HIGH-RISK SERIES
Heightened Attention Could Save Billions More and Improve Government Efficiency and Effectiveness
Report to Congressional Committees
United States Government Accountability Office
View GAO-25-107743. For more information, contact Michelle Sager at (202) 512-6806 or SagerM@gao.gov.
Highlights of GAO-25-107743, a report to congressional committees
Heightened Attention Could Save Billions More and Improve Government Efficiency and Effectiveness
Why GAO Did This Study
The federal government is one of the world’s largest and most complex entities. About $6.8 trillion in outlays in fiscal year 2024 funded a broad array of programs and operations. GAO’s High-Risk Series identifies government operations with serious vulnerabilities to fraud, waste, abuse, and mismanagement, or in need of transformation.
This biennial update describes the status of high-risk areas, outlines actions that are needed to assure further progress, and identifies a new high-risk area needing attention by the executive branch and Congress.
GAO uses five criteria to assess progress in addressing high-risk areas: (1) leadership commitment; (2) agency capacity; (3) an action plan; (4) monitoring efforts; and (5) demonstrated progress. Ratings are based on analysis of actions taken up to the end of the 118th Congress.
Efforts to address high-risk issues have contributed to hundreds of billions of dollars saved. Over the past 19 years (fiscal years 2006-2024), these financial benefits totaled nearly $759 billion or an average of $40 billion per year.
What GAO Recommends
Executive branch agencies need to address thousands of open GAO recommendations to bring about lasting solutions to the 38 high-risk areas.
Continued congressional oversight is essential to achieve greater progress and legislation is needed in some cases. Congress also should consider requiring that interagency groups formed to address these challenges use leading practices for collaboration.
What GAO Found
Since GAO’s 2023 update to the High-Risk List, Congress and executive branch agencies have taken actions resulting in notable improvements across the 37 high-risk areas. These efforts over the last two years resulted in about $84 billion in financial benefits. However, the progress made overall varied. Ten areas improved and three regressed, while the others maintained their position, were rated for the first time, or were newly added, as shown on page 5. Lasting solutions to high-risk problems save billions of dollars, improve service to the public, and increase government performance and accountability.
New Area: Improving the Delivery of Federal Disaster Assistance
Natural disasters have become costlier and more frequent. In 2024, there were 27 disasters with at least $1 billion in economic damages. Overall, these events resulted in 568 deaths and significant economic effects on the affected areas. Their frequency and intensity have severely strained the Federal Emergency Management Agency (FEMA) and its workforce.
Recent natural disasters—including wildfires in Southern California and hurricanes in the Southeast—demonstrate the need for federal agencies to deliver assistance as efficiently and effectively as possible and reduce their fiscal exposure.

The federal approach to disaster recovery is fragmented across over 30 federal entities. So many entities involved with multiple programs and authorities, differing requirements and timeframes, and limited data sharing across entities could make it harder for survivors and communities to navigate federal programs.
FEMA and other federal entities—including Congress—need to address the nation’s fragmented federal approach to disaster recovery. Attention is also needed to improve processes for assisting survivors, invest in resilience, and strengthen FEMA’s disaster workforce and capacity.
Several Areas Critical to Better Managing the Cost of Government
|
|
Reducing Billions in Significant Improper Payments and Fraud |
Since 2003, federal agencies have reported about $2.8 trillion in estimated improper payments, including over $150 billion government-wide in each of the last 7 years. These figures do not represent a full accounting of improper payments because agencies have not reported estimates for some programs as required. For example, we found that agencies failed to report fiscal year 2023 improper payment estimates for nine risk-susceptible programs.
The areas on the High-Risk List include programs that represented about 80 percent of the total government-wide reported improper payment estimate. These include two of the fastest-growing programs—Medicare and Medicaid—as well as the unemployment insurance system and the Earned Income Tax Credit. While agencies and the Department of the Treasury are taking some steps to address this issue, much more needs to be done to control billions of dollars in overpayments and prevent fraud. Implementation of GAO’s recommendations by agencies and the Congress would help achieve better program integrity.
|
|
Closing Large Gaps in Revenue Owed to the Government |
In 2024, the Internal Revenue Service (IRS) projected that the gross tax gap—the difference between taxes owed and taxes paid on time—was $696 billion for tax year 2022. IRS estimated that it will collect an additional $90 billion through late payments and enforcement actions, leaving an estimated $606 billion net tax gap. Also, IRS is continually addressing billions of dollars of attempted tax fraud through identity theft. Further, the Department of the Interior does not have reasonable assurance that it is collecting the entirety of the billions owed on oil and gas leases on federal lands. Actions by federal agencies and Congress on related GAO recommendations can help significantly to close these gaps and improve the government’s fiscal position.
|
|
Better Controlling Cost Growth and Schedule Delays in High Dollar Value Procurements |
The government has great difficulty in controlling the costs of major acquisitions in its more than $750 billion procurement portfolio. This includes procurements critical to national defense, nuclear weapon systems modernization and clean up, space programs, and health care to veterans. Many major acquisitions by agencies such as the Department of Defense (DOD), the Department of Energy, the National Aeronautics and Space Administration, and the Department of Veterans Affairs (VA) have experienced cost growth, schedule delays, or both. Implementation of GAO’s recommendations, which include more consistently applying leading practices, could yield billions in savings and provide more timely delivery.
|
|
Rightsizing the Government’s Property Holdings Could Generate Substantial Savings |
The federal government is one of the nation’s largest property holders. Annual maintenance and operating costs for its 277,000 buildings exceeded $10.3 billion in fiscal year 2023. Managing real property was designated high risk in 2003 because of large amounts of underused property and the great difficulty in disposing of unneeded holdings and ensuring the safety of workers and visitors. Costliness and underuse of government property holdings have been exacerbated by the recent use of telework and growing amounts of deferred maintenance, which rose from $170 billion in 2017 to $370 billion in 2024.
GAO recommended more appropriate utilization benchmarks be established to guide better and more timely property management. Also, lessons need to be applied from recent failed attempts to expedite disposals to establish a more viable process. Efforts are also needed to better manage and maintain property.
|
|
Achieving Greater Financial Management Discipline at DOD |
DOD is the only major federal agency to have never achieved an unmodified “clean” opinion on its financial statements. The department is committed to the goal of achieving a clean opinion on its statements and has made important progress in reaping several financial and operational benefits. A clean opinion was recently obtained by the Marine Corps, in addition to several smaller components. DOD needs to redouble its efforts to revamp financial management systems, more promptly fix problems identified by its auditors, and focus more on ensuring a well-qualified workforce to attain proper accountability and potential savings.
Harnessing Modern Information Technology to Improve Services and Programs
The federal government spends more than $100 billion annually on IT, with the vast majority of this spent on operations and maintenance of existing systems rather than new technology. Currently, the government, in many cases, is carrying out critical missions with decades-old legacy technology that also carries tremendous security vulnerabilities. Many attempts to implement new systems have too often run far over budget, experienced significant delays, and delivered far fewer improvements than promised. Recent challenges at the Federal Aviation Administration (FAA), Department of Education, and VA vividly illustrate this situation.
· FAA has experienced increasing challenges with aging air traffic control systems in recent years and has been slow to modernize the most critical and at-risk systems. A 2023 operational risk assessment determined that of FAA’s 138 systems, 51 (37 percent) were unsustainable with significant shortages in spare parts, shortfalls in sustainment funding, little to no technology refresh funding, or significant shortfalls in capability. An additional 54 (39 percent) were potentially unsustainable.
· The Department of Education's Office of Federal Student Aid did not adequately plan for its deployment of the Free Application for Federal Student Aid (FAFSA) Processing System. The initial rollout of the new system was delayed several times, faced several critical technical issues, and experienced very poor customer service. This contributed to about 9 percent fewer high school seniors and other first-time applicants submitting a FAFSA, as of August 25, 2024.
· After three unsuccessful attempts between 2001 and 2018, VA initiated a fourth effort—the electronic health record (EHR) modernization program—to replace its health records system. In 2022, the Institute for Defense Analysis estimated that EHR modernization life cycle costs would total $49.8 billion—$32.7 billion for 13 years of implementation and $17.1 billion for 15 years of sustainment. VA remains in the early stages of deploying its new EHR system across 160 locations. As of December 2024, VA deployed the EHR system to just six of its locations and plans to deploy it at four more locations in 2026. There are over 160 remaining locations for EHR implementation.
These are examples of poor performance that led GAO to designate Improving IT Acquisitions and Management as a government-wide high-risk area in 2015. There have been some improvements, including closing unneeded data centers, which saved billions of dollars. Congressional oversight by the House Committee on Oversight and Government Reform, Subcommittee on Government Operations, has helped spur improvements and included exhortations to have Chief Information Officers (CIO) more involved.
Of the 1,881 recommendations made by GAO for this high-risk area since 2010, 463 remained open as of January 2025. Agency leaders need to give this area a higher priority and provide their CIOs necessary authorities and support if the government is ever to reap the benefits of modern technology.
Expediting the Pace of Cybersecurity and Critical Infrastructure Protections
While improvements have been made and efforts continue, the government is still not operating at a pace commensurate with the evolving grave cybersecurity threats to our nation’s security, economy, and well-being. State and non-state actors are attacking our government and private-sector systems thousands of times each day. In addition to national security and intellectual property, systems supporting daily life of the American people are at risk, including safe water, ample supply of energy, reliable and secure telecommunications, and our financial services.
GAO has made 4,387 related recommendations since 2010. While 3,623 have been implemented or closed, 764 have not been fully implemented. Also, greater federal efforts are needed to better understand the status of private sector technological developments with cybersecurity implications—such as artificial intelligence— and to continue to enhance public and private sector coordination.
Seizing Opportunities to Better Protect Public Health and Reduce Risk
Several of GAO’s high-risk areas focus on addressing critical weaknesses in public health efforts. GAO’s recommendations focus on
· ensuring the Department of Health and Human Services significantly elevates its ability to provide leadership and coordination of public health emergencies;
· providing the Food and Drug Administration with a much greater capacity to (1) inspect foreign drug manufacturers that produce many of the drugs consumed by Americans and (2) take stronger actions to address persistent drug shortages, including cancer therapies;
· improving the timeliness and quality of care given to our veterans, including mental health and suicide prevention, especially in rural areas;
· ensuring better health care by the Indian Health Service to Tribes and their members;
· providing national leadership to prevent drug abuse and further reduce overdose deaths; and
· ensuring the Environmental Protection Agency provides more timely reviews of potentially toxic chemicals before they are introduced into commercial production and widespread public use.
There is also a need for a more comprehensive approach to food safety to address fragmentation among 15 different federal agencies and at least 30 federal laws. While the United States has one of the safest food supplies in the world, every year millions of people are sickened by foodborne illnesses, tens of thousands are hospitalized, and thousands die. A more proactive, coordinated approach that takes greater advantage of modern technology would be in the best interest of Americans and would lead to a more efficient government.
Other Concerning High-Risk Areas
|
|
Modernizing our Financial Regulatory Systems |
Actions are needed to strengthen oversight of financial institutions and address regulatory gaps. The March 2023 bank failures and rapid adoption of emerging technologies in the marketplace have highlighted continued challenges in the regulatory system since GAO initially designated this area as high-risk in 2009, during the financial crisis. In particular, the Federal Reserve should improve procedures so that decisions to escalate supervisory concerns happen in a timely manner and Congress should consider designating a federal regulator for certain crypto asset markets, as we recommended.
|
|
Resolving the Federal Role in Housing Finance |
There is an essential need for Congress to clarify the federal role for Fannie Mae and Freddie Mac, two private sector entities that provide underwriting for the U.S. mortgage market. They are still in federal conservatorship from the 2008 global financial crisis with no clear path forward. The other key federal players, Ginnie Mae and the Federal Housing Administration, have had their portfolios greatly expanded to $2.6 trillion and $1.4 trillion respectively. Consequently, the federal government is greatly exposed to a downturn in the housing market.
|
|
Addressing Long-Standing Issues with the Bureau of Prisons |
Prison buildings are deteriorating and in need of repair and maintenance, while facilities are understaffed, putting both incarcerated people and staff at risk. Moreover, efforts to prevent recidivism have not been thoroughly evaluated, undermining a key goal to help incarcerated people make a successful transition into society once released. The Bureau of Prisons has made some progress, but much more needs to be done.
|
|
Fixing the United States Postal Service’s (USPS) Outdated Business Model |
Congress acted to alleviate certain fiscal pressures and USPS is trying to reduce costs, but it is still losing money ($16 billion in fiscal years 2023 and 2024) and has extensive liabilities and debt ($181 billion in fiscal year 2024). USPS estimates that the fund supporting postal retiree benefits will be depleted in fiscal year 2031. At that point, USPS would be required to pay its share of retiree health care premiums, which USPS projects to be about $6 billion per year. There is a fundamental tension between the level of service Congress expects and what revenue USPS can reasonably be expected to generate. Congress needs to establish what services it wants USPS to provide and negotiate a balanced funding arrangement.
|
|
Addressing the Government’s Human Capital Challenges |
Twenty areas are on GAO’s High-Risk List in part due to skills gaps or an inadequate number of staff. Moreover, the personnel security clearance system is not yet being managed in the best manner to ensure that people are adequately screened to handle sensitive information.
Icon sources: GAO, USPS, and Icons-Studio/stock.adobe.com.
GAO’s 2025 High-Risk List, Changes Since 2023
|
High-risk area |
Change since 2023 |
|
Improving the Delivery of Federal Disaster Assistancea,b (area not rated because it is newly added) |
n/a |
|
Funding the Nation’s Surface Transportation Systema (area not rated because it primarily involves congressional action) |
n/a |
|
HHS Leadership and Coordination of Public Health Emergenciesb (area rated for the first time) |
n/a |
|
Strengthening Management of the Federal Prison System (area rated for the first time) |
n/a |
|
Unemployment Insurance Systema,b (area rated for the first time) |
n/a |
|
DOD Approach to Business Transformation |
↑ |
|
DOD Business Systems Modernization |
↑ |
|
DOD Contract Management |
↑ |
|
Emergency Loans for Small Businesses |
↑ |
|
Government-wide Personnel Security Clearance Processa,b |
↑ |
|
National Efforts to Prevent, Respond to, and Recover from Drug Misuseb |
↑ |
|
National Flood Insurance Programa |
↑ |
|
Resolving the Federal Role in Housing Financea,b |
↑ |
|
U.S. Government’s Environmental Liabilitya,b |
↑ |
|
USPS Financial Viabilitya |
↑ |
|
DOD Weapon Systems Acquisitiona |
↓ |
|
Improving IT Acquisitions and Managementa,b |
↓ |
|
Managing Federal Real Propertyb |
↓ |
|
Acquisition and Program Management for DOE’s National Nuclear Security Administration and Office of Environmental Managementa |
● |
|
DOD Financial Management |
● |
|
Enforcement of Tax Lawsa |
● |
|
Ensuring the Cybersecurity of the Nationa,b |
● |
|
Improving and Modernizing Federal Disability Programsb |
● |
|
Improving Federal Management of Programs that Serve Tribes and Their Membersb |
● |
|
Improving Federal Oversight of Food Safetya,b |
● |
|
Limiting the Federal Government’s Fiscal Exposure by Better Managing Climate Change Risksa,b |
● |
|
Management of Federal Oil and Gas Resources |
● |
|
Managing Risks and Improving VA Health Care |
● |
|
Medicare Program and Improper Paymentsa |
● |
|
Modernizing the U.S. Financial Regulatory Systema,b |
● |
|
NASA Acquisition Management |
● |
|
Protecting Public Health Through Enhanced Oversight of Medical Products |
● |
|
Protecting Technologies Critical to U.S. National Securityb |
● |
|
Strategic Human Capital Managementb |
● |
|
Strengthening Department of Homeland Security IT and Financial Management Functions |
● |
|
Strengthening Medicaid Program Integritya,b |
● |
|
Transforming EPA’s Process for Assessing and Managing Chemical Risks |
● |
|
VA Acquisition Management |
● |
Legend: h indicates area progressed on
one or more criteria since 2023; i indicates area declined on one or more
criteria since 2023;
● indicates no change since 2023;
n/a = not applicable
Source: GAO. | GAO-25-107743
aLegislation is likely to be necessary to effectively address this high-risk area.
bCoordinated efforts across multiple entities are necessary to effectively address this high-risk area.
February 25, 2025
The Honorable Rand Paul, M.D.
Chairman
The Honorable Gary C. Peters
Ranking Member
Committee on Homeland Security and Governmental Affairs
United States Senate
The Honorable James Comer
Chairman
The Honorable Gerald E. Connolly
Ranking Member
Committee on Oversight and Government Reform
House of Representatives
Since the early 1990s, our high-risk program has focused attention on government operations with significant vulnerabilities to fraud, waste, abuse, and mismanagement or that need transformation to address economy, efficiency, or effectiveness challenges. This effort, supported by the Senate Committee on Homeland Security and Governmental Affairs and the House of Representatives Committee on Oversight and Government Reform, has brought much-needed attention to problems impeding effective government and costing billions of dollars each year.
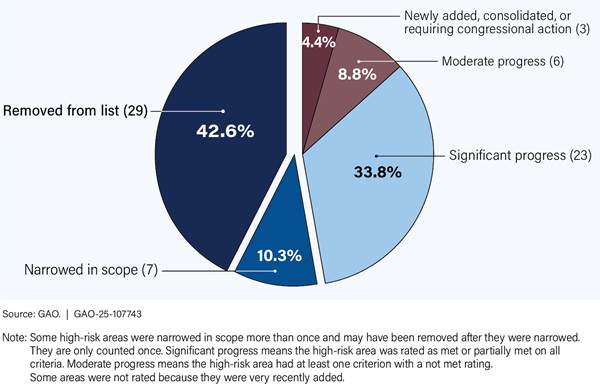
About 53 percent of high-risk areas identified over the years have either been removed from the list or narrowed in scope. Significant progress has been made on many other areas, as they have met or partially met all five criteria for removal (see fig. 1).
The federal government is one of the world’s largest and most complex entities. About $6.8 trillion in outlays in fiscal year 2024 funded a broad array of programs and operations.
Efforts to address high-risk issues have contributed to hundreds of billions of dollars saved. Over the past 19 years (fiscal years 2006 through 2024), these financial benefits totaled nearly $759 billion or an average of about $40 billion per year. Since our last update in 2023, we recorded approximately $84 billion in financial benefits as agencies took action to address high-risk areas. Progress on high-risk areas has also resulted in many other benefits that cannot be measured in dollar terms, such as improved service to the public and enhanced ability to achieve agency missions. Further progress to narrow or remove the 38 areas remaining on the High-Risk List can help save billions more dollars, improve services to the public, and increase government performance and accountability.
Congressional action, such as passing laws and holding hearings, is critical for making meaningful progress on high-risk areas. Table 1 lists examples of congressional actions that helped make progress on high-risk areas.
|
High-risk area |
Congressional actions |
|
HHS Leadership and Coordination of Public Health Emergencies |
Congress established the Office of Pandemic Preparedness and Response Policy in 2022 within the Executive Office of the President by enacting the Prepare for and Respond to Existing Viruses, Emerging New Threats, and Pandemics Act (PREVENT Pandemics Act).a This office, which launched in July 2023, is charged with coordinating federal activities to prepare for, and respond to, pandemic and other biological threats. |
|
The National Defense Authorization Act for Fiscal Year 2025 established the position of DOD Performance Improvement Officer in statute and gave the position responsibilities related to performance improvement, business reform and transformation efforts, and DOD’s Strategic Management Plan.b |
|
|
In 2022, Congress mandated that DOD establish a target goal for completing cleanup of sites contaminated by military munitions.c |
|
|
Congress held hearings in April and December 2024 on changes to the U.S. Postal Service’s delivery network, on-time delivery performance, financial viability, and implementation of the Postal Service Reform Act of 2022. |
|
|
Congress helped the Department of Defense (DOD) address some gaps in senior leadership and mitigate risks to its industrial base (the large collection of companies that provide supplies, parts, and manufacturing for DOD’s weapons systems). The Senate confirmed DOD’s first Assistant Secretary for Industrial Base Policy in March 2023, who issued DOD’s first National Defense Industrial Strategy in January 2024. Further, legislation, such as acquisition reforms required by the National Defense Authorization Act for Fiscal Year 2024, has prompted DOD to consider how to address structural barriers that impede its progress in making change, such as its requirements process.d |
|
|
In December 2023, the Senate confirmed the second National Cyber Director. The presence of this leadership should facilitate the high-level attention and coordination needed to address cyber threats and challenges facing the nation. |
|
|
Limiting the Federal Government’s Fiscal Exposure by Better Managing Climate Change Risks |
The National Defense Authorization Act for Fiscal Year 2024 directed DOD to incorporate the impact of military installation environmental resilience into certain guidance documents.e For example, guidance documents should define specific military installation resilience hazards—such as wind, wildfire, and flooding—to ensure consistent impact reporting across DOD. |
Source: GAO. | GAO‑25‑107743
aConsolidated Appropriations Act, 2023. Pub. L. No. 117-328, div. F, tit. II, 136 Stat. 4459, 5706 (2022).
bNational Defense Authorization Act for Fiscal Year 2025, Pub. L. No. 118-159, 902 (2024).
cNational Defense Authorization Act for Fiscal Year 2024, Pub. L. No. 118-31, 137 Stat. 136 (2023).
dJames M. Inhofe National Defense Authorization Act for Fiscal Year 2023, Pub. L. No. 117-263, 326, 136 Stat. 2395, 2518-19 (2022).
eNational Defense Authorization Act for Fiscal Year 2024, Pub. L. No. 118-31, 2857, 137 Stat. 136, 767 (2023).
Agency leaders took actions to implement our recommendations in some high-risk areas, resulting in significant financial benefits (see table 2).
|
High-risk area |
Executive actions |
|
To prevent potential fraud in the Paycheck Protection Program (PPP), the Small Business Administration (SBA) established additional controls for PPP loans, as we recommended. In June 2023, SBA reported that the agency prevented the funding of 174,000 potentially ineligible or fraudulent PPP applications (after they were initially approved by lenders), representing $3.6 billion in net potential savings. By applying similar controls to two other pandemic programs, SBA detected and prevented about 4,600 potentially ineligible or fraudulent Shuttered Venue Operators Grant Program applications since its launch in April 2021 and about 31,000 Restaurant Revitalization Fund applications since its launch in May 2021, representing $2.1 billion and $2.8 billion in net potential savings, respectively. SBA has continued to review and deny PPP forgiveness applications since January 2022, saving about $2.9 billion as of July 2023. |
|
|
The annual premiums collected by the National Flood Insurance Program are generally insufficient to cover high losses, especially in years of catastrophic flooding. As we recommended, Federal Emergency Management Agency adjusted its rate‑setting methodology in October 2021. This improved the accuracy of the premiums charged and reduced financial risk to taxpayers and the federal government, resulting in savings of $1.24 billion from fiscal years 2022 through 2024. |
|
|
In April 2024, the Department of Energy (DOE) and regulators at the Hanford Site in Washington State proposed an agreement under which DOE would treat millions of gallons of low-activity radioactive waste using grout instead of glass. We recommended in December 2021 that DOE analyze additional disposal options for this waste, including identifying facilities that could receive grouted low-activity waste from Hanford. We estimate that this approach will save about $7.5 billion if DOE can move forward as planned under a finalized agreement with Hanford regulators. In May 2024, the DOE’s Office of Environmental Management (EM) announced that it does not plan to resume construction of its $12 billion Pretreatment Facility at Hanford. We have repeatedly recommended that EM pause construction on the Pretreatment Facility until it resolved significant technical issues. EM plans to keep the facility in standby until at least 2029 while evaluating pretreatment options, saving $6 billion over 5 years. In March 2023, EM completed a program-wide strategy and reviewed opportunities to balance cleanup costs with health and environmental risks. This resulted in the decision to accelerate the cleanup of certain nuclear waste at EM’s Savannah River Site in South Carolina by an estimated 22 years, avoiding more than $2.4 billion in costs. |
|
|
The National Institute on Aging (NIA) initiated an IT project to improve research into Alzheimer’s disease by compiling and analyzing real world data. In March 2024, Congress cited our ongoing work that found the NIA’s project minimally met the four characteristics of a reliable cost estimate. Congress urged the agency to pause planned awards for the project. In light of our work and other developments in Alzheimer’s research, NIA decided not to fund the project in April 2024, resulting in reduced expenses of approximately $282 million over 6 years. |
|
|
The Internal Revenue Service (IRS) took actions to identify potentially ineligible COVID-19 related sick and family leave credit claims. This allowed IRS to recapture ineligible refunds and adjust taxes, resulting in additional collection of taxes of about $285.2 million as of March 2024. |
|
|
In November 2019, the Centers for Medicare & Medicaid Services (CMS) completed the phase-in of reduced payments for specific hospital outpatient services to more closely align with payments for the same services provided in physician practices, which our previous work supports.a CMS estimated the change saved the Medicare program about $864 million in fiscal year 2023. |
Source: GAO. | GAO‑25‑107743
a84 Fed. Reg. 61,142 (Nov. 12, 2019).
Substantial additional efforts are needed to achieve greater progress and to address backsliding in some high-risk areas since the 2023 update. Sustained congressional attention and executive branch leadership remain key to success.
This report describes (1) high-risk areas needing significant attention; (2) progress made addressing high-risk areas, the reasons for that progress, and the resulting benefits from agency and congressional actions; and (3) additional actions that are still needed. We identified one new high-risk area in 2025. This high-risk area—Improving the Delivery of Federal Disaster Assistance—is being added because of the increasing cost and complexity of federal support as disasters become more frequent and intense.
This update is based primarily on reports we issued before February 2025. High-risk area ratings are based on analysis of agency actions taken up through and including the 118th Congress, before the start of the 119th Congress and the new administration. We will continue to monitor and evaluate ongoing agency and congressional actions, which will be reflected in our 2027 high-risk update.
New High-Risk Area: Improving the Delivery of Federal Disaster Assistance
Natural disasters have become costlier and more frequent. In 2024, there were 27 disasters with at least $1 billion in economic damages. Overall, these events resulted in 568 deaths and significant economic effects on affected areas. Their frequency and intensity have severely strained the Federal Emergency Management Agency (FEMA) and its workforce.
Recent natural disasters—including wildfires in Southern California and hurricanes in the Southeast (see fig. 2)—demonstrate the need for federal agencies to deliver assistance as efficiently and effectively as possible and reduce their fiscal exposure. For fiscal years 2015 through 2024, appropriations for disaster assistance totaled at least $448 billion.[1] Additionally, in December 2024 the Disaster Relief Supplemental Appropriations Act, 2025, appropriated $110 billion in supplemental appropriations for disaster assistance.[2]

