Department of Health and Human Services, and the National Aeronautics and Space Administration provided technical comments on the report, which we addressed as appropriate. Officials from 19 other agencies told us that they did not have any comments on the draft. OMB did not respond to our request for comments.
We are sending copies of this report to the appropriate congressional committees; the heads of the 23 civilian CFO Act agencies, including the Secretary of the Department of Homeland Security; the Director of the Cybersecurity and Infrastructure Security Agency; the Director of OMB; the inspectors general of the 23 agencies; and other interested parties. In addition, the report is available at no charge on the GAO website at https://www.gao.gov.
If you or your staff have any questions about this report, please contact me at FranksJ@gao.gov. Contact points for our Offices of Congressional Relations and Public Affairs may be found on the last page of this report.
GAO staff who made key contributions to this report are listed in Appendix III.

Jennifer R. Franks
Director, Center for Enhanced Cybersecurity
Information Technology and Cybersecurity
Appendix I: Survey Questions Sent to 23 Civilian Chief Financial Officers Act of 1990 (CFO Act) Agencies
This appendix contains the survey questions sent to the 23 civilian Chief Financial Officers Act agencies to obtain their perspectives regarding the Continuous Diagnostics and Mitigation (CDM) program. We sent the survey to agency liaisons in order to provide it to agency CDM experts. We received responses from all 23 agencies.
Survey Questions
Section A: Overview/Background Information
1. Who is your current integrator(s)? (Check all that apply.)
Booz Allen Hamilton
CGI
ManTech
Other: _____________________
2. Which Dynamic and Evolving Federal Enterprise Network Defense (DEFEND) group does your agency belong to? (Select one response.)
Group A
Group B
Group C
Group D
Group E
Group F
a. What would you like to see from CISA in the next generation of contracts?
b. What would you like to see from the integrator in the next generation of contracts?
3. Please respond to each question in the table below.
|
Question |
Response |
|
Approximately how many government-furnished equipment (GFE) endpoints are at your agency? |
|
|
On average, how many of these endpoints are discoverable through CDM? |
|
|
Approximately how many GFE endpoints are mobile devices? |
|
|
On average, how many mobile devices are discoverable through CDM? |
|
|
Approximately how many GFE networking devices are at your agency? |
|
|
On average, how many networking devices are discoverable through CDM? |
|
|
Approximately how many GFE input/output devices are at your agency? |
|
|
On average, how many input/output devices are discoverable through CDM? |
|
4. Approximately what percentage of high-value assets does your agency tag through the CDM program?
___________ %
a. If applicable, how does your agency accomplish tagging?
5. What is the status of each of the following components of the CDM capabilities at your agency? (Select one response per row.)
|
Component |
Not Started |
Initiation |
Development / Acquisition |
Testing |
Operations & Maintenance |
Other (please specify) |
|
Hardware asset management (HWAM) |
|
|
|
|
|
|
|
Software asset management (SWAM) |
|
|
|
|
|
|
|
Security management configuration settings (CSM) |
|
|
|
|
|
|
|
Software vulnerabilities (VUL) |
|
|
|
|
|
|
|
Component |
Not Started |
Initiation |
Development / Acquisition |
Testing |
Operations & Maintenance |
Other (please specify) |
|
Account/access/managed privileges (PRIV) |
|
|
|
|
|
|
|
Trust determination for people granted access (TRUST) |
|
|
|
|
|
|
|
Credentials and authentication (CRED) |
|
|
|
|
|
|
|
Security-related training (BEHAVE) |
|
|
|
|
|
|
|
Component |
Not Started |
Initiation |
Development / Acquisition |
Testing |
Operations & Maintenance |
Other (please specify) |
|
Management of events (MNGEVT) |
|
|
|
|
|
|
|
Operate, monitor, and improve (OMI) |
|
|
|
|
|
|
|
Design and build-in security (DBS) |
|
|
|
|
|
|
|
Boundary protection (BOUND) |
|
|
|
|
|
|
|
Supply chain risk management (SCRM) |
|
|
|
|
|
|
|
Ongoing authorization (OA) |
|
|
|
|
|
|
|
Component |
Not Started |
Initiation |
Development/ Acquisition |
Testing |
Operations & Maintenance |
Other (please specify) |
|
Discovery / classification (DISC) |
|
|
|
|
|
|
|
Data protection (PROT) |
|
|
|
|
|
|
|
Data loss prevention (DLP) |
|
|
|
|
|
|
|
Data breach/spillage mitigation (MIT) |
|
|
|
|
|
|
|
Information rights management (IRM) |
|
|
|
|
|
|
What factors, if any, have had a substantially positive or negative impact on your agency’s rollout of the components listed in question 5?
a. What factors, if any, have had a substantially positive or negative impact on your agency’s rollout of the components listed in question 5?