The federal approach to disaster recovery is fragmented across over 30 federal entities. So many entities involved with multiple programs and authorities, differing requirements and timeframes, and limited data sharing across entities could make it harder for survivors and communities to navigate federal programs.
FEMA and other federal entities—including Congress—need to address the nation’s fragmented federal approach to disaster recovery. Attention is also needed to improve processes for assisting survivors, invest in resilience, and strengthen FEMA’s disaster workforce and capacity.
High-Risk Areas Needing Significant Attention
While all high-risk areas should make more progress, the areas described below require significant attention. These areas feature emerging issues requiring government responses, large and rapidly growing costs, or a failure to make any progress in the past several years.
|
|
Reducing Billions in Significant Improper Payments and Fraud |
Several Areas Critical to Better Managing the Cost of Government
Since 2003, federal agencies have reported about $2.8 trillion in estimated improper payments, including more than $150 billion government-wide in each of the last 7 years (see fig. 3).[3] These figures do not represent a full accounting of improper payments because agencies have not reported estimates for some programs as required. For example, we found that agencies failed to report fiscal year 2023 improper payment estimates for nine risk-susceptible programs.[4]
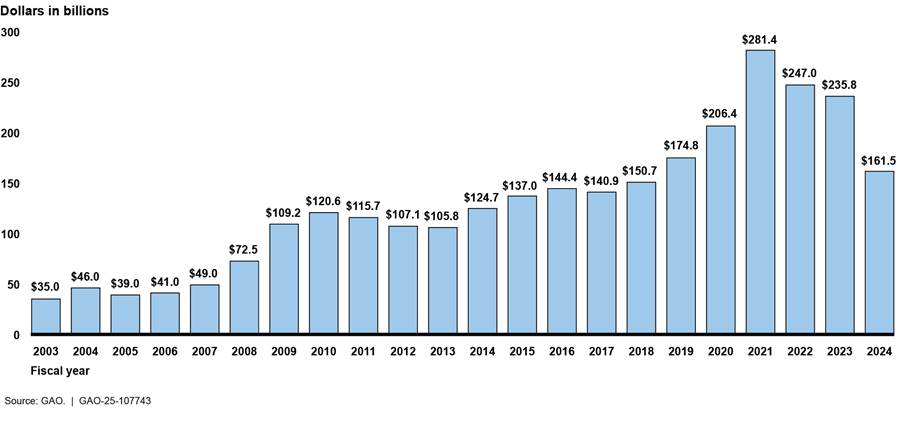
The areas on the High-Risk List include programs that represented about 80 percent of the total government-wide reported improper payment estimate for fiscal year 2023. These include two of the fastest-growing programs—Medicare and Medicaid—as well as the unemployment insurance system and the Earned Income Tax Credit. While agencies and the Department of the Treasury are taking some steps to address this issue, much more needs to be done to control billions of dollars in overpayments and prevent fraud. Implementation of our recommendations by agencies and the Congress would help achieve better program integrity.
|
|
Closing Large Gaps in Revenue Owed to the Government |
In 2024, the Internal Revenue Service (IRS) projected that the gross tax gap—the difference between taxes owed and taxes paid on time—was $696 billion for tax year 2022 (see fig. 4). IRS estimated that it will collect an additional $90 billion through late payments and enforcement actions, leaving an estimated $606 billion net tax gap.
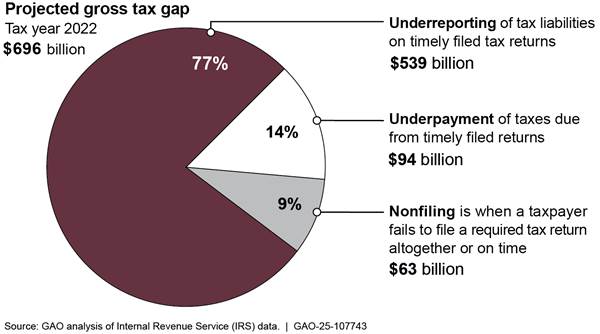
IRS is also continually addressing billions of dollars of attempted tax fraud through identity theft. Further, the Department of the Interior does not have reasonable assurance that it is collecting the entirety of the billions owed on oil and gas leases on federal lands. Actions by federal agencies and Congress on related GAO recommendations can help significantly to close these gaps and improve the government’s fiscal position.
|
|
Better Controlling Cost Growth and Schedule Delays in High Dollar Value Procurements |
The government has great difficulty in controlling the costs of high dollar value acquisitions in its more than $750 billion procurement portfolio. This includes procurements critical to national defense, nuclear weapon systems modernization and cleanup, space programs, and health care to veterans. Many major acquisitions by agencies such as the Department of Defense (DOD), the Department of Energy, the National Aeronautics and Space Administration (NASA), and the Department of Veterans Affairs (VA) have experienced cost growth, schedule delays, or both.
For example, NASA is developing eight projects which each exceed $2 billion in life-cycle costs, known as category 1 projects. Three of them were experiencing schedule delays and four exceeded their cost baseline as of mid-2024 (see fig. 5).
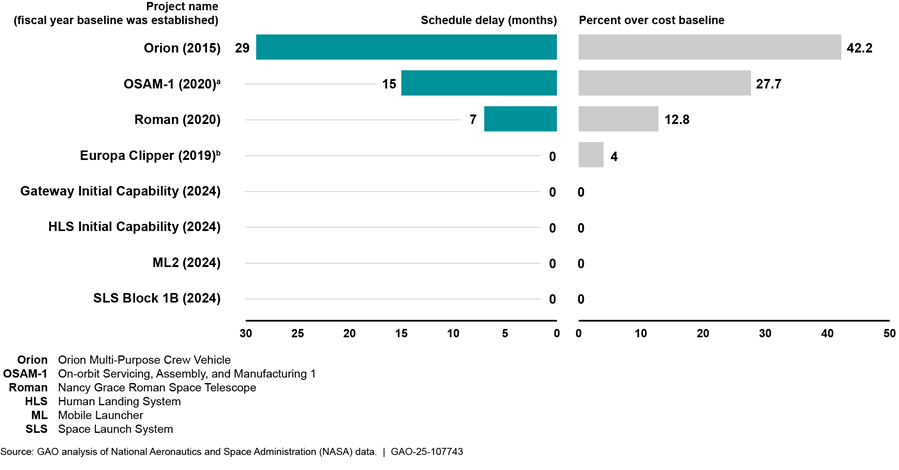
Note: Data are as of July 2024. The Commercial Crew Program, which is also a category 1 project, is excluded from this analysis because it has a tailored project life cycle and project management requirements and did not establish a baseline.
aNASA announced in March 2024 that it planned to discontinue OSAM-1 due to continued technical, cost, and schedule challenges, among other reasons. As of October 1, 2024, NASA was in the process of shutting down the project.
bThe Europa Clipper project launched 11 months ahead of its schedule baseline in October 2024.
Implementation of our recommendations, such as more consistently applying leading practices, could yield billions in savings and provide faster delivery of innovative capability.
|
|
Rightsizing the Government’s Property Holdings Could Generate Substantial Savings |
The federal government is one of the nation’s largest property holders. Annual maintenance and operating costs for its 277,000 buildings exceeded $10.3 billion in fiscal year 2023. Managing real property was designated high risk in 2003 because of large amounts of underused property and the great difficulty in disposing of unneeded holdings and ensuring safety of workers and visitors. Costliness and underuse of government property holdings have been exacerbated by the recent use of telework and growing amounts of deferred maintenance, which rose from $170 billion in 2017 to $370 billion in 2024 (see fig. 6).
Figure 6: Federal Civilian Agencies’ and U.S. Department of Defense Reported Estimates of Deferred Maintenance and Repairs, Fiscal Years 2017–2024
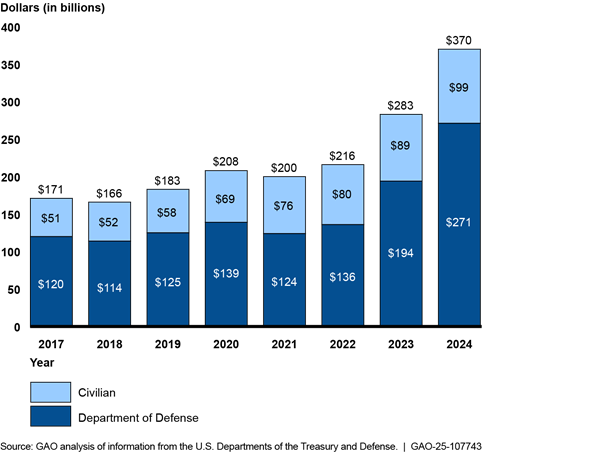
We recommended more appropriate utilization benchmarks be established to guide better and more timely property management. Also, lessons need to be applied from recent failed attempts to expedite disposals to establish a more viable process. Efforts are also needed to better manage and maintain property.
|
|
Achieving Greater Financial Management Discipline at DOD |
DOD is the only major federal agency to have never achieved an unmodified “clean” opinion on its financial statements. The department is committed to the goal of achieving a clean opinion on its statements and has made important progress in reaping several financial and operational benefits (see fig. 7).
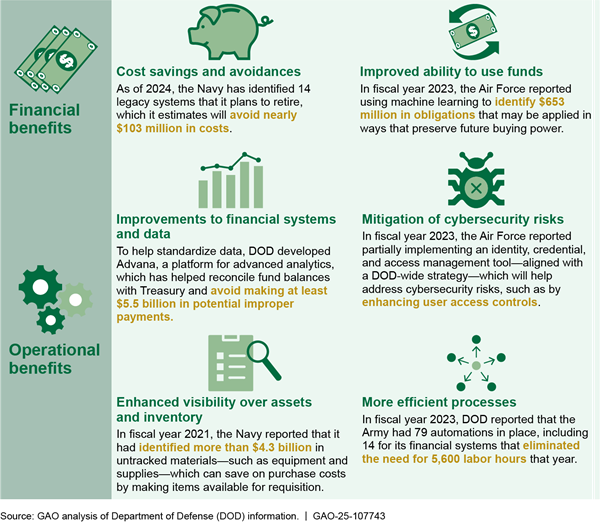
A clean opinion was recently obtained by the Marine Corps, in addition to several smaller components. DOD needs to redouble its efforts to revamp financial management systems, more promptly fix problems identified by its auditors, and focus more on ensuring a well-qualified workforce to attain proper accountability and potential savings.
Harnessing Modern Information Technology to Improve Services and Programs
The federal government spends over $100 billion annually on IT, with the vast majority of this spent on operations and maintenance of existing systems rather than new technology. Currently, the government, in many cases, is carrying out critical missions with decades-old legacy technology that also carries tremendous security vulnerabilities. Many attempts to implement new systems have too often run far over budget, experienced significant delays, and delivered far fewer improvements than promised. Recent challenges at the Federal Aviation Administration (FAA), Department of Education, and VA vividly illustrate this situation.
· FAA has been experiencing increasing challenges with aging air traffic control systems in recent years and has been slow to modernize the most critical and at-risk systems. A 2023 operational risk assessment determined that of FAA’s 138 systems, 51 (37 percent) were unsustainable with significant shortages in spare parts, shortfalls in sustainment funding, little to no technology refresh funding, or significant shortfalls in capability. An additional 54 (39 percent) were potentially unsustainable.
· The Department of Education’s Office of Federal Student Aid did not adequately plan for its deployment of the Free Application for Federal Student Aid (FAFSA) Processing System. The initial rollout of the new system was delayed several times and faced several critical technical issues and very poor customer service. This contributed to about 9 percent fewer high school seniors and other first-time applicants submitting a FAFSA, as of August 25, 2024.
· After three unsuccessful attempts between 2001 and 2018 to replace its health records system, VA initiated a fourth effort—the electronic health record (EHR) modernization program. In 2022, the Institute for Defense Analysis estimated that EHR modernization life cycle costs would total $49.8 billion—$32.7 billion for 13 years of implementation and $17.1 billion for 15 years of sustainment. As of December 2024, VA deployed the EHR system to just six of its locations and plans to deploy it at four more locations in 2026. There are over 160 remaining locations for EHR implementation.
These are examples of poor performance that led us to designate Improving IT Acquisitions and Management as a government-wide high-risk area in 2015. There have been some improvements, including closing unneeded data centers, which saved billions of dollars. Congressional oversight by the House Committee on Oversight and Government Reform, Subcommittee on Government Operations, has helped spur improvements and included exhortations to have Chief Information Officers (CIO) more involved.
Agencies need to urgently address nine critical actions associated with three major IT management challenges that we have identified (see fig. 8).
Figure 8: Nine Critical Actions Federal Agencies Need to Take to Address Three Major IT Management Challenges
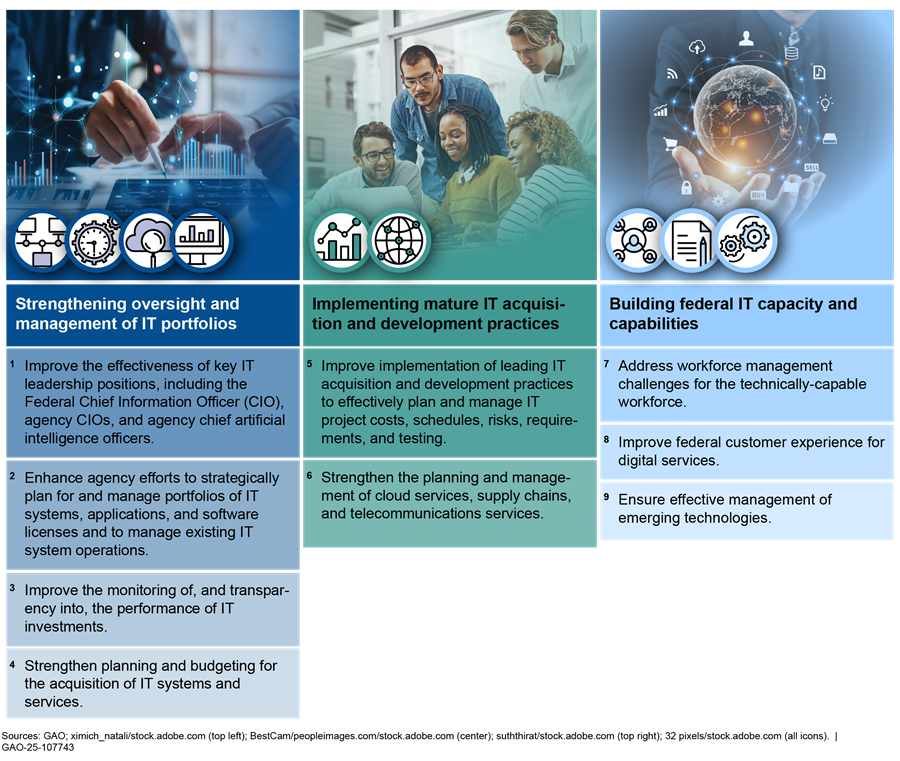
Of the 1,881 recommendations we made for this high-risk area since 2010, 463 remained open as of January 2025. Agency leaders need to give this area a higher priority and provide their CIOs necessary authorities and support if the government is ever to reap the benefits of modern technology.
Expediting the Pace of Cybersecurity and Critical Infrastructure Protections
While improvements have been made and efforts continue, the government is still not operating at a pace commensurate with the evolving grave cybersecurity threats to our nation’s security, economy, and well-being. State and non-state actors are attacking our government and private-sector systems thousands of times each day. In addition to national security and intellectual property, systems supporting daily life of the American people are at risk, including safe water, ample supply of energy, reliable and secure telecommunications, and our financial services.
Agencies need to urgently address 10 critical actions associated with four major cybersecurity challenges (see fig. 9).
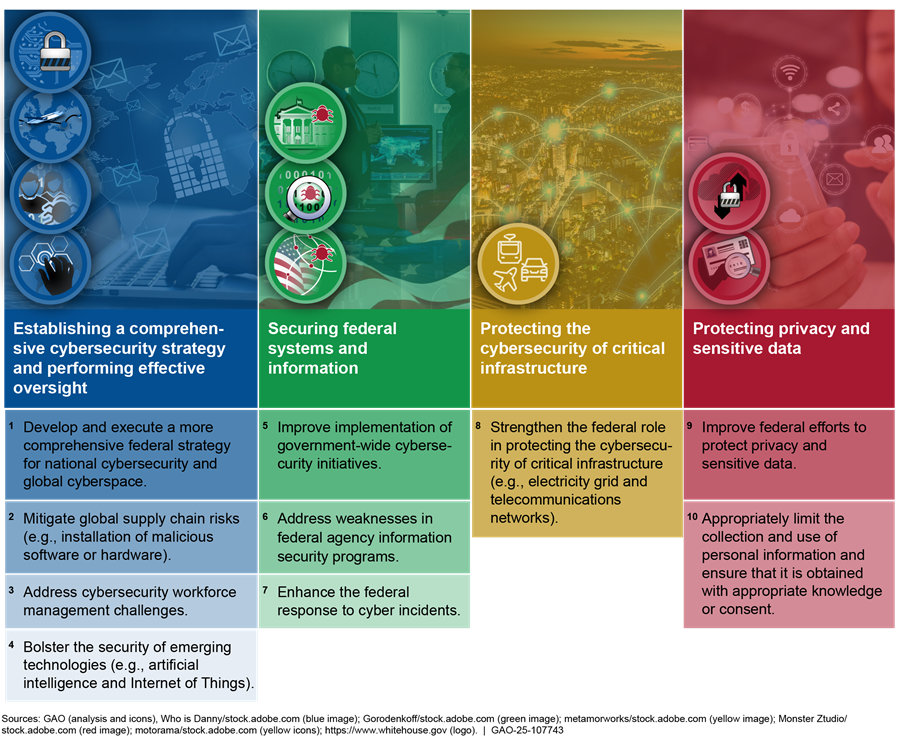
We have made 4,387 related recommendations since 2010. While 3,623 have been implemented or closed, 764 have not been fully implemented. Also, greater federal efforts are needed to better understand the status of private sector technological developments with cybersecurity implications—such as artificial intelligence—and to continue to enhance public and private sector coordination.
Seizing Opportunities to Better Protect Public Health and Reduce Risk
Several high-risk areas focus on addressing critical weaknesses in public health efforts. Our recommendations focus on
· ensuring the Department of Health and Human Services significantly elevates its ability to provide leadership and coordination of public health emergencies;
· providing the Food and Drug Administration (FDA) with a much greater capacity to (1) inspect foreign drug manufacturers that produce many of the drugs consumed by Americans, and (2) take stronger actions to address persistent drug shortages, including cancer therapies;
· improving the timeliness and quality of care given to our veterans, including mental health and suicide prevention, especially in rural areas;
· ensuring better health care by the Indian Health Service to Tribes and their members;
· providing national leadership to prevent drug abuse and further reduce overdose deaths; and
· ensuring the Environmental Protection Agency provides more timely reviews of potentially toxic chemicals before they are introduced into commercial production and widespread public use.
There is also a need for a more comprehensive approach to food safety to address fragmentation among 15 different federal agencies and at least 30 federal laws. While the United States has one of the safest food supplies in the world, every year millions of people are sickened by foodborne illnesses, tens of thousands are hospitalized, and thousands die. A more proactive, coordinated approach that takes greater advantage of modern technology would be in the best interest of Americans and would lead to a more efficient government.
Further, the FDA has struggled to meet inspection targets for foreign and domestic food facilities because of limited capacity and workforce. For example, it only conducted an average of 917 foreign food safety inspections each year from fiscal years 2018 through 2023, about 5 percent of its target of 19,200 annual inspections for this period (see fig. 10). In fiscal year 2023, FDA conducted a total of 1,175 foreign inspections—far fewer than its annual target of 19,200 inspections, according to FDA data. Also, according to FDA data, in 2023 FDA did not inspect—or attempt to inspect—about 41 percent of high-risk domestic food facilities and about 55 percent of non-high-risk domestic food facilities by the date they were due for inspection.
Figure 10: Food and Drug Administration’s (FDA) Performance in Meeting Annual Targets for Foreign Food Facility Inspections According to FDA Data, Fiscal Years 2018–2023
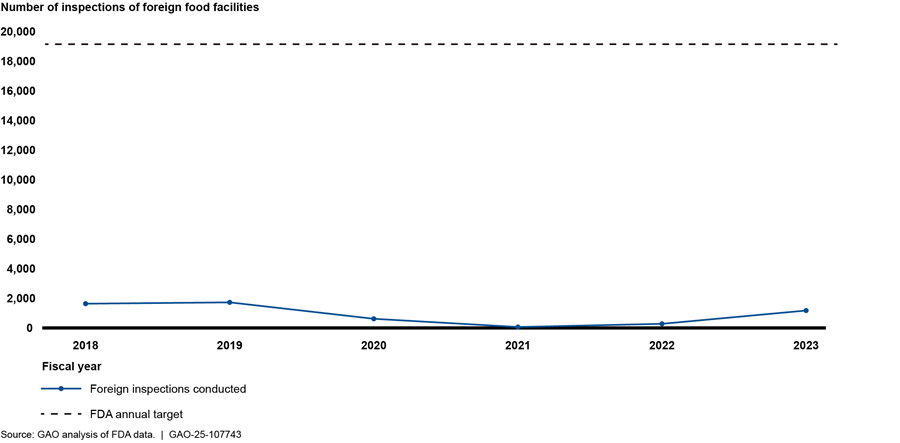
Note: FDA has interpreted the FDA Food Safety Modernization Act to require that, beginning in 2016, the agency inspect 19,200 foreign facilities per year. FDA includes both completed and attempted inspections in its fiscal year totals to track its progress covering foreign food facilities in FDA’s inventory that are due for inspection. Attempted inspections occur when FDA investigators attempt to conduct an inspection of a food facility, but the inspection cannot be completed.
Other Concerning High-Risk Areas
|
|
Modernizing Our Financial Regulatory Systems |
Actions are needed to strengthen oversight of financial institutions and address regulatory gaps. The March 2023 bank failures and rapid adoption of emerging technologies in the marketplace have highlighted continued challenges in the regulatory system since we initially designated this area as high-risk in 2009 during the financial crisis. In particular, the Federal Reserve should improve procedures so that decisions to escalate supervisory concerns happen in a timely manner, and Congress should consider designating a federal regulator for certain crypto asset markets, as we recommended.
|
|
There is an essential need for Congress to clarify the federal role for Fannie Mae and Freddie Mac, two private sector entities that provide underwriting for the U.S. mortgage market. They are still in federal conservatorship from the 2008 global financial crisis with no clear path forward. The other key federal players, Ginnie Mae and the Federal Housing Administration, have had their portfolios greatly expanded to nearly $2.7 trillion and $1.4 trillion, respectively. Consequently, the federal government is greatly exposed to a downturn in the housing market.
Federal housing and financial regulatory agencies have taken steps to strengthen the mortgage finance system. For example, they have adopted a final rule to implement quality control standards for automated mortgage valuation models.[5] Additionally, in September 2024, the Federal Housing Finance Agency launched a new dashboard for its joint initiative with the Consumer Financial Protection Bureau—the National Mortgage Database program, which helps examine the effect of mortgage market reforms. The dashboard reports publicly available quarterly data on residential mortgage performance.
To make further progress, federal housing agencies should continue to strengthen their oversight of the mortgage finance system. Congress should also determine the future federal role in this system and craft a plan to end federal conservatorship of the Fannie Mae and Freddie Mac enterprises.
|
|
Addressing Long-Standing Issues with the Bureau of Prisons |
Prison buildings are deteriorating and in need of repair and maintenance while facilities are understaffed, putting both incarcerated people and staff at risk. Moreover, efforts to prevent recidivism have not been thoroughly evaluated, undermining a key goal to help incarcerated people transition into society once released.
The Bureau of Prisons (BOP) has made some progress in this high-risk area since our 2023 update. For example, in fiscal year 2023, BOP filled a newly created position for Chief of Addiction Medicine to further demonstrate BOP’s support of Opioid Use Disorder treatment. BOP also finalized a strategic framework outlining goals, strategies, and initiatives to direct its overall improvement efforts.
Further, in March 2024, BOP’s then Director agreed to a set of 22 metrics that we developed to gauge BOP’s progress in addressing this high-risk issue. These metrics include actions or efforts for BOP to improve its management of staff and resources, planning and monitoring, and its implementation of the First Step Act of 2018.[6]
|
|
Fixing the United States Postal Service’s (USPS) Outdated Business Model |
Since our last update in 2023, USPS has taken further steps to implement its 10-year strategic plan released in March 2021. The Postmaster General, USPS’s executives, and its Board of Governors have all championed the plan and adjusted it to USPS’s changing operating environment and economic circumstances. In implementing this plan, USPS has worked to modernize and streamline its mail and package delivery network and improve the career development and retention of its workforce.
Congress acted to alleviate certain fiscal pressures and USPS is trying to reduce costs, but it is still losing money ($16 billion in fiscal years 2023 and 2024) and has extensive liabilities and debt ($181 billion in fiscal year 2024). USPS estimates that the fund supporting postal retiree benefits will be depleted in fiscal year 2031. At that point, USPS would be required to pay its share of retiree health care premiums, which USPS projects to be about $6 billion per year. There is a fundamental tension between the level of service Congress expects and what revenue USPS can reasonably be expected to generate. Congress needs to establish what services it wants USPS to provide and negotiate a balanced funding arrangement.
|
|
Addressing the Government’s Human Capital Challenges |
Twenty areas are on the High-Risk List in part due to skills gaps or an inadequate number of staff. Moreover, the personnel security clearance system is not yet being managed in the best manner to ensure that people are adequately screened to handle sensitive information.
OPM and agencies have taken some steps to assess and address skills gaps. For example, in June 2024, OPM identified the risks and mitigating strategies associated with its skills gaps, as we recommended. As a result, OPM is better positioned to monitor skills gaps across the agency and determine if risk mitigation strategies are successful.
In addition, in 2023, OPM conducted an analysis to identify common hiring needs across multiple agencies. OPM’s analysis helped establish a pooled hiring strategy that saves time and resources through a centralized coordination of federal government hiring to address skills gaps within the IT and human capital management workforce.
Ten High-Risk Areas Have Increased Their Progress Rating Since 2023
Ten high-risk areas improved since our last update in 2023. These areas are highlighted below and described in greater detail in appendix III.
|
|
FEMA has taken an important step to help move NFIP toward financial solvency by implementing a revised premium rate-setting methodology that better aligns premiums with the flood risk of individual properties. FEMA leadership has also demonstrated its commitment to effectively administrating NFIP by continuing to implement our outstanding recommendations. As a result, the two remaining criteria that had not been met in 2023—leadership commitment and demonstrated progress—are now met.
Having met all five criteria, this area is now transitioning to congressional monitoring only. To make further progress, Congress needs to enact comprehensive reforms to NFIP that would address the program’s challenges.
|
|
DOD has taken significant action to establish its new approach to business transformation and to institutionalize this approach into its systems, processes, and governance structures. DOD has further developed its capacity to manage these efforts, including (1) increasing staffing for its Performance Improvement Directorate and (2) conducting assessments to determine whether it had the needed funding, staff, and other capabilities to support its priority performance improvement initiatives.
With its approach to business transformation now nearly in place, DOD’s attention has turned to implementation. To address remaining issues, DOD needs to demonstrate that its approach is leading to positive effects on its performance improvement efforts and meaningful improvements to its business operations. Once fully institutionalized and if effectively implemented, the department should be able to achieve and sustain business reform on a broad, strategic, department-wide, and integrated basis. DOD will need to assess and report on the results of its performance improvement initiatives over time to demonstrate that these efforts are leading to meaningful improvements.
|
|
DOD issued department-wide and combatant command-specific guidance for operational contract support and embedded it into training and planning. Operational contract support includes supplies, services, and construction for deployed military forces around the world. Because of these actions, DOD has achieved a met rating in all five criteria for the operational contract support segment of this high-risk area. That segment is being removed from the area.
To address challenges with service acquisitions, DOD created an action plan with steps to more strategically manage services. Service acquisitions include management, IT, and administrative support. DOD also developed a dashboard to monitor spending on these acquisitions. To make further progress, DOD should ensure military department guidance identifies responsibilities to collectively prioritize, aggregate, and review service requirements on a recurring basis and finalize the methodology for forecasting budget needs.
|
|
The rating for the leadership commitment criterion increased to met due, in part, to the Secretary of Defense issuing a department-wide memorandum calling for DOD to take steps to remove DOD business systems modernization from the High-Risk List. The memorandum also called for the department CIO to accelerate the retirement of noncompliant legacy defense business systems. Additionally, DOD developed a draft action plan that includes specific actions and associated milestones to better manage business systems acquisitions, investment management, and business enterprise architecture efforts.
To make further progress, DOD needs to improve management of its business systems acquisitions by enhancing its investment management guidance and completing planned updates to its federated business enterprise architecture.
|
|
National Efforts to Prevent, Respond to, and Recover from Drug Misuse |
Federal agencies have increased their capacity to reduce drug overdose deaths, such as by expanding access to opioid overdose reversal medication. As of February 2025, estimates by the Centers for Disease Control and Prevention for the 12-month period ending in September 2024 were part of the first substantial drop in predicted provisional overdose deaths since January 2015. However, agencies still need to determine the cause of this decline, and the number of overdose deaths remains high.
To make further progress, federal agencies must effectively coordinate and implement a strategic national response and make progress toward reducing drug misuse rates, overdose deaths, and the resulting harmful effects to society.
The additional five high-risk areas that made progress since 2023 are Resolving the Federal Role in Housing Finance, USPS Financial Viability, Emergency Loans for Small Businesses, Government-wide Personnel Security Clearance Process, and U.S. Government’s Environmental Liability. Additional details on these areas can be found in app. III.
High-Risk Areas Have Made Varied Progress
Twenty-two high-risk areas have met one or more of the five criteria for removal from the High-Risk List. Ten areas improved while three areas declined since our last update in 2023 (see table 3).[7] Most areas, while making some improvements, maintained their prior ratings.
|
High-risk area |
Change since 2023 list |
Number of criteria |
||
|
|
|
Met |
Partially met |
Not met |
|
National Flood Insurance Programa |
↑ |
5 |
0 |
0 |
|
DOD Approach to Business Transformation |
↑ |
3 |
2 |
0 |
|
DOD Contract Management |
↑ |
3 |
2 |
0 |
|
Resolving the Federal Role in Housing Financea,b |
↑ |
3 |
2 |
0 |
|
USPS Financial Viabilitya |
↑ |
3 |
2 |
0 |
|
Emergency Loans for Small Businesses |
↑ |
2 |
3 |
0 |
|
Government-wide Personnel Security Clearance Processa,b |
↑ |
2 |
3 |
0 |
|
DOD Business Systems Modernization |
↑ |
1 |
4 |
0 |
|
National Efforts to Prevent, Respond to, and Recover
from |
↑ |
0 |
5 |
0 |
|
U.S. Government’s Environmental Liabilitya,b |
↑ |
0 |
3 |
2 |
|
Managing Federal Real Propertyb |
↓ |
1 |
4 |
0 |
|
DOD Weapon Systems Acquisitiona |
↓ |
0 |
4 |
1 |
|
Improving IT Acquisitions and Managementa,b |
↓ |
0 |
3 |
2 |
|
NASA Acquisition Management |
• |
4 |
1 |
0 |
|
Strengthening Department of Homeland Security IT and |
• |
3 |
2 |
0 |
|
Medicare Program & Improper Paymentsa |
• |
2 |
3 |
0 |
|
Acquisition and Program Management for DOE’s National |
• |
1 |
4 |
0 |
|
DOD Financial Management |
• |
1 |
4 |
0 |
|
Enforcement of Tax Lawsa |
• |
1 |
4 |
0 |
|
Ensuring the Cybersecurity of the Nationa,b |
• |
1 |
4 |
0 |
|
Improving Federal Management of Programs That Serve |
• |
1 |
4 |
0 |
|
Protecting Public Health Through Enhanced Oversight
of |
• |
1 |
4 |
0 |
|
Protecting Technologies Critical to U.S. National Securityb |
• |
1 |
4 |
0 |
|
VA Acquisition Management |
• |
1 |
4 |
0 |
|
Strategic Human Capital Managementb |
• |
1 |
3 |
1 |
|
Improving and Modernizing Federal Disability Programsb |
• |
0 |
5 |
0 |
|
Management of Federal Oil and Gas Resources |
• |
0 |
5 |
0 |
|
Managing Risks and Improving VA Health Care |
• |
0 |
5 |
0 |
|
Modernizing the U.S. Financial Regulatory Systema,b |
• |
0 |
5 |
0 |
|
Strengthening Medicaid Program Integritya,b |
• |
0 |
5 |
0 |
|
Transforming EPA’s Process for Assessing and Managing
|
• |
0 |
5 |
0 |
|
Limiting the Federal Government’s Fiscal Exposure by
Better |
• |
0 |
4 |
1 |
|
Improving Federal Oversight of Food Safetya,b |
• |
0 |
3 |
2 |
|
Unemployment Insurance Systema,b (area rated for the first time) |
n/a |
2 |
3 |
0 |
|
Strengthening Management of the Federal Prison System |
n/a |
0 |
5 |
0 |
|
HHS Leadership and Coordination of Public Health
Emergenciesb |
n/a |
0 |
2 |
3 |
|
Funding the Nation’s Surface Transportation Systema |
n/a |
0 |
0 |
0 |
|
Improving the Delivery of Federal Disaster Assistancea,b |
n/a |
0 |
0 |
0 |
Legend:
↑: area progressed on one or more criteria since 2023
↓: area declined on one or more criteria since 2023
●: no change in rating since 2023
n/a: not applicable
Source: GAO. | GAO‑25‑107743
aLegislation is likely to be necessary to effectively address this high-risk area.
bCoordinated efforts across multiple entities are necessary to effectively address this high-risk area.
Figure 11 and table 4 summarize the status for high-risk areas that remain on the List and rating changes since the last update.
Figure 11: Number of 2025 High-Risk Areas Receiving Met, Partially Met, and Not Met Ratings for Each Criterion and Area Ratings Changes Since 2023
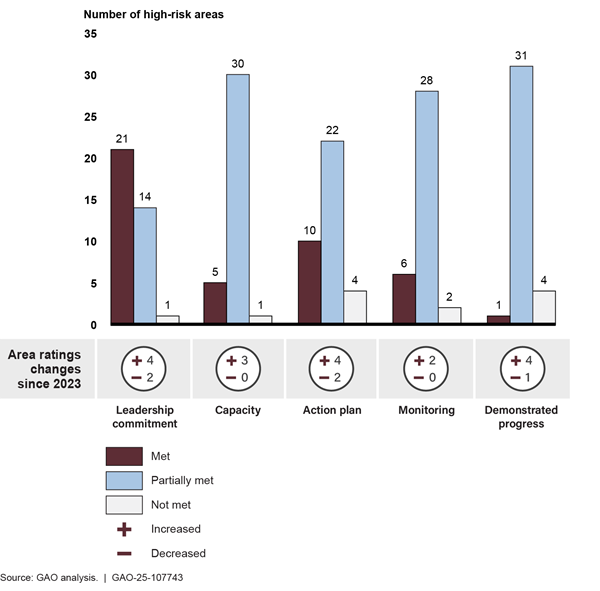
Note: The figure reflects ratings of overall high-risk areas. It does not include two areas that did not receive ratings in this update.
Table 4: 2025 High-Risk Area Ratings and Rating Changes on Five Criteria for Removal from GAO’s High-Risk List
|
|
Criteria |
||||
|
High-risk area |
Leadership commitment |
Capacity |
Action plan |
Monitoring |
Demonstrated progress |
|
National Flood Insurance Program |
|
|
|
|
|
|
NASA Acquisition Management |
|
|
|
|
|
|
DOD Approach to Business Transformation |
|
|
|
|
|
|
DOD Contract Management |
|
|
|
|
|
|
Resolving the Federal Role in Housing Finance |
|
|
|
|
|
|
Strengthening Department of Homeland Security IT and Financial Management Functions |
|
|
|
|
|
|
USPS Financial Viability |
|
|
|
|
|
|
Emergency Loans for Small Businesses |
|
|
|
|
|
|
Medicare Program & Improper Payments |
|
|
|
|
|
|
Government-wide Personnel Security Clearance Process |
|
|
|
|
|
|
Unemployment Insurance System |
|
|
|
|
|
|
Acquisition and Program Management for DOE’s National Nuclear Security Administration and Office of Environmental Management |
|
|
|
|
|
|
DOD Business Systems Modernization |
|
|
|
|
|
|
DOD Financial Management |
|
|
|
|
|
|
Enforcement of Tax Laws |
|
|
|
|
|
|
Ensuring the Cybersecurity of the Nation |
|
|
|
|
|
|
Improving Federal Management of Programs that Serve Tribes and Their Members |
|
|
|
|
|
|
Managing Federal Real Property |
|
|
|
|
|
|
Protecting Public Health Through Enhanced Oversight of Medical Products |
|
|
|
|
|
|
Protecting Technologies Critical to U.S. National Security |
|
|
|
|
|
|
VA Acquisition Management |
|
|
|
|
|
|
Strategic Human Capital Management |
|
|
|
|
|
|
Improving and Modernizing Federal Disability Programs |
|
|
|
|
|
|
Management of Federal Oil and Gas Resources |
|
|
|
|
|
|
Managing Risks and Improving VA Health Care |
|
|
|
|
|
|
Modernizing the U.S. Financial Regulatory System |
|
|
|
|
|
|
National Efforts to Prevent, Respond to, and Recover from Drug Misuse |
|
|
|
|
|
|
Strengthening Management of the Federal Prison System |
|
|
|
|
|
|
Strengthening Medicaid Program Integrity |
|
|
|
|
|
|
Transforming EPA’s Process for Assessing and Managing Chemical Risks |
|
|
|
|
|
|
DOD Weapon Systems Acquisition |
|
|
|
|
|
|
Limiting the Federal Government’s Fiscal Exposure by Better Managing Climate Change Risks |
|
|
|
|
|
|
Improving Federal Oversight of Food Safety |
|
|
|
|
|
|
U.S. Government's Environmental Liability |
|
|
|
|
|
|
Improving IT Acquisitions and Management |
|
|
|
|
|
|
HHS Leadership and Coordination of Public Health Emergencies |
|
|
|
|
|
Legend:
![]() Met
Met ![]() Partially Met
Partially Met ![]() Not Met
Not Met ![]() Increased
Increased ![]() Decreased
Decreased
Source: GAO. | GAO‑25‑107743
Effective Interagency Collaboration Is Essential to Making Progress on High-Risk Areas
High-risk areas are among the most technically complex and challenging issues for government to address. Achieving meaningful progress on high-risk areas requires coordinated efforts across federal agencies, often with other governments (for example, at state and local levels), nongovernmental organizations, contractors, and the private sector. At least 18 areas on the current High-Risk List involve coordinated efforts across agencies and other entities.
There are several tools for forging successful partnerships across groups. One way progress has been made on high-risk areas is through interagency working groups and other mechanisms that bring together the relevant federal agencies and entities. We have developed eight leading practices for agencies to effectively work together on shared goals (see fig. 12).[8]
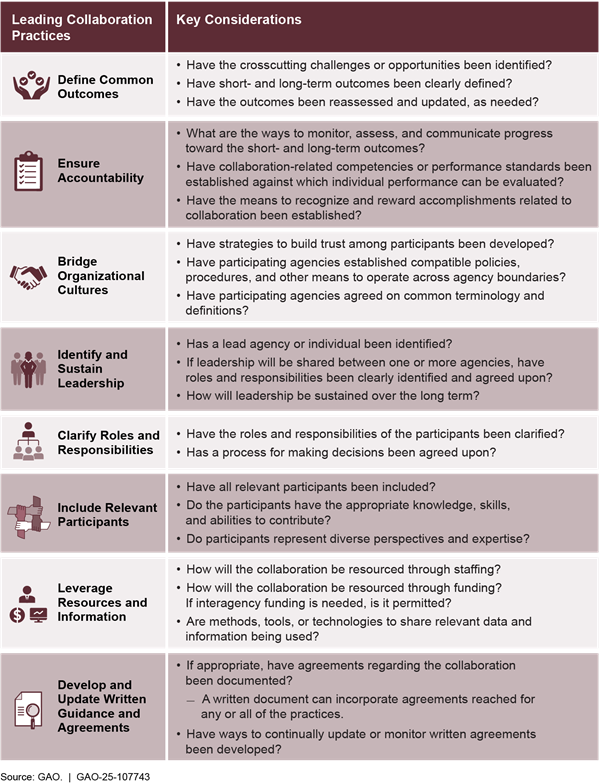
However, a lack of or ineffective collaboration can stall progress. When interagency groups do not collaborate effectively, they can struggle to address government-wide challenges on high-risk areas. For example:
· The Food Safety Working Group, composed of officials from the Centers for Disease Control and Prevention, FDA, and Food Safety and Inspection Service, and established in 2009 to coordinate federal efforts and develop goals to make food safer, has not met since 2011 and is no longer active.
· The disparate and fragmented delivery of federal disaster recovery efforts makes it difficult for communities to know who to turn to for help.
Congress will increasingly need to provide oversight of integrated approaches to help its decision-making on the many issues requiring effective collaboration across federal agencies, levels of government, and sectors. Congress should consider requiring that interagency groups formed to address these challenges develop and implement a collaboration plan incorporating the leading interagency collaboration practices. This would help the groups increase their efficiency and effectiveness and achieve intended outcomes.
Matter for Congressional Consideration
Congress should consider requiring that interagency groups formed to address high-risk and other key challenges develop and implement a collaboration plan incorporating GAO’s leading interagency collaboration practices. (Matter for Congressional Consideration 1)
The high-risk program continues to be a top priority at GAO. We will maintain our emphasis on identifying high-risk issues across government and on providing recommendations and sustained attention to help address them. We will also continue working collaboratively with Congress, agency leaders, and the Office of Management and Budget (OMB) to address these issues.
OMB’s role is especially important because many high-risk areas are government-wide or involve multiple agencies. Resource investments are also associated with correcting a number of high-risk problems. OMB is required to conduct portfolio reviews to address programs identified by GAO as high risk.[9] OMB has worked to develop a standardized, federal government-wide approach to building agencies’ capacity for improved program and project management, including reviewing portfolios of agency programs, assessing their effectiveness, and offering guidance to agencies for improved program management. These actions could enhance progress on high-risk areas.
Progress has been achieved through leadership meetings between OMB, agencies, and GAO to discuss planned actions to address individual high-risk areas. OMB accelerated the pace of these meetings in the past 4 years. Since the beginning of this 4-year cycle of trilateral meetings in 2021, OMB has convened meetings on 23 high-risk areas. These trilateral meetings led to greater progress on high-risk issues. We expect OMB to continue to hold these meetings with a goal of meeting on all high-risk areas before our next update in 2027.
We are providing this update to the President and Vice President, congressional leadership, the appropriate congressional committees, other Members of Congress, OMB, and the heads of major departments and agencies.

Gene L. Dodaro
Comptroller General
of the United States
We developed guidance to determine which federal programs and functions should be designated high risk.[10] We consider qualitative factors, such as whether the risk
· involves public health or safety, service delivery, national security, national defense, economic growth, or privacy or citizens’ rights; or
· could result in significantly impaired service, program failure, injury, or loss of life, or significantly reduce economy, efficiency, or effectiveness.
We also consider the exposure to loss in monetary or other quantitative terms. At a minimum, $1 billion must be at risk in areas such as
· the value of major assets being impaired;
· revenue sources not being realized;
· major agency assets being lost, stolen, damaged, wasted, or underused;
· potential for, or evidence of, improper payments or fraud; or
· presence of contingencies or potential liabilities.
Before designating an area as high risk, we also consider the status and effectiveness of corrective measures that are planned or under way.
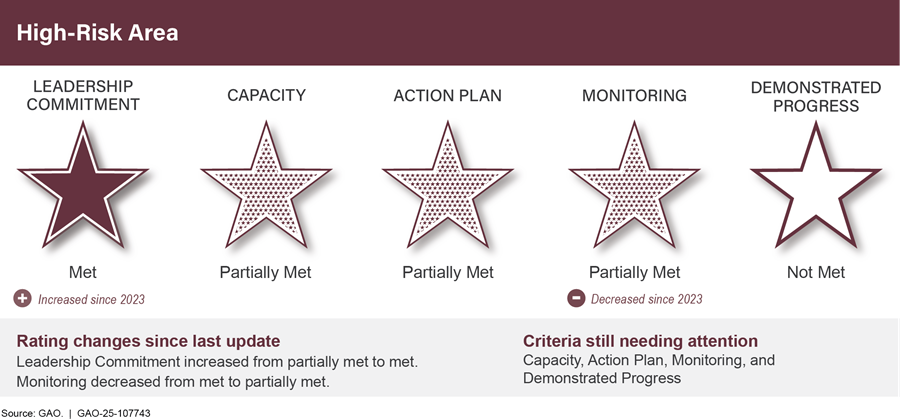
To make progress on high-risk areas, administration and agency leaders need to provide top-level attention. Congressional action is also needed for some high-risk areas. We determine whether to remove agencies from the High-Risk List based on whether their actions are grounded in the five criteria for removal below (see fig. 13).

We rate high-risk areas on the following scale:
Met. Actions have been taken that meet the criterion. There are no significant actions that need to be taken to further address this criterion.
Partially met. Some, but not all, actions necessary to meet the criterion have been meet.
Not met. Few, if any, actions toward meeting the criterion have been taken.
Figure 14 illustrates the varying degrees of progress in each of the five criteria for a high-risk area.
Some high-risk areas are divided into segments. For example, the high-risk area Managing Federal Real Property includes four segments—Underutilized Property, Data Reliability, Facility Security, and Building Condition—to reflect four interrelated parts of the overall high-risk area. Multidimensional high-risk areas such as these have separate ratings for each segment as well as a summary rating that reflects a composite of the ratings. We do not rate high-risk areas that primarily need congressional action.
In 1990, we began a program to report on government operations that we identified as high risk. Since then, generally coinciding with the start of each new Congress, we have reported on the status of progress addressing high-risk areas and have updated the High-Risk List. Our last high‑risk update was in April 2023.[11] That update identified 37 high-risk areas. This year, we added one high-risk area—Improving the Delivery of Federal Disaster Assistance. With this addition, this 2025 update identifies 38 high-risk areas.
Overall, this program has served to identify and help resolve serious weaknesses in areas that involve substantial resources and provide critical services to the public. Since our program began, the federal government has taken high-risk problems seriously and has made long-needed progress toward correcting them. In 29 cases, progress has been sufficient for us to remove the high-risk designation. A summary of changes to our High-Risk List over the past 35 years is shown in table 5.
|
|
Number of areas |
|
Original High-Risk List in 1990 |
14 |
|
High-risk areas added since 1990 |
54a |
|
High-risk areas removed since 1990 |
29 |
|
High-risk areas separated out from existing area |
2 |
|
High-risk areas consolidated since 1990 |
2 |
|
High-Risk List in 2025 |
38 |
Source: GAO. | GAO‑25‑107743
aThis number includes areas that are also counted as “High-risk areas separated out from existing area.”
How Can Agencies Use the Criteria to Make Progress on High-Risk Issues?
The five high-risk criteria form a roadmap for efforts to improve and ultimately address high-risk issues. Addressing some of the criteria leads to progress, while satisfying all criteria is central to removal from the list. Congressional attention, Office of Management and Budget engagement, and federal agencies’ sustained leadership, planning, and execution are key practices for successfully addressing high-risk areas.
In March 2022, we reported on key practices for addressing the five high-risk criteria to facilitate progress on high-risk areas. See figure 15 for key practices that can help agencies demonstrate leadership commitment and sustain continuity for high-risk efforts.