Section B: Program Performance
6. How helpful, if at all, was the CDM program in reducing the threat surface of your agency? (Select one response.)
Extremely helpful
Very helpful
Moderately helpful
Somewhat helpful
Not at all helpful
No opinion
a. What are some examples of how the CDM program helped or did not help reduce the threat surface of your agency?
7. Has the CDM program made the overall cybersecurity posture of your agency better, worse, or has it stayed the same? (Select one response.)
Much better
Somewhat better
Stayed the same
Somewhat worse
Much worse
No opinion
a. What are some examples of how the CDM program has made your agency’s overall cybersecurity posture better, worse, or stay the same?
8. How much has the CDM program improved your agency’s cybersecurity incident response capabilities, if at all? (Select one response.)
Greatly improved
Moderately improved
Somewhat improved
Did not improve
No opinion
a. What are some examples of how the CDM program has improved or not improved your agency’s cybersecurity incident response capabilities?
9. How helpful, if at all, is the CDM program at providing outcomes that allow your agency to manage risk that aligns with each of the following functions of the NIST Cybersecurity Framework? (Select one response per row.)
|
|
Extremely helpful |
Very helpful |
Moderately helpful |
Somewhat helpful |
Not at all helpful |
No opinion |
|
Identify |
|
|
|
|
|
|
|
Protect |
|
|
|
|
|
|
|
Detect |
|
|
|
|
|
|
|
Respond |
|
|
|
|
|
|
|
Recover |
|
|
|
|
|
|
a. Is there any context related to your helpfulness ratings above that you’d like to share?
10. From your perspective, how helpful, if at all, is the Agency-Wide Adaptive Risk Enumeration (AWARE) score in prioritizing your agency’s cybersecurity risks? (Select one response.)
Extremely helpful
Very helpful
Moderately helpful
Somewhat helpful
Not at all helpful
No opinion
a. How does the AWARE score influence your agency’s risk assessment or analysis program, if at all?
11. Overall, to what extent has the CDM program delivered a positive return on investment for your agency? (Select one response.)
Large extent
Moderate extent
Small extent
No extent
No opinion
12. What value, if any, is there in enabling CISA access via the persistent access capability (PAC)? (Select one response.)
High value
Moderate value
Low value
No value
No opinion
Not applicable
13. Approximately how often does your agency use CDM tools to perform automated asset discovery? (Select one response.)
Every 1 – 7 days
Every 8 – 14 days
Every 15 – 28 days
Other, please specify: _____________
14. Approximately how often does your agency use CDM tools to perform vulnerability enumeration on managed endpoints? (Select one response.)
Every 1 – 7 days
Every 8 – 14 days
Every 15 – 28 days
Other, please specify: _____________
15. On average, how many hours does it take to automatically ingest discovered vulnerability enumeration results into the CDM Agency Dashboard? (Select one response.)
1 – 24 hours
25 – 48 hours
49 – 72 hours
73 – 96 hours
Other, please specify: _____________
Section C: CDM and Federal Information Security Modernization Act (FISMA) Reporting Requirements
16. On average, how would you rate the quality of data ingested into your CDM dashboard? (Select one response.)
Extremely reliable
Very reliable
Moderately reliable
Somewhat reliable
Not at all reliable
No opinion
a. How are you measuring the quality of data?
17. In the CDM program’s current state, how helpful, if at all, does your agency find the program in supporting FISMA reporting requirements? (Select one response.)
Extremely helpful
Very helpful
Moderately helpful
Somewhat helpful
Not at all helpful
No opinion
a. What are some of the reasons for your usefulness rating above?
18. If applicable, approximately what percent of the time do you have to manually edit incorrect data when submitting feeds through CyberScope?
___________ % of the time
[ ] Not applicable
a. What concerns, if any, does your agency have with data quality that relate to the dashboard, FISMA metrics, or other factors that affect your answer above?
Section D: CDM Usage in other Cyber Initiatives
19. How helpful, if at all, are the CDM tools at each of the following? (Select one response per row.)
|
|
Extremely helpful |
Very helpful |
Moderately helpful |
Somewhat helpful |
Not at all helpful |
No opinion |
|
Zero trust architecture |
|
|
|
|
|
|
|
Visibility into cloud assets |
|
|
|
|
|
|
|
Endpoint detection and response |
|
|
|
|
|
|
|
Insight into operational technology[35] |
|
|
|
|
|
|
|
Managing internet of things devices |
|
|
|
|
|
|
|
TIC 3.0[36] modernization |
|
|
|
|
|
|
Section E: Opportunities to Improve CDM
20. How satisfied or dissatisfied is your agency with the CISA CDM program management office (PMO)’s receptiveness to concerns raised by your agency about the CDM program? (Select one response.)
Very satisfied
Somewhat satisfied
Neither satisfied nor dissatisfied
Somewhat dissatisfied
Very dissatisfied
No opinion
I have not raised concerns to the PMO (SKIP to question 22.)
a. What has been your agency’s experience with the PMO, including issues you may have discussed involving CISA?
b. What has been your agency’s experience with the PMO, including issues you may have discussed involving the integrator?
21. How satisfied or dissatisfied is your agency with the CISA CDM PMO’s ability to resolve concerns raised by your agency? (Select one response.)
Very satisfied
Somewhat satisfied
Neither satisfied nor dissatisfied
Somewhat dissatisfied
Very dissatisfied
No opinion
I have not raised concerns to CISA CDM PMO (SKIP to question 22).
a. Approximately what percent of the time have resolved concerns reappeared?
___________ %
22. Since August 2023, has your agency experienced any of the challenges below with the CDM program? (Select one response per row.)
|
Challenge |
Yes |
No |
I don’t know |
|
External (integrator/CISA) staff turnover |
|
|
|
|
Internal (agency) staff turnover |
|
|
|
|
Data integration and quality issues |
|
|
|
|
Funding |
|
|
|
|
Lack of program flexibility |
|
|
|
|
Duplicate or missing hardware inventories |
|
|
|
|
Operating & maintaining the CDM solution |
|
|
|
|
Lack of integrator staff experience |
|
|
|
a. In your agency’s opinion, which challenges are the most important to address?
23. How helpful would it be for CDM to implement the items below in the future? (Select one response per row.)
|
|
Extremely helpful |
Very helpful |
Moderately helpful |
Somewhat helpful |
Not at all helpful |
No opinion |
|
Additional data points in the dashboard |
|
|
|
|
|
|
|
Additional training for staff |
|
|
|
|
|
|
|
Leveraging generative artificial intelligence |
|
|
|
|
|
|
|
Asset discovery in the cloud |
|
|
|
|
|
|
|
Automated processes |
|
|
|
|
|
|
|
Additional flexibility around closing gaps in implementation |
|
|
|
|
|
|
a. Which items in question 23 are the most important to your agency?
b. Are there any other important items for CDM to implement?




Jennifer R. Franks at FranksJ@gao.gov
In addition to the individual named above, Jeffrey Knott (Assistant Director), Kevin Smith (Analyst-in-Charge), Amanda Andrade, Brandon Berney, Tasha Beyzavi, Chris Businsky, Donna Epler, Nolan Metcalf, Evan Nelson Senie, Brandon Sanders, Claire Saint-Rossy, and Walter Vance made key contributions to this report.
The Government Accountability Office, the audit, evaluation, and investigative arm of Congress, exists to support Congress in meeting its constitutional responsibilities and to help improve the performance and accountability of the federal government for the American people. GAO examines the use of public funds; evaluates federal programs and policies; and provides analyses, recommendations, and other assistance to help Congress make informed oversight, policy, and funding decisions. GAO’s commitment to good government is reflected in its core values of accountability, integrity, and reliability.