What Is the History of Programs Removed from the High-Risk List?
A summary of areas removed from our High-Risk List over the past 35 years is shown in table 6.
|
High-risk area |
Year removed |
Years on list |
|
Federal Transit Administration Grant Management |
1995 |
5 |
|
Pension Benefit Guaranty Corporation |
1995 |
5 |
|
Resolution Trust Corporation |
1995 |
5 |
|
State Department Management of Overseas Real Property |
1995 |
5 |
|
Bank Insurance Fund |
1995 |
4 |
|
Customs Service Financial Management |
1999 |
8 |
|
Farm Loan Programs |
2001 |
11 |
|
Superfund Programs |
2001 |
11 |
|
National Weather Service Modernization |
2001 |
6 |
|
The 2000 Census |
2001 |
4 |
|
The Year 2000 Computing Challenge |
2001 |
4 |
|
Asset Forfeiture Programs |
2003 |
13 |
|
Supplemental Security Income |
2003 |
6 |
|
Student Financial Aid Programs |
2005 |
15 |
|
FAA Financial Management |
2005 |
6 |
|
Forest Service Financial Management |
2005 |
6 |
|
HUD Single-Family Mortgage Insurance & Rental Housing Assistance Programs |
2007 |
13 |
|
U.S. Postal Service’s Transformation Efforts and Long-term Outlook |
2007 |
6 |
|
FAA’s Air Traffic Control Modernization |
2009 |
14 |
|
DOD Personnel Security Clearance Program |
2011 |
6 |
|
2010 Census |
2011 |
3 |
|
IRS Business Systems Modernization |
2013 |
18 |
|
Management of Interagency Contracting |
2013 |
8 |
|
Establishing Effective Mechanisms for Sharing and Managing Terrorism-Related Information to Protect the Homeland |
2017 |
12 |
|
DOD Supply Chain Management |
2019 |
29 |
|
Mitigating Gaps in Weather Satellite Data |
2019 |
6 |
|
DOD Support Infrastructure Management |
2021 |
24 |
|
2020 Decennial Census |
2023 |
6 |
|
Pension Benefit Guaranty Corporation Insurance Programs |
2023 |
20 |
Source: GAO. | GAO‑25‑107743
For a summary of actions taken that resulted in removal of these high-risk areas, please see appendix II of our report on key practices for successfully addressing high-risk areas and removing them from the High-Risk List.[12]
When Were Areas Added to the High-Risk List?
The areas on our 2025 High-Risk List and the year each was designated as high risk are shown in table 7.
|
High-risk area |
Year designated |
|
DOD Weapon Systems Acquisition |
1990 |
|
Acquisition and Program Management for DOE’s National Nuclear Security Administration and Office of Environmental Management |
1990 |
|
Enforcement of Tax Laws |
1990 |
|
Medicare Program and Improper Payments |
1990 |
|
NASA Acquisition Management |
1990 |
|
DOD Contract Management |
1992 |
|
DOD Business Systems Modernization |
1995 |
|
DOD Financial Management |
1995 |
|
Ensuring the Cybersecurity of the Nation |
1997 |
|
Strategic Human Capital Management |
2001 |
|
Improving and Modernizing Federal Disability Programs |
2003 |
|
Managing Federal Real Property |
2003 |
|
Strengthening Department of Homeland Security IT and Financial Management Functions |
2003 |
|
Strengthening Medicaid Program Integrity |
2003 |
|
DOD Approach to Business Transformation |
2005 |
|
National Flood Insurance Program |
2006 |
|
Protecting Technologies Critical to U.S. National Security |
2007 |
|
Funding the Nation’s Surface Transportation System |
2007 |
|
Improving Federal Oversight of Food Safety |
2007 |
|
Modernizing the U.S. Financial Regulatory System |
2009 |
|
Protecting Public Health Through Enhanced Oversight of Medical Products |
2009 |
|
Transforming EPA’s Processes for Assessing and Managing Chemical Risks |
2009 |
|
USPS Financial Viability |
2009 |
|
Management of Federal Oil and Gas Resources |
2011 |
|
Limiting the Federal Government’s Fiscal Exposure by Better Managing Climate Change Risks |
2013 |
|
Resolving the Federal Role in Housing Finance |
2013 |
|
Improving IT Acquisitions and Management |
2015 |
|
Managing Risks and Improving VA Health Care |
2015 |
|
Improving Federal Management of Programs that Serve Tribes and Their Members |
2017 |
|
U.S. Government’s Environmental Liability |
2017 |
|
Government-wide Personnel Security Clearance Process |
2018 |
|
VA Acquisition Management |
2019 |
|
Emergency Loans for Small Businesses |
2021 |
|
National Efforts to Prevent, Respond to, and Recover from Drug Misuse |
2021 |
|
Unemployment Insurance System |
2022 |
|
HHS Leadership and Coordination of Public Health Emergencies |
2022 |
|
Strengthening Management of the Federal Prison System |
2023 |
|
Improving the Delivery of Federal Disaster Assistance |
2025 |
Source: GAO. | GAO‑25‑107743
The following pages provide overviews of the 38 high-risk areas on our updated list. Each overview discusses (1) why the area is high risk, (2) the actions that have been taken and that are under way to address the problem since our last update in 2023, and (3) what remains to be done. Each of these high-risk areas is also described on our High-Risk List website, https://www.gao.gov/high-risk-list.
Improving the Delivery of Federal Disaster Assistance
To help improve timely disaster assistance for survivors and communities, the federal government needs to reduce fragmentation across its disaster assistance programs.
Why Area Is Being Added to the High-Risk List
In recent years, natural disasters have become costlier and more frequent. For example, in 2018, the National Oceanic and Atmospheric Administration calculated that the United States sustained 14 disasters that each cost more than $1 billion in total economic damages. By 2024, the number of disasters costing at least $1 billion almost doubled to 27. That same year, at least 568 people died, directly or indirectly, as a result of those disasters. In addition to natural disasters, the COVID-19 pandemic—which was a federally declared disaster—tested federal agencies’ capacity to mount an equitable and effective nationwide response.
Recent disasters demonstrate the need for the federal government to take government-wide action to deliver assistance efficiently and effectively and reduce its fiscal exposure.
· Hurricanes Helene and Milton occurred within 2 weeks of one another in 2024 and affected some of the same areas in the Southeast (see fig. 16). These two disasters resulted in over 200 deaths and are expected to cost over $50 billion, according to the National Oceanic and Atmospheric Administration.
· On January 8, 2025, the President approved a major disaster declaration for historic wildfires in Los Angeles County, California. The wildfires are unprecedented in their size, scope, and the damage they caused.
Figure 16: Road Repair Following Hurricane Helene, North Carolina

Disaster assistance includes providing support to communities and survivors for response to, recovery from, and resilience to man-made and natural disasters. For fiscal years 2015 through 2024, appropriations for disaster assistance totaled at least $448 billion.[13] In total, the Federal Emergency Management Agency (FEMA) approved over two million households for federal disaster assistance in 2024.
The Disaster Relief Fund, administered by FEMA, pays for several key disaster response, recovery, and mitigation programs that assist communities impacted by federally declared emergencies and major disasters. Appropriations to this fund have generally increased over time, as shown in figure 17. Other federal agencies have specific authorities and resources outside of the Disaster Relief Fund to support certain disaster response and recovery efforts.
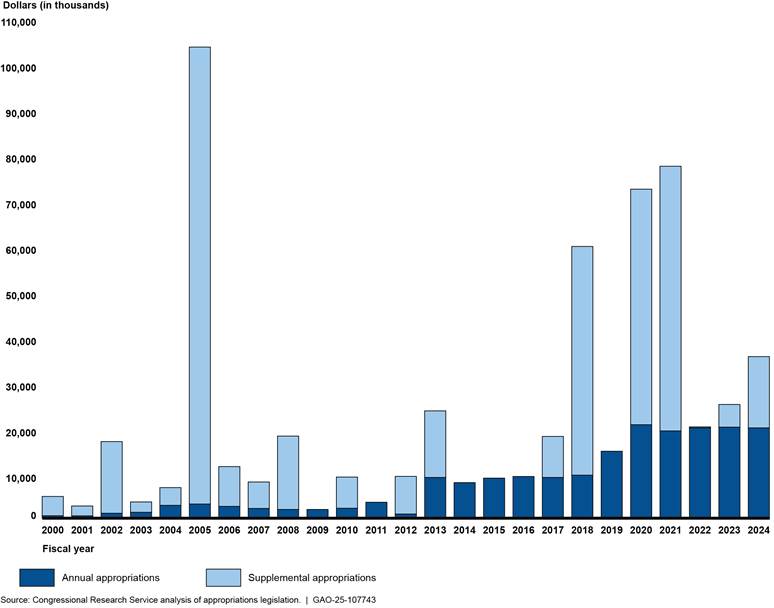
Note: Fiscal year 2013 numbers do not reflect the impact of sequestration. Supplemental data include contingent appropriations and all appropriations under the heading of “Disaster Relief” or “Disaster Relief Fund” including the language “for an additional amount.” Appropriations do not account for transfers or rescissions. Reductions reflected in the net total data include transfers and rescissions specifically enumerated in appropriations acts. Deflator used was drawn from the FY2024 Budget of the United States Government, “Historical Tables: Table 1.3—Summary of Receipts, Outlays, and Surpluses or Deficits (—) in Current Dollars, Constant (FY2012) Dollars, and as Percentages of GDP: 1940—2028.”
The number of federal disaster declarations and the expectation for federal support have increased. As shown in figure 18, federal support for disaster recovery lasts for years. For example, according to FEMA, the agency is managing over 600 open major disaster declarations—some of which occurred almost 20 years ago—in various stages of response and recovery.
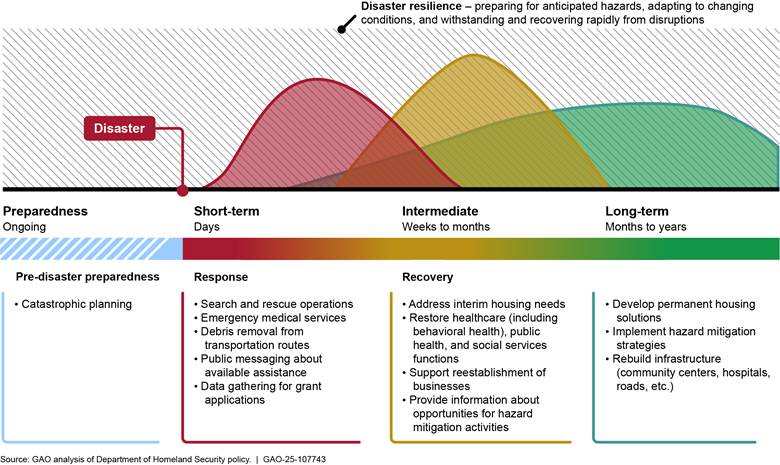
We previously raised concerns about federal disaster assistance as part of another high-risk area, Limiting the Federal Government’s Fiscal Exposure by Better Managing Climate Change Risks. In addition, we have reported on the potential for fraud in FEMA and Department of Housing and Urban Development (HUD) disaster assistance programs. The U.S. Global Change Research Program, in its Fifth National Climate Assessment, states that climate change is increasing the chances of multiple climate hazards occurring simultaneously or consecutively across the United States and its territories.
Given the rise in the number and cost of disasters and increasing programmatic challenges related to the delivery of federal disaster assistance identified in our work, disaster assistance merits elevation as its own high-risk issue. This area is not being rated as it was recently added to the High-Risk List. We have identified four key challenges:
· Improving processes for assisting survivors
· Reducing fragmentation of the federal approach to disaster assistance
· Strengthening FEMA’s disaster workforce and capacity
· Investing in resilience
Improving Processes for Assisting Survivors
Survivors face numerous challenges receiving needed aid, including lengthy and complex application review processes. Federal agencies are taking steps to help improve disaster assistance to survivors. For example, in 2023, the Small Business Administration (SBA) implemented the Disaster Assistance for Rural Communities Act to simplify the process for a governor or tribal government chief executive to request an agency disaster declaration in counties with rural communities that have experienced significant damage.[14]
We found in February 2024 that rural areas face unique challenges in seeking SBA assistance following a disaster. For example, we found that disaster survivors may not be aware of SBA’s disaster loans. We recommended that SBA should distinguish between rural and urban communities in its outreach and marketing plan and incorporate actions to mitigate the unique challenges rural communities face in accessing its Disaster Loan Program. SBA agreed with our recommendation, and we will continue to monitor its progress to address it.
Administered by HUD, the Community Development Block Grant Disaster Recovery (CDBG-DR) funds provide significant, flexible federal recovery funding for states and localities affected by disasters and generally support long-term recovery. HUD, however, does not require CDBG-DR grantees to collect accurate data on critical milestones.
A HUD-funded 2019 study on the timeliness of CDBG-DR housing activities found that all but one of the eight grantees in the study faced challenges in developing a grant management system. HUD could better ensure that its grantees identify problem milestones and address delays in assisting survivors by requiring grantees to collect and analyze timeliness data, as we recommended. As of February 2025, HUD said it had explored options for requiring grantees to collect milestone data and was evaluating how best to address this recommendation to ensure the needs of disaster survivors are met in a timely manner. We will continue to monitor their progress to address this issue.
Federal law created the National Flood Insurance Program (NFIP) to reduce the escalating costs of federal disaster assistance for flood damage, while also keeping flood insurance affordable. The NFIP transferred the financial burden of flood risk from property owners to the federal government. We discuss reforms needed to improve the program’s solvency and the nation’s flood resilience in the NFIP high-risk area. We have other ongoing work about the state of the homeowner’s insurance market, including concerns about the availability and affordability of coverage, and the issue of a lack of flood insurance coverage and what can be done to address it.
Reducing Fragmentation of the Federal Approach to Disaster Assistance
The federal approach to disaster recovery is fragmented across more than 30 federal entities. These entities are involved with multiple programs and authorities and have differing requirements and timeframes. Moreover, data sharing across entities is limited. This fragmented approach can make it harder for survivors and communities to successfully navigate multiple federal programs.
Congress and federal agencies have taken steps to better manage fragmentation, such as through interagency agreements and reducing program complexity, but the challenges remain. In November 2022, we recommended that Congress should consider establishing an independent commission to recommend reforms to the federal approach to disaster recovery. The commission should follow our leading practices for interagency collaboration.
Agencies could also do more to effectively manage
fragmentation across disaster recovery programs. We recommended that FEMA, HUD,
and the Department of Transportation (DOT)
should identify and take steps to better manage fragmentation
between their individual disaster recovery programs and other federal programs.
Agencies are taking steps to address our recommendations. For example, FEMA was
working with interagency partners to explore the viability of a single disaster
assistance application but has not yet determined a course of action as of
February 2024. DOT also reported that it has taken steps to reduce
fragmentation within its own programs. However, it is unclear, how, if at all,
DOT is working with other federal agencies to identify ways to reduce
fragmentation across federal programs.
FEMA—as administrator of several disaster recovery programs—should also take steps to better manage fragmentation across its own programs, as we recommended. Such actions could make the programs simpler, more accessible and user-friendly, and improve the effectiveness of federal disaster recovery efforts. Reforming the federal government’s approach to disaster recovery and reducing fragmentation could improve service delivery to disaster survivors and communities and improve the effectiveness of recovery efforts. As of February 2024, FEMA had taken steps to streamline the applications for two of its recovery programs. However, FEMA will need to demonstrate that it has thoroughly considered available options to reduce fragmentation across its own programs, identified those FEMA intends to implement, and then taken steps to fully implement this recommendation.
In response to the challenges that wildfires pose for the nation, the Infrastructure Investment and Jobs Act required the establishment of the Wildland Fire Mitigation and Management Commission in 2021.[15] In September 2023, the commission issued a set of policy priorities and recommendations calling for greater coordination, interoperability, collaboration, and simplification within the wildfire system. We have found that as the incidence and severity of massive wildfires increases, FEMA and other agencies could find additional opportunities to ensure their programs are effective. For example, we recommended in December 2024 that FEMA assess ways to provide immediate post-wildfire mitigation assistance and establish a process to collect, assess, and incorporate ongoing feedback from Fire Management Assistance Grants recipients. Taking these steps would help foster more resilient communities and reduce the future demand on federal resources.
Strengthening FEMA’s Disaster Workforce and Capacity
FEMA has long-standing workforce management issues that make supporting response and recovery efforts difficult. In recent years, the increasing frequency and costs of disasters, the COVID-19 pandemic, and other responsibilities have placed additional pressures on FEMA. FEMA's management of its workforce challenges and staffing levels has limited its capacity to provide effective disaster assistance.
For example, we found that FEMA had an overall staffing gap of approximately 35 percent across different positions at the beginning of fiscal year 2022. The gaps varied, but Public Assistance, Hazard Mitigation, and Logistics generally had lower percentages of staffing targets filled—between 44 and 60 percent at the beginning of fiscal year 2022. These positions serve important functions, including administering assistance to state and local governments, creating safer communities by managing risk reduction activities, and coordinating all aspects of resource planning and movement during a disaster.
We also found that FEMA has fallen short of its yearly staffing target between 2019 and 2022, and that gap continues to grow. For example, FEMA only had nine percent of its disaster-response workforce available for Hurricane Milton response, according to its daily operations brief. Many responders have declined deployments in recent disasters because of burnout or severe conditions in the field. We have made numerous recommendations to help FEMA better manage catastrophic or concurrent disasters.
For example, FEMA should develop and implement a methodology that provides a more comprehensive assessment of a jurisdiction’s response and recovery capabilities including its fiscal capacity. Without an accurate assessment, FEMA runs the risk of recommending to the President that federal disaster assistance be awarded to jurisdictions that may not need it. FEMA has taken steps to update the factors considered when evaluating a request for a major disaster declaration for Public Assistance, specifically the estimated cost of assistance, via the federal rulemaking process three times—in 2016, 2017, and 2020. However, as of January 2025, the agency has not issued a final rule updating the estimated cost of assistance.
The COVID-19 pandemic marked the first time the Disaster Relief Fund has been used to respond to a nationwide public health emergency. FEMA used its typical process to estimate its obligations for COVID-19. However, FEMA did not meet its accuracy goal for COVID-19 in any fiscal year from 2021 through 2023. By identifying and documenting lessons learned for estimating obligations based on its experience with COVID-19, as we recommended, FEMA can better position itself to adapt to similar estimation challenges in the future.
Investing in Resilience
Disaster resilience can reduce the need for more costly future recovery assistance. In our Disaster Resilience Framework, we reported that the reactive and fragmented federal approach to disaster risk reduction limits the federal government’s ability to facilitate significant reduction in the nation’s overall disaster risk.
FEMA’s hazard mitigation assistance programs provide assistance for eligible long-term solutions that reduce the impact of future disasters, thereby increasing disaster resilience. The Infrastructure Investment and Jobs Act made supplemental appropriations for fiscal years 2022 through 2026 to FEMA for the Safeguarding Tomorrow Revolving Loan Fund program ($500 million), Building Resilient Infrastructure and Communities program ($1 billion), and Flood Mitigation Assistance program ($3.5 billion).[16]
· The Safeguarding Tomorrow through Ongoing Risk Mitigation Act of 2021 authorized FEMA to award capitalization grants—seed funding—to help eligible states, territories, Tribes, and the District of Columbia establish revolving loan funds for mitigation assistance.[17] In response, FEMA established the Safeguarding Tomorrow Revolving Loan Fund grant program in 2022, which we are reviewing in ongoing work.
· The Building Resilient Infrastructure and Communities program provides pre-disaster mitigation grants to help eligible states, territories, and Tribes continue investing in a variety of mitigation activities. These activities focus on infrastructure projects and building capability and capacity among local communities. We are also reviewing this program.
· FEMA’s Flood Mitigation Assistance program provides funding to states, territories, Tribes, and local communities for projects and planning that reduce the long-term risk of flood damage to structures insured under the National Flood Insurance Program.
Individuals who lack sufficient insurance coverage often face greater challenges in recovery. If disaster survivors are uninsured or underinsured, they may have to rely more on federal disaster assistance. Until recent regulatory changes, FEMA did not award any housing assistance to individuals who received at least the maximum FEMA award for housing repairs from their insurance company, even if there was a gap between their insurance coverage and their losses. For disasters with Individual Assistance declared on or after March 22, 2024, FEMA will now award housing assistance to those who receive insurance payouts that exceed the FEMA maximum award for their losses, up to the statutory maximums, if they have eligible unmet needs or uncovered losses.[18] FEMA officials said they expect the amounts of Individual Assistance awards to increase due to this change.
What Remains to Be Done
To address this high-risk area, agencies should better coordinate across disaster recovery programs, improve disaster assistance programs to survivors, and facilitate more significant reduction to the nation’s overall disaster risk. FEMA also needs to strengthen its disaster workforce by addressing staffing gaps. There are 63 open recommendations related to this high-risk area as of January 2025. For example:
· FEMA, HUD, and DOT should identify and take steps to better manage fragmentation between their disaster recovery programs and other federal programs.
· SBA will need to distinguish between rural and urban communities in its outreach and marketing plan and incorporate actions to mitigate challenges encountered by rural communities in accessing the Disaster Loan Program.
· FEMA should assess ways to provide assistance for immediate post-wildfire mitigation and take steps to provide such assistance.
· FEMA should identify and document lessons learned related to estimating obligations for declared catastrophic disasters.
· Department of Energy should integrate lessons learned from previous disasters into the resilience goals of its grid recovery and technical assistance efforts and better support utilities in improving resilience to hurricanes.
Congressional Actions Needed
There are four matters for congressional consideration to help address the nation’s delivery of disaster assistance. For example, Congress should consider:
· establishing an independent commission to recommend reforms to the federal government's approach to disaster recovery, and
· establishing permanent statutory authority for a disaster assistance program administered by HUD or another agency that responds to unmet needs in a timely manner and directing the applicable agency to issue implementing regulations.
Potential Benefits
By identifying and taking steps to better manage disaster assistance and the negative effects of the fragmented approach to disaster assistance, federal agencies could improve service delivery to disaster survivors and communities, improve the effectiveness of disaster recovery, and potentially reduce the federal government’s fiscal exposure.
Contact Information
For additional information about this high-risk area, contact Chris Currie, Director, Homeland Security and Justice, at (404) 679-1875 or CurrieC@gao.gov.
Funding the Nation’s Surface Transportation System
Congress should pass a sustainable funding solution for surface transportation.
Why Area Is High Risk
The nation’s surface transportation system—including highways, transit, and rail systems that move both people and freight—is aging and faces increasing demands on its use. At the same time, revenues from motor fuel and truck-related taxes supporting the Highway Trust Fund—the major source of federal surface transportation funding—are insufficient to repair and upgrade this system. Because projected spending will exceed these tax revenues, it is important that federal funding for surface transportation provided to states and other grantees through Department of Transportation (DOT) programs be spent wisely and effectively.
Area Rating
To bolster the Highway Trust Fund, Congress has cumulatively transferred about $273 billion in general revenue to the Fund on 10 occasions from 2008 through 2021, including $118 billion under the Infrastructure Investment and Jobs Act (IIJA),[19] enacted in November 2021. Without the most recent transfer under the IIJA, the Congressional Budget Office (CBO) projected that spending would have exceeded revenues in 2022. These transfers each represented a one-time infusion of funding instead of a sustainable long-term source of revenue.
Since our last update in 2023, spending from the Highway Trust Fund has continued to exceed motor fuel and truck-related taxes deposited into the fund. Specifically, under the current surface transportation reauthorization act (the IIJA), outlays from the Highway Trust Fund have exceeded revenues deposited each year. According to CBO, outlays exceeded revenues by about $8.2 billion in fiscal year 2023 and are projected to do so by about $9 billion in fiscal year 2024.
Moreover, the revenues supporting the Highway Trust Fund continue to erode. For example, if held constant, the 18.4 cent-per-gallon federal tax on gasoline will have about half of the purchasing power in 2025 relative to when federal motor fuel taxes were last raised in 1993. Growing use of electric vehicles may further reduce revenues available from motor fuel taxes on gasoline and diesel fuel. In its Annual Energy Outlook 2023, the U.S. Energy Information Administration estimated that electric vehicles would account for between 11 and 26 percent of on-road vehicles by 2050.
CBO projects that, in the absence of a sustainable, long-term funding solution for the Highway Trust Fund, an additional $211 billion from other sources will be required to maintain current spending levels plus inflation through 2034. Without additional congressional action, the balance of the Highway Trust Fund will be exhausted beginning in 2028 (see fig. 19).
Note: This projection also assumes no further augmentation of highway-related taxes to the Highway Trust Fund from general revenues or other sources. By law, the Highway Trust Fund may not incur negative balances.
To inform congressional efforts to align surface transportation revenues with spending and improve how effectively revenues are spent, we have examined (1) user-based funding alternatives to supplement eroding revenues from motor fuel taxes, and (2) DOT’s use of discretionary grant programs to better target existing spending.
User-based funding alternatives. In January 2022, we reported on a Federal Highway Administration program that provided grants to states to pilot and research user-based revenue mechanisms to support the Highway Trust Fund as alternatives to federal motor fuel taxes. Most participating states used program funds to explore mileage fee systems, which charge drivers a fee based on their miles driven.
We found that the Federal Highway Administration had not established criteria to identify whether state pilot approaches could be expanded or applied nationwide to collect revenues to support the long-term solvency of the Highway Trust Fund. We recommended that the Federal Highway Administration develop and apply criteria to do so, which would provide more information to Congress on the potential for a national mileage fee system to help maintain the long-term solvency of the Highway Trust Fund. In April 2024, we confirmed that the Federal Highway Administration had developed a framework and criteria to assess the scalability of state pilot projects. We will continue to monitor the Federal Highway Administration’s implementation of this recommendation as it uses this framework and criteria to evaluate pilot projects.
Discretionary grants. The IIJA authorized over 25 surface transportation discretionary grant programs and increased funding for some existing programs. Since November 2023, we have reported on DOT’s award process for awarding billions of dollars to applicants through a variety of discretionary grant programs. In these reviews and others over the last decade, we have identified numerous concerns with DOT’s management of its discretionary grant programs. We found:
· DOT did not take a consistent or transparent approach to evaluating and awarding discretionary grants. For example, we reported in January 2024 that DOT did not clearly define the “exemplary project” criteria it used to advance applications for potential selection for an Infrastructure for Rebuilding America award. As a result, we recommended that DOT clearly define in its Notice of Funding Opportunity and evaluation plan how an application may qualify as an “exemplary project.”
· DOT sometimes did not provide clear rationales for key selection decisions. For example, we reported in August 2024 that DOT did not fully document its rationale for rating similar applicants for an award under the Rural Surface Transportation Grants Program differently nor for requesting additional information from some but not other applicants. As a result, we recommended that DOT fully document the rationale behind key decisions related to advancing and selecting applications for award.
Discretionary grant programs can help target federal transportation spending. To achieve this, DOT should enhance the clarity and transparency of its evaluation process and its rationale for key decisions when making awards.
Congressional Actions Needed
The IIJA represented an important infusion of funds into the Highway Trust Fund, but it did not address the underlying structural problems. Congress should pass a long-term, sustainable plan for funding surface transportation. This is the pivotal action that will determine whether this issue is removed from the High-Risk List.
Benefits
Since this area was added to the High-Risk List in 2007, financial benefits to the federal government related to our work in this high-risk area totaled nearly $600 million. In addition, there were more than 40 other benefits due to progress in this high-risk area. For example:
· We recommended that Congress consider modifying federal surface transportation programs to adequately tie grant awards to federal goals and performance. The Moving Ahead for Progress in the 21st Century Act included provisions to move toward a more performance-based surface transportation program, in part by establishing national performance goals in areas such as infrastructure condition, safety, and system reliability.[20]
· We recommended that DOT develop an implementation plan for the agency’s transition to a performance-based approach. In 2018, DOT developed a plan that articulated the agency’s goals for the transition to a performance-based approach for funding surface transportation, as well as timelines and specific activities for achieving each goal.
Contact Information
For additional information about this high-risk area, contact Elizabeth Repko, Director, Physical Infrastructure, at (202) 512-2834 or RepkoE@gao.gov.
HHS Leadership and Coordination of Public Health Emergencies
The Department of Health and Human Services (HHS) must improve its leadership and coordination of public health emergencies to save lives, mitigate severe economic impacts, and prepare the nation to respond to multiple simultaneous threats.
Why Area Is High Risk
We added this area to the High-Risk List in January 2022 because of persistent deficiencies in HHS’s ability to perform its role of leading the nation’s preparedness for, and response to, public health emergencies, including extreme weather events, infectious disease outbreaks, pandemics, and intentional acts.
These deficiencies hindered the nation’s response to the COVID-19 pandemic, the 2022 mpox outbreak, and to a variety of other past emergencies, such as hurricanes. Addressing the deficiencies and related concerns we have raised is paramount as the nation continues to face emerging and concurrent threats that could affect the health and security of the nation.
Area Rating
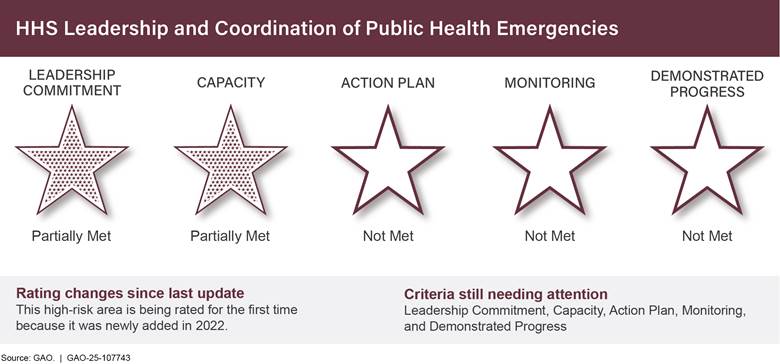
This is the first time we are rating HHS’s leadership and coordination of public health emergencies against the high-risk issue criteria since adding this area in 2022. HHS has partially met two criteria and has not met three criteria.
Leadership commitment: partially met. In September 2024, in response to the area’s high-risk designation, HHS officials informed us that the department had designated two lead agencies to manage and coordinate this high-risk area—the Administration for Strategic Preparedness and Response (ASPR) and the Office of the Assistant Secretary for Legislation. These offices will assist in leading efforts, including taking a broader coordination role to engage other HHS offices and act as the main channel of communication to the Deputy Secretary of Health and Human Services. HHS has established regular bi-annual meetings and quarterly reporting on HHS’s actions to periodically review and address this high-risk area.
In addition, HHS leadership devoted resources to develop an All-Hazards Plan, finalized in July 2024, which we reviewed. The plan describes how HHS will operationalize and coordinate its responsibility to lead the federal public health and medical response to emergencies and disasters. According to officials, the plan incorporated lessons learned from the COVID-19 pandemic and past preparedness exercises, as well as GAO findings, and involved 70 HHS staff within 18 agencies.
While efforts have begun, continued cross-agency planning and department-wide coordination is needed to further demonstrate leadership commitment. For example, in December 2024, HHS developed a coordinated, department-wide after-action program to identify and resolve recurring emergency response challenges, as we recommended. We will continue to monitor its implementation, per our April 2024 recommendation.
Further, it remains to be seen how HHS’s leadership in this area will align in practice with that of the White House, including the Office of Pandemic Preparedness and Response Policy that was stood up in July 2023. This office is charged with coordinating federal activities to prepare for, and respond to, pandemic and other biological threats. Although the new office will provide strategic policy direction, White House and HHS officials told us that HHS will continue to be responsible for leading and coordinating the public health and medical response across applicable departments and agencies.
Moreover, it is important for HHS to coordinate with its preparedness and response partners, which include other federal agencies, such as the Federal Emergency Management Agency, and nonfederal jurisdictions—states, territories, Tribes, and localities. Jurisdictions have primary responsibility for leading the preparation for and response to public health threats in their areas. Failing to coordinate can impede HHS’s response to an emergency. For example, we found that HHS did not know whether jurisdictions had isolation and quarantine plans to keep people from spreading infectious diseases. As a result, the agency did not know where to focus its emergency assistance. We have ongoing work examining HHS coordination with its public health partners.
Capacity: partially met. We have repeatedly reported on limitations of HHS’s capacity to lead and coordinate public health emergencies. For example, ASPR has not met its enrollment target for its public health emergency responder workforce since we started reporting on this topic in June 2020. As part of the National Medical Disaster System, these responders are called up to help overwhelmed jurisdictions during a public health emergency.
Workforce planning is a critical component of ensuring agency capacity to meet its mission. A strong public health infrastructure and workforce is important for the federal government to effectively respond to, and contain, public health threats. Individual agencies have taken initial steps to enhance workforce capacity, but it is too soon to determine their effect on overall capacity to address this high-risk area. For example:
· In January 2022, we reported that the Food and Drug Administration (FDA) did not have an agency-wide strategic workforce plan to coordinate human capital efforts, nor did it have performance measures in place to evaluate the effectiveness of its human capital strategies. In January 2024, FDA issued an agency-wide strategic workforce plan with performance measures, which the agency intends to refine on an annual basis, as we recommended.
· In January 2024, we reported ASPR had not conducted an agency-wide workforce assessment to prioritize the skills and competencies of greatest need to achieve the agency’s goals and mission. In March 2024, ASPR awarded a contract to a vendor to complete a workforce assessment of the entire agency in summer 2025, as we recommended. Once the assessment is completed, ASPR will need to develop strategies to address hiring needs and adhere to strategic human capital planning principles. Further, we reported ASPR had established a new in-house hiring office, but we recommended that it develop performance measures to help monitor its progress in addressing hiring concerns.
Moreover, three HHS agencies critical to public health emergencies—ASPR, the Centers for Disease Control and Prevention, and FDA—are undergoing or have recently completed reform efforts. It remains to be seen the extent to which these efforts will help provide the capacities needed to address this high-risk area. See fig. 20 for the four broad categories that can help the Congress assess proposed reforms, along with relevant sub-categories of questions, and selected key questions. We have ongoing and planned work that will allow us to continue to monitor the effects of these reform efforts on this high-risk area.
Figure 20: Categories for Key Questions to Assess Agency Reform Efforts
Action plan: not met. HHS needs to develop a specific action plan or plans that define root causes, solutions, milestones, necessary resources, and steps for implementing corrective measures to address the persistent deficiencies we have identified. Without such a plan, HHS cannot be assured that it is addressing the root causes of the deficiencies and related concerns to identify solutions that will address this high-risk area. HHS officials indicated that implementing its new coordinated, department-wide after-action program—as we recommended in April 2024—could be a tool to determine and monitor corrective actions.
Monitoring: not met. HHS cannot measure progress on addressing this high-risk area because it lacks an action plan. Action plans should contain milestones and metrics to allow HHS to monitor progress toward improving its leadership and coordination of public health emergencies.
Demonstrated progress: not met. HHS needs to address persistent deficiencies in this high-risk area. For example, we found that during recent public health emergency responses, such as for COVID-19 and mpox, jurisdictions were not clear on how and from whom to request life-saving medicines and supplies, causing confusion and delays. Additionally, Tribes did not have the facilities needed to receive and store supplies from the Strategic National Stockpile, the federal stockpile of medical supplies that can be distributed to jurisdictions during emergencies.
What Remains to Be Done
As of January 2025, 83 recommendations related to preparing for and responding to public health emergencies remain open. Additional progress could be made if HHS were to implement open recommendations related to cross-agency planning and department-wide coordination, managing risks, and developing performance measures for hiring. For example, HHS should
· implement its new department-wide after-action program;
· assess state and territorial planning for isolation and quarantine and determine whether federal actions are needed to help jurisdictions close any gaps;
· develop an approach to manage risks associated with the gaps between the Strategic National Stockpile’s supply levels and recommended quantities;
· develop a mechanism to routinely monitor, evaluate, and report on coordination efforts for infectious disease modeling across HHS;
· ensure the plan to implement the public health situational awareness and biosurveillance network includes specific near-term and long-term actions that can be completed to show progress;
· establish specific goals and performance measures for ASPR’s in-house hiring office to help address areas of concern the new office was intended to address, including service quality; and
· develop and document plans for restructuring the Public Health Emergency Medical Countermeasures Enterprise, the interagency group of experts that advises on prioritizing, developing, procuring, deploying, and effectively using medical supplies and other countermeasures for the Strategic National Stockpile.
Benefits
There were more than 40 benefits to the federal government and American people due to progress in this high-risk area since it was added to the list in 2022. For example:
· ASPR entered into a contract to conduct a strategic, agency-wide assessment of its workforce needs. This is important for ensuring the agency can meet its mission of leading the nation’s medical and public health preparedness for, response to, and recovery from disasters and emergencies.
· ASPR developed a process to evaluate the web-based and in-person training provided to emergency responders. This is a key step to helping keep these responders safe.
· HHS established a memorandum of understanding with the Department of Labor to share information related to medical devices with emergency use authorizations—which allow the temporary use of unapproved medical products during emergencies. This should improve coordination, decision-making, and guidance and regulation development between these two agencies, especially during fast-paced and often hectic emergency situations.
Contact Information
For additional information about this high-risk area, contact Mary Denigan-Macauley, Director, Health Care, at (202) 512-7114 or DeniganMacauleyM@gao.gov.
Strengthening Management of the Federal Prison System
The Federal Bureau of Prisons (BOP) needs to improve its resource management to help ensure the safety and security of its staff and incarcerated individuals, and better plan and evaluate programs that help formerly incarcerated people succeed in their communities.
Why Area Is High Risk
BOP is responsible for the care, custody, safety, and rehabilitation of approximately 155,000 incarcerated people. It is one of the largest employers at the Department of Justice (DOJ) with more than 35,000 correctional officers and staff.
We designated this area to be high-risk in 2023 because leadership changes and longstanding staffing challenges represent a serious threat to the safety of staff and incarcerated people. BOP also faces challenges with aging and deteriorating infrastructure, which likewise affects safety. It also needs improvements in planning for programs to prepare incarcerated people for release. Better monitoring and evaluation are needed to improve management of the federal prison system.
Area Rating
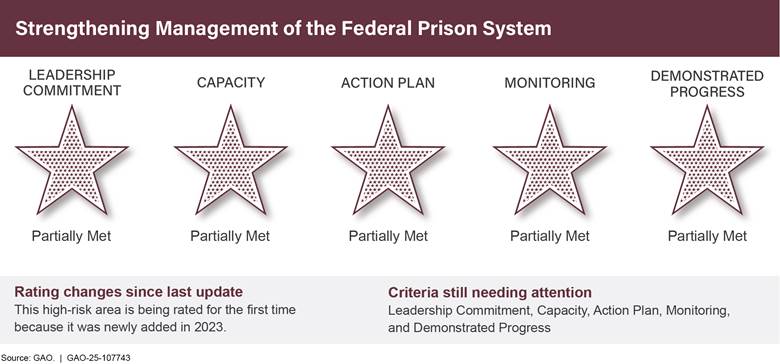
We are rating this high-risk area for the first time since it was added to the High-Risk List in 2023.
Leadership commitment: partially met. The BOP Acting Director began his term in January 2025 as the seventh Director or Acting Director serving the agency in 8 years. Prior to this, the former Director had begun to demonstrate leadership commitment through a number of initiatives and planned efforts, such as creating strategic goals and new oversight positions. While these actions have shown promise, many were recently announced and have not been fully implemented.
Further, in March 2024, the former Director agreed to a set of 22 metrics that we developed to gauge BOP’s progress in addressing this high-risk issue. These metrics include actions or efforts for BOP to improve its management of staff and resources, planning, monitoring, as well as implementation of the First Step Act of 2018.[21]
Capacity: partially met. BOP has worked to increase capacity but more attention is needed. For example, BOP clarified the number of agency personnel it needed to expand its medication assisted drug treatment program, as we recommended. Further, it began collecting more precise and useful information to identify the number of individuals in custody who have identification documents. These documents, such as a driver’s license and Social Security card, help individuals secure housing, transportation, and other supports that are needed for a successful reentry following incarceration, as shown in figure 21.
Figure 21: Examples of Situations When People Reentering the Community May Need Identification Documents
In reporting on their progress on the 22 metrics in November 2024, BOP officials described several efforts to better manage resources. For example, BOP officials used Direct Hire Authority to expedite its hiring processes. This authority allows agencies to expedite hiring by eliminating competitive rating and ranking procedures and veterans’ preference for specific positions. As a result of this and other hiring efforts, BOP realized a net increase of about 900 employees in 2024.
BOP also requested a higher salary rate for correctional officers and nurses from the Office of Personnel Management (OPM) and as of January 2025 was awaiting response. In addition, officials have begun to assess data needs and analytic capabilities to better manage operations. However, BOP is still implementing some of these efforts.
Further, BOP should develop a mechanism to determine if it is offering a sufficient amount of programs to meet the needs of its incarcerated population.
Action plan: partially met. BOP has made some progress in developing action plans. For example, BOP worked with DOJ to develop a 5-year funding proposal in November 2024 for its staffing and infrastructure needs, which it shared with the Office of Management and Budget. According to the proposal, BOP’s crumbling infrastructure is a root cause of the safety crisis and its needs total about $3 billion across more than 3,600 buildings. In addition, DOJ and OPM are reviewing BOP’s newly developed capital investment plan. However, more work is needed. For example, BOP has not developed and implemented a plan for analyzing data to help identify and address the impact of staffing challenges on staff and incarcerated people as we recommended.
Further, we found that BOP has two key mechanisms—its program review process and its administrative remedy program—that allow it to gather information from facilities about the root causes of challenges associated with restrictive housing (previously known as solitary confinement). However, BOP could better leverage these mechanisms to pursue corrective measures and ensure compliance and enhance operations, as we recommended.
Monitoring: partially met. In reporting on their progress on the 22 metrics in November 2024, BOP officials reported they reorganized their Office of Internal Affairs and hired more investigators to monitor and address employee misconduct. In addition, BOP announced several initiatives to enhance its monitoring efforts, but as of November 2024, many of these have not been fully implemented. For example, BOP announced that it is establishing a behavioral health branch to unify previously siloed branches and ensure the assessment and improvement of patient outcomes.
BOP also has assessed the effectiveness of its policies and procedures for facilitating enrollment in Medicaid or other health care coverage for individuals nearing reentry, as we recommended, helping ensure continuity of care. Further, BOP enhanced its internal tracking systems to identify and address unnecessary delays and costs for its maintenance and repair projects.
However, BOP has not fully addressed other monitoring-related issues. For example, BOP needs to address our recommendation to collect and assess data on the timeliness of risk and needs assessments and develop a process to remediate findings that occur across multiple facilities.
Demonstrated progress: partially met. Since we added management of the federal prison system to the list in 2023, BOP has made some progress addressing the metrics we developed. For example, in fiscal year 2023, BOP filled a newly created position for Chief of Addiction Medicine to further support Opioid Use Disorder treatment within BOP. Also, BOP finalized a strategic framework outlining goals, strategies, and initiatives to direct its overall improvement efforts. However, other actions to address the metrics are still in development, including updating its human capital plan and evaluating employee misconduct efforts.
Further, despite recent success with recruiting, BOP still faces staffing shortages—estimating a deficit of more than 9,500 correctional officers and about 3,000 medical professionals. It also needs to better manage its overall staffing allocations. Its use of overtime has increased annually since 2021 and is up 43 percent since that year—to almost 9 million hours in 2024.
What Remains to Be Done
To make further progress in this area, BOP needs to maintain stabilized leadership. In addition, BOP needs to sustain or fully implement its proposed action items in response to the 22 metrics we developed, including actions or efforts to improve its management of staff and resources, planning, monitoring, and implementation of the First Step Act of 2018.
As of January 2025, 25 recommendations remain open. For example, BOP should:
· develop and implement a reliable method for calculating staffing levels,
· develop and implement a plan for analyzing data to help identify and address the causes and potential impacts of staffing challenges,
· assess the outcomes of its recruiting incentives,
· collect and monitor complete and accurate data on incarcerated people’s risk and needs assessments,
· develop a mechanism to monitor if it is offering a sufficient amount of First Step Act programs and activities, and
· develop and implement a process to address any identified patterns of noncompliance related to restrictive housing policies.
Benefits
Progress in addressing this high-risk area has resulted in seven nonfinancial benefits since it was added to the List in 2023. For example:
· BOP modified its data system to identify and track disaster-related projects.
· BOP implemented its plan for managing its portfolio of drug education and treatment programs.
· BOP assessed the effectiveness of its health care policies and procedures for facilitating enrollment in Medicaid or other health care coverage.
Contact Information
For additional information about this high-risk area, contact Gretta L. Goodwin, Director, Homeland Security and Justice, at (202) 512-8777 or GoodwinG@gao.gov.
Unemployment Insurance System
The Department of Labor (DOL) needs to continue to work with states and Congress to fully execute its plan for transforming the Unemployment Insurance (UI) system to improve service to unemployed workers, align the system with the current workforce, and strengthen program integrity.
Why Area Is High Risk
In June 2022, we designated the UI system as high risk. UI is a joint federal-state system that provides temporary financial assistance to eligible workers who become unemployed through no fault of their own. We found that UI’s administrative and program integrity challenges pose significant risks to service delivery and expose the system to significant financial losses through fraud and improper payments. Long-standing challenges with UI administration and outdated IT systems have hindered states’ ability to meet the needs of unemployed workers, especially during economic downturns. Such challenges have also contributed to impaired service, declining access, and disparities in benefit distribution.
Our analysis of DOL’s estimates found that UI improper payments peaked at an estimated $78 billion in fiscal year 2021 (an estimated improper payment rate of 19 percent) and decreased to an estimated $6 billion in fiscal year 2024 (an estimated improper payment rate of 16 percent), see table 8.
|
|
Fiscal year 2021 |
Fiscal year 2022 |
Fiscal year 2023a |
Fiscal year 2024 |
|
Estimated UI improper payment amount |
$78 billion |
$19 billion |
$48 billion |
$6 billion |
|
Estimated UI improper payment rate |
19 percent |
22 percent |
32 percent |
16 percent |
Source: GAO analysis of Office of Management and Budget PaymentAccuracy.gov data. | GAO-25-107743
Note: Improper payment estimates and rates displayed in the table include both improper and unknown payments. Executive agency estimates of improper payments also treat as improper any payments whose propriety cannot be determined due to lacking or insufficient documentation. The estimated improper payment rate is the estimated amount in improper payments divided by the amount in program outlays for a given program in a given fiscal year.
aMost of the estimated improper payments reported for fiscal year 2023 occurred in the temporary Pandemic Unemployment Assistance program from April 2020 through its expiration in September 2021.
These estimated improper payments include those caused by fraud. In September 2023, we estimated that the fraud in UI programs during the pandemic—from April 2020 through May 2023—was likely between $100 billion and $135 billion.
Area Rating
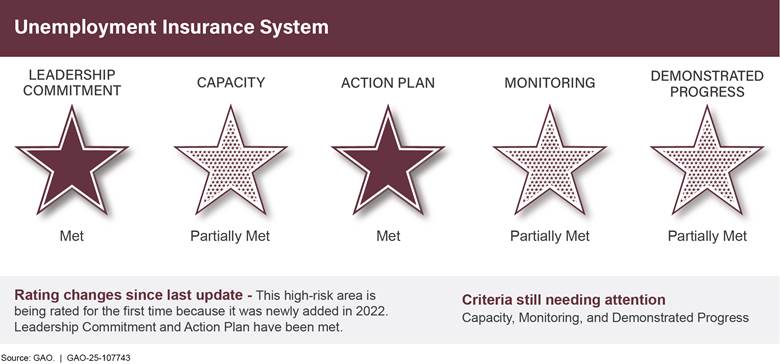
This is the first time we are rating the UI system against the high-risk criteria since designating this system as high risk in 2022. DOL has met two criteria and partially met three criteria.
Leadership commitment: met. In April 2024, in response to our high-risk designation and recommendation, DOL released a comprehensive plan for transforming the UI system. The plan includes actions at the national and state levels and recommended legislative reforms. Also, in October 2024, DOL officials told us that they created a permanent office to oversee implementation of this plan. Specifically, DOL moved the Office of Unemployment Insurance Modernization—responsible for overseeing its UI transformation efforts—from a temporary location within the Office of the Secretary into a permanent one within the Employment and Training Administration’s Office of Unemployment Insurance.
In addition, DOL’s fiscal year 2025 congressional budget justification outlines a set of principles to guide congressional efforts to reform the UI system. These principles include providing adequate benefits, reflecting the modern economy and labor force, ensuring accessibility for workers, and operating with integrity. Furthermore, Congress has held hearings on reforming the UI system. According to DOL officials, Congress enacted legislation in November 2024 that addressed one of DOL’s recommended reforms by expanding eligibility for reemployment services to all regular UI claimants. Congress has also introduced legislation that would address some of DOL’s other recommended reforms.
Capacity: partially met. We identified some of the UI system’s capacity challenges, including staffing limitations, outdated IT infrastructure, and the limited effectiveness of benefit triggers (economic criteria that extend the number of weeks of UI benefits) during economic downturns. As of September 2023, DOL had provided states with $204.2 million in grant funding from the American Rescue Plan Act of 2021 to modernize their IT systems. The funding supported efforts including migrating systems from outdated IT infrastructure to cloud-based technologies and improving the UI customer experience. However, DOL’s other key IT modernization efforts are still in progress, including an initiative that aims to change how states build and buy technology.
In addition, DOL’s UI transformation plan calls on Congress to provide sustained investments in modernizing the UI system. These investments include increasing administrative funding to better match states’ needs and providing long-term support to help states address evolving fraud risks. DOL’s Office of Inspector General also proposed that Congress extend the statute of limitations for fraud related to the pandemic UI programs. We support this proposal, which would give our oversight partners and federal law enforcement additional time to investigate and pursue fraudulently obtained payments in these programs.
Action plan: met. DOL’s UI transformation plan identifies the root causes of the UI system’s challenges and actions to address them. Specifically, the plan includes 53 actions at the national and state level to address root causes in seven areas: (1) adequately funding UI administration, (2) delivering high-quality customer service, (3) building resilient and responsive state IT systems, (4) bolstering state UI programs against fraud, (5) ensuring equitable access to robust benefits and services, (6) rebuilding and stabilizing the long-term funding of state UI benefits, and (7) strengthening reemployment and connections to suitable work.
Regarding the funding of state UI benefits, many states took federal loans to pay benefits during the pandemic, due to the high numbers of claims they received. Since June 2021, when 19 states and territories held approximately $53.5 billion in federal loans, 16 states and territories have fully repaid their loan balances. As of December 2024, two states and one territory held federal loans totaling approximately $27 billion.
DOL’s UI transformation plan also includes recommended legislative reforms for congressional action, including
· ensuring all entitled and eligible individuals experiencing employment loss receive UI’s income support,
· providing adequate benefits in every state, and
· allowing states to retain up to five percent of recovered fraudulent UI overpayments for program integrity use.
Monitoring: partially met. In January 2025, DOL officials told us that the agency was monitoring the status of the national- and state-level actions in its UI transformation plan. For example, DOL requires states that have received UI IT modernization grants to report their progress on a quarterly basis. However, as of January 2025, DOL had not measured states’ UI IT performance against established standards, as we recommended. Doing so would enhance DOL’s ability to monitor whether states' UI systems are performing efficiently and effectively.
Demonstrated progress: partially met. DOL officials told us that 47 of the 53 actions in its UI transformation plan were completed or underway as of December 2024 (see table 9). Specifically, officials said that 20 of the actions had been completed and 27 were underway. However, DOL needs to continue working with states and Congress to fully execute this plan. DOL can also demonstrate progress by implementing our UI-related recommendations and those of the DOL Office of Inspector General. These recommendations align with DOL’s principles and vision for UI reform and are critical for resolving significant risks.
Table 9: The Department of Labor’s Unemployment Insurance Transformation Plan, by Action Area and Status, as of December 2024
|
Action area |
DOL or state actions completed or underway |
DOL or state actions planned |
DOL’s recommended legislative reforms (not yet enacted)a |
|
1. Adequately funding Unemployment Insurance (UI) administration |
2 |
0 |
2 |
|
2. Delivering high-quality customer service |
7 |
2 |
0 |
|
3. Building resilient and responsive state IT systems |
5 |
0 |
0 |
|
4. Bolstering state UI programs against fraud |
12 |
0 |
9 |
|
5. Ensuring equitable access to robust benefits and services |
11 |
2 |
5 |
|
6. Rebuilding and stabilizing the long-term funding of state UI benefits |
1 |
0 |
2 |
|
7. Strengthening reemployment and connections to suitable work |
9 |
2 |
3 |
|
Total |
47 |
6 |
21 |
Source: Department of Labor (DOL), Building Resilience: A Plan for Transforming Unemployment Insurance, April 2024, and interviews with DOL officials. | GAO-25-107743
aSome of DOL’s recommended legislative reforms are relevant to multiple action areas. Specifically, DOL’s UI transformation plan lists two reforms under both action areas 1 and 4. For the purposes of this table, we count them once, under action area 4.
What Remains to Be Done
Since we added the UI system to the High-Risk List in June 2022, DOL has implemented 13 of our recommendations. As of January 2025, 14 recommendations to DOL remain open, five of which we consider to be priority recommendations. Addressing these recommendations will help DOL make progress in this high-risk area. For example, DOL should
· fully execute its UI transformation plan,
· measure states’ UI IT performance against established standards,
· assess lessons learned from the pandemic to inform its future disaster response efforts and support Congress on ways to address future emergencies, and
· study and advise Congress and other policymakers on various options to systematically support self-employed and contingent workers—who are generally ineligible for UI—during periods of involuntary unemployment.
Benefits
Strengthening the UI system—which we added to the High-Risk List in 2022—can improve service to unemployed workers and reduce the system’s exposure to financial risks. By addressing audit recommendations, including fully executing its UI transformation plan, DOL may achieve quantifiable results in reducing improper payment rates, including those caused by fraud; improving efficiency in claims processing and restoring pre-pandemic payment timeliness levels; better reaching current worker populations; and enhancing equity in benefit distributions.
Contact Information
For additional information about this high-risk area, contact Thomas Costa, Director, Education, Workforce, and Income Security, at (202) 512-7215 or CostaT@gao.gov.
DOD Approach to Business Transformation
The Department of Defense (DOD) should continue to institutionalize its new approach to business transformation by implementing consistent monitoring and reporting to demonstrate progress on its performance improvement efforts. Once fully institutionalized, and if effectively implemented, this approach should support the department’s efforts to achieve and sustain business reform.
Why Area Is High Risk
DOD spends tens of billions of dollars each year to maintain key business operations intended to support the warfighter. These operations include systems and processes related to the management of contracts, finances, the supply chain, support infrastructure, and weapon systems acquisition. Weaknesses in these areas adversely affect DOD’s efficiency and effectiveness. They also render its operations vulnerable to waste, fraud, and abuse. DOD’s approach to transforming these business operations is linked to its ability to perform its overall mission and support the readiness and capabilities of U.S. military forces.
We designated DOD’s approach to managing business transformation as a high-risk area in 2005 because DOD had not taken the necessary steps to achieve and sustain business reform on a broad, strategic, department-wide, and integrated basis. In addition, it did not initially have an integrated plan for business transformation improvements.
However, DOD has made sustained progress, including maintaining senior leadership’s commitment and use of its Strategic Management Plan to guide performance improvement efforts. DOD has also established mechanisms to monitor and report on its efforts, but those have not yet been fully implemented.
Area Rating
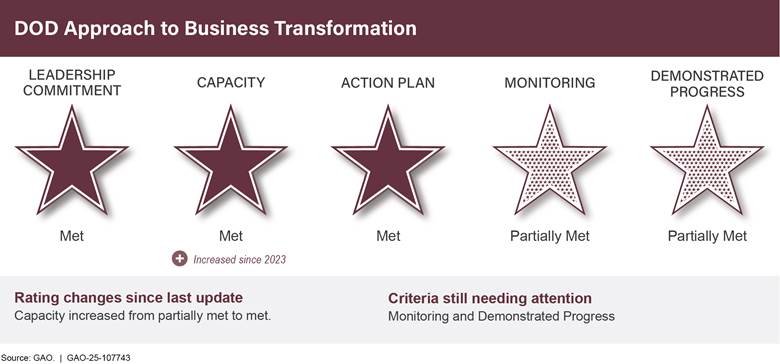
DOD has continued to make significant progress in developing an approach to business transformation through its performance improvement efforts. Since our last update, we have increased the capacity rating from partially met to met. The ratings for all other criteria remain unchanged.
Leadership commitment: met. DOD senior leadership has continued to demonstrate a strong commitment to the department’s approach to performance improvement. For example, the Deputy Secretary of Defense designated a set of priority performance improvement initiatives in August 2023 and directed the Performance Improvement Officer (PIO) to conduct regular assessments of these initiatives. In addition, the Deputy Secretary appointed new high-level governing bodies to be responsible for the department’s Strategic Management Plan (SMP). The Deputy Secretary also established a new council to support the plan’s management as well as other aspects of the department’s performance improvement efforts.
DOD has also maintained dedicated leadership positions responsible for performance improvement efforts. For example, DOD has continued the Director of Administration and Management’s role as the department’s PIO and made the Deputy PIO role a career position. The National Defense Authorization Act for Fiscal Year 2025 established the position of DOD Performance Improvement Officer in statute and gave the position responsibilities related to performance improvement; business reform and transformation efforts; and the SMP.[22] In addition, each of the DOD components and principal staff assistants have designated performance improvement and data leaders within their individual organizations.