Obtaining Copies of GAO Reports and Testimony
The fastest and easiest way to obtain copies of GAO documents at no cost is through our website. Each weekday afternoon, GAO posts on its website newly released reports, testimony, and correspondence. You can also subscribe to GAO’s email updates to receive notification of newly posted products.
Order by Phone
The price of each GAO publication reflects GAO’s actual cost of production and distribution and depends on the number of pages in the publication and whether the publication is printed in color or black and white. Pricing and ordering information is posted on GAO’s website, https://www.gao.gov/ordering.htm.
Place orders by calling (202) 512-6000, toll free (866) 801-7077,
or
TDD (202) 512-2537.
Orders may be paid for using American Express, Discover Card, MasterCard, Visa, check, or money order. Call for additional information.
Connect with GAO
Connect with GAO on X,
LinkedIn, Instagram, and YouTube.
Subscribe to our Email Updates. Listen to our Podcasts.
Visit GAO on the web at https://www.gao.gov.
To Report Fraud, Waste, and Abuse in Federal Programs
Contact FraudNet:
Website: https://www.gao.gov/about/what-gao-does/fraudnet
Automated answering system: (800) 424-5454
Media Relations
Sarah Kaczmarek, Managing Director, Media@gao.gov
Congressional Relations
A. Nicole Clowers, Managing Director, CongRel@gao.gov
General Inquiries
[1]The Federal Information Security Modernization Act of 2014 (FISMA 2014), Pub. L. No. 113-283, 128 Stat. 3073 (Dec. 18, 2014), largely superseded the Federal Information Security Management Act of 2002 (FISMA 2002), Title III of Pub. L. No. 107-347, 116 Stat. 2899, 2946 (Dec. 17, 2002). As used in this report, FISMA refers both to FISMA 2014 and those provisions of FISMA 2002 that were either incorporated into FISMA 2014 or were unchanged and continue in full force and effect.
[2]44 U.S.C. § 3551(4) notes that one purpose of FISMA is to “provide a mechanism for improved oversight of federal agency information security programs, including through automated security tools to continuously diagnose and improve security.”
[3]The goals of the CDM program are to (1) decrease agency threat surface, (2) increase visibility into the cybersecurity posture of agencies, (3) improve agencies’ abilities to respond to cybersecurity incidents, and (4) streamline FISMA reporting. A threat surface consists of all hardware and software that may be exposed to compromise due to insecure configurations or known vulnerabilities. Keeping threat surfaces as small as possible is a basic security measure.
[4]GAO, Cybersecurity: DHS and Selected Agencies Need to Address Shortcomings in Implementation of Network Monitoring Program, GAO‑20‑598 (Washington, D.C.: Aug. 18, 2020).
[5]The 23 civilian Chief Financial Officers Act of 1990 agencies are the Departments of Agriculture, Commerce, Education, Energy, Health and Human Services, Homeland Security, Housing and Urban Development, the Interior, Justice, Labor, State, Transportation, the Treasury, and Veterans Affairs; the Environmental Protection Agency; General Services Administration; National Aeronautics and Space Administration; National Science Foundation; Nuclear Regulatory Commission; Office of Personnel Management; Small Business Administration; Social Security Administration; and the U.S. Agency for International Development. We did not include the Department of Defense in our review, because the Department of Defense is not covered by the CDM program.
[6]The CDM program groups together agencies for which an integrator (contractor) is assigned to perform implementation work.
[7]A threat surface consists of all hardware and software that may be exposed to compromise due to insecure configurations or known vulnerabilities. Keeping threat surfaces as small as possible is a basic security measure.
[8]We received responses from each of the 23 civilian CFO Act agencies.
[9]In our survey, and within this report, we use a Likert scale to rate agency agreement with a particular topic or question. A Likert scale is a survey question that asks respondents to rate agreement with a statement or question. For our survey the scale offers ratings of extremely, very, somewhat, moderately, not at all, and no opinion.
[10]Zero trust architecture is a set of cybersecurity principles that are founded on the concept that no actor, system, network, or services operating outside of, or within, an organization’s security perimeter should be trusted. Instead, the principles suggest that organizations must verify anything and everything that attempts to establish access to their systems, services, and networks.