Capacity: increased to met. Since 2022, DOD has increased staffing for its Performance Improvement Directorate from 15 staff to 56 with an additional 13 authorized but vacant as of September 2024. The directorate has also continued developing and using tools that enhance capacity, such as the department’s Advana data analytics platform.[23] For example, DOD is updating its Business Health Metrics application—which provides DOD leaders with an overview of how the department’s business operations are performing—in response to a provision in the National Defense Authorization Act for Fiscal Year 2024.
The department has also taken steps to ensure that DOD components and principal staff assistants have the capacity to support performance improvement efforts. For example, the Navy’s Performance Improvement Office has increased its staff to 19 after having reduced it to 8 in early 2022.
Further, DOD has conducted initial assessments to determine whether it has the needed funding, staff, and other capabilities to support the Deputy Secretary of Defense’s priority performance improvement initiatives. For example, DOD used the results of an initial assessment on warehouse utilization to propose additional resources supporting the initiative’s capacity as part of DOD’s budget process.
Action plan: met. DOD has continued to update goals and measures in its Strategic Management Plan (SMP) through its annual performance plans and performance reports required by law.[24] The department has begun using Advana applications, such as Strategic Priorities Metrics—its application for tracking implementation of the SMP—in reviews by senior leaders and governance bodies. DOD also uses it to prepare the department’s annual performance plans and reports.
DOD has incorporated the SMP into other department processes, including the Planning, Programming, Budgeting, and Execution process. For example, the department aligned some investments in its fiscal year 2025 budget overview with strategic priorities in the SMP. DOD plans to further incorporate the SMP into its budget process in fiscal year 2026 and beyond.
Monitoring: partially met. DOD has taken important steps to establish department-wide monitoring of performance improvement initiatives, but some of these efforts have yet to be fully implemented. Using the Performance Improvement Framework it established in October 2022, DOD identified 79 performance improvement initiatives in its prior two budget submissions. DOD also reported on the accomplishments from some of its performance improvement initiatives as a part of its Fiscal Year 2024 Annual Performance Report, released in January 2025.
DOD also initially assessed its priority performance improvement initiatives and identified metrics to enable ongoing monitoring. As of October 2024, however, DOD leadership had not approved those metrics nor used them to monitor those initiatives. Regular collection and monitoring of information on the performance improvement initiatives—including its priority initiatives—over time would help the department to both show progress and make necessary changes to the initiatives.
Demonstrated progress: partially met. DOD has taken significant action to establish its new approach to business transformation and to institutionalize this approach into its systems, processes, and governance structures. For example, DOD took action to sustain its leadership commitment and build its capacity to oversee reform. In addition, DOD has continued to report progress in implementing its SMP, including that it met or exceeded about three-quarters of its performance measure targets in its Annual Performance Report for Fiscal Year 2023.
With this business transformation approach now nearly in place, DOD’s attention has turned to implementation. Once fully institutionalized, and if effectively implemented, the department should be able to achieve and sustain business reform on a broad, strategic, department-wide, and integrated basis. Assessing and reporting on the results of its performance improvement initiatives over time will be critical for the department to demonstrate that these efforts are leading to meaningful improvements.
For more than a decade, DOD and Congress have experimented with different organizational structures to try to facilitate successful reform within the department. We have assessed many of these structures and the initiatives that have resulted from them and found that demonstrating sustained progress has been a frequent challenge for the department. By strengthening its monitoring of reform initiatives and demonstrating that its efforts are resulting in improved outcomes, the department should be positioned to address these challenges.
What Remains to Be Done
DOD needs to demonstrate that its approach is leading to positive effects on its performance improvement efforts, including meaningful improvements to DOD's business operations. Specifically, DOD should:
· conduct regular assessments of its performance improvement initiatives, including its priority initiatives;
· consistently report on the activities and resulting accomplishments of its efforts, as required by statute;[25] and
· demonstrate that its established approach to business transformation is resulting in improved outcomes.
Two of our recommendations related to this high-risk area remain open as of January 2025, including that DOD:
· routinely and comprehensively monitor and evaluate ongoing efficiency initiatives, including establishing baselines from which to measure progress, periodically reviewing progress made, and evaluating results; and
· develop and issue guidance clarifying the requirements for using Business Health Metrics.
We plan to evaluate the extent to which DOD demonstrates these regular assessments and reporting during the next budget cycle and through related efforts.
Benefits
Progress in the DOD approach to business transformation high-risk area resulted in more than $50 million in financial benefits and 20 other benefits since it was added to the List in 2005, including:
· implementing a consistent, department-wide time-to-hire measure, and
· identifying time frames and deliverables for a new department-wide human resource IT system.
Contact Information
For additional information about this high-risk area, contact Alissa H. Czyz, Director, Defense Capabilities and Management, at (202) 512-4300 or CzyzA@gao.gov.
DOD Business Systems Modernization
The Department of Defense (DOD) needs to improve management of its business systems acquisitions by enhancing its investment management guidance and completing planned updates to its federated business enterprise architecture.
Why Area Is High Risk
DOD spends billions of dollars each year to acquire and modernize business systems, including ones that address key areas such as personnel, financial management, health care, and logistics. However, significant challenges impede DOD’s efforts to improve this systems environment. For FY 2024, the department requested approximately $43.3 billion for its unclassified IT investments, including its major IT and other business programs which are intended to help the department sustain its key business operations. Further, DOD plans to spend $9.1 billion from FY 2022 through FY 2024 on 21 selected major IT business programs.
This high-risk area comprises three segments that address critical challenges facing DOD. First, business systems acquisition management should be improved to achieve better cost, schedule, and performance outcomes. Second, DOD’s portfolio of business system investments should be managed more effectively and efficiently. Finally, DOD’s federated business enterprise architecture should be leveraged to help it identify and address potential duplication and overlap.
Overall Area Rating
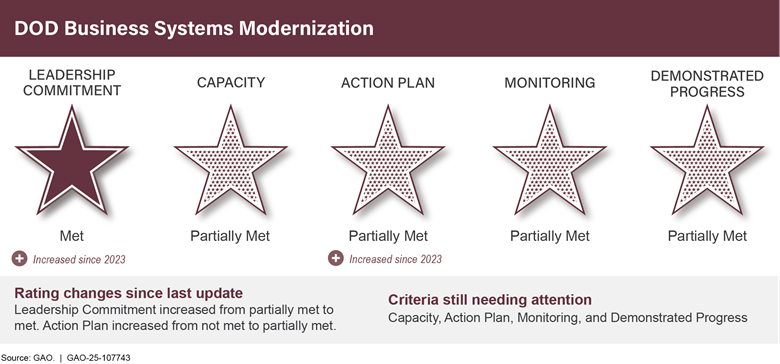
Since our 2023 update, leadership commitment increased from partially met to met. In October 2023, the Secretary of Defense issued a department-wide memorandum calling for the department to take steps to remove DOD business systems modernization from the High-Risk List. The memorandum also called for the department’s Chief Information Officer (CIO) to accelerate the retirement of noncompliant legacy defense business systems. These actions contributed to progress in multiple segments for this area.
The rating for action plan increased from not met to partially met, while the ratings for the remaining three criteria are unchanged.
DOD’s Business Systems Acquisition Management
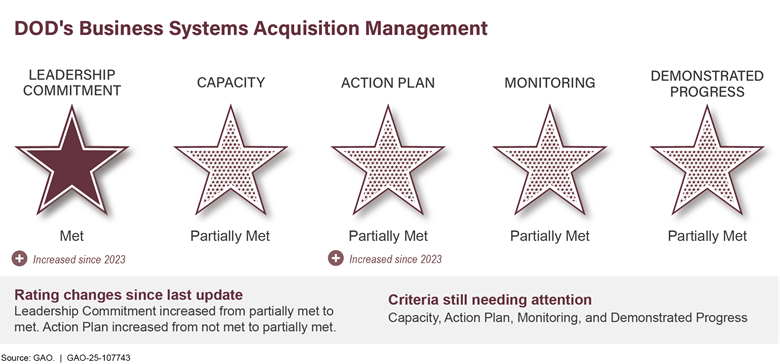
Leadership commitment: increased to met. Since our last update, the department exercised consistent leadership to help ensure that it addresses management weaknesses related to defense business systems acquisitions. For example, DOD has established and maintained stable roles and responsibilities formerly held by the Chief Management Officer, a position that was repealed by the National Defense Authorization Act (NDAA) for 2021.[26]
According to officials from the Office of the DOD CIO, the department reconstituted the Defense Business Council, responsible for overseeing DOD’s business system investments and issuing associated guidance, in October 2023. In addition, since February 2023, the Office of the DOD CIO has frequently discussed with us the department’s plans and actions for addressing this high-risk area. According to department officials, as of January 2025, the department does not yet have a signed charter for the reconstituted Defense Business Council due to a requirement in the NDAA for Fiscal Year 2025 calling for the department’s Performance Improvement Officer to co-chair the council.
Capacity: partially met. We reported in July 2024 that, according to DOD officials, to address employee turnover, DOD is providing leadership and staff with the knowledge and skills needed to understand modern software development. This includes, for example, Agile software development. Agile development uses an iterative approach where software is continuously evaluated on its functionality, quality, and customer satisfaction. Further, the department plans to leverage a January 2020 human capital analysis that included planned actions and reviews intended to, among other things, identify skills and other resource gaps.
According to department officials, they are working to determine the appropriate next steps to identify skills and resource gaps as originally documented in the January 2020 human capital analysis. However, DOD officials did not provide a date for when they anticipate developing a plan for revamping the actions identified in the human capital analysis.
Action plan: increased to partially met. DOD developed a draft action plan for FY 2025 that includes a roadmap with specific actions and associated milestones to help the department to improve management of its portfolio of defense business systems. The plan documents when the department plans to issue updates to its key acquisition guidance, including DOD Instruction 5000.75, which governs defense business systems acquisitions. Officials stated they intend to finalize the plan by the end of January 2025.
Further, the draft plan does not include all elements of an effective action plan, such as identifying responsible parties and the resources needed to implement corrective actions.
Monitoring: partially met. DOD provides information about its major business system investments to the Federal IT Dashboard. This dashboard is a public website that allows federal agencies and the public to view details of federal IT investments and to track their progress over time. For example, we reported that more than half of the DOD IT business programs we reviewed fully reported performance data associated with their efforts to achieve operational performance goals. Such information may allow DOD and the public to monitor progress in improving business system acquisition outcomes.
However, the remaining programs did not fully report the required performance metrics data. Further, DOD’s draft action plan, if approved, can serve as the basis for monitoring progress over time.
Demonstrated progress: partially met. DOD has had mixed success in implementing business system investments that meet cost, schedule, and performance commitments. For example, DOD reported varied progress on performance to the dashboard (see fig. 23 for programs’ reported performance metrics and progress toward achieving their goals).
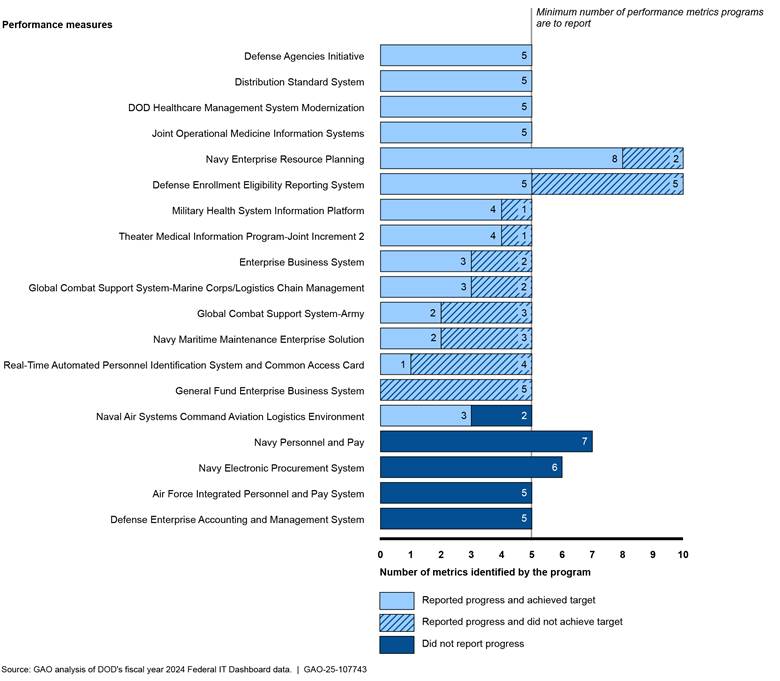
DOD’s Business Systems Investment Management Process
Leadership commitment: increased to met. Since our last update, the department has maintained stable roles and responsibilities. Further, in October 2024 the department published its updated Defense Business Systems Certification and Management Guidance, which documents the oversight process for defense business systems. In addition, according to officials, in November 2023, the Defense Business Systems Cross Functional Board, which is Chaired by the DOD Deputy CIO for Information Enterprise, was established to, among other things, develop oversight processes for defense business systems.
Capacity: partially met. As of September 2024, officials from the Offices of the Director of Administration and Management and the DOD CIO expect that the department’s 2020 human capital analysis will help inform progress addressing capacity challenges for this segment. As noted earlier, DOD officials did not provide a date for when they anticipate developing a plan for revamping the actions identified in the human capital analysis.
Action plan: increased to partially met. The draft action plan described earlier includes specific actions and associated milestones to address remaining actions for this segment. The draft action plan documents, among other things, when the department plans to issue updates to its key investment management guidance. As noted earlier, the draft plan is still pending final approval. Further, the draft plan does not include all elements of an effective action plan, such as identifying resources needed to implement the corrective actions, developing performance metrics to evaluate progress, and being accessible and transparent to other agencies, Congress, and the public.
Monitoring: increased to partially met. DOD’s draft action plan could also help to monitor broader progress in improving the business system investment management process. For example, the draft plan includes milestones and metrics such as updating the investment management guidance by the third quarter of FY 2025. The plan is pending approval, but once finalized, could serve as a basis for monitoring progress in this segment over time.
Demonstrated progress: partially met. DOD has reassigned responsibilities for updating its business systems investment management guidance, after the Chief Management Officer position was dissolved. Nevertheless, DOD needs to show continued progress in addressing our recommendations associated with the investment management process, such as improving department-wide investment management guidance to include all elements called for in our recommendations. For example, we reported that the department’s investment management guidance should fully describe what documentation is required to substantiate compliance with the statutory requirements documented in our report, including, among other things, ensuring that systems have valid, achievable requirements, and that they comply with the department’s auditability requirements.
DOD’s Federated Business Enterprise Architecture
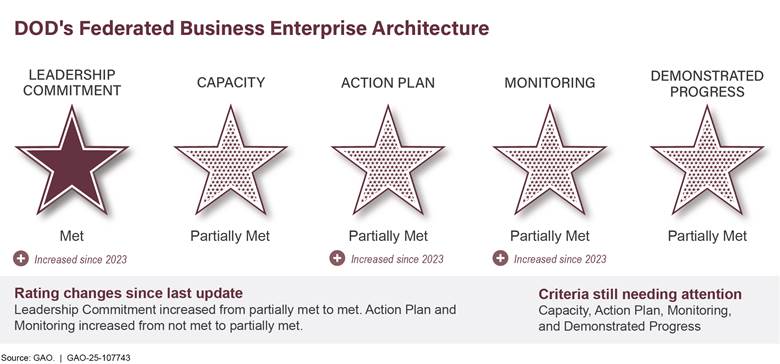
Leadership commitment: increased to met. DOD’s business enterprise architecture is a tool to provide DOD with the capacity to make sound investment decisions. It also serves as a blueprint for the department’s business transformation efforts. In January 2024, DOD published its Business Enterprise Architecture Framework, which describes the purpose, background, and vision for DOD's business enterprise architecture modernization. The framework also describes the Defense Business System Cross Functional Board, which is to oversee, among other things, establishing and maintaining the business enterprise architecture.
In addition, Office of the DOD CIO officials stated they plan to publish a business enterprise architecture guidebook by the end of the second quarter of FY 2025. This guidebook is to describe business enterprise architecture governance, roles and responsibilities, use cases, use of enterprise-level architecture tools, and best practices for DOD business architecture development.
Capacity: partially met. In September 2024, officials from the Office of the DOD CIO stated that the department has identified principal staff assistants to validate the 17 end-to-end business processes and associated content in the business enterprise architecture. Nevertheless, as noted earlier, the department needs to ensure that it has the appropriate skills and resources, including the skills and resources for completing planned updates to the architecture.
Action plan: increased to partially met. DOD has developed a draft action plan to identify actions necessary to make broader progress in improving its business enterprise architecture efforts, which includes completing updates to the architecture during fiscal year 2025. As noted earlier, the plan is pending approval but still missing some elements of an effective action plan.
Monitoring: increased to partially met. DOD identified updates to its business enterprise architecture in its draft action plan, which includes tasks and associated milestones that it can monitor as it works to address this high-risk area. As noted earlier, the plan is still pending approval. Nevertheless, such an action plan can serve as a basis for monitoring progress over time.
Demonstrated progress: partially met. DOD’s Business Enterprise Architecture Framework demonstrates progress in this segment since our 2023 High-Risk update. However, the department needs to complete its related efforts, including publishing its Business Enterprise Architecture Guidebook and completing planned updates to its architecture. In addition, the department needs to demonstrate that it is using its updated business enterprise architecture to guide its modernization efforts.
Further, DOD needs to demonstrate progress in addressing our remaining open recommendations. These include actively and consistently assessing potentially duplicative or overlapping systems, clarifying roles and responsibilities for its business enterprise architecture, and integrating its business and IT architectures.
What Remains to Be Done
DOD needs to take action to finalize an effective action plan to improve the management of its portfolio of defense business systems, fully identify and report the required performance metric data of its remaining programs, improve department-wide investment management guidance, and publish its Business Enterprise Architecture Guidebook and compete planned updates to its architecture.
As of January 2025, 21 recommendations remained open. DOD needs to
· update business system investment management and acquisition policy and guidance;
· finalize a plan, document performance measures, and clarify roles and responsibilities for improving its business enterprise architecture;
· develop and implement plans for documenting detailed system compliance with the business enterprise architecture;
· clarify the CIO role, address supply chain risk management, and ensure that major IT business programs report on required performance metrics, as appropriate, as part of the department's submission to the Federal IT Dashboard; and
· ensure that IT business programs developing software use the metrics and management tools required by DOD and consistent with those identified in GAO's Agile Assessment Guide.
Benefits
We have identified more than $3.6 billion in financial benefits and more than 60 other benefits since this area was added to the High-Risk List in 1995. For example:
· DOD avoided approximately $2 billion in expenditures on planned IT investments by improving its approach to modernizing its business systems.
· DOD avoided almost $1 billion in planned program expenditures when it cancelled the Air Force's Expeditionary Combat Support System because of issues with program life-cycle costs and implementation weaknesses.
· DOD avoided approximately $168 million by identifying and eliminating duplicative systems and terminating legacy systems.
· DOD completed business process reengineering documentation for the Army’s Integrated Personnel and Pay System. This helps ensure that its business processes are streamlined and as efficient as practicable.
· DOD improved the information used to develop its budget requests and make oversight decisions. This reduces the risk that it will make investment decisions based on unreliable information.
Contact Information
For additional information about this high-risk area, contact Vijay A. D’Souza, Director, Information Technology and Cybersecurity, at (202) 512-7650 or DSouzaV@gao.gov.
DOD Contract Management
The Department of Defense (DOD) needs to improve its management of contracts for service acquisitions by ensuring requirements are reviewed and validated and budget needs are forecasted.
Why Area Is High Risk
DOD spends hundreds of billions of dollars annually on contracts for goods and services. If these contracts are not well managed, the department would lack the information needed to make informed and cost-effective decisions and reduce its vulnerability to various risks. For these reasons, we added DOD’s contract management to our High-Risk List in 1992. Since then, DOD has made progress addressing various challenges, such as increasing the size and skills of its acquisition workforce responsible for contract management.
More recently, however, DOD has experienced challenges in two areas: service acquisitions and operational contract support (OCS). Service acquisitions include management, IT, and administrative support, whereas OCS pertains to supplies, services, and construction for deployed military forces around the world. Validating requirements for service acquisitions and forecasting the associated budget needs can help ensure that DOD’s service acquisitions are not duplicative and consider anticipated spending. Issuing department-wide guidance for OCS and embedding it into training and planning can help ensure consistency and preparedness during military operations.
Overall Area Rating
The overall ratings for two of the five criteria—action plan and monitoring—have increased from partially met to met since 2023. Specifically, DOD created an action plan to address the remaining challenges for service acquisitions and improved its monitoring thereof. The following sections present more detailed information on service acquisitions and OCS. Because DOD has made significant progress improving its OCS functions and achieved a met rating for all five criteria, we are removing this segment from the High-Risk List.
Service Acquisitions
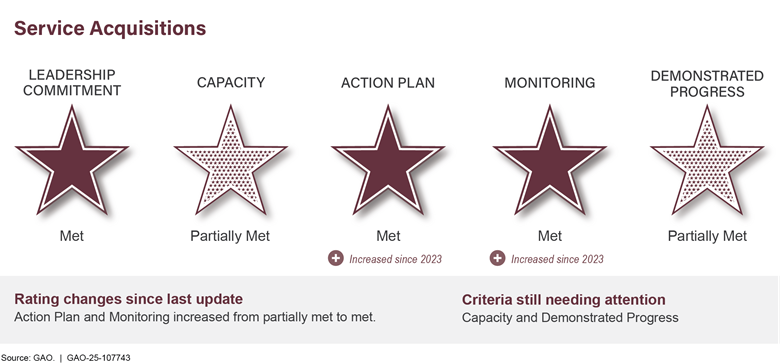
Leadership commitment: met. DOD has maintained its commitment to improve service acquisitions by revising key policies and establishing a venue for overseeing and managing service contracts. Specifically, DOD revised its service acquisition policy in January 2020 to clarify the purpose, timing, and data for the reviews that validate each service requirement, as we recommended. DOD plans to revise this policy again by September 2025 to codify annual department-wide reviews of service requirements. These annual reviews—the most recent of which was in fiscal year 2024—assess service acquisition policies and processes and provide an opportunity to identify lessons learned, best practices, and DOD-wide efficiencies.
In June 2023, DOD also established the Services Acquisition Executive Steering Committee and associated working groups, as we recommended. The committee brings together personnel from various communities within DOD that can sometimes be siloed, such as requirements and budgeting, to identify ways to improve service acquisitions.
Capacity: partially met. DOD is taking steps to demonstrate it has the department-wide capacity to oversee service acquisitions. For example, DOD reinstituted annual department-wide reviews of service requirements and delegated responsibilities for these reviews to personnel in the office of the Deputy Under Secretary of Defense for Acquisition and Sustainment. For the fiscal year 2024 review, these personnel conducted 40 meetings from February to March 2024 covering 197,000 contracts worth $163 billion in obligations.
While the Navy has designated an official to aggregate and review service requirements to identify efficiencies, the Army and Air Force are still working to identify personnel to conduct similar annual reviews on a recurring basis, as we recommended. We have previously reported that personnel who are assigned to key positions often have multiple and competing responsibilities, resulting in capacity issues, and, in turn, minimal effect on how DOD manages service acquisitions.
Action plan: increased to met. DOD drafted an action plan to fully address the remaining challenges for service acquisitions. In its October 2024 action plan, DOD identified three strategic actions to improve service acquisitions: (1) using budget needs collected during service requirement reviews to inform annual budget submissions; (2) conducting department-wide reviews of service requirements; and (3) revising its service acquisition policy. DOD’s action plan identified the offices responsible for these actions, the required resources, potential obstacles, and completion time frames.
DOD’s action plan also identified several actions to manage service acquisitions more strategically. Specifically, DOD’s Service Acquisition Working Group will convene monthly or as required to identify actions to improve the oversight, management, and execution of service acquisitions. Additionally, DOD’s Services Acquisition Executive Steering Committee will convene twice a year or as required to consider, prioritize, and approve any recommended actions to improve service acquisitions. Further, DOD uses category management—an Office of Management and Budget-led initiative to help agencies buy more strategically and achieve efficiencies—to better manage its spending for both goods and services.
Monitoring: increased to met. DOD has taken various steps to monitor service acquisitions, as required by policy. Most notably, in fiscal year 2024, the Deputy Under Secretary of Defense for Acquisition and Sustainment restarted the department-wide reviews of service requirements. These annual reviews assess the effectiveness of service acquisition policies and processes by analyzing data and identifying lessons learned, best practices, and DOD-wide efficiencies. In June 2024, the department issued a memorandum that captured the common themes, best practices, and needed actions from the fiscal year 2024 review.
DOD has also developed a dashboard that tracks spending for service acquisitions that was made available department-wide in November 2024. Further, DOD established a separate working group under the Services Acquisition Executive Steering Committee that will meet monthly or as required to identify ways to improve the oversight, management, and execution of service acquisitions.
Demonstrated progress: partially met. DOD has continued to make strides over the last several years to improve service acquisitions. For example, DOD has issued policies and direction, established multiple working groups, reinstated department-wide annual reviews of requirements, and collected the first 5-year forecasts of budget needs. DOD also plans to revise its service acquisition policy again by September 2025 to codify annual department-wide reviews of service requirements.
Actions are still under way to ensure that a senior official at the military departments regularly aggregates and reviews service requirements to identify efficiencies, as we recommended. The Navy has designated an official, and the Air Force and Army anticipate having the same by June 2025. DOD is also still trying to determine the best methodology to forecast budget needs for service contracts, as we recommended. DOD plans to assess the 5-year forecasts submitted so far and determine the best methodology moving forward by June 2025.
Operational Contract Support
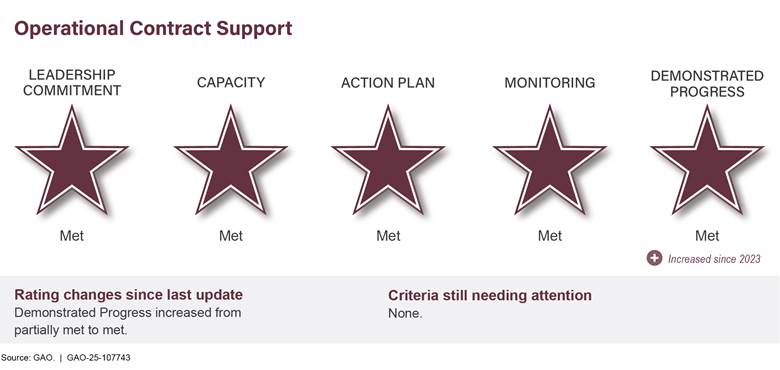
Leadership commitment: met. DOD sustained its leadership commitment and support to address OCS issues. For example, DOD repeatedly updated guidance on roles and responsibilities for OCS planning and execution throughout the department in 2017, 2020, 2022, and 2024. These updates included identifying responsibilities of the Deputy Assistant Secretary of Defense (Logistics) related to both OCS and vendor threat mitigation (previously known as vendor vetting). Also, in March 2020, DOD expanded the role of the Functional Capabilities Integration Board—senior leaders’ primary forum for OCS issues—to include recurring quarterly updates on OCS capabilities to improve support to military operations.
Capacity: met. DOD addressed OCS capability shortfalls that previously created risks to operational effectiveness, timelines, and resource expenditures. For example, DOD completed all 15 actions outlined in the August 2018 Joint Requirements Oversight Council memorandum aimed at improving policy, education, personnel, and force structure analysis.
DOD also created a functional competency model with nine OCS-specific skills against which to assess DOD civilians. According to DOD officials, this model helps inform education, training, hiring practices, and other manpower decisions, such as the development of a first-ever OCS manpower study. However, in September 2020, DOD dissolved the Joint Contingency Acquisitions Support Office, which provided OCS support to combatant commands. To ensure this OCS capability is not lost, DOD officials said they are developing training for OCS planners at the combatant commands.
Action plan: met. In February 2023 and June 2024, DOD issued its tenth and eleventh OCS Action Plans. The plans provide goals and objectives to measure DOD’s progress addressing OCS capability shortfalls in five areas: training, education, lessons learned, policy changes, and emerging requirements.
Monitoring: met. DOD maintains several formal and informal groups to monitor OCS progress, such as the Functional Capabilities Integration Board and its Council of Colonels, the Vendor Threat Mitigation Working Group, and the OCS Data and Information Group. These groups meet regularly and are co-chaired by senior officials in the Office of the Secretary of Defense and Joint Staff. Specifically, these groups track how well DOD has addressed the OCS capability shortfalls identified in the annual OCS Action Plans.
Demonstrated progress: increased to met. DOD has made significant progress improving its OCS functions. For example, DOD issued a directive formalizing DOD policy and responsibilities on assessing and responding to risks posed by vendors who oppose U.S. interests, as we recommended. Further, two combatant commands—Africa and Indo-Pacific—issued command-specific vendor threat mitigation guidance.
Additionally, in November 2024, DOD revised its primary OCS instruction detailing, among other things, how OCS should be integrated throughout the department, including into operation plans and training. Specifically, the instruction directs the military departments to, among other things, develop requirements for contingency contract administrative services in operation plans for theater support contracts. The instruction also provides details on integration of OCS into planning efforts, including as part of operation plans. Moreover, the instruction directs the military departments to provide relevant OCS training and related material to personnel supporting OCS efforts, assess and report lessons learned from OCS efforts, and implement OCS initiatives. As a result of these actions, DOD should be better positioned to identify, obtain, and manage contractor support during contingency operations.
What Remains to Be Done
Attention is needed to forecast budget needs and aggregate and review service requirements for DOD’s service acquisitions. As of January 2025, there were four open recommendations related to this high-risk area. For example, to enhance management of its service acquisitions, DOD needs to
· finalize efforts to identify data sources and implement a methodology for forecasting budget needs for service contracts across a 5-year period; and
· update military department guidance to ensure service requirements are collectively prioritized, aggregated, and reviewed on a recurring basis by a senior official to identify efficiencies.
Benefits
Improvements in DOD’s contract management over the past 19 years have resulted in about $50.9 billion in financial benefits and more than 300 other benefits since we added this area to the High-Risk List in 1992. For example:
· DOD’s and other federal agencies’ increased use of category management—the Office of Management and Budget-led effort to help agencies buy more strategically and achieve efficiencies—has resulted in more than $48 billion in cost savings. For 3 of the last 5 fiscal years (fiscal years 2020–2024), DOD has met at least 90 percent of the Office of Management and Budget’s established goals for category management.
· DOD increased the size and skills of its acquisition workforce. A skilled acquisition workforce is vital to maintaining military readiness, increasing DOD’s buying power, and achieving savings.
· From 2011 through 2024, DOD implemented solutions to institutionalize and improve OCS capabilities, including the development of 11 annual action plans to track progress toward key goals to address capability shortfalls in training, education, lessons learned, policy changes, and emerging requirements.
Contact Information
For additional information about this high-risk area, contact William Russell, Director, Contracting and National Security Acquisitions, at (202) 512-4841 or RussellW@gao.gov.
Emergency Loans for Small Businesses
The Small Business Administration (SBA) needs to further improve its oversight of emergency loans for small businesses by developing analytics to detect improper payments and addressing weaknesses that its financial statement auditor reported.
Why Area Is High Risk
From March 2020 through March 2022, SBA made or guaranteed more than 16 million loans and grants through the Paycheck Protection Program (PPP) and the COVID-19 Economic Injury Disaster Loan (COVID-19 EIDL) program. This process provided about $1.1 trillion in emergency funding to help small businesses.
SBA quickly set up these programs to respond to the adverse economic conditions small businesses faced during the COVID-19 pandemic. But quick implementation left SBA susceptible to making improper payments (those made in incorrect amounts or that should not have been made at all, including fraudulent activity). In November 2024, SBA’s financial statement auditor reported that for the fifth consecutive year, deficiencies associated with the two programs led to SBA being unable to ensure that loans went to (or were forgiven for) eligible borrowers.
Area Rating
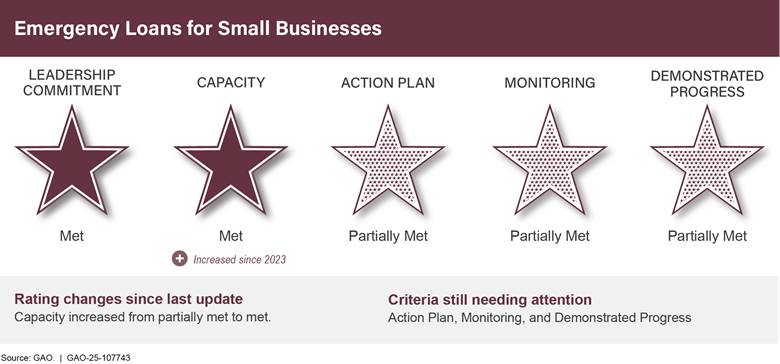
We have increased the rating for capacity from partially met to met since our 2023 report. The ratings for all other criteria remain unchanged. Although SBA has increased its capacity to address fraud in its emergency loans for small businesses, issues remain, as summarized below.
Leadership commitment: met. Since 2023, SBA has made senior executives responsible for managing its efforts to resolve concerns identified by its financial statement auditor and us. For example, SBA’s Chief Financial Officer is now responsible for coordinating SBA’s efforts to address financial statement auditor concerns. Additionally, in January 2024, SBA created an Office of Enterprise Integrity. The office, led by the Chief Risk Officer and overseen by the Chief Financial Officer, is responsible for the agency’s enterprise and fraud risk management functions. Finally, in June 2024, SBA formed a Fraud Data Analytics Team that will finalize SBA’s data strategy for fraud risk. This new team is chaired by the Chief Risk Officer and reports to SBA’s Fraud Risk Management Board.
In addition, SBA continues to have dedicated groups to address other areas of concern. These include a Fraud Risk Management Board that serves as SBA’s antifraud entity; an Enterprise Risk Management Board that manages agency-wide risks, such as those posed by its emergency loan programs; and a Senior Management Council that focuses on internal controls. These groups consist of officials from across the agency.
Capacity: increased to met. We previously reported that SBA’s Fraud Risk Management Board did not have a permanent program manager. Since then, SBA has hired a Chief Risk Officer and a program manager. The Chief Risk Officer is responsible for, among other things, ensuring risk-management activities across SBA are coordinated and internal controls are designed and implemented. The program manager is responsible for developing and implementing fraud risk processes, tools, policies, standards, and procedures in alignment with our fraud risk management framework and best practices.
In addition, SBA employed a contractor to support the Fraud Data Analytics Team. This contractor is helping the team implement a fraud data analytics strategy (discussed below).
Action plan: partially met. In November 2024, the financial statement auditor reported that material weaknesses remained in SBA’s controls over PPP and COVID-19 EIDL. For example, the auditor found that SBA did not sufficiently design the review process for PPP loan forgiveness. SBA also did not adequately design and implement controls to ensure that COVID-19 EIDL loans were issued to eligible borrowers and accurately recorded. According to SBA, it has made efforts to strengthen internal controls and will continue remediation efforts in the coming year. In January 2025, SBA finalized a remediation strategy for its financial statement audit. Among other things, the strategy identifies the highest priority target areas, remediation steps, and target dates to complete those steps.
In addition, SBA approved a fraud data analytics strategy in May 2024. The strategy outlines eight goals for SBA to implement over the next 3–5 years, identifies existing gaps, and includes activities to help SBA overcome the gaps and achieve its goals. For example, while the strategy envisions a centralized fraud analytics entity to standardize activities across SBA, SBA’s programs currently operate independently.
These efforts may help SBA address concerns related to its use of data to identify potential fraud. We recommended that SBA develop cross-program data analytics to better identify applicants who tried to defraud multiple programs. We also recommended that SBA obtain external data that could help verify applicant information and detect potential fraud. According to SBA officials, to address these recommendations, the agency procured third-party services to help validate customer identity. However, as of November 2024, SBA was still finalizing an agreement to obtain access to external data.
Monitoring: partially met. According to SBA officials, the agency’s working groups and boards, described above, meet regularly on a weekly or quarterly basis. SBA also has included a risk-management strategy in its fiscal year 2022–2026 strategic plan and performance measures in its fiscal year 2023 annual performance report. These measures include tracking SBA’s progress toward reducing material weaknesses in its financial statement audit and closing open recommendations from us and the Office of Inspector General.
However, the financial statement auditor has continued to find deficiencies related to SBA’s monitoring of PPP lenders and processes performed by its contractor. For example, the auditor found that SBA did not implement a monitoring process sufficient to ensure that PPP lenders followed procedures and resolved identified eligibility concerns.
Demonstrated progress: partially met. SBA has addressed many of our previous concerns related to its oversight of PPP and COVID-19 EIDL. We reported in 2023 that SBA developed and implemented oversight plans for both programs, developed data analytics for COVID-19 EIDL, reported the estimated improper payment amount and rate for PPP, and assessed fraud risks in PPP and COVID-19 EIDL. Since then, SBA has addressed additional recommendations we made by developing strategies to manage fraud risks in both programs.
However, SBA’s financial statement auditor has been unable to express an opinion on whether SBA’s financial statements are fairly presented for 5 years in a row. This is because SBA has been unable to provide adequate evidence to support a significant number of transactions and account balances related to PPP and COVID-19 EIDL, among other things (see fig. 24). The 2024 financial statement audit included 56 recommendations to SBA, including 32 directly related to its pandemic relief programs. SBA management concurred with all the findings and recommendations in the audit.
Figure 24: Results of Audits of Small Business Administration Financial Statements, Fiscal Years 2019–2024
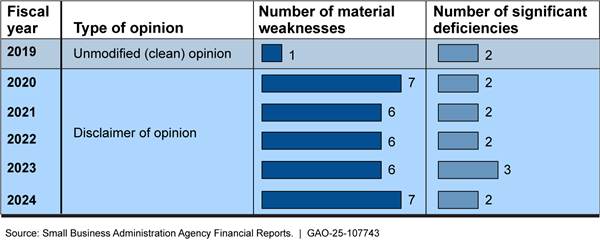
Notes: Data in figure includes all the material weaknesses and significant deficiencies that the Small Business Administration’s financial statement auditor identified, not just those related to the Paycheck Protection Program or the COVID-19 Economic Injury Disaster Loan program.
An unmodified (clean) opinion means the auditor concluded that financial statements are presented fairly in accordance with generally accepted accounting principles.
A disclaimer of opinion means the auditor was unable to obtain sufficient, appropriate evidence on which to base an opinion.
A material weakness is a deficiency, or combination of deficiencies, in internal controls over financial reporting, such that there is a reasonable possibility that a material misstatement of the entity’s financial statements will not be prevented, or detected and corrected, on a timely basis.
A significant deficiency is a deficiency, or a combination of deficiencies, in internal control over financial reporting that is less severe than a material weakness, yet important enough to merit attention by those charged with governance.
What Remains to Be Done
SBA needs to (1) increase its use of data to identify potential fraud and (2) address the material weaknesses identified by its financial statement auditor. Recommendations made by the auditor include implementing a process sufficient to ensure that PPP lenders followed procedures and resolved identified eligibility concerns and designing and implementing controls to ensure that COVID-19 EIDL loans were issued to eligible borrowers and accurately recorded.
We made 10 recommendations to SBA focused on this high-risk area, including those discussed above. Two remained open as of January 2025. Additionally, SBA’s financial statement auditor made numerous recommendations to SBA in November 2024. SBA could make additional progress if it were to complete actions to implement open recommendations, such as
· developing and using cross-program data analytics,
· identifying and obtaining external data to help verify applicant information, and
· addressing the material weaknesses identified by its financial statement auditor.
Benefits
Progress to address this high-risk area has resulted in more than $14.8 billion in financial benefits since we added it to our list in 2021. These benefits are associated with SBA’s implementation of a PPP oversight plan and incorporation of that enhanced fraud detection screening into its oversight of other SBA pandemic response programs. For example, SBA
· implemented an oversight plan to identify and respond to risks in PPP. Through the review of loans under this plan, SBA prevented more than $6.4 billion in potentially fraudulent loans from being forgiven.
· incorporated its PPP fraud-detection screening into two later pandemic relief programs—the Shuttered Venue Operators Grant Program and the Restaurant Revitalization Fund—when the programs launched in April and May 2021. Through these efforts, SBA was able to prevent more than $4.8 billion in potentially fraudulent applications from being funded.
Progress to address this high-risk area also has resulted in more than 10 other benefits. For example, SBA finalized strategies that outlined specific actions to address identified fraud risks in PPP and EIDL in August 2023.
Contact Information
For additional information about this high-risk area, contact Courtney LaFountain, Acting Director, Financial Markets and Community Investment, at (202) 512-8678 or LaFountainC@gao.gov.
Government-wide Personnel Security Clearance Process
Agencies responsible for reforming the personnel security clearance process have developed policies and performance measures to assess quality but need to take further action to improve the timely processing of clearances and address IT system challenges.
Why Area Is High Risk
A high-quality personnel security clearance process is necessary to prevent the unauthorized disclosure of information that could cause exceptionally grave damage to U.S. national security. Ongoing reforms in this area are promising, including the development of policies and performance measures to assess the quality of the clearance process. However, challenges remain regarding the timely processing of clearances and development of the new National Background Investigation Services (NBIS) IT system.
Area Rating
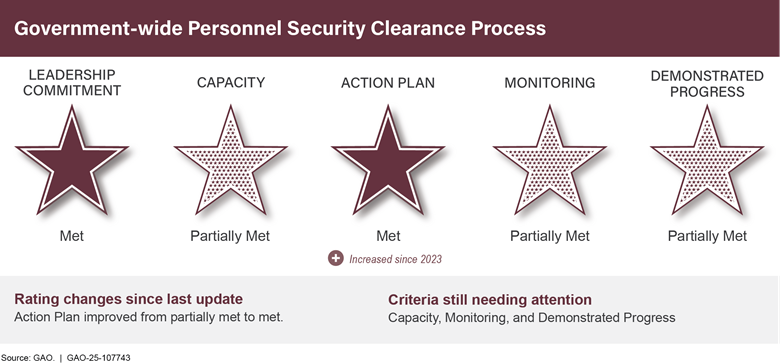
Since we issued our last update, ratings for four out of the five criteria—leadership commitment, capacity, monitoring, and demonstrated progress— remain unchanged. The rating for action plan increased to met. Specifically, responsible agencies have substantially advanced personnel vetting reform, known as Trusted Workforce 2.0. This reform is designed to transform and align the security clearance process as well as other vetting processes, including determining suitability for government employment and credentialing for access to agency systems or facilities. A key aspect of Trusted Workforce 2.0 is the continuous vetting of individuals to ensure they remain trustworthy to hold a security clearance or a position of public trust.
Leadership commitment: met. The Security Clearance, Suitability, and Credentialing Performance Accountability Council (PAC) is the government-wide entity responsible for reforming the personnel security clearance process, which determines eligibility to access classified information or to hold a sensitive position. It has four principal members: the Deputy Director for Management of the Office of Management and Budget, the Director of National Intelligence (DNI), the Under Secretary of Defense for Intelligence and Security, and the Director of the Office of Personnel Management (OPM).
The PAC has demonstrated leadership commitment to oversee the implementation of personnel vetting reform that it initiated in 2018. For example, since our 2023 High-Risk Report, the Executive Agents (the DNI and the Director of OPM) have issued guidance documents, including new guidance on implementing performance management standards and strategies related to Trusted Workforce 2.0.
Capacity: partially met. The Director of the Defense Counterintelligence and Security Agency (DCSA)—which conducts background investigations for 95 percent of the federal workforce—issued a strategic workforce plan for the agency’s entire personnel vetting workforce in September 2023, as we recommended. Additionally, in fiscal year 2024, DCSA established a process to provide a monthly status update on its IT systems to help ensure it makes an informed determination of risks—including for NBIS and legacy personnel vetting systems it is still using until NBIS is fully functional, as we recommended.
However, DCSA needs to improve how it manages the development of the NBIS system, an IT system critical to the successful implementation of the Trusted Workforce 2.0 reform effort that replaces legacy personnel vetting systems. In June 2024, we testified that DCSA had not revised the NBIS system schedule to meet all the characteristics of a reliable schedule, as defined in GAO’s best practice guide for scheduling and Agile software development. Additionally, DCSA continues to face delays in the development of the system. We also reported that the NBIS program’s cost estimate from 2022 was not reliable, meaning that DCSA may be unable to accurately project NBIS costs (see fig. 25).
Figure 25: GAO’s Assessment of National Background Investigation Services System Schedule and Cost Estimate, as of 2023
The Department of Defense (DOD) planned for NBIS to be fully operational in 2019 but missed that goal and continued to miss subsequent goals. In early 2024, DOD notified Congress that it would not meet its goal to be operational by the second quarter of fiscal year 2025. DOD reported that the NBIS delay would result in additional costs to the government to sustain legacy IT systems and to complete NBIS development. DOD finalized a new NBIS “roadmap” in September 2024 with projected milestone dates for NBIS development through fiscal year 2027. Moreover, in June 2024, we reported that DCSA did not fully address all planning steps of DOD’s risk management framework when considering the cybersecurity risks of NBIS and legacy systems. We also found that DCSA lacked an oversight process to help ensure that appropriate privacy controls are implemented.
Action plan: increased to met. Since our 2023 update, the Executive Agents issued an additional planning document that defines measurable performance goals for the reform effort. Specifically, in November 2023, the Executive Agents issued performance measure implementation guidance for assessing the quality of all phases of the personnel security clearance process, including those for initiations, investigations, and adjudications, that includes measurable targets. The guidance also includes new measures for continuous vetting, which we previously recommended. Moreover, the Executive Agents issued new timeliness objectives based on an evidence-based review of the initiation, investigation, and adjudication phases of the personnel security clearance process and developed a plan with goals and milestones to achieve them, as we recommended.
We have previously recognized the Executive Agents’ issuance of updated standards, including the Federal Personnel Vetting Investigative Standards in May 2022, the Common Principles in Applying Federal Personnel Vetting Adjudicative Standards in July 2022, and the Federal Personnel Vetting Performance Management Standards in September 2022.
Monitoring: partially met. The PAC continues to monitor and report publicly on the progress of personnel vetting reform. ODNI also collects data from agencies to oversee the personnel security clearance process as the government-wide Security Executive Agent. A senior official stated the PAC plans to report publicly on its performance measures issued to assess quality in all phases of the personnel security clearance process. We believe these planned steps are positive developments because transparent public reporting, including ensuring that reported data are reliable, will help foster accountability and trust in clearance process reforms.
However, we found that ODNI’s clearance timeliness data are not sufficiently reliable for us to determine the percentage of executive branch agencies that did or did not meet timeliness objectives. The Intelligence Community Inspector General reported in November 2023 that multiple intelligence community elements did not accurately collect, document, and report required security clearance processing timeliness information. According to the report, intelligence community elements also did not consistently calculate timeliness metrics.
In addition, we found that timeliness data for a sample of six executive branch agencies contained inaccuracies. For example, summary statistics we calculated from case-level data for five of the six agencies were inconsistent with comparable statistics ODNI had for each agency. Also, officials from three of these agencies stated they found similar inconsistencies. Such inconsistencies indicate that agencies or ODNI used unreliable methods to calculate statistics, or their data contained inaccuracies. For the remaining agency, we calculated statistics using its case-level data and found they were inconsistent with timeliness-related statistics it submitted to ODNI.
Demonstrated progress: partially met. Since 2023, the PAC demonstrated progress with the security clearance process by implementing multiple GAO recommendations, but additional work remains. Actions taken include issuing performance measure implementation guidance to assess the quality of investigations and the other phases of the clearance process. DCSA also issued a strategic workforce plan for the agency’s entire personnel vetting workforce, as we recommended.
Moreover, the Executive Agents issued new timeliness objectives based on an evidence-based review of the initiation, investigation, and adjudication phases of the personnel security clearance process and developed a plan with goals and milestones to achieve them, as we recommended. However, we were not able to determine the number of agencies that met security clearance timeliness goals because we determined that agency security clearance data collected by ODNI were not sufficiently reliable.
While OPM has taken some steps to strengthen its IT environment where legacy systems still reside, DOD had not fully planned for the cybersecurity of, or fully implemented privacy controls for, NBIS and those legacy systems. This is largely due to the absence of an oversight process that would ensure accountability. Until DOD establishes an oversight process and fully implements privacy controls, it unnecessarily increases the risks of disclosure, alteration, or loss of sensitive information on its personnel vetting systems. We also have an ongoing review assessing DCSA’s implementation of cybersecurity controls for selected NBIS and legacy background investigation systems that will be issued in a sensitive report.
What Remains to Be Done
To make progress in this high-risk area, attention is needed to improve (1) development of the NBIS system, (2) reliability of ODNI’s clearance timeliness data, and (3) planning for the cybersecurity and privacy controls of NBIS and legacy systems. As of January 2025, 12 open recommendations to ODNI and DOD remain in this area, including the following:
· The Secretary of Defense, in coordination with the DCSA Director, should ensure that control assessment plans are documented and that assessments align with these plans.
· The Secretary of Defense should direct DCSA's Chief Information Officer to ensure the agency's policies and procedures include key information and are reviewed and updated as required.
· The Secretary of Defense, in coordination with the DCSA Director, should ensure DCSA’s Chief Information Officer assigns security and privacy requirements to the system and to the environment in which the system operates and documents the results.
Congressional Actions Needed
As of January 2025, one matter for congressional consideration remains open. Congress should consider requiring that the Secretary of Defense develop a reliable program schedule and cost estimate for NBIS as defined in GAO’s guides on schedule assessment, cost estimating and assessment, and agile assessment. In addition, Congress should consider requiring that the Director of National Intelligence ensure that agencies submit reliable data on the time they take to complete the initiation, investigation, and adjudication phases of the security clearance process to ODNI to assist it in overseeing agencies’ performance in meeting clearance timeliness objectives.
Benefits
There have been 20 benefits because of progress in this area since it was added to the list in 2018. For example, in September 2024, we verified that DCSA updated privacy impact assessments for three NBIS and three legacy systems to address deficiencies we identified. In addition, ODNI and OPM issued performance measures in November 2023 for departments and agencies to collect, assess, and report on the quality of all phases of the personnel security clearance process.
Contact Information
For additional information about this high-risk area, contact Alissa H. Czyz, Director, Defense Capabilities and Management, at (202) 512-4300 or CzyzA@gao.gov.
National Efforts to Prevent, Respond to, and Recover from Drug Misuse
Federal agencies must effectively coordinate and implement a strategic national response and make progress toward reducing drug misuse rates, overdose deaths, and the resulting harmful effects to society.
Why Area Is High Risk
Drug misuse—the use of illicit drugs and the misuse of prescription drugs—has been a persistent and long-standing public health issue in the U.S. Hundreds of thousands of people have died from misusing drugs, and society and the economy have suffered significant harms. In recent years, the federal government has spent billions of dollars and enlisted more than a dozen federal agencies to address drug misuse and its effects. In September 2024, the Department of Health and Human Services renewed a 2017 determination marking the opioid crisis as a public health emergency.
Area Rating
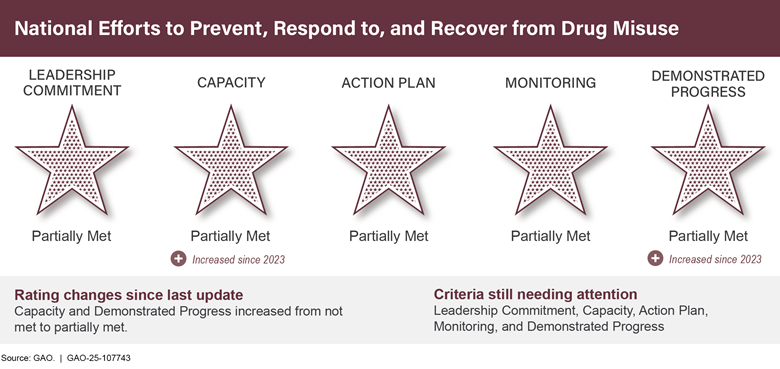
Since this area was added to the High-Risk List in 2021, federal agencies have made progress in several areas. As a result, the capacity and demonstrated progress criteria ratings have increased to partially met. The following issues present challenges for the federal government in fully addressing the five high-risk criteria:
· The 2024 National Drug Control Strategy meets some but not all statutory requirements. For example, the Office of National Drug Control Policy (ONDCP) has not developed the required 2-year and 5-year performance measures and targets for each National Drug Control Strategy goal and objective established for reducing drug use, availability, and the consequences of drug use.[27] It has also not developed the required estimate of federal funding and other resources needed to achieve each performance objective and target, among other requirements.[28] Federal agencies need to ensure their programs support related goals from the strategy.
· The availability of treatment for substance use and mental health has not kept up with demand. For example, as of April 2024, the Health Resources and Services Administration estimated that about 120 million Americans live in areas with mental health professional shortages.
· The rates of drug misuse and drug overdoses continue to be high, even though nationwide drug overdose deaths decreased by about 21 percent since our 2023 update.[29] Moreover, provisional data from the Centers for Disease Control and Prevention’s (CDC) National Center for Health Statistics shows overdose deaths have declined to below 100,000 for the first time during the 12-month period ending in June 2024 since 2021. Disparities remain across various demographics, as discussed later.
Leadership commitment: partially met. ONDCP leaders have demonstrated commitment to addressing drug misuse, and federal agencies have established interagency working groups to help address drug misuse issues. For example, in September 2024, ONDCP developed the Drug Control Data Dashboard. This contains an interactive collection of drug data that will be updated annually. The dashboard is intended to help federal agencies better understand the scope and nature of the drug crisis.
However, ONDCP has yet to both issue a strategy by the statutorily prescribed deadline and issue a strategy that meets all the statutory requirements.[30] A key aspect of leadership commitment includes being positioned to sustain efforts. Given the delay in issuing the strategy and the new presidential administration, it is too soon to tell whether the federal government is positioned to sustain the efforts it set out in the most recent strategy.[31] Additionally, we have ongoing work evaluating how the Drug Enforcement Administration and U.S. Immigration and Customs Enforcement work together to coordinate on drug investigations.
Capacity: increased to partially met. Since our last update, this rating increased from not met to partially met. In March 2023, the U.S. Food and Drug Administration approved the first naloxone product, a medication that rapidly reverses the effects of opioid overdose, for over the counter, nonprescription use. Expanding national access to naloxone helped increase capacity to prevent opioid overdose deaths.
Also in March 2023, the Federal Bureau of Prisons developed a plan identifying the staff and funding resources necessary to achieve its drug education and treatment program goals. The Bureau also issued a report on the allocated drug treatment positions by positions that are currently filled or vacant.
Additionally, in December 2022, Congress passed and the President signed a law eliminating the requirement for health care providers to obtain a waiver to prescribe buprenorphine for the treatment of opioid use disorder.[32] As a result, more providers will be able to prescribe this medication, which increases access to treatment and addresses persistent treatment gaps.
Nevertheless, significant gaps in the availability of substance use and mental health treatment persist. For example, as of July 2024, demand for treatment increased among active-duty service members and their families, and, like broader trends across the U.S., these individuals experience challenges accessing behavioral health care providers in part due to inaccurate information in network directories.
ONDCP’s proposed federal drug control budget for fiscal year 2025 is $44.5 billion, a $890.7 million increase from the prior fiscal year. However, the 2024 strategy highlights the need for additional resources for drug misuse prevention, treatment, and recovery. While the strategy helps guide these efforts, it does not list the resources necessary to expand treatment for substance use disorders as required by law.[33] Additionally, we have ongoing work on ONDCP’s capacity to conduct effective anti-drug media campaigns.
Action plan: partially met. The 2024 strategy sets forth an action plan to address drug misuse by targeting the two drivers of the crisis—preventing drug use and dismantling the supply chains of illicit drugs. While the strategy and its accompanying documents fully addressed some of the statutory requirements, it only partially addressed or did not address others. For example, for the first time, the strategy included a systematic plan for increasing data collection to develop policy-relevant data and evidence. However, the strategy lacked annual quantifiable and measurable objectives and specific targets to accomplish long-term quantifiable goals.[34]
In addition, in 2021, the U.S. and Mexico signed the Bicentennial Framework for Security, Public Health, and Safe Communities to reduce drug trafficking into the U.S., among other priorities. However, the Department of State and the U.S. Agency for International Development have not identified the milestones and performance indicators that will be used to assess progress toward the goals and objectives in the framework.
Monitoring: partially met. Federal agencies have taken some actions to improve their monitoring and data collection efforts. For example, we reported in December 2024 that the Substance Abuse and Mental Health Services Administration collected information to monitor how grant recipients used funding from the State Opioid Response and Tribal Opioid Response grant programs, including steps the agency took to address grantee challenges with using the funding. However, some grant recipients reported challenges obtaining data on services and results of other grant recipients, which could help them improve the services they offer.
ONDCP released its National Drug Control Assessment in May 2024.[35] It included an evaluation of the national drug control program agencies’ progress in meeting the annual performance targets. For example, in 2023, ONDCP’s High Intensity Drug Trafficking Areas program exceeded its target for the number of drug cases it supported. However, it did not meet its target for number of drug trafficking organizations dismantled or disrupted by the funded task forces.
Although ONDCP monitors progress in this way, ONDCP did not issue its 2024 Performance Review System report until December 2024 due to delays in its interagency clearance processes. This report is to assess the federal government’s overall efforts to address the goals and objectives in the 2024 strategy, including specific 2-year and 5-year targets for accomplishing the strategy’s long-term goals.[36] ONDCP officials told us that the agency plans to use future Performance Review System reports to adjust the strategy’s policy and program actions as necessary to achieve its goals.
Demonstrated progress: increased to partially met. ONDCP improved its 2024 strategy by listing data that will be used as evidence for demonstrating any progress as a result of recent drug control policymaking and related activities.
As of February 2025, the CDC estimated the predicted provisional number of drug overdose deaths was 86,882 for the 12-month period ending in September 2024. This represents a 21 percent decrease from the 12-month period ending in September 2022, which was the time period with the latest data available for the last update, and it was part of the first substantial drop since provisional drug overdose data became available for January 2015.[37]
Despite this progress, significant work remains for agencies to determine why the drug overdose deaths rate is declining to better understand what efforts are working. Drug overdose death rates remain at historic highs in the U.S., demonstrating the need for federal agencies to improve national efforts to prevent, respond to, and recover from drug misuse (see fig. 26).
Figure 26: Predicted Provisional Number of Drug Overdoses in the United States, 12-month Periods Ending in January 2015 through September 2024
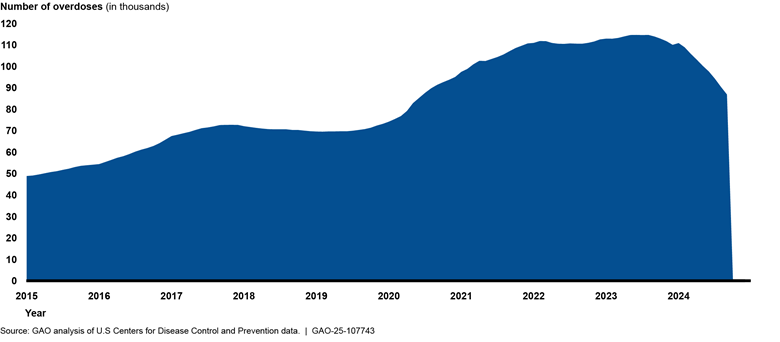
Note: Predicted provisional counts represent estimates of the number of deaths adjusted for incomplete reporting. These provisional data are not comparable with final data and are subject to change. 12-month periods are the number of deaths received and processed for the 12-month period ending in the month indicated. Drug overdose deaths are identified using ICD–10 underlying cause-of-death codes: X40–X44, X60–X64, X85, and Y10–Y14. Data were accessed on February 12, 2025. The counts were based on data available for analysis as of February 2, 2024.
Additionally, certain segments of the population are impacted more than others. For example, the CDC reported that in 2023, the drug overdose death rate for males was over twice as high as for females.[38] By age group, overdose death rates were higher for those aged 25 to 64 compared to those aged 15 to 24 and 65 and over. Among race and ethnicity groups, drug overdose death rates were highest for the American Indian and Alaska Native (non-Hispanic) population.
What Remains to Be Done
To address these issues, ONDCP needs to issue a strategy that meets all the statutory requirements, list the resources necessary to expand treatment for substance use disorders as required by law, and determine why the drug overdose death rate is declining to better understand what efforts are working.
It is also important to address numerous recommendations we made to federal entities over the last few years. Thirty-eight of these recommendations remained open as of January 2025, including:
· The Substance Abuse and Mental Health Services Administration should complete and implement a documented plan for collecting and reporting information about Opioid Response grant subrecipients.
· ONDCP should routinely implement an approach, based on key planning elements, to meet the requirements for the 2024 National Drug Control Strategy and future strategy iterations.
· The need to develop monitoring and evaluation plans critical to assess progress toward the goals and objectives of the Bicentennial Framework for Security, Public Health, and Safe Communities with the U.S. Agency for International Development to reduce drug trafficking to the U.S.
· The Drug Enforcement Administration should solicit input from distributors, or associations representing distributors, and develop additional guidance for distributors regarding their roles and responsibilities for suspicious orders monitoring and reporting to prevent diversion while ensuring an adequate and uninterrupted supply of controlled substances for legitimate medical needs.
Benefits
There were nearly 20 benefits to the federal government due to progress in this high-risk area since it was added to the list in 2021. For example:
· In April 2023, ONDCP enhanced its strategy by releasing a Drug Data Plan, which discussed ongoing efforts to improve the timeliness, accuracy, and accessibility of drug data—including fatal and nonfatal overdose data—to inform policymaking.
· In November 2023, the Substance Abuse and Mental Health Services Administration reported to Congress on its more comprehensive, in-depth assessment of the State Opioid Response grant program. The agency analyzed data for different client demographic groups, identified disparities in outcomes, and described efforts to address these disparities.
· In March 2024, the Veterans Health Administration developed and deployed a dashboard to measure potential differences in mental health care quality by vulnerable demographic groups, such as rurality.
Contact Information
For additional information about this high-risk area, contact Triana McNeil, Director, Homeland Security and Justice, at (202) 512-8777 or McNeilT@gao.gov; Alyssa M. Hundrup, Director, Health Care, at (202) 512-7114 or HundrupA@gao.gov; or Thomas Costa, Director, Education, Workforce, and Income Security, at (202) 512-7215 or CostaT@gao.gov.
National Flood Insurance Program
Congress should consider comprehensive reform of the National Flood Insurance Program (NFIP) to improve the program’s solvency and the nation’s flood resilience.
Why Area Is High Risk
Congress created NFIP with two competing goals—keeping flood insurance affordable and keeping the program fiscally solvent. Emphasizing affordability by charging policyholders discounted premiums that do not reflect the full risk of flood loss has led to insufficient premium revenue to pay for claims. This has transferred some of the financial burden of flood risk from individual property owners to taxpayers.
Since this area was added to the High-Risk List in 2006, the Federal Emergency Management Agency (FEMA) has taken important steps to help move NFIP toward financial solvency. This entails implementing a revised premium rate-setting methodology that better aligns premiums with the flood risk of individual properties. FEMA also developed a legislative proposal to improve the program’s solvency and address affordability, among other reforms. However, Congress has yet to enact comprehensive reforms to NFIP that would address the program’s challenges. Such reform could determine whether this issue remains on the High-Risk list.
Area Rating
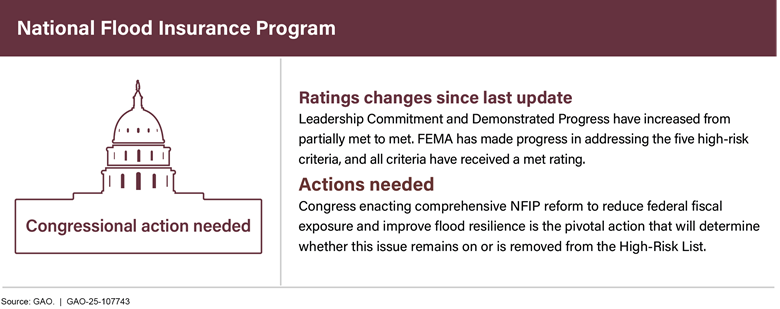
Since the 2023 High-Risk update, the criteria ratings for leadership commitment and demonstrated progress have increased from partially met to met. FEMA has taken steps to improve NFIP’s financial solvency and its administration of NFIP by implementing our outstanding recommendations.
Leadership commitment: increased to met. FEMA leadership has helped ensure sustained progress in moving NFIP toward financial solvency by establishing a new rate-setting methodology that better aligns premiums with a property’s flood risk. FEMA also has engaged in efforts to increase consumer participation in the flood insurance market. Further, FEMA leadership continues to demonstrate a commitment to the effective administration of NFIP by implementing many of our outstanding recommendations.
Capacity: met. FEMA’s full implementation of its new rate-setting methodology has demonstrated a capacity for addressing challenges and completing major projects. FEMA will need to continue to assess its ability to address challenges because responding to multiple natural disasters can strain its capacity.
Action plan: met. Since this area was added to the High-Risk List in 2006, FEMA has completed several planning efforts that have improved NFIP. For example, FEMA created a plan to identify and analyze flood risk data to identify options for increasing consumer participation in the flood insurance market.
Monitoring: met. FEMA monitors NFIP premium rates to ensure they continue to reflect the risk of flood losses. For example, FEMA maintains contracts evaluating actuarial techniques and risk models and regularly evaluates the accuracy of those risk models. This remains key to monitoring NFIP’s fiscal exposure.
Demonstrated progress: increased to met. FEMA has demonstrated progress by meeting the four high-risk criteria. In addition, FEMA continues to show a commitment to addressing our outstanding recommendations. Specifically, by fully implementing its new rate-setting methodology, identifying options to increase consumer participation in the flood insurance market, and evaluating its compensation practices for insurers, FEMA has shown a commitment to sustaining improvements to its administration of NFIP.
Congressional Actions Needed
Despite FEMA’s efforts to address NFIP’s fiscal solvency, premiums do not yet reflect the full risk of flood loss. This increases the likelihood of future borrowing from the Department of the Treasury to pay claims from major natural disasters. As of February 2025, FEMA’s debt was $22.5 billion, even after Congress canceled $16 billion of it in October 2017.
Reducing NFIP’s federal fiscal exposure and improving flood resilience would require Congress to enact comprehensive reform of NFIP. Such reform is needed to help balance NFIP’s competing programmatic goals of keeping insurance affordable while maintaining fiscal solvency. We identified interrelationships as well as potential benefits and challenges associated with potential actions to constitute comprehensive reform (see fig. 27).
Address outstanding debt. FEMA is unlikely to repay its debt to Treasury and attempting to do so likely would lead some policyholders to drop coverage. Without congressional action to address the debt, it is likely NFIP’s existing debt will continue to grow, actuarial soundness will be delayed, and affordability concerns will increase.
Implement full-risk premiums. Premiums that do not reflect the full risk of loss are an underlying cause of NFIP's federal fiscal exposure. Discounted premiums obscure that exposure, contribute to policyholders’ misperception of flood risk, and discourage private sector involvement.
Address affordability more effectively. Current policy addresses affordability through discounted premiums. This approach hides the program’s fiscal exposure, hinders private market growth by providing artificially low premiums, and is not cost-effective because the discounts are not based on need.
Encourage greater consumer participation. Some consumers might not purchase flood insurance because they underestimate their flood risk or overestimate the amount of federal assistance they would expect to receive after a disaster. Without flood insurance, consumers are at greater financial risk from flooding and may be more reliant on federal disaster assistance.
Remove barriers to private sector involvement. Greater private sector involvement in the flood insurance market could help decrease federal fiscal exposure. However, under FEMA’s interpretation of NFIP statute, private coverage to satisfy NFIP’s continuous coverage requirement is not permitted. Further, FEMA believes it cannot offer risk-based partial refunds for midterm cancellations when consumers switch to private policies. As a result, consumers may be discouraged from seeking private coverage.
Support NFIP flood resilience efforts. Fees on NFIP policies help support NFIP flood resilience efforts, such as mitigation, mapping, and community participation. If the number of NFIP policies decreases, FEMA will have less funding for these efforts, making it more difficult to plan for, absorb, recover from, and more successfully adapt to adverse events.
As of January 2025, nine matters for congressional consideration related to this area remained open. In addition to comprehensive reform, we recommend that Congress consider
· addressing NFIP’s legacy and potential future debt, which could include canceling the debt while also providing funding to make up for the statutorily generated premium shortfall or allowing the immediate transition to full-risk premiums accompanied by a means-based assistance program, among other options;
· providing any affordability assistance for flood insurance through a means-based program that is reflected in the federal budget rather than through statutorily discounted premiums;
· authorizing and requiring FEMA to allow private flood insurance coverage to satisfy NFIP’s continuous coverage requirement and offer risk-based partial refunds for midterm cancellations of NFIP policies that are replaced by private flood insurance policies; and
· requiring FEMA to evaluate how comprehensive and up-to-date flood risk information could be used to determine which properties should be subject to the mandatory purchase requirement.
Benefits
Since we added NFIP to the High-Risk List in 2006, progress in this area has resulted in more than $4.4 billion saved and over 30 other benefits to the federal government. Examples include the following
· Under its updated rate-setting methodology, FEMA (1) ties premiums to individual property flood risk rather than to broadly defined flood zones, (2) integrates input from commercial catastrophe models, (3) accounts for more sources of flooding, and (4) accounts for the replacement cost value of the property. Further, the new methodology includes the information necessary for FEMA to calculate full-risk premium rates for all policies, including subsidized policies.
· FEMA improved information about the mandatory purchase requirement, as we recommended. Specifically, it analyzed available flood risk data to identify strategies for increasing consumer participation in the flood insurance market. It also provided this information to Congress to help inform its decision-making on how, if at all, to revise the mandatory purchase requirement to increase consumer participation.
· FEMA implemented procedures to annually analyze profit and expense information for determining compensation for Write Your Own insurers that sell and service federal flood insurance policies and adjust claims. These procedures and the insights gained from analysis of the results each year will help to inform FEMA as it revises its compensation practices for Write Your Own insurers as required by the Biggert-Waters Flood Insurance Reform Act of 2012.
Contact Information
For additional information about this high-risk area, contact Alicia Puente Cackley, Director, Financial Markets and Community Investment, at (202) 512-8678 or CackleyA@gao.gov.
Resolving the Federal Role in Housing Finance
Housing agencies should strengthen oversight of the mortgage finance system. Congress should also determine the future federal role in this system and craft a plan to end federal conservatorship of the Fannie Mae and Freddie Mac enterprises.
Why Area Is High Risk
The federal government has provided significant capital support to the Federal National Mortgage Association (Fannie Mae) and Federal Home Loan Mortgage Corporation (Freddie Mac), collectively known as the enterprises. It also uses federal guarantees to support housing policy objectives. These guarantees ensure private lenders receive timely payments, thus transferring the risk of borrower default to the government.
During the 2007-2009 financial crisis, the federal role in housing finance expanded. It remains large today and could grow if the enterprises incur major future losses and draw on additional Treasury commitments.[39] We designated this area as high risk because of this significant fiscal exposure and because objectives for the future federal role remain unestablished, such as the structure of the enterprises.
Several federal agencies support housing finance, for example by providing mortgage loans to homeowners and managing the secondary mortgage market.
· The Consumer Financial Protection Bureau (CFPB) implements and enforces federal consumer financial laws, including those related to the provision of products and services to homebuyers and homeowners.
· The Department of Housing and Urban Development (HUD) supports mortgages through insurance and guarantee programs. HUD’s Federal Housing Administration (FHA) insures a single-family mortgage portfolio of more than $1.4 trillion. The Government National Mortgage Association (Ginnie Mae), a government-owned corporation within HUD, guarantees the performance of nearly $2.7 trillion in mortgage-backed securities with FHA or other federal support.
· The Federal Housing Finance Agency (FHFA) is responsible for overseeing Fannie Mae and Freddie Mac and has held them in conservatorship since 2008.[40] The enterprises operate in the secondary mortgage market, purchasing home mortgage loans from lenders who originate the loans and holding those loans in their portfolios or packaging them to issue federally guaranteed mortgage-backed securities that may be sold. FHFA’s initial focus was reducing the enterprises’ losses and their operational and credit risk during the financial crisis, and stabilizing the mortgage and housing markets. The conservatorships were intended to be temporary but have lasted over 16 years as FHFA turned its focus to longer-term issues once the enterprises returned to profitability.
Area Rating
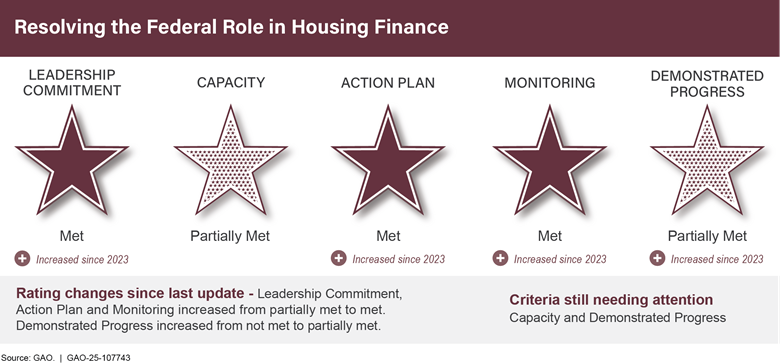
Since our last update, federal agencies have made enough progress to merit increases in four criteria. Specifically, leadership commitment, action plan, and monitoring increased from partially met to met, and demonstrated progress increased from not met to partially met. The capacity criterion remains unchanged.[41]
Leadership commitment: increased to met. In its 2023 report to Congress, FHFA highlighted efforts to strengthen the enterprises’ capital positions. For example, it continued a comprehensive review of their pricing framework, implemented changes in up-front fees to better align them with the risk and capital associated with underlying loans, and requested input on FHFA’s oversight goals and policy priorities.
In July 2024, CFPB finalized a rule to establish a registry of certain financial companies, including nonbank mortgage companies.[42] This new rule requires a nonbank covered entity to register with CFPB when it becomes subject to an agency or court order due to violations of certain consumer protection laws. We previously found that the share of home mortgages serviced by nonbanks increased significantly over a three-year period.[43] Additionally, FHFA noted that the enterprises’ exposure to nonbanks had increased, primarily due to increased loan sales and servicing volume (see fig. 28). In 2016, we recommended CFPB collect more comprehensive data on the identity and number of nonbank mortgage servicers in the market to improve its ability to monitor the consumer effect of nonbank servicers. While CFPB previously implemented this recommendation, the July 2024 rule will allow CFPB to cast a wider net in its oversight efforts.
Figure 28: Percentage of Loans in Agency Mortgage-Backed Securities Serviced by Nonbanks, by Dollar Value, as of 2014 and Second Quarter 2024
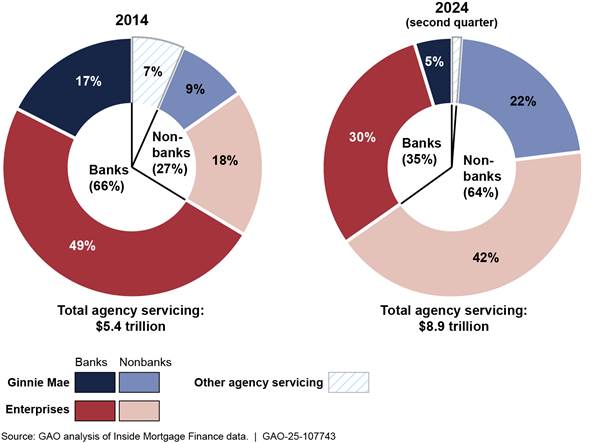
Note: Agency securities are those that Ginnie Mae or the enterprises (Fannie Mae and Freddie Mac) guaranteed. “Other” refers to loans that Ginnie Mae or the enterprises serviced or state housing finance agencies held. Percentages may not sum to 100 due to rounding.
Congressional actions are still needed to realize significant progress in this area, including legislation establishing objectives for the future of the enterprises. For example, in its May 2024 report on nonbank risks, the Financial Stability Oversight Council recommended that Congress consider providing Ginnie Mae and FHFA authority to oversee the safety and soundness of nonbank mortgage servicers. We also recommended that Congress grant FHFA explicit authority to examine third parties that do business with and play a critical role in the enterprises’ operations (including nonbanks).
Capacity: partially met. The enterprises have generally operated profitably since 2012 and increased their combined capital reserves to $154.2 billion. However, the enterprises still have not reached sufficient levels of capital to exit conservatorship. While FHFA and the Department of the Treasury (Treasury), as shareholder, could move the enterprises closer to exiting conservatorship, congressional action is essential to directing the administration regarding their future.
FHA’s Mutual Mortgage Insurance (MMI) Fund has met its statutory minimum capital ratio requirement annually since fiscal year 2014. However, the requirement is not based on a specified risk threshold (which defines the level of stress the MMI Fund should be able to withstand). Congress should consider specifying the economic conditions the fund would be expected to withstand to remain self-sufficient. If such legislation is enacted, FHA would have to comply with a capital ratio consistent with these conditions.
Action plan: increased to met. Housing and regulatory agencies have taken steps to strengthen the mortgage finance system. In 2024, CFPB, FHFA, and the federal financial regulators adopted a final rule to implement quality control standards mandated by the 2010 Dodd-Frank Wall Street Reform and Consumer Protection Act (Dodd-Frank Act) for the use of automated valuation models by mortgage originators and secondary market issuers.[44] As a result, certain mortgage originators and secondary mortgage market issuers must adopt policies, procedures, and control systems designed to ensure confidence in the mortgage collateral estimates produced by these models and to protect against data manipulation.
In 2024, CFPB also issued proposed revisions to mortgage servicing rules that it stated would, if finalized, likely reduce avoidable foreclosures. CFPB also expects these revisions to add resiliency to the mortgage market in the event of a future crisis.
Monitoring: increased to met. Housing and regulatory agencies have taken steps to better monitor programs and mortgage finance system changes. For example, FHFA and CFPB established a joint initiative—the National Mortgage Database program—to help examine the effect of mortgage market reforms. In September 2024, FHFA unveiled a new dashboard for the program that reports publicly available quarterly data on residential mortgage performance. It provides statistics at the national and state levels and for the 100 largest metropolitan areas.
HUD identified metrics that measure how its program for foreclosed properties supports its regulatory goal of strengthening neighborhoods and communities, as we recommended. These metrics were included in HUD's fiscal year 2024 annual performance plan to highlight impactful policy changes. By identifying and tracking new metrics, HUD can monitor progress toward important program goals.
FHA, which insured the foreclosed mortgages, evaluated outcomes for its 2017 pilot program for conducting physical inspections of those properties, as we recommended. The pilot allowed mortgage servicers to ensure the properties met HUD standards before conveying them to HUD’s inventory. The pilot’s improved monitoring reduced from 65 percent to 2 percent the share of properties FHA reconveyed to mortgage servicers due to property-related issues, potentially saving servicers more than $10,000 for each avoided reconveyance. FHA also sold properties in the pilot an average of 5 days faster, saving approximately $300 per property.
Demonstrated progress: increased to partially met. Federal agencies have demonstrated significant progress in strengthening program oversight, including assessing risks to the mortgage finance system. For example, in October 2023, FHFA organized a tabletop exercise for the Financial Stability Oversight Council’s Nonbank Mortgage Servicing Task Force to stress test a significant nonbank failure scenario, revealing potential coordination issues with participants, including FHFA and Ginnie Mae. FHFA officials said they were incorporating lessons learned and, with the task force, developing monitoring metrics and an interagency response plan to facilitate coordination.
However, Ginnie Mae did not identify takeaways, citing legal restrictions and confidentiality concerns as the reason for their limited involvement. For example, Ginnie Mae did not develop responses to exercise discussion questions about issues beyond those subject to legal restrictions and confidentiality concerns. Furthermore, its default planning activities did not address interagency coordination nor include processes to ensure lessons learned are incorporated into its strategy. Accordingly, Ginnie Mae is missing an opportunity to assess and possibly enhance collaboration with other agencies and its own strategy during a crisis. Further, as part of any broader housing finance reform strategies from the administration, HUD and Treasury should consider recommendations from the 2019 plans that could help address system vulnerabilities, as we recommended.
Beyond agency efforts, congressional action is fundamental to addressing this high-risk area. It will be difficult to resolve the federal role in housing finance until Congress enacts objectives for the enterprises’ exit from conservatorship and their future structure. The ongoing conservatorships could create uncertainties for the real estate market, and a future economic downturn could adversely affect the enterprises’ portfolios. Additionally, agencies will be limited in assessing progress against specific mortgage finance goals until Congress provides a blueprint for their future role.
What Remains to Be Done
Federal housing agencies should address our six open recommendations as of January 2025:
· Ginnie Mae should develop processes for participating in interagency exercises—taking into consideration the potential risks and benefits of sharing nonpublic information in a crisis—and for incorporating lessons learned from the exercises into its issuer default strategy.
· The Secretaries of HUD and Treasury, as part of developing future housing finance reform plans, should consider recommendations from the 2019 plans that could help address system vulnerabilities and ensure future plans address all GAO framework elements.
Congressional Actions Needed
Resolving the federal role in housing finance will be difficult without congressional action. As of January 2025, six matters for congressional consideration remained open. For example, Congress should consider
· legislation that establishes objectives for the future federal role in housing finance, including a transition plan that enables the enterprises to exit federal conservatorship and considers the role of all relevant federal entities, including FHA and Ginnie Mae;
· requiring Ginnie Mae to evaluate the adequacy of its current guarantee fee for single-family mortgage-backed securities and report to Congress with recommendations, if any, on revising the fee; and
· specifying the economic conditions FHA’s MMI Fund would be expected to withstand without substantial risk of drawing on supplemental funds, and requiring FHA to specify and comply with a capital ratio consistent with these conditions.
Benefits
Financial benefits to the federal government due to progress in this area have totaled nearly $4.6 billion since it was added in 2013. In addition, there were more than 20 other benefits. For example:
· In March 2023, FHA codified procedures to standardize processes for the different types of loan sales it uses to dispose of defaulted single-family loans and to produce more reasonable calculations for minimum acceptable pricing in its loan sales. The revised methodology will ensure that mortgages are not sold below certain thresholds, thus reducing losses to the government.
· FHA also issued standard operating procedures, which set primary goals for loan sales, and stated that sales may have additional mission-driven goals. FHA provided documentation that, in 2022, it exceeded the mission-driven goal for percentage of sales to nonprofit or local government bidders.
Contact Information
For additional information about this high-risk area, contact Jill Naamane, Director, Financial Markets and Community Investment, at (202) 512-8678 or NaamaneJ@gao.gov.
U.S. Government’s Environmental Liability
The federal government’s environmental liability is vast and growing. The Departments of Energy (DOE) and Defense (DOD) bear the bulk of this liability. They, along with other agencies, need to identify and address environmental risks and ensure sufficient capacity to monitor and transparently report on this liability.
Why Area Is High Risk
The federal government's environmental liability represents the estimated cost to clean up areas where federal activities have contaminated the environment. This liability increased to $645 billion in fiscal year 2023 from $212 billion in fiscal year 1997.
DOE is responsible for the largest share ($544.5 billion in fiscal year 2024) of this liability, which is related primarily to retrieving, treating, and disposing of nuclear and hazardous waste. DOD is responsible for the second-largest share ($101.1 billion in fiscal year 2024), which is related primarily to environmental cleanup and restoration activities at or near current and former DOD installations. The remaining liability is shared among other agencies, including the Department of the Interior and General Services Administration (GSA). We added this area to our High-Risk List in 2017.
Area Rating

Since our last update, the rating for demonstrated progress increased from not met to partially met while the remaining four criteria ratings remain unchanged.
Leadership commitment: partially met. As in 2023, federal agencies continue to partially meet this criterion. DOE’s Office of Environmental Management (EM), which is responsible for almost 80 percent of DOE’s overall environmental liabilities, has increased its attention to environmental liabilities in recent years. In addition, DOD recently took several steps to address liabilities. DOE and DOD leaders should sustain leadership in this area because of the size and scope of activities needed to address their long-term cleanup responsibilities. Interior and GSA could also benefit from increased attention to tracking and reporting liabilities.
In December 2024, DOD set, for the first time, goals to address environmental liabilities for sites contaminated by military munitions. In 2022, we recommended, and Congress subsequently mandated, that DOD establish such a target goal for completing cleanup of these sites.[45] In addition, DOD improved management of its program to clean up radioactively contaminated sites in 2024 by developing a more detailed cost estimate, creating a roadmap for the cleanup program, and establishing program-level risk management procedures.
EM has also developed several key programmatic initiatives and guiding documents, including a program plan and a 10-year strategic vision, that could be useful frameworks for other agencies to follow. We maintain that continuity of such EM leadership initiatives could help DOE reduce its environmental liabilities. EM also benefited from having the same leader at the head of the agency from 2019 until 2024, but this leader left in June 2024. EM now has a new leader, and the agency has had significant leadership turnover at lower levels (see fig. 29). Whether EM will sustain recent progress under future leadership is unclear.
Figure 29: Leadership Changes in Calendar Years 2023 and 2024 for the Department of Energy Office of Environmental Management