[11]EDR combines real-time continuous monitoring and collection of endpoint data (for example, networked computing devices such as workstations, mobile phones, and servers) with rules-based automated response and analysis capabilities. EDR provides increased visibility necessary to respond to advanced forms of cybersecurity threats.
[12]Cloud computing provides agencies with potential opportunities to obtain IT services more efficiently. However, if not effectively implemented, it also poses cybersecurity risks. Other relevant initiatives that we did not include in our scope include, for example, the Trusted Internet Connections (TIC) program, internet of things devices, and operational technology devices. We did not include these initiatives because CISA and OMB did not state that they were among the key initiatives that CDM should directly support.
[13]Office of Management and Budget, Moving the U.S. Government Toward Zero Trust Cybersecurity Principles, M-22-09 (Washington, D.C.: Jan. 26, 2022).
[14]Office of Management and Budget, Improving Detection of Cybersecurity Vulnerabilities and Incidents on Federal Government Systems through Endpoint Detection and Response, M-22-01 (Washington, D.C.: Oct. 8, 2021).
[15]OMB’s zero trust strategy discusses the use of CDM to support cloud architecture.
[16]GAO, Evidence-Based Policymaking: Practices to Help Manage and Assess the Results of Federal Efforts, GAO‑23‑105460 (Washington, D.C.: July 12, 2023).
[17]FISMA requires agencies to report annually to the heads of OMB and DHS, certain congressional committees, and GAO on the adequacy and effectiveness of their information security policies and procedures. OMB and DHS work with interagency partners to develop the Chief Information Officer FISMA metrics, which are intended to be used by the agencies, OMB, and DHS to track agencies’ progress in implementing cybersecurity capabilities. Further, FISMA requires OMB to report annually, in consultation with DHS, on the effectiveness of agency information security policies and practices.
[18]The CDM program is used government-wide by civilian agencies in addition to the 23 agencies selected for our review.
[19]Agencies participating in the program’s shared services offering, however, have their tools and maintenance covered in perpetuity. The shared services offering provides non-CFO Act agencies with access to CDM capabilities, leveraging an approach that is tailored to small and micro-agencies.
[20]Cybersecurity and Infrastructure Security Agency, CDM Technical Capabilities Volume 2, v. 2.5 (Arlington, VA: July 2023).
[21]Office of Management and Budget, Fiscal Year 2024 Guidance on Federal Information Security and Privacy Management Requirements, M-24-04 (Washington, D.C.: Dec. 4, 2023). M-24-04 was subsequently rescinded by M-25-04, which repeats the obligations in M-24-04.
[22]Office of Management and Budget, Federal Zero Trust Strategy, M-22-09.
[23]Office of Management and Budget, Endpoint Detection and Response, M-22-01.
[25]Operations and maintenance refers to the day-to-day operations of a capability, as opposed to, for example, capability development.
[26]CISA officials stated that activities associated with pilots would depend on enactment of agency budgets.
[27]According to CISA, data quality activities are an ongoing and continuous responsibility shared between agencies and CISA under established processes. CISA does not have the capabilities or authority to operate within each participating agency’s IT environment, and therefore relies on transparent and timely cooperation to rectify any perceived data quality issues raised by agencies’ stakeholders.
[29]Office of Management and Budget, Federal Zero Trust Strategy, M-22-09.
[30]Officials from three agencies considered CDM to not be helpful at all. Officials from five agencies had no opinion.
[31]According to CISA, technologies that fulfill EDR capability requirements may also additionally perform hardware asset management and software asset management functionality and satisfy those capability requirements. For more information, see: Cybersecurity and Infrastructure Security Agency, CDM Technical Capabilities Volume 2, v. 2.5 (Arlington, VA: July 2023).
[32]M-22-01.
[33]Office of Management and Budget, Federal Zero Trust Strategy, M-22-09.
[34]Two agencies reported that they had not raised issues to the PMO and were excluded from the count.
[35] (i.e., programmable systems or devices that interact with the physical environment, e.g., physical access control, transportation, environmental monitoring, and measurement systems)
[36] Trusted Internet Connections 3.0