Note: EM has seven field site managers for the Carlsbad Field Office, EM-Los Alamos, the Hanford Field Office, the Idaho Cleanup Project Site, Oak Ridge Site, Portsmouth/Paducah Sites, and Savannah River Site. The EM Consolidated Business Center line manages several smaller EM sites. Those who announced their departure in 2023 left EM by the end of April 2024.
EM has begun to incorporate risk-informed decision-making into program guidance, but it struggles to make risk-informed trade-offs within and across sites, as we originally reported in 2019. For example, we found in 2023 that officials at EM’s Los Alamos site did not comprehensively analyze cost and risk options for efficiently achieving site cleanup objectives.
Both DOE and DOD need to take steps to improve their environmental liability estimates. In December 2024, the DOE Inspector General announced that an independent audit of DOE’s financial statements identified a material weakness for internal controls related to financial reporting of EM’s environmental liability estimates. Specifically, the independent auditors determined that EM headquarters had not ensured that its environmental liability estimate was adequately supported with valid cost estimates, schedules, and assumptions. In addition, DOD’s Office of Inspector General continues to find that DOD did not include all cleanup, closure, or disposal costs in its environmental liabilities estimate and could not provide supporting records to demonstrate the list of environmental cleanup sites was complete.
Capacity: not met. Federal agencies do not have sufficient workforce capacity to effectively address their environmental liabilities. We reported in March 2024 that staffing shortages contributed to two-thirds of GSA buildings being out of compliance with GSA’s asbestos management inspection policy. Consequently, GSA is potentially not reporting complete information on its costs to address asbestos liabilities.
Within DOE, EM continues to be understaffed, which has caused project failures, schedule delays, cost overruns, and workplace accidents. EM needs to take several steps to improve workforce management to ensure it has the capacity to carry out its mission. These include that EM develop a forward-looking workforce plan and regularly survey employees to be proactive in retention.
DOE also needs buy-in from stakeholders for many of its cleanup decisions. However, in September 2024, we found that EM does not have a national framework outlining an approach for how its cleanup sites are to engage with stakeholders and governments. We recommended that EM develop such a framework. EM then could be better positioned to build and maintain trust with stakeholders and governments affected by its decisions.
Action plan: not met. Federal agencies have not developed formal plans to address environmental liabilities.
EM has highlighted the importance of pursuing opportunities for reducing environmental liabilities in documents such as its 10-year strategic vision and program plan. However, EM also has opportunities to improve these planning documents. For example, we recommended that EM ensure that its strategic plans, roadmaps, and program management plans follow best practices for being comprehensive for the entire EM program and, as applicable, for each site. We also recommended DOE develop a comprehensive, risk-informed approach to prioritizing its research and development investments. By taking this action, EM would better position itself to direct limited research and development resources to its highest priorities, leading to safer, more efficient, and more effective cleanup approaches.
Further, DOE also has an opportunity to consider all viable alternatives for treating the highly radioactive portion of Hanford’s tank waste, which EM refers to as high-level waste. We reported in September 2024 that, according to experts, alternative methods could help EM remove waste from Washington State earlier and save billions of dollars. We recommended that DOE pause design and construction of a facility intended to treat this waste—called the High-Level Waste Facility—while obtaining an independent analysis of opportunities to optimize treatment of Hanford’s high-level waste.
Monitoring: partially met. DOE has taken some positive steps to implement improved program management practices to track estimated cleanup costs. For example, as of fiscal year 2024, EM sites were developing life-cycle cost and schedule estimates to use as baselines for tracking progress and monitoring site work.
EM can improve its monitoring of cleanup progress by developing different performance metrics. For example, EM sites’ goals and performance metrics do not consistently link to EM-wide program goals or mission areas. Such metrics could track progress across DOE’s cleanup program as well as within specific types of cleanup, as we reported regarding groundwater in November 2024.
In addition, EM has not assessed whether its contracting approach for base operations—that is, activities that do not directly advance the cleanup mission—is ensuring cost-effective management of these activities. For fiscal year 2022, EM’s base operations totaled $3.1 billion, or 42 percent, of the approximately $7.5 billion annual EM budget request. Assessing whether EM’s contracting approach ensures or improves the cost-effectiveness of base operations would provide management a clear understanding of whether its reliance on particular contract mechanisms—such as performance evaluations—is achieving the intended results.
Other agencies could also do more to better understand, monitor, and report on their cleanup costs. For example, we reported in 2024 that DOD had not informed Congress about total fiscal exposures for remediation activities for a large fuel spill at the Red Hill facility in Hawaii. Similarly, DOD’s May 2024 report to Congress on DOD’s costs to clean up emerging contaminants known as per- and polyfluoroalkyl substances (PFAS) stated that DOD expects the estimated future costs for PFAS cleanup will increase over the current estimate of $7.09 billion as DOD learns more about the extent of cleanup required.
Demonstrated progress: increased to partially met. Agencies have demonstrated some progress to move toward reducing federal environmental liability. For example, in April 2024, DOE, the U.S. Environmental Protection Agency, and the Washington State Department of Ecology announced a holistic agreement proposing sweeping changes to DOE’s approach to cleaning up the Hanford Site. These changes are expected to result in significant cost savings, in part because they propose that DOE will grout—immobilize in a concrete-like mixture—certain low-activity waste from 22 tanks at Hanford.
In addition, in 2023, U.S. Department of Agriculture’s Forest Service updated their estimate of potential future cleanup costs related to abandoned hardrock mines from about $6 billion to $12 billion. This updated estimate will help Congress and other decision makers understand the full scope of the federal government’s cleanup responsibilities for abandoned hardrock mines. In contrast, Interior has not taken steps we recommended in January 2023 to update cost estimates to incorporate known information about potential future cleanup costs related to abandoned hardrock mines.
In response to our recommendation related to cleanup of sites closed through multiple rounds of the Base Realignment and Closure process, DOD informed Congress in January 2024 about closeout cleanup milestones and estimated sites and associated costs for long-term management. By sharing this information, DOD provided Congress with greater clarity on the full cost of base closures.
What Remains to Be Done
Attention is needed in the areas of environmental liability estimates, workforce planning, stakeholder engagement, developing formal plans, performance goals and metrics, cost-effectiveness of contracting approaches, and cleanup costs to make progress in this high-risk area. Specifically, as of January 2025, 69 recommendations had not been implemented, including 45 recommendations made since 2023. Of these 69 recommendations, 62 pertain to either DOE or DOD and include the following:
· DOE should revise EM’s cleanup policies and develop a program management plan that incorporates the essential elements of a risk-informed decision-making framework.
· DOE should pause construction on the High-Level Waste Facility at Hanford until it takes several actions, including obtaining an independent analysis to ensure an optimal high-level waste treatment plan.
· DOE should take a number of steps to improve EM’s workforce management, including (1) developing a forward-looking workforce plan and (2) providing guidance and training to hiring and resource managers on the use of all available recruitment, hiring, and retention flexibilities, benefits, and incentives.
· DOE should develop a national framework that defines EM’s strategy for engagement with stakeholders and governments and incorporates elements of leading practices for engagement.
· DOD should expand information about its fiscal exposure related to the Red Hill Bulk Fuel Facility by clearly identifying anticipated costs for defueling, remediating, and closing Red Hill in supplemental reports or other budget materials.
· DOE should conduct root cause analyses of EM’s cost and schedule overruns, implement corrective actions, and report annually on the outcome of their implementation.
· DOE should develop a comprehensive approach to prioritizing EM’s research and development across cleanup sites that follows a risk-informed decision-making framework.
· DOE should develop and use performance metrics to regularly inform EM’s groundwater cleanup decisions and document progress toward cleanup goals.
Congressional Actions Needed
We have 16 matters for congressional consideration related to this area, all of which remain unaddressed.
For example, DOE faces legal uncertainties in implementing alternative approaches to managing both its low-activity waste and highly radioactive waste at Hanford, which could save billions of dollars and help to reduce DOE’s environmental liabilities. Congressional action is needed to clarify DOE's authority at Hanford to determine whether portions of the tank waste can be managed as a waste type other than high-level radioactive waste and be disposed of outside the state of Washington. It should be done in a manner that does not impair the regulatory authorities of the Environmental Protection Agency or any state and in consultation with the Nuclear Regulatory Commission. Clarifying DOE’s authority could help the department pursue alternative cost-effective approaches that could be hindered by legal challenges.
In addition, Congress should consider
· enacting legislation to establish a new, dedicated DOE Under Secretary position for nuclear waste management and environmental cleanup; and
· implementing an annual reporting requirement to help ensure EM prioritizes workforce management issues and addresses recurring workforce issues.
Benefits
More than $15.9 billion in financial benefits and more than 30 other benefits to the federal government have been realized since this area was added to our list in 2017. For example:
· In April 2024, DOE and Hanford regulators proposed an agreement under which DOE would treat millions of gallons of low-activity waste using grout instead of glass. This agreement was finalized in January 2025. We recommended in December 2021 that DOE analyze additional disposal options for this waste, including identifying facilities that could receive grouted low-activity waste from Hanford. We estimate that this approach will save about $7.5 billion if DOE can move forward as planned.
· In May 2024, EM stated that it does not plan to resume construction of its $12 billion Pretreatment Facility at the Hanford Site. In 2012, we recommended that EM pause construction on the Pretreatment Facility until it resolved significant technical issues. EM plans to keep the facility in standby until at least 2029—saving $6 billion over 5 years—while evaluating pretreatment options.
· In March 2023, EM completed a program-wide strategy and conducted a review of opportunities to balance cleanup costs with health and environmental risks. This resulted in the decision to accelerate the cleanup of certain nuclear waste at EM’s Savannah River Site in South Carolina by an estimated 22 years and avoiding almost $2.4 billion in costs.
Contact Information
For additional information about this high-risk area, contact Nathan J. Anderson, Director, Natural Resources and Environment, at (202) 512-3841 or AndersonN@gao.gov.
USPS Financial Viability
The U.S. Postal Service (USPS) should continue taking steps to restore its financial viability, and Congress should consider additional changes to fully address USPS’s unsustainable business model.
Why Area Is High Risk
USPS needs to take action to address its poor financial condition. USPS is required by law to provide nationwide postal service—known as the universal service obligation. It has long been expected to be financially self-sufficient by covering its expenses with revenue from the sale of its products and services. USPS has taken significant actions under its own authority since our last update in 2023, but it still cannot fully fund its current level of services and financial obligations.
USPS’s most profitable product, First-Class Mail volume, will likely continue to decline. In addition, USPS faces an increasingly competitive package delivery market, even though it has made significant changes to deliver more packages more efficiently. Meanwhile, USPS’s expenses, particularly employee compensation, continue to rise, and its large unfunded liabilities remain.
Area Rating

Since our last update, USPS has continued to implement its 10-year strategic plan, and consequently the rating for leadership commitment has increased to met. Ratings for the remaining four criteria remain unchanged.
Leadership commitment: increased to met. USPS has taken further steps to implement its 10-year strategic plan released in March 2021. The Postmaster General, USPS’s executives, and its Board of Governors have all championed the plan and adjusted it to USPS’s changing operating environment and economic circumstances. USPS’s leadership ensured that the plan provides a wide-ranging blueprint for organizational change and is focused on achieving USPS’s financial viability.
In implementing this plan, USPS has worked to modernize and streamline its mail and package delivery network and improve the career development and retention of its workforce. Additionally, Congress has exercised continued oversight of USPS, focusing on changes to USPS’s delivery network and financial viability.
Capacity: partially met. USPS has continued to take steps to improve its financial capacity. For example, to increase its revenue, USPS has raised prices on First-Class Mail, periodicals, and other mail products three times since our 2023 update.
However, according to USPS, progress on its efficiency initiatives and lower inflation means that it will wait until at least July 2025 before proposing any further price increases for mail products. In addition, USPS stated that it made over $13.6 billion in capital commitments in fiscal years 2023 and 2024, including for new vehicle acquisitions and new or upgraded facilities.[46] It also paid $1 billion of its required $2.3 billion fiscal year 2024 payment toward its unfunded liability for Federal Employees Retirement System pension benefits.
Nevertheless, USPS’s business model remains unsustainable for several reasons:
· First, USPS’s expenses exceeded revenue by about $16 billion in fiscal years 2023 and 2024 due to increasing labor compensation expenses and declining mail volumes.
· Second, USPS has stated $40 billion in capital investments will be needed to continue meeting its universal service mission. However, its revenue might not fully fund these investments.
· Finally, USPS still must meet its long-term unfunded liabilities and debt—of which USPS’s unfunded liability for pension benefits and retiree health is the largest part. At fiscal year 2024’s end, USPS’s long-term unfunded liabilities and debt totaled about $181 billion or about 228 percent of USPS’s fiscal year 2024 revenue (see fig. 30). USPS officials have stated that it currently cannot provide postal services and fully meet its obligations.
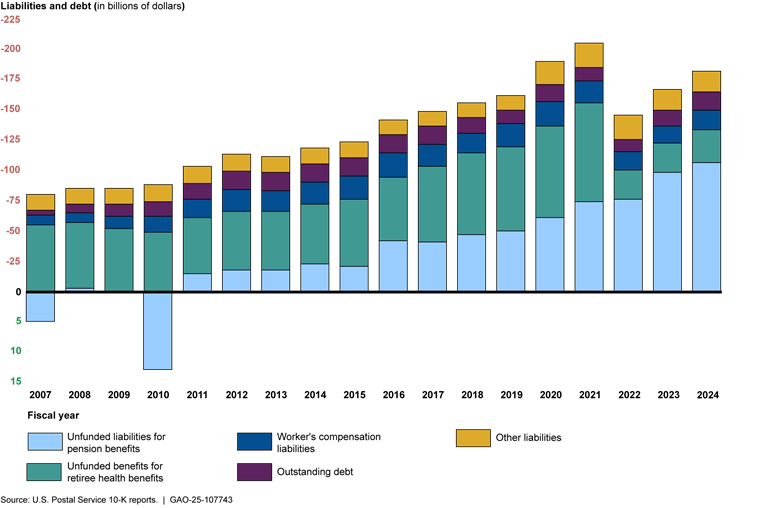
Note: Unfunded retiree health benefits decreased by $57.6 billion in fiscal year 2022 due to the Postal Service Reform Act of 2022. The act repealed a requirement to prepay future retiree health benefits and canceled unpaid past due payments for such prefunding.
USPS estimates that the fund supporting postal retiree health benefits will be depleted in fiscal year 2031. At that point, USPS would be required to pay its share of retiree health care premiums, which USPS projects to be about $6 billion per year. If USPS is unable to pay those premiums some combination of reduced retiree medical benefits, increased retiree or employee payments, higher postage rates, or payments from the federal government to fund these premiums could potentially occur.
Action plan: met. USPS’s 10-year strategic plan continues to include strategies intended to achieve financial viability under the business model modified by the Postal Service Reform Act of 2022. In particular, its updated version of the strategic plan, published in September 2024, notes that USPS’s progress to date “is not enough to make us [USPS] financially sustainable,” and lists numerous goals and objectives for achieving sustainability. According to USPS, its strategic plan was developed based on an analysis of key challenges facing USPS and the postal industry. USPS annually adjusts the over 150 planned projects based on changing conditions and needs. It also regularly issues public reports on progress made toward the financial goals stated in its strategic plan. In fiscal year 2024, USPS updated its strategic plan to revisit USPS’s key challenges and summarize USPS’s major strategies going forward.
Monitoring: met. USPS continues to monitor its financial viability through its independently audited financial reports. These reports provide information on financial trends, such as revenues and expenses, unfunded liabilities, and debt obligations. USPS has also created a website showing service performance data for certain products and has issued additional reports to the President, the Postal Regulatory Commission, and Congress on operational and financial information, as required by the Postal Service Reform Act of 2022.
Demonstrated progress: partially met. Congress and USPS continue to make progress toward achieving financial viability. For example, the Postal Service Reform Act of 2022 significantly reduced USPS’s unfunded liabilities. Further, projects supporting USPS’s new strategic plan are intended, in part, to improve its financial viability. For example, USPS has reduced its transportation expense by about $1.3 billion between fiscal years 2023 and 2024. Reporting on these projects will provide USPS leadership the ability to track progress and measure outcomes.
However, despite the progress described above, USPS forecasts annual net losses until fiscal year 2031 as well as more than $100 billion dollars in unfunded liabilities 4 years into its 10-year strategic plan. As a result, USPS needs to make further progress to improve its financial condition, and Congress should consider whether further legislative action is needed.
What Remains to Be Done
It is important that USPS addresses the issues described above. We have ongoing reviews evaluating USPS’s financial sustainability and USPS’s consolidation of processing facilities. However, USPS should continue to take actions under its own authority to enhance its financial viability while still meeting its mission to provide universal postal service as outlined above. Additionally, congressional action is needed as discussed below.
Congressional Actions Needed
The Postal Service Reform Act of 2022 partially addressed the level of postal services the nation requires and significantly reduced USPS’s long-term unfunded liabilities.[47] For example, the act repealed a requirement to prepay future retiree health benefits on an annual basis and canceled billions in unpaid past due payments for such prefunding. However, USPS will still have to meet its remaining long-term liabilities and debt—of which its liability for retiree health and pension benefits remains the largest part.
There are four open matters to Congress for this high-risk area:
· Reassessing and determining the level of universal postal service the nation requires.
· Determining the extent to which USPS should be financially self-sustaining and what change to law would be appropriate to enable USPS to meet this goal.
· Determining the most appropriate institutional structure for USPS.
· Passing legislation to put postal retiree health benefits on a more sustainable financial footing.
Benefits
Progress in this high-risk area has resulted in about $1.4 billion in financial benefits and more than 20 other benefits since it was added in 2009. For example:
· USPS improved its Strategic Plan project implementation guidance. We found that USPS could better incorporate leading practices in five areas, such as capturing lessons learned. As a result, USPS updated its Strategic Plan guidance documents to help implement its strategic plan.
· USPS improved its capital investment process. We found that USPS did not follow all leading practices for capital investments. Subsequently, USPS revised its policy for capital investments, including a process for thorough evaluation of investment alternatives.
· USPS developed better guidance for its initiatives. Our work found that USPS estimates of expected savings from initiatives had limitations that affect their reliability. Subsequently, USPS established guidance for considering, developing, refining, and approving initiatives.
Contact Information
For additional information about this high-risk area, contact David Marroni, Director, Physical Infrastructure, at (202) 512-2834 or MarroniD@gao.gov.
DOD Weapon Systems Acquisition
The Department of Defense (DOD) needs to improve oversight of its weapon systems acquisition and make better informed investment decisions to ensure the timely delivery of critical capabilities to the warfighter.
Why Area Is High Risk
DOD remains alarmingly slow in delivering new and innovative weapon system capabilities, even as national security threats continue to evolve. In June 2024, we reported that DOD planned to invest more than $2 trillion to develop and acquire its costliest weapon programs. Yet, the expected timeframe for major defense acquisition programs to deliver even an initial capability to the warfighter is 10 years—a timeframe incompatible with evolving threats and the rate of technological change.
Legislation—such as acquisition reforms required by the National Defense Authorization Act for Fiscal Year 2024—has prompted DOD to consider how to address structural barriers that impede its progress in making change, such as its requirements processes. Despite policies that provide increased flexibility, DOD continues to struggle to rapidly deliver complex, software-driven weapon systems.
This high-risk area comprises four segments critical for making overall improvement in weapon systems acquisition: (1) acquisition policy and oversight, (2) software development and cybersecurity, (3) defense industrial base, and (4) innovation investments. We added this area to our High-Risk List in 1990.
Overall Area Rating
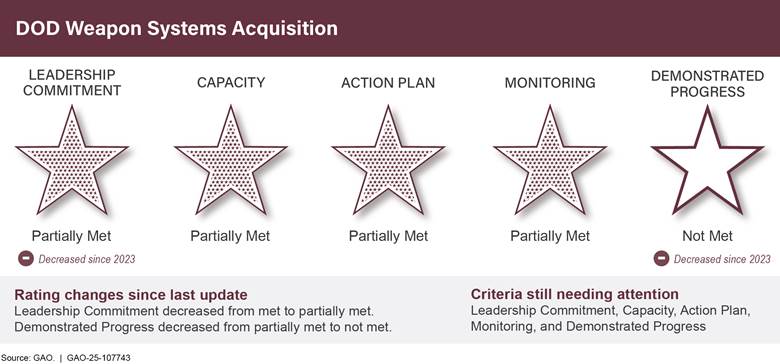
Overall ratings for three criteria remain unchanged since 2023. However, the leadership commitment rating decreased to partially met and the demonstrated progress rating decreased to not met because DOD has yet to take actions to deliver innovative capability to the warfighter and achieve acquisition efficiencies.
The following sections present more detailed information on the four segments summarized in the overall rating. This is the first time we are reporting detailed ratings for each segment.
Acquisition Policy and Oversight

Leadership commitment: partially met. DOD leadership continues its focus on how to execute and oversee programs under the Adaptive Acquisition Framework (AAF), with an emphasis on data-driven oversight. For example, DOD issued updated guidance in 2022 to ensure visibility into the total cost of major defense acquisition programs that use multiple acquisition pathways. DOD also reported initiating an Intellectual Property Community of Practice in February 2024 with five other nations as a part of a joint sustainment supply chain forum.
However, DOD should implement GAO-identified improvements to its acquisition policies that could help improve its acquisition outcomes and rapidly address current and emerging threats. For example, DOD has not updated its acquisition policies to fully incorporate leading practices—including the use of iterative development and modern design tools—that private sector companies use to drive innovation and speed in product development, as we recommended.
DOD is updating its AAF policies, but one recently updated policy and the draft we reviewed of another policy do not fully implement leading practices to achieve positive outcomes. Further, although DOD’s military departments have issued policies in alignment with DOD’s goals and AAF, they do not consistently reflect leading practices.
Capacity: partially met. DOD has identified the resources needed to enhance its acquisition workforce and modernize its acquisition reporting system—a key tool in department and congressional oversight of DOD’s acquisition programs. For example, in 2024, DOD released its Acquisition and Sustainment Workforce Framework aimed at building acquisition and sustainment workforce skills and capabilities. Initiatives captured in the framework include simplifying workforce policies and processes and developing a single workforce hub with resources to simplify and consolidate workforce areas, such as recruiting and training.
DOD established a data governance structure to collaborate on policies, guidance, and best practices related to the use of acquisition data. DOD also issued an implementation plan for its acquisition reporting process that designated some leadership roles and responsibilities for the effort, including offices responsible for maintaining the reporting system. However, it has not established an implementation team with the capacity to manage and implement its data reporting processes, as called for by leading practices.
Action plan: partially met. DOD updated its strategic management plan for fiscal years 2022–2026 to incorporate some outcome-driven performance goals and measures toward meeting national defense strategy goals. DOD also initiated a comprehensive review of its AAF pathway policies in February 2024 to identify needed changes.
However, DOD has yet to formalize an action plan that includes solutions to address root causes to acquisition challenges, such as when the AAF and its associated pathways do not achieve intended outcomes. For example, programs using the middle tier of acquisition pathway—one designed to rapidly develop prototypes or field capabilities within 5 years—have the potential to gain efficiencies. However, some programs plan to finish 5-year prototyping efforts only to require significant additional system development before providing any operational capability to the warfighter.
Monitoring: partially met. DOD has made limited progress in its efforts to conduct data-driven oversight. For example, in November 2023, DOD established guidance for a new reporting system for the major capability acquisition pathway. It also initiated studies to explore how analytic models could improve portfolio decision making.
However, it has not determined key information, such as reporting overall time frames, for programs using multiple pathways to deliver a capability. In addition, DOD has not updated its reporting guidance and data framework to improve cost and schedule reporting on its middle tier of acquisition pathway. DOD officials stated that work is ongoing to address these issues in 2025. For example, DOD completed a 120-day review to determine whether the AAF is achieving its original objectives, and it determined that metrics need to be further developed to assess the condition of the pathways, among other things.
Demonstrated progress: not met. DOD has yet to show it has achieved better acquisition outcomes through the AAF. Since DOD established the AAF in 2020, we have recommended updates to acquisition policies and other program-specific actions aimed at helping DOD and the military departments improve acquisition cost, schedule, and performance outcomes, and deliver fieldable capability with speed.
DOD’s major defense acquisition programs are costing more and taking longer to provide capability to the warfighter, despite increasing needs to deliver capability quickly. For example, the Navy’s acquisition approach for its Constellation class Guided Missile Frigate is inconsistent with leading ship design practices and the Navy expects to deliver its lead ship 3 years late. Further, while DOD’s offensive hypersonic weapon efforts place a high priority on delivering quickly, most of these efforts have not adopted leading practices for product development.

Software Development and Cybersecurity
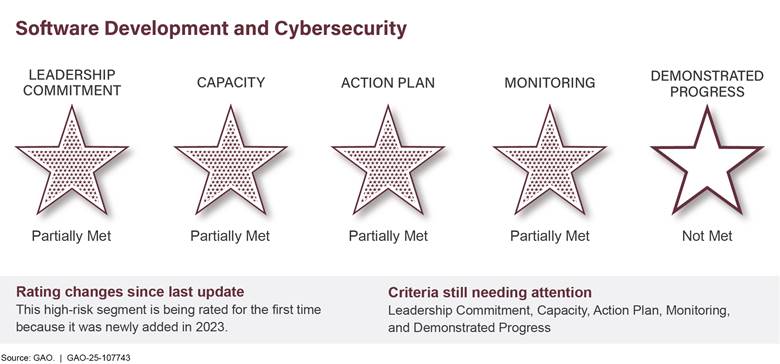
Leadership commitment: partially met. DOD leadership in the Office of the Secretary of Defense has improved key aspects of software development and weapon system cybersecurity. Since our last update in 2023, senior leaders established an implementation plan for the department’s software modernization strategy, executed the congressionally mandated Strategic Cybersecurity Program, and updated software acquisition guidance.
However, DOD leadership has not consistently prioritized activities intended to improve software development and weapon system cybersecurity. For example, we found that DOD continues to struggle to allocate the resources and tools necessary to transform software development within the department.
Capacity: partially met. DOD has made efforts to increase the capacity of its software development and cybersecurity workforces. We recently found that 34 of the 53 software-intensive acquisition programs we reviewed identified challenges with hiring and retaining their software workforce. To address these challenges, DOD has taken steps to establish a congressionally mandated cadre of software development and acquisition experts but is still in the early stages of doing so. DOD officials reported that they are addressing the legislation by educating their workforce and department leadership on modern practices for software acquisition, among other things. However, the DOD cadre remains understaffed and lacks specific plans on how to expand.
Action plan: partially met. DOD has developed some plans to guide its software modernization efforts but has not yet fully addressed other software and cybersecurity actions. In March 2023, DOD published an implementation plan for its department-wide software modernization strategy as we recommended. Among other things, the implementation plan outlines tasks associated with DOD’s Software Modernization Strategy goals and includes current and proposed metrics for assessing some of these tasks.
However, the implementation plan also notes the need to develop additional measures for certain tasks. DOD officials stated additional measures and metrics would be included in an implementation plan for DOD’s Software Science and Technology Strategy, a key department-wide strategy that establishes goals for delivering resilient software capabilities at the speed of relevance. DOD published its Software Science and Technology Strategy Implementation Plan in August 2024. While this implementation plan includes goals and tasks, it lacks the metrics to ensure goals and outcomes. Further, DOD remains challenged to identify resources, including staff, to implement its plans.
Monitoring: partially met. DOD has made some advances in tracking and validating the effectiveness of its efforts to improve software development and cybersecurity. On software development, officials from the Office of the Secretary of Defense told us in September 2024 that they regularly collect software development metrics and programmatic information from programs that are using DOD’s software acquisition pathway. They also noted that DOD will continue to develop means to enable monitoring of software modernization progress. This effort is still in early phases of implementation and DOD has yet to provide us with these metrics.
On cybersecurity, DOD’s AAF calls for decision-makers to review cybersecurity strategies for major defense acquisition programs at all major decision points. However, DOD has not established a mechanism to inform decision-makers in a timely manner of changes to developmental cybersecurity test plans between major decision points.
Demonstrated progress: not met. DOD has yet to demonstrate that it has improved software development or cybersecurity outcomes of its acquisition programs. For example, we found that DOD’s acquisition policies and guidance do not support oversight of weapon programs that are outside of the software acquisition pathway but that are using a modern iterative software development approach. We also found that DOD’s requirements processes do not support these programs. As a result, programs on other acquisition pathways, such as those developing new aircraft or ships, may not be positioned to refine software capability needs in iterations or conduct effective oversight of software capabilities that are delivered in iterations through modern software development practices. While DOD reported an increased use of the software acquisition pathway, we found that few of DOD’s costliest weapon programs were using the pathway for its software development.
The limited use of the software acquisition pathway—and the lack of corresponding policies and guidance supporting oversight for programs that are using modern iterative software development principles on other AAF pathways and requirements processes to support these programs—emphasizes the importance of incorporating these principles into policy and guidance for all programs using modern iterative software development. In addition, the Navy and Marine Corps have not developed guidance to help acquisition programs better communicate cybersecurity requirements to contractors as we recommended.
Defense Industrial Base
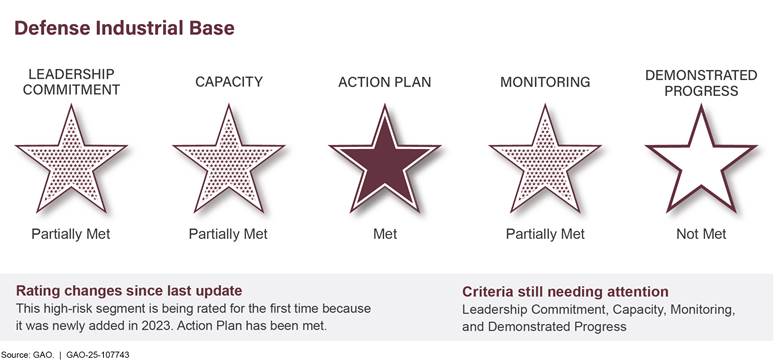
Leadership commitment: partially met. DOD, with assistance from Congress, has addressed some deficiencies in senior leadership to guide efforts to mitigate industrial base risks, but other gaps remain. In March 2023—following years of DOD struggling to drive change in policy due to shifting priorities and resource shortages—the Senate confirmed DOD’s first Assistant Secretary of Defense for Industrial Base Policy. In January 2024, the Assistant Secretary issued DOD’s first National Defense Industrial Strategy. The strategy identifies resilient supply chains, workforce readiness, flexible acquisition, and economic deterrence as four long-term priorities to guide industrial action and resource allocation.
However, we recently found that the Navy’s approach for managing the ship industrial base is not guided by a long-term strategy that aligns with the National Defense Industrial Strategy. In addition, DOD had not linked its industrial base assessment instructions and acquisition policies to AAF pathways, as we recommended.
Capacity: partially met. DOD has demonstrated an ability to focus its workforce and funding to mitigate industrial base risks in response to world crises, but problems persist. For example, DOD is using Defense Production Act funding to increase production to replace weapons sent to Ukraine. However, DOD has only partially identified the funding needed to mitigate its highest priority risks related to implementing the National Defense Industrial Strategy. In addition, the strategy identified workforce readiness as one of its long-term priorities, citing shortages in skilled laborers, engineers, and other science and technology fields. The strategy also identified workforce challenges tied to nuclear submarine production and onshoring domestic production of semiconductors.
Action plan: met. In October 2024, DOD issued an implementation plan for its National Defense Industrial Strategy, as we recommended. The plan identifies the top six cross-cutting initiatives that senior DOD leaders believe will drive significant progress, mitigate key risks to the defense mission, and unify DOD’s efforts for directing investments, resources, and collaboration. The plan also identifies immediate, medium-term, and long-term activities for the six initiatives. DOD intends to update the plan annually after the President’s Budget Request is released.
Monitoring: partially met. DOD has identified the types of metrics it plans to use to gauge progress toward implementing the National Defense Industrial Strategy but has not started reporting its progress. For example, DOD has spent billions since fiscal year 2018 to mitigate a variety of risks but did not have performance measures to gauge and report its progress.
Further, the Navy should identify the information needed to inform investments in the Columbia class supplier base to evaluate outcomes of submarine supplier development funding, as we recommended. In October 2024, DOD announced plans to track its progress toward mitigating risks for six priority initiatives identified in the implementation plan for the National Defense Industrial Strategy. DOD expects to issue a classified annex of the implementation plan in January 2025 with detailed metrics. DOD also plans to reissue the implementation plan annually after the release of the President’s Budget Request.
Demonstrated progress: not met. DOD has not implemented measures that would better position it to mitigate its highest priority industrial base risks. While the department has developed an implementation plan for its National Defense Industrial Strategy and an approach for tracking and reporting on its progress, it is too soon to tell if the plan will be properly resourced to support DOD’s short- and long-term efforts, and whether the efforts achieve their intended benefits.
Innovation Investments

Leadership commitment: partially met. DOD’s leadership initiated new approaches for quickly adopting innovative technologies in certain areas. For example, DOD leadership emphasized the need to move the department toward a more iterative approach to testing and evaluating weapon systems and has updated its operational test and evaluation policy.
DOD has also made progress in implementing a capability portfolio management approach to identify needed capabilities, the systems necessary to provide those capabilities, and the technologies that enable those systems. For example, DOD has completed a technology review of its assured positioning, navigation, and timing portfolio.
However, DOD leadership is not ensuring its costliest weapon programs are structured for speed and innovation. For example, in April 2022, we recommended that the Navy manage its robotic autonomous systems as a portfolio and appoint leadership to advocate for and oversee these investments. As of November 2024, the Navy has not yet addressed these recommendations. DOD also has not documented the roles, responsibilities, and authorities of the leadership positions and organizations responsible for acquiring hypersonic weapons, as we recommended.
Capacity: partially met. DOD has coordinated resources for implementing certain innovation efforts, such as those within the Defense Innovation Unit (DIU), which is focused on accelerating the adoption of commercial technology across the military. For example, in December 2023, DIU formed the Defense Innovation Community of Entities—a group of innovation organizations from across DOD and the military departments—to enhance interagency collaboration and optimize efforts to provide innovative capabilities to warfighters.
However, DOD is lacking the infrastructure to fully equip weapon programs with the modern tools that could accelerate development and delivery. We found that few programs using the major capability acquisition and middle tier of acquisition pathways planned to use digital twins—digital representations of physical objects that enable real-time collaboration and informed decision-making to deliver products with speed—throughout all cycles of their development. Programs cited complications in ensuring open, adaptable, and secure digital engineering tools among the challenges to implementing such leading practices.
Action plan: partially met. DOD has started to identify ways it can align research and development with new acquisition pathways to better support its innovation efforts. For example, in May 2023, DOD issued the National Defense Science and Technology Strategy, which described its strategic lines of effort, including creating and fielding capabilities at speed and scale.
The plan does not, however, identify specific milestones, metrics, or resources needed for its implementation. In addition, military departments have not assessed their needs for modular open systems approaches or determined how to align resources. DIU also has not documented how it will assess the progress of the Defense Innovation Community of Entities.
Monitoring: not met. DOD has yet to track and validate its innovation efforts as we recommended. Specifically, DOD should define the desired mix of near-term, less risky incremental innovation investments and long-term, disruptive innovation investments within the military departments. It should also annually assess whether that mix is achieved through better alignment with leading commercial companies’ approaches to innovative technology development. DOD said it intends to fund a study to evaluate the advantages and risks associated with defining the mix of investments.
DOD has also developed roadmaps for its 14 critical technology areas to assess and prioritize near-term and far-term capabilities to help address the goals of the National Defense Science and Technology Strategy. While this is a step in the right direction, DOD continues to lack effective monitoring of its innovation investments. We have found that DOD lacks plans for addressing issues such as performance management that in turn make it more difficult to insert innovation. For example, DIU lacks a complete performance management process for its latest strategic goal of helping DOD solve its most critical operational gaps, limiting DOD’s insight into whether it is making progress.
Demonstrated progress: not met. DOD is making investments in rapid prototyping and experimentation efforts. DOD reported that, as of December 2024, it has successfully transitioned several experimentation technologies to the warfighter including underwater communications, targeting cells, unmanned surface vessels, and improved communications and sensing capabilities. However, for its costliest weapon programs, DOD’s innovation investments continue to be structured around lengthy, linear development programs rather than the faster, iterative development approaches that our work has shown are necessary to quickly get relevant capabilities to warfighters.
While most of these weapon programs reported using an iterative development approach, they do not plan to fully implement the related leading practices to realize the benefits. For example offensive hypersonic weapon efforts that GAO reviewed placed a high priority on delivering quickly by intending to deliver a minimum viable product—one with the initial capabilities needed for users to recognize value.
However, most of the efforts did not implement key practices such as soliciting user feedback to determine what capabilities to include in their minimum viable product or employing modern digital engineering tools. Without planning to fully implement leading product development practices in the most expensive weapon programs, DOD will continue to miss opportunities to deliver capability with speed and enable further innovation.
What Remains to Be Done
To make progress in this high-risk area, significant management attention is needed. Some of the actions DOD should take related to the four segments include:
· Acquisition policy and oversight: Update acquisition policies to fully implement leading practices for product development, establish an implementation team to manage and implement data reporting processes, formalize an action plan to address root causes to acquisition challenges, improve reporting on key information for programs using multiple pathways and middle tier of acquisition programs, and demonstrate better acquisition outcomes by delivering fieldable capability with speed.
· Software development and cybersecurity: Prioritize resources needed to transform software development within the department, establish a mechanism to inform decision-makers about cybersecurity updates in a timely manner, and improve oversight of software development and cybersecurity for weapon programs that are using modern software approaches.
· Defense Industrial Base: Track and report progress toward mitigating risks identified in the National Defense Industrial Strategy, develop a long-term ship industrial base strategy, identify funding needed to mitigate the highest priority industrial base risks, and address workforce challenges tied to submarine and semiconductor production, among others.
· Innovation investments: Structure acquisition programs for speed and innovation to align with leading practices; provide adaptable and secure digital engineering tools; assess the needs for modular open systems approaches and how to align resources to support these efforts; identify specific activities, milestones, and metrics to guide implementation of the National Defense Science and Technology Strategy; define the desired mix of incremental and disruptive innovation investments; and assess whether its innovative efforts are working as intended.
As of January 2025, 238 recommendations to DOD related to this high-risk area remain open, such as:
· update DOD and component acquisition policies to fully implement the key product development principles used by leading companies;
· develop and use performance measures to monitor the aggregate effectiveness of mitigation efforts for DOD-wide industrial base risks; and
· define the desired mix of incremental and disruptive innovation investments within military departments and annually assess whether that mix is achieved.
Congressional Actions Needed
There are also five open matters for congressional consideration, including:
· To support oversight of weapon systems acquisition and inform budget decisions, Congress should consider requiring DOD to report on each major acquisition program’s systems engineering status in the department’s annual budget request, beginning with the budget requesting funds to start development.
· To support oversight of the Navy’s shipbuilding programs, Congress should consider
· updating statutory certification and production readiness review reporting requirements for Navy shipbuilding programs under section 8669c of title 10 United States Code, to require certification of the completion of basic and functional design in 3D modeling and the positioning and routing of all major distributive systems prior to the start of construction (consistent with leading industry practices in ship design).
· requiring, as part of section 8669c of title 10, United States Code, that the Navy certify that detail design will be completed for each block of a ship's construction before beginning construction of that block.
· requiring, as part of section 8669c of title 10, United States Code, that the Navy report on the degree of vendor-furnished information completeness supporting the overall maturity and stability of a ship's design before beginning construction.
· To support oversight of divestments in tactical aircraft, Congress should consider requiring the Air Force to provide specific types of data and analyses to Congress before making determinations to divest tactical aircraft. These data and analyses should include cost assessments inclusive of all relevant factors, gaps in capacity and capability created by the divested asset, and realistic strategies for mitigating those gaps, as well as the cost of these strategies.
Benefits
Since this area was added to the High-Risk List in 1990, progress in the acquisition of DOD weapon systems has led to about $275 billion in financial benefits and more than 450 other benefits. For example:
· DOD established a plan to assess the effects of recent acquisition reform efforts and updated guidance to ensure visibility into the total cost of weapon system programs that use multiple efforts or acquisition pathways.
· DOD has established new guidance for an iterative approach to software development and has begun to share these practices across software development efforts.
· DOD issued guidance that includes instructions for using financial flexibilities associated with the Defense Laboratory Modernization Program.
· DOD issued its first National Defense Industrial Strategy in January 2024, which lays out the long-term priorities for industrial base action.
Contact Information
For additional information about this high-risk area, contact Shelby S. Oakley, Director, Contracting and National Security Acquisitions, at (202) 512-4841 or OakleyS@gao.gov.
Improving IT Acquisitions and Management
To better manage substantial annual investments in IT, the Office of Management and Budget (OMB) and other federal agencies need to strengthen oversight and management of IT portfolios, implement mature IT acquisition and development practices, and build federal IT capacity and capabilities.
Why Area Is High Risk
The executive branch has undertaken numerous initiatives to better manage the more than $100 billion that is annually invested in IT. However, federal IT investments too frequently fail to deliver capabilities in a timely, cost-effective manner. Recognizing the seriousness of issues related to the government-wide management of IT, in December 2014 Congress enacted federal IT acquisition reform legislation, commonly referred to as the Federal Information Technology Acquisition Reform Act (FITARA).[48] In 2015, we added the government’s management of IT acquisitions and operations to the High-Risk List.
Since then, this high-risk area has become increasingly more complex as technologies have evolved and the skills needed to manage such technologies have changed. Further, critical government systems have continued to age and become either obsolete or extremely costly to maintain. Key management challenges—such as a lack of disciplined project planning and program oversight—continue to hamper effective acquisition and management of the government’s IT assets.
Area Rating
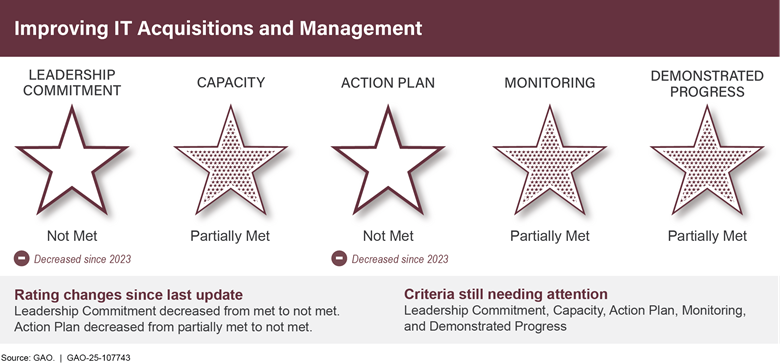
Ratings for three of the five high-risk criteria have remained unchanged since 2017. However, OMB—which, by law, has broad IT acquisition and management oversight responsibilities for the federal government—has not maintained its level of leadership commitment to ensure that agencies improve IT acquisitions and management. As such, the leadership commitment rating decreased from met to not met. In addition, agencies have not maintained efforts to develop and implement action plans to address IT management issues. Therefore, the action plan rating decreased from partially met to not met. Other IT challenges also persist, including workforce issues, weak agency portfolio oversight and management, and undisciplined development and acquisition practices.
Leadership commitment: decreased to not met. This rating has decreased because OMB has not maintained leadership support and commitment to improving agencies’ IT acquisitions and management. For example, we reported in November 2024 that OMB did not fulfill three FITARA requirements to review high-risk IT investments. In addition, OMB did not meet or only partially met all five FITARA requirements for IT portfolio reviews, including for the Federal Chief Information Officer (CIO) to be involved with each agency’s annual review.
Further, while OMB previously demonstrated its leadership commitment by, among other things, issuing guidance for covered agencies to implement FITARA provisions, OMB has not revised this guidance since 2015 and it is now outdated. OMB’s lack of annual IT portfolio reviews and updated high-risk investment review guidance has directly resulted in agencies’ inability to fulfill their FITARA requirements.
Capacity: partially met. Since our 2023 update, OMB and the General Services Administration (GSA) have strengthened their management of the Technology Modernization Fund (TMF), which awards federal agencies funds to, among other things, replace aging IT systems. OMB and GSA have addressed issues related to the collection of administrative fees used to offset operating expenses for overseeing the fund and issued guidance for improving the reliability of projects’ cost estimates.
However, GSA was not positioned to fully recover these fees in a timely manner and decided to stop collecting them. Instead, GSA and OMB implemented a plan to set aside money from the fund to cover its operating expenses and helped ensure TMF’s ability to fund future projects. In addition, GSA updated its TMF guidance to identify required data elements and fields to help ensure the accuracy and completeness of projects’ cost estimates. While agencies’ planned cost savings for TMF projects were substantial—about $741 million—their actual savings as of February 2023 were minimal, only about $15 million.
Agencies have also made progress in implementing key IT workforce planning activities, such as establishing a workforce planning process, assessing gaps in competency and staffing needs, and implementing activities to address any such gaps. However, four agencies have not yet implemented those workforce planning activities, as we recommended.[49]
Further, progress in improving the role of federal agency CIOs is limited. For example, as of December 2024, 10 of the 24 major federal agencies had not yet fully implemented our recommendations to ensure agency policies address the role of the CIO for key responsibilities in areas such as IT investment management and the IT workforce, consistent with federal laws and OMB’s FITARA guidance.
Moreover, because the Federal CIO position was not established in law, its IT management responsibilities were more limited than federal agency CIOs and private sector CIOs. For example, within some individual management areas the Federal CIO’s responsibilities often involved providing high-level advice, coordination, or support, in contrast to the more directly involved roles of agency and private sector CIOs. Congress should consider formalizing the Federal CIO position and establishing responsibilities and authorities for government-wide IT management. In addition, OMB should increase collaboration between CIOs and other executives and consider managerial skills in CIO hiring criteria. As of December 2024, Congress and OMB have not addressed these issues.
Action plan: decreased to not met. This rating has decreased because agencies have not maintained efforts to develop and implement action plans to address IT acquisition issues on troubled mission-critical systems in need of the most attention.
For example, the Department of Education's Office of Federal Student Aid (FSA) did not develop a plan to tailor guidance on defining and managing requirements to fit its incremental approach to deploying the Free Application for Federal Student Aid (FAFSA) Processing System. This system is intended to replace FSA’s aging system that processes the forms students and parents use to apply for financial aid (known as the FAFSA form).
The initial rollout of the new system was delayed several times and its eventual rollout in December 2023 was immediately met with technical issues, some of which were critical. These technical issues led to troubling effects on students, parents, and schools, including their ability to plan for the upcoming school year. This contributed to about 9 percent fewer high school seniors and other first-time applicants submitting a FAFSA as of August 25, 2024.
In January 2025, Education officials reported that FSA had implemented changes to improve the user experience and streamline the completion of the FAFSA. However, multiple technical issues remain that continue to affect some students and their families, making it harder for them to complete a FAFSA.
Until FSA develops and implements a plan for tailoring its approach for defining and managing requirements for the FAFSA Processing System, it will continue to be at increased risk of delivering functionality that does not fully meet user needs. In addition, Education should review the FAFSA application process to identify additional ways to reduce the burden on students and families by addressing the remaining technical issues.
In another example, the Federal Aviation Administration (FAA), within the Department of Transportation, has recently been experiencing increasing challenges with aging air traffic control systems. After a shutdown of the national airspace in 2023 due to the outage of an aging air traffic control system, FAA conducted an operational risk assessment to evaluate the sustainability of all air traffic control systems. The assessment determined that of its 138 systems, 51 (37 percent) were unsustainable and 54 (39 percent) were potentially unsustainable (see fig. 32).
Figure 32: Federal Aviation Administration (FAA) Air Traffic Control (ATC) System Sustainment Ratings

Of the 105 unsustainable and potentially unsustainable systems, 58 (29 unsustainable and 29 potentially unsustainable systems) have critical operational effects on the safety and efficiency of the national airspace (see fig. 33).
Figure 33: Federal Aviation Administration (FAA) Air Traffic Control System Safety and Efficiency Operational Impact Categories by Sustainment Rating
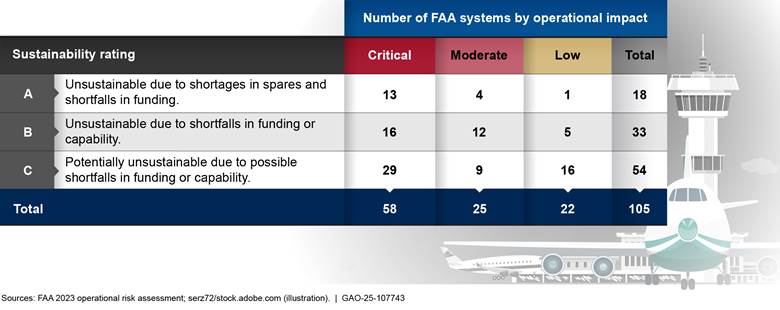
While FAA had 64 ongoing investments aimed at modernizing 90 of the 105 unsustainable and potentially unsustainable systems, it has been slow to modernize the most critical and at-risk systems. In some cases, they were not planned to be completed for 10 to 13 years. In addition, because FAA did not have ongoing investments associated with four of these critical systems it is unknown when associated systems will be modernized. FAA should report to Congress on how it is mitigating risks of all unsustainable and critical systems that are identified in the annual operational risk assessments.
Further, the Department of Veterans Affairs (VA) has faced challenges in implementing its new electronic health record (EHR) system. After three unsuccessful attempts between 2001 and 2018, VA initiated a fourth effort—the EHR modernization program—to replace its legacy system. In 2022 the Institute for Defense Analysis estimated that EHR modernization life cycle costs would total $49.8 billion—$32.7 billion for 13 years of implementation and $17.1 billion for 15 years of sustainment.
In April 2023, VA halted future deployment of its EHR system to make improvements at five locations currently using the system. In March 2024, VA deployed its EHR system at a sixth location. There are over 160 remaining locations for EHR implementation. However, in its updated fiscal year 2024 action plan, VA did not include any corrective actions, milestones, or performance measures related to deploying this system. In December 2024, VA announced that it had restarted predeployment planning activities and selected four additional locations to deploy its EHR system in mid-2026.
Monitoring: partially met. Agencies made some progress by taking actions to improve oversight of IT programs, performance measurement, and risk management. However, agencies need to take additional actions, such as monitoring progress in addressing competency and staffing gaps, and measuring IT performance against established standards.
Demonstrated progress: partially met. Since 2023, agencies have made progress by taking actions such as establishing mechanisms to track savings and cost avoidances from the migration and deployment of cloud services, and implementing strategies to reduce IT contract duplication. Specifically, OMB and agencies fully implemented 150 of our recommendations since our 2023 update.
However, the federal government needs to, among other things,
· improve the effectiveness of key IT leadership positions, including the federal CIO and agency CIOs;
· develop reliable cost estimates and schedules and effectively manage requirements; and
· address workforce management challenges for the technically-capable workforce.
What Remains to Be Done
Agencies need to urgently address nine critical actions associated with three major IT management challenges that we have identified (see fig. 34).
Figure 34: Nine Critical Actions Federal Agencies Need to Take to Address Three Major IT Management Challenges
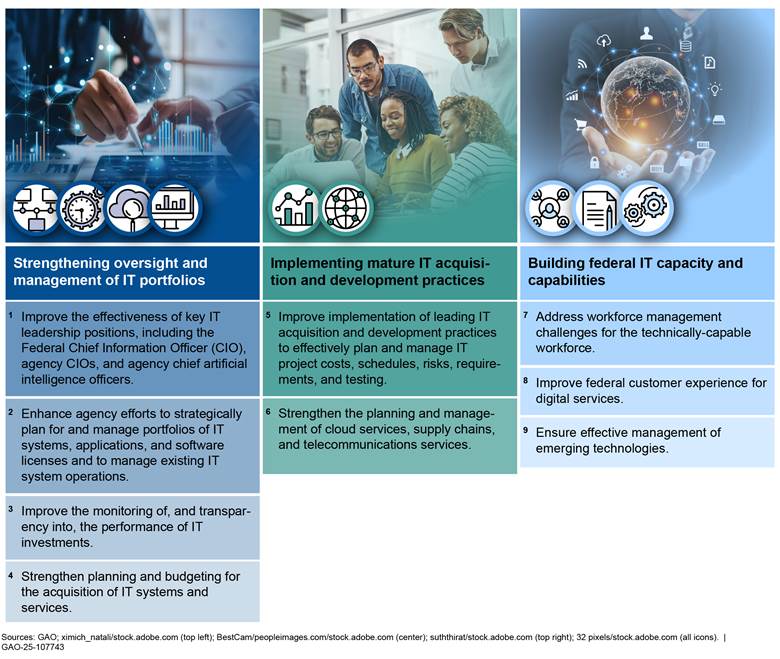
Also, agencies have fully implemented 1,286 (68 percent) of the 1,881 total recommendations we have made since fiscal year 2010 to address shortcomings in IT acquisitions.[50] As part of addressing the nine critical actions, agencies should implement our remaining 463 open recommendations related to this high-risk area. For example, federal agencies need to
· improve the monitoring of, and transparency into, the performance of IT investments;
· strengthen the planning for and management of cloud services and supply chains; and
· ensure effective management of emerging technologies.
Congressional Actions Needed
Congress should consider formalizing the Federal CIO position and establishing responsibilities and authorities for government-wide IT management, an open recommendation for this high-risk area that we suggested in September 2022. In addition, continued oversight by Congress to hold agencies accountable for implementing FITARA provisions and addressing longstanding IT acquisition and management weaknesses is essential.
Benefits
Financial benefits due to progress in this high-risk area totaled more than $9.3 billion since it was added to the list in 2015. Additionally, there were more than 600 other benefits due to progress in this high-risk area over the past 10 years. For example:
· In April 2019, we reported mixed progress at 24 agencies toward achieving OMB’s goals for closing federal data centers. These agencies had also made limited progress against OMB’s data center optimization targets. By December 2023, 23 of the 24 agencies had met data center closure, optimization, and savings goals. By reducing the number of duplicative or outdated federal data centers, agencies reduced spending and projected costs in this area by $6.6 billion from fiscal years 2012 through 2021.
· In January 2018, we found that 21 of 22 selected agencies did not identify $4.5 billion in fiscal year 2016 IT obligations. In addition, 14 agencies did not follow OMB guidance to involve the acquisition office to identify IT acquisitions for CIOs’ reviews. By March 2022, all of these agencies had addressed recommendations to ensure that all IT-related acquisitions are properly identified and to involve the acquisition office in this process.
· The National Institute on Aging (NIA) initiated a federal project to improve research into Alzheimer’s disease by compiling and analyzing real world data. In March 2024, Congress cited our ongoing work that found the NIA’s project minimally met the four characteristics of a reliable cost estimate. Congress urged the agency to pause a planned award for the project. In light of our work and other developments in Alzheimer’s research, NIA decided not to fund the project in April 2024, resulting in reduced expenses of approximately $282 million over 6 years.
Contact Information
For additional information about this high-risk area, contact Carol Harris, Director, Information Technology and Cybersecurity, at (202) 512-4456 or HarrisCC@gao.gov.
Managing Federal Real Property
Better management of the federal government’s real property portfolio is needed to effectively dispose of unneeded buildings, collect reliable real property data, and improve the security, condition, and configuration of federal facilities.
Why Area Is High Risk
Federal agencies have long struggled with underutilized space, which costs millions of dollars. This has been further complicated following the COVID-19 pandemic and increased telework where federal agencies are not using a significant portion of space in their office buildings. Congress and the Office of Management and Budget (OMB) took steps in 2024 to require agencies to measure and improve utilization, but those efforts are just beginning. In addition, the process for disposing of federal assets remains complex.
While the General Services Administration (GSA) has improved the accuracy of addresses in its Federal Real Property Profile database, the data are not yet reliable. This makes it difficult to manage federally owned assets.
The Department of Homeland Security (DHS) has taken steps over the years to improve facility security, but more progress is needed. Contract guards did not detect prohibited items in about half of our 27 covert tests in 2024. This is a rate comparable to the Federal Protective Service’s (FPS) own covert testing results. In addition, FPS has not yet fully deployed the Post Tracking System, under development since 2013, to verify that all guards were qualified to stand post, due to ongoing interoperability, technical, and data reliability problems.
This year we are adding a new segment, “Building Condition,” to this high-risk area for several reasons. The federal government’s annual maintenance and operating costs for its 277,000 buildings exceeded $10.3 billion in fiscal year 2023. However, federal agencies have deferred maintenance and repairs on many buildings, creating a backlog. We found that these needs had more than doubled, going from $170 billion to $370 billion from fiscal years 2017 through 2024. In addition, agency officials said they need to reconfigure office space to support increased telework and maximize use of their headquarters buildings.
Overall Area Rating
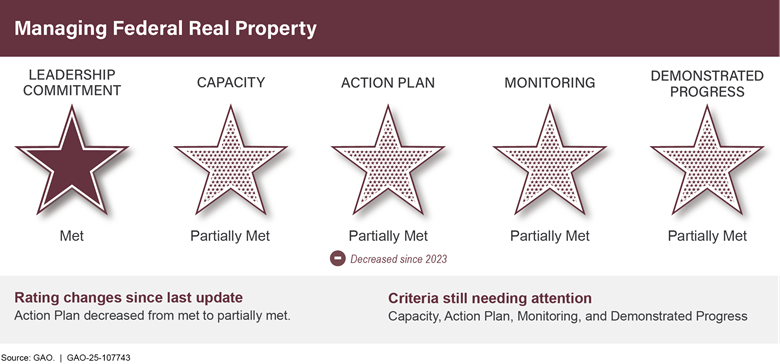
Since the last update, overall ratings remain unchanged except for the action plan criterion, which decreased from a met to a partially met rating in two of the four segments: Underutilized Property and Facility Security. The following sections present more detailed information on the three segments summarized in the overall rating.
Underutilized Property
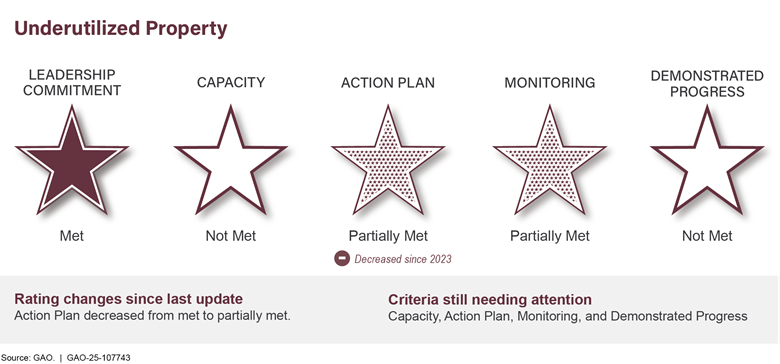
Leadership commitment: met. GSA, OMB, and Congress continue to demonstrate leadership commitment to disposing of unneeded property. For example, GSA officials said that GSA initiated a full portfolio assessment to identify assets for disposal on a rolling basis. Since our last update, GSA identified 34 assets to begin the disposal process. GSA estimates that disposing of these buildings will reduce GSA’s inventory by over 6 million square feet and save $1.8 billion over 10 years. In August 2024, OMB established a new benchmark for measuring utilization that could help agencies identify and shed unneeded space. Enacted in January 2025, the Utilizing Space Efficiently and Improving Technologies (USE IT) Act includes additional requirements for agencies to measure building utilization and plan to dispose of underused space.[51]
Capacity: not met. The Federal Assets Sale and Transfer Act of 2016 (FASTA) established a temporary, three-round process to increase the federal government’s capacity to identify and dispose of unneeded assets, among other things.[52] Recently enacted legislation also directed an additional round to identify additional properties.[53] Prior to this legislation, officials from GSA and the temporary Public Buildings Reform Board (the Board) said that they expected the process to date to result in only one of three rounds succeeding.
This process required coordination among GSA, OMB, and the Board. In October 2022, we found that GSA did not have an approach to leverage knowledge gained from setbacks experienced in the FASTA disposal process. While GSA has identified strategies for disposing of unneeded properties, GSA needs to develop a documented process to work with relevant stakeholders to identify and implement solutions to address numerous setbacks encountered throughout the FASTA process.
Action plan: decreased to partially met. Federal agencies have had mixed results in planning to address property utilization. OMB’s utilization benchmark and the USE IT Act require agencies to measure attendance and right-size spaces.[54] However, these efforts are just beginning. GSA and the Board did not develop a plan for identifying a unified list of assets for the final round of FASTA disposals. Outside of the FASTA process, GSA identified 34 properties for disposal independently of the Board.
Monitoring: partially met. OMB and Congress have taken steps to better monitor space utilization in federal office buildings. In October 2023, we found that the headquarters buildings for 17 of 24 federal agencies were used at or below an estimated average of 25 percent capacity for 1 week in each of the first 3 months of 2023. However, agency officials identified challenges to increasing space utilization, including a lack of benchmarks to measure building utilization. Since then, OMB and the USE IT Act have established new building utilization benchmarks but implementation is just beginning.
Demonstrated progress: not met. Since our last update, little progress was made in improving the outcomes of the FASTA disposal process. We reported in October 2022 that GSA and other stakeholders faced setbacks implementing the FASTA process, including delaying the sale of properties OMB had approved for disposal in the first round. As of December 2024, the entire FASTA process identified 12 properties for disposal, 10 of which sold for a total of $194 million. In addition, while agencies are implementing the new OMB and USE IT Act office space utilization benchmarks, potential space-saving benefits have not yet been realized.[55]
Data Reliability
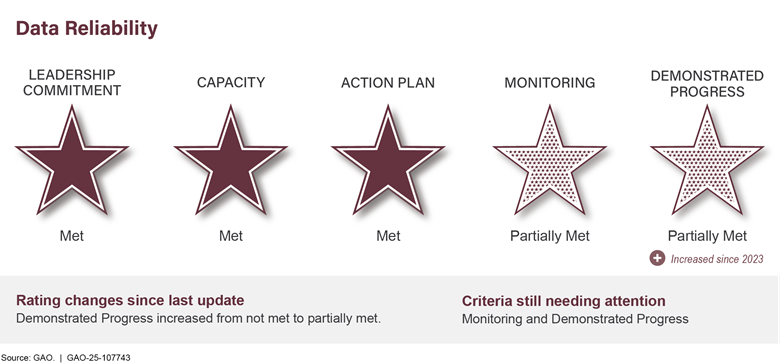
Leadership commitment: met. GSA continues to demonstrate leadership commitment in improving its data reliability. For example, in August 2024, the Federal Real Property Council (the Council) published program guidance to help federal agencies continually improve the quality of data they submit to the Federal Real Property Profile database.[56] The guidance is intended to ensure that data elements accurately describe the attributes of their real property assets.
Capacity: met. The government continues to take actions to increase agencies’ capacity to submit accurate data. For example, the 2024 data quality improvement guidance instructs agencies to concentrate their initial data quality improvement efforts on certain data elements. These data elements consist of the core, largely static data elements, such as property type and property use, that are most easily verified with external information.
Action plan: met. GSA established a strategic initiative to improve real property data accuracy through data standards and management in its strategic plan for fiscal years 2022 through 2026. In addition, the Council published the previously mentioned data quality improvement guidance.
Monitoring: partially met. GSA implemented a tool that alerts agencies to potentially incorrect location data in the Federal Real Property Profile database. However, the data continue to contain errors in key data fields.
The U.S. Department of Defense (DOD) has also worked to improve its monitoring of real property data. In November 2018, we found that DOD was not effectively recording and reporting data, which led to inaccurate and incomplete real property information. Subsequently, DOD has defined and documented the data elements that are most significant for decision-making. In addition, the Navy, Air Force, and Army improved monitoring of their respective processes for recording all required real property information. However, DOD has not completed a department-wide approach to improving its data quality.
Demonstrated progress: increased to partially met. GSA relies on federal agencies to submit accurate data to the Federal Real Property Profile database. However, GSA’s Validation and Verification process has addressed some, but not all, key errors in the data. For example, in 2020, we reported that 67 percent of addresses in the database were incorrectly formatted or incomplete. Specifically, our analysis of the location data in the 2023 database found that over 98 percent were correctly formatted. However, our analysis also showed that the location data continue to have key errors.
Facility Security
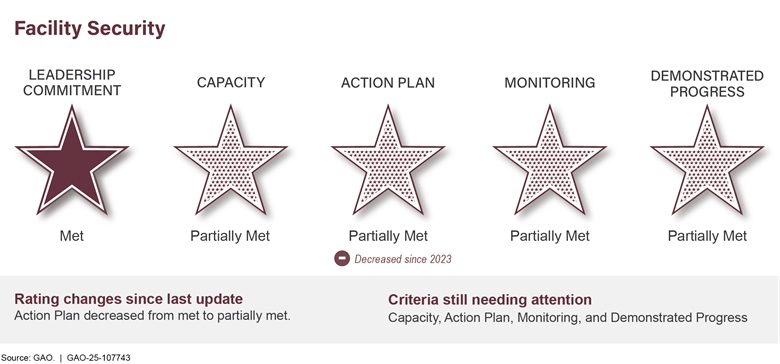
Leadership commitment: met. The administration and DHS continue to demonstrate leadership commitment to improve facility security. In November 2023, President Biden issued Executive Order 14111, superseding and updating Executive Order 12977, which established the Interagency Security Committee (ISC), now chaired by DHS.[57] This update clarifies the ISC’s oversight role in monitoring agencies’ compliance with ISC’s physical security standards at federal facilities.
Capacity: partially met. FPS has taken some steps to address the agency’s long-standing staffing and human capital management challenges. In 2022, we reported that 21 percent of FPS’s authorized positions were not filled, a staffing shortage that persisted in 2024. We found FPS and DHS Management Directorate’s human capital office were not collaborating on the hiring process, which partly caused the staffing shortage. We recommended that FPS and the DHS Management Directorate—in which FPS is placed—strengthen mechanisms to facilitate collaboration and agreement on hiring processes. FPS has begun to define and document roles and responsibilities, steps for decision-making, and time frames for completing hiring actions. Once fully implemented, our recommendation could help FPS more effectively and efficiently address its staffing shortages.
Action plan: decreased to partially met. While FPS made progress in developing performance measures, we identified new challenges with facility security. In 2024, FPS developed performance measures and related performance targets for each of the strategic objectives in its strategic plan.
However, in 2024, we conducted 27 covert tests at selected federal facilities and found that FPS’s contract guards failed to detect prohibited items about half the time. These results, which are consistent with FPS’s findings in its internal covert testing program, raise questions about how effectively the guards detect prohibited items. We recommended that FPS collect more consistent data about the causes of test failures, analyze those data, and then use that analysis to improve contract guards’ detection capabilities.
Monitoring: partially met. The ISC improved its oversight of FPS-recommended security countermeasures to protect federal facilities, as we recommended in May 2023. The ISC is updating its annual questionnaire to include questions that will assess agencies' implementation of FPS-recommended countermeasures, according to ISC officials. The ISC has also developed standard operating procedures to assess how agencies document risk acceptance when they do not implement FPS-recommended countermeasures in their facilities.
However, FPS has had mixed success implementing two data systems to help it oversee contract guards. FPS expects the data system that tracks contract guards’ training requirements to be fully implemented by 2025. However, the data system that FPS uses to verify if contract guards are qualified to stand post—the Post Tracking System—continues to face technology, interoperability, and data reliability challenges. In 2025, we recommended that DHS determine whether to replace the Post Tracking System or make corrective actions to the existing system.
Demonstrated progress: partially met. Federal agencies have made mixed progress improving their management of facility security risks. The Federal Aviation Administration, Forest Service, Agricultural Research Service, and U.S. Customs and Border Protection improved their physical security programs so they aligned with the ISC risk management standard. Although the Department of Veterans Affairs has taken steps to assess physical security risks to their facilities, it has not yet fully implemented our 2018 recommendations to improve alignment with the ISC risk management standard.
Further, in response to recommendations we made after the January 2021 attack on the U.S. Capitol, the Capitol Police Board and the Capitol Police developed procedures to obtain outside assistance in an emergency as well as to either implement recommended security countermeasures or document risk acceptance if those countermeasures were not implemented.
Building Condition
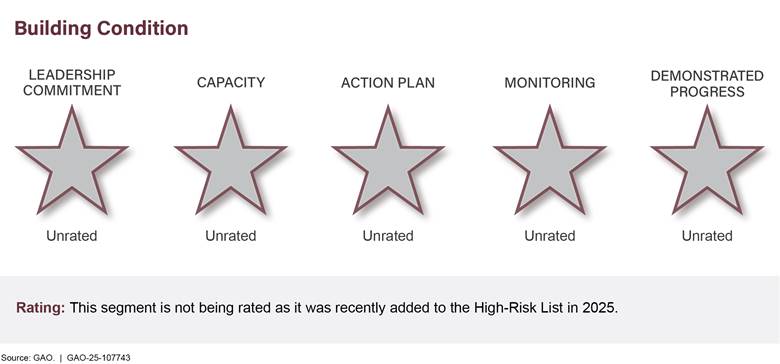
Leadership commitment. The administration and agencies need to make a compelling business case to Congress for funding facility repair and maintenance needs. In 2023, we reviewed four agencies and found they did not fully communicate the potential costs of maintenance backlogs to Congress. For example, those four agencies did not provide sufficient information in their financial and budget documents to explain how much of their backlog supported agency missions. As a result, Congress and the public do not have a clear picture of the anticipated costs to address deferred maintenance resources needed to support critical government functions. We recommended that GSA and the Departments of Health and Human Services, the Interior, and Energy fully communicate repair needs to Congress and the public.
Capacity. Officials from all four agencies we reviewed in 2023 said that maintenance funding had not kept up with costs, leading to increased deferred maintenance and repairs. Similarly, in a separate report, agency officials indicated they need additional budget resources to reconfigure their spaces to support increased telework. They ranked this as the top challenge to increasing utilization of their headquarters buildings. For example, U.S. Department of Agriculture officials said they would need millions of dollars in investments to update their two-building headquarters to support higher density and office sharing.
Action plan. Federal plans for reducing the repair backlog and better configuring buildings are limited. Better information on the scale and potential impacts of the repair backlog and the benefits of modern configurations would help make a business case for funding. In 2023, we recommended that agencies provide more information on their repair backlog estimates based on leading practices for managing deferred maintenance and repair. In addition, we found in 2023 that military barracks were in poor condition, including some with safety risks like sewage overflow and inoperable fire systems, and recommended that DOD clarify guidance and the service branches update minimum health and safety standards.
In addition, agencies ranked the need for additional budget resources to reconfigure their spaces to support a hybrid office environment as the top challenge to increasing utilization. As a first step for determining how much space agencies need, in August 2024, OMB issued a benchmark for measuring utilization in the modern office space that accounts for increased telework.
Monitoring. GSA has not effectively monitored its maintenance contractors to ensure they implemented required maintenance and repairs. In 2024, the GSA Inspector General found that operations and maintenance contractors did not complete all work orders for service requests and preventive maintenance. In some cases, operations and maintenance contractors marked work orders as complete even though the work was not actually completed. The Inspector General recommended that GSA improve its oversight of contractors.
Demonstrated progress. DOD and federal civilian building repair backlogs have more than doubled, going from $171 billion to $370 billion from fiscal years 2017 through 2024 (see fig. 35). Unless this trend reverses, federal assets will continue to deteriorate and lead to premature replacement, which can be significantly more expensive than the cost of repairs had they not been delayed. In addition, if agencies continue to operate in office buildings that are poorly configured, they will continue to underutilize those buildings, spending unnecessary operating funds.
Figure 35: Federal Civilian Agencies’ and U.S. Department of Defense Reported Estimates of Deferred Maintenance and Repairs, Fiscal Years 2017–2024
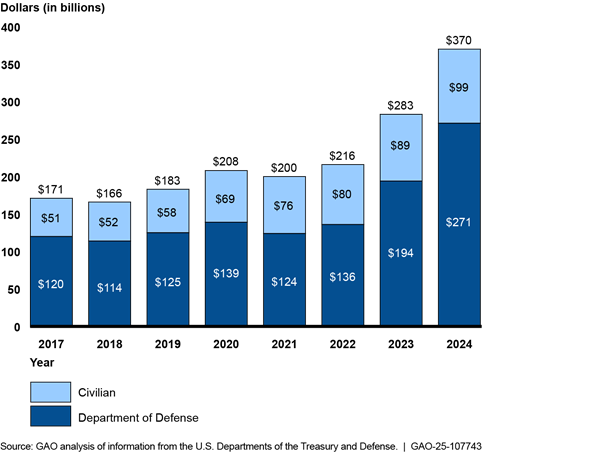
What Remains to Be Done
Work remains to be done to improve building utilization, data reliability, facility security, and building condition. Specifically, there are 58 open recommendations related to underutilized property, data reliability, facility security, and building condition. Implementing these recommendations in addition to addressing issues identified above will help agencies make progress. For example:
· OMB should better identify and shed unneeded space by holding agencies accountable for applying the new utilization benchmark as soon as possible.
· GSA should help federal agencies improve the disposal of underutilized property by applying lessons from the FASTA process to improve the property disposal process.
· GSA should help federal agencies improve their data reliability by implementing the data quality standards identified in its August 12, 2024, guidance, and ensuring street address information is accurate.
· FPS should improve the success rate of prohibited item detection by collecting more consistent data, analyzing the data, and applying the analysis.
· Federal agencies should provide more information to Congress and the public regarding the deferred maintenance and repair backlog, including, at a minimum, the amount needed to support their missions.
· DOD should update and clarify guidance on barracks conditions, obtain complete funding information, and increase oversight of barracks programs.
Benefits
Progress in managing the federal real property high-risk area since this area was added to the list in 2003 resulted in more than $3.6 billion in financial benefits and more than 250 other benefits. For example:
· We removed the Costly Leasing segment from this area in 2021 because lease costs had decreased enough that it was no longer a high-risk concern. According to GSA estimates, the purchase of the Department of Transportation’s headquarters building in 2020, which it had previously leased, will save taxpayers more than $409 million in lease costs over 30 years.
· The USE IT Act, enacted in January 2025, requires federal agencies to measure their use of public buildings and reduce excess capacity.
· In August 2024, OMB issued a utilization benchmark to help federal agencies identify opportunities to dispose and consolidate office space, support multiagency co-locations, reduce costs, and enhance efficiency.
· In August 2024, the Council published data validation and verification guidance to help agencies provide more reliable real property data.
Contact Information
For additional information about this high-risk area, contact David Marroni, Director, Physical Infrastructure, at (202) 512-2834 or MarroniD@gao.gov.
Acquisition and Program Management for DOE’s National Nuclear Security Administration and Office of Environmental Management
The National Nuclear Security Administration (NNSA) and the Office of Environmental Management (EM) need to improve oversight of their acquisition processes and better manage their multi-billion dollar portfolios, programs, and projects.
Why Area Is High Risk
The Department of Energy (DOE) oversees a broad range of programs including nuclear security and waste cleanup. DOE relies primarily on contractors to carry out its portfolios, programs, and projects. It spends more than 90 percent of its annual budget on contracts. In fiscal year 2024, DOE’s budget was about $50.2 billion, of which $24.1 billion went to NNSA and $8.7 billion went to EM.
We designated this area as high risk in 1990 because DOE’s record of inadequate management and oversight of contractors left it vulnerable to fraud, waste, abuse, and mismanagement. In 2009, this area was narrowed to focus on NNSA and EM within DOE. NNSA is responsible for modernizing the nation’s nuclear stockpile and related infrastructure, as well as leading programs to address global nuclear security and to fuel the nuclear Navy. EM was created to clean up hazardous and radioactive waste at sites and facilities contaminated from decades of nuclear weapons production and nuclear energy research.
Overall Area Rating
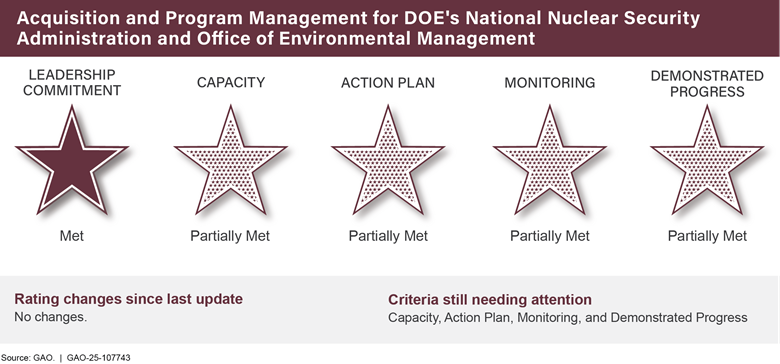
Overall ratings for all five criteria remain unchanged since 2023. Two criteria for the Acquisition and Program Management for the EM segment—action plan and monitoring–—increased from partially met to met. The following sections present more detailed information on the NNSA and EM segments summarized in the overall rating.
Acquisition and Program Management for the National Nuclear Security Administration (NNSA)

Leadership commitment: met. NNSA leadership developed initiatives to improve acquisition and program management. For example, in September 2022, NNSA made numerous recommendations to more efficiently modernize the nuclear security enterprise and to improve federal and contractor workforce recruitment and retention through its Enhanced Mission Delivery Initiative (EMDI). In October 2024, NNSA issued its Enterprise Blueprint plan, which aims to improve the delivery of mission-critical infrastructure over the next 25 years.
NNSA is exploring alternatives to address its acquisition challenges, such as by (1) developing a plan to use a series of lease-purchase agreements to acquire additional production space at its Kansas City National Security Campus and (2) creating new leadership positions for mission critical programs. Designating a focal point to comprehensively communicate NNSA’s numerous efforts to improve management and operations will demonstrate continued leadership commitment.
Capacity: partially met. NNSA and its contractors have taken some steps to address challenges in recruiting and retaining staff. For example, NNSA has increased recruiting and outreach events and offered incentive payments to recruit and retain staff. Further, NNSA contractors have taken steps to address recruiting and retention challenges and have generally met planned staffing levels in recent years. However, NNSA’s federal workforce continues to be understaffed. NNSA has developed a new workforce planning process that officials said would enable the agency to make a stronger case for its workforce needs in future budget justifications.
NNSA has taken several steps to improve its capacity to manage construction projects. For example, NNSA implemented a new tool to provide more transparency about its budgetary priorities when resources are scarce, as we recommended. NNSA also released an Enterprise Blueprint that addresses, among other things, balancing investments across priorities. In addition, NNSA issued a directive to streamline its project management requirements for lower-cost construction projects. However, cost overruns and schedule delays on larger construction projects continue to put budgetary pressure on NNSA’s resources and its ability to address new priorities.
Action plan: partially met. NNSA has developed separate plans and initiatives, rather than an overall action plan, to address management challenges. For example, NNSA’s Enhanced Mission Delivery Initiative report made a variety of recommendations to reform certain acquisition and program management practices. However, other efforts relevant to improving performance in this high-risk area, such as developing risk registers and involving third party experts for project requirements planning, are not captured through an overall action plan. Synthesizing these various efforts to demonstrate how they connect to high-risk improvement would enable NNSA to improve its planning efforts.
We also recommended that NNSA revise its process for reviewing lessons learned from prior acquisitions—such as those that have resulted in solicitation cancellations or contract terminations—to avoid past mistakes and improve acquisition planning. Similarly, DOE’s Insider Threat Program should track actions responding to long-standing findings from independent reviewers, as we recommended.
Monitoring: partially met. NNSA has made efforts to better monitor project performance. For example, in April 2024, NNSA implemented a new executive dashboard to monitor construction projects with forward-looking metrics on project cost and schedule performance. NNSA has also taken steps to improve cost estimates related to project design for construction projects. Such steps may help NNSA better monitor contractor performance of design activities and develop new tools and processes for identifying and mitigating risk.
However, NNSA needs to further strengthen its monitoring of workforce issues and project and program performance. For example, NNSA has not implemented sufficient metrics to determine whether its Enhanced Mission Delivery Initiative reforms will achieve intended results. In addition, NNSA's efforts to recruit and retain staff could be hampered because it has not (1) established a continuing process to systematically analyze and share information about recruitment and retention challenges to inform its actions nor (2) regularly assessed the outcomes of its actions to determine if they have addressed recruitment and retention challenges.
Additionally, NNSA’s Production Modernization programs do not yet have sufficient schedules and cost estimates to ensure the effective integration of programs and their associated construction projects.
Demonstrated progress: partially met. NNSA has limited estimated cost growth associated with its two nuclear weapon acquisition programs in the production phase. In addition, most of the small construction projects NNSA funded between fiscal years 2019 to 2023 met or were expected to meet their cost targets at completion. Further, NNSA has committed to improving cost and schedule information related to the modernization of its capability to produce plutonium pits (a key component of a nuclear weapon), as we recommended.
However, NNSA’s larger construction projects have not been as cost-effective. Specifically, as of March 2023, NNSA’s portfolio of 18 major construction projects ($100 million or more) had a combined cost overrun of at least $2.1 billion and schedule delays of about 10 years. Most of these overruns were associated with the Uranium Processing Facility project, whose costs have since increased (see fig. 36).

Note: The Main Process Building project plans to construct a nuclear facility to house processes for casting enriched uranium into various shapes and producing special uranium oxides. This project is part of the overall Uranium Process Facility project that intends to construct and equip four new facilities to meet the enriched uranium needs for the nation's nuclear weapons stockpile and the U.S. Navy.
Acquisition and Program Management for the Office of Environmental Management (EM)
Leadership commitment: met. EM’s leadership has continued to demonstrate its commitment to improving oversight of its acquisitions and better managing its portfolios, programs, and projects. For example, EM developed its 2020 Program Management Protocol to update its waste clean-up policy and reflect leading practices for program management. This protocol requires cleanup sites to analyze the root causes of cost and schedule overruns and to get approval from EM leadership for revised cost and schedule estimates. EM has begun a two-phase review of the protocol’s implementation that it hopes to complete by August 2025, but EM officials said that may take additional time (see fig. 37).
Figure 37: Office of Environmental Management's Progress in Completing its Review of the Program Management Protocol Implementation at 15 Cleanup Sites, as of April 2024
Progress in this high-risk area will depend on ensuring stability in key leadership positions and continued focus on initiatives that result in positive outcomes. Since our last update, one of EM’s longest serving agency heads left the agency, and there has been significant turnover at the site leadership level.
Capacity: partially met. EM has taken some steps to implement leading practices for effective strategic workforce planning and to assess its acquisition workforce. For example, EM made some progress in filling vacancies through a hiring surge in fiscal year 2023 when it hired 320 new staff.
However, EM continues to face staffing shortages. For example, EM is understaffed compared to its identified workforce needs, particularly in mission-critical positions such as nuclear safety specialists and electrical engineers. It has also struggled to hire and retain staff at several EM sites, including the Los Alamos site in New Mexico and Savannah River site in South Carolina. Further, 44 percent of EM’s staff will be eligible to retire by 2030, yet EM does not have a forward-looking workforce plan to prepare for and manage current and future workforce needs. Congress should consider implementing an annual reporting requirement to help ensure EM prioritizes workforce management and addresses recurring workforce problems.
Action plan: increased to met. EM has taken significant action in recent years to develop corrective action plans that address root causes of issues. For example, EM’s 2020 Program Management Protocol requires sites to conduct root cause analyses to identify the underlying causes of events that result in undesirable cost and schedule performance outcomes when changes to cost or schedule estimates exceed a certain threshold. These undesirable outcomes include cost overruns, schedule delays, missed or postponed milestones, and performance shortcomings. In 2023, DOE added a requirement to its Order 413.3B—which governs capital asset project management—to help ensure that certain projects experiencing issues develop corrective action plans and that DOE assesses the effectiveness of corrective action plans in resolving root causes.
EM said it would work to improve a site’s root cause analysis as we recommended. It said EM would work to ensure that the analysis is accompanied by a corrective action plan, and corrective actions are tracked through completion and resolve the root causes of issues. These steps will help EM better manage projects to avoid cost or schedule increases.
Monitoring: increased to met. EM’s recent implementation of the 2020 Program Management Protocol has provided sites with additional tools to more effectively monitor and control program risk. For example, EM is updating its site-specific life-cycle cost and schedule estimates so they can be used by government officials as baselines to monitor work progress at a particular site.
EM has also updated its standard operating procedures to improve its use of available tools to monitor and ensure the effectiveness of corrective actions. In particular, EM is revising its guidance and procedures in a manner that is expected to facilitate the agency better analyzing federal management’s performance, oversight, and role when conducting root cause analyses of issues that arise on certain cleanup projects. In the past, we found that EM did not always acknowledge its own role in issues that arise on cleanup projects. For example, EM hired an inexperienced contractor that provided insufficient subcontractor oversight resulting in cost overruns and schedule delays at the Waste Isolation Pilot Plant in New Mexico. However, EM’s root cause analysis did not acknowledge that it hired the inexperienced contractor and failed to ensure that the contractor had sufficient support.
EM’s anticipated revisions to its standard operating procedures should help the agency address this issue and help ensure the use of existing institutional tools to help prevent project management challenges. As a result, we have increased the rating for the monitoring criterion to met.
Demonstrated progress: partially met. EM has recently made decisions that could save the government billions of dollars. In 2024, DOE, the Environmental Protection Agency (EPA), and the state of Washington proposed an agreement under which DOE would treat a portion of tank waste at the Hanford Site using options included in our recommendation in 2021. We estimate that this approach will save about $7.5 billion if DOE moves forward as planned under a finalized agreement with Hanford regulators.
In April 2024, DOE also stated it does not plan to resume construction of a pretreatment facility at Hanford that has faced significant technical issues and has been paused since 2012, following our 2013 recommendation to halt construction. EM plans to keep the facility in standby until at least 2029 while it evaluates pretreatment options.
Further, in March 2023, EM developed a strategy and conducted a review of opportunities to balance cleanup costs with human health and environmental risks. This review included the decision to accelerate the cleanup of certain nuclear waste at EM’s Savannah River Site in South Carolina—steps which are now underway. As a result, EM estimated it would complete some cleanup activities 22 years earlier than planned and avoid several billion dollars in costs. These examples are noteworthy successes in EM’s acquisition and program management approach—and reflect an increasing commitment to risk-informed decision-making.
EM has taken important steps toward resolving the persistent acquisition and program management challenges that placed it on the High-Risk List. While it will take several years to fully resolve the challenges to capacity issues we identified above, we recognize the significant progress that EM has made in recent years to initiate and sustain those efforts. Once these efforts are completed, it will have demonstrated enough progress such that we may be able to remove EM from the High-Risk List.
What Remains to Be Done
Attention is needed to improve workforce planning, project planning and management, and monitoring construction projects’ cost overruns and schedule to make progress on this high-risk area. Specifically, 179 of our recommendations related to this high-risk area remain open as of January 2025. They include
· developing a life cycle cost estimate for establishing NNSA’s pit production capability that aligns with cost estimating best practices.
· ensuring that schedule and cost estimating requirements for NNSA’s production modernization program incorporate best practices.
· revising EM's workforce planning to be forward-looking, clearly document human capital performance targets and measures, and include comprehensive succession plans.
Congressional Actions Needed
We have six matters for congressional consideration related to this high-risk area that are unaddressed. For example, Congress should consider
· implementing an annual reporting requirement to help ensure EM prioritizes workforce management and addresses recurring workforce problems. Such a requirement could include annual reporting on EM's efforts to implement recommendations and strategies, or additional direction on how EM and DOE should address workforce problems that numerous reports have identified.
· clarifying—in a manner that does not impair the regulatory authorities of EPA and any state—DOE’s authority to determine, in consultation with the Nuclear Regulatory Commission, whether portions of the tank waste at the Hanford site can be managed as a waste type other than high-level radioactive waste.
Benefits
Progress in this high-risk area has led to about $36 billion in financial benefits and more than 150 other benefits since this area was added to the High-Risk List in 1990. For example
· In April 2024, DOE announced a proposed agreement with the EPA and the Washington State Department of Ecology under which DOE would treat a portion of the low activity waste at Hanford with grout instead of glass. In December 2021 we recommended that DOE analyze additional disposal options for this waste, including identifying facilities that could receive grouted low-activity waste from Hanford. We estimate that grouting this waste instead of treating it with glass will save approximately $7.5 billion if DOE moves forward as planned under a finalized agreement with Hanford regulators.
· In April 2024, EM stated that it does not plan to resume construction of its $12 billion Pretreatment Facility at the Hanford Site. We have previously reported that DOE faces significant technical issues at this facility and recommended pausing construction until these issues are resolved. EM plans to keep the facility on standby until at least 2029—saving $6 billion over 5 years—while evaluating pretreatment options.
· NNSA finalized a tool to inform tradeoff decisions between various modernization programs to manage the affordability of its portfolio of weapon’s modernization programs.
Contact Information
For additional information about this high-risk area, contact Allison Bawden or Nathan Anderson, Directors, Natural Resources and Environment, at (202) 512-3841 or BawdenA@gao.gov or AndersonN@gao.gov.
DOD Financial Management
The Department of Defense (DOD) spends over $1 trillion annually to provide the military forces needed to deter war and to protect the security of the United States. However, DOD faces long-standing internal control weaknesses and should continue strengthening its information systems, action plans, and monitoring efforts to efficiently manage its financial resources. Addressing control weaknesses will result in the financial management operations and controls required to produce reliable, useful, and timely financial information and prevent and detect improper payments and fraud.
Why Area Is High Risk
DOD’s financial management is hampered by ineffective processes, aging systems, and inadequate controls; incomplete corrective action plans; and insufficient monitoring and reporting. Further, DOD has not taken effective steps to manage its interrelated fraud risks, including developing and implementing a robust fraud risk management program.
DOD financial management has been on our High-Risk List since 1995. DOD’s spending makes up almost half of the federal government’s discretionary spending, and its physical assets make up about 82 percent of the federal government’s total physical assets. While DOD continues to take positive steps, it has not yet received an audit opinion on its annual department-wide financial statements because it has been unable to accurately account for and report on its spending or physical assets. For example, DOD needs better accountability for global spare parts to manage the Joint Strike Fighter Program and must address the Government Furnished Property material weakness. However, one positive step was that the Marine Corps received a clean audit opinion on its fiscal year 2023 financial statements, the first military service to ever do so.
Area Rating
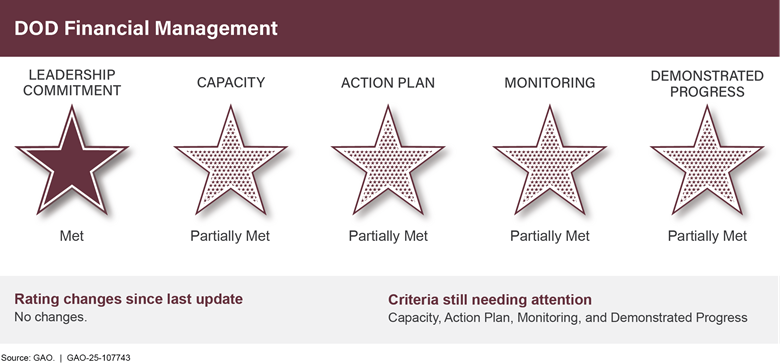
The ratings for all five criteria remain unchanged since 2023. In this update, we are expanding this high-risk area to include DOD fraud risk management. Because we do not rate issues when they are first added to the list, the overall ratings for this area do not reflect this addition.
Ineffective fraud risk management compromises the financial integrity of DOD's programs and trillion-dollar annual expenditures. For example, in 2018, DOD reported to Congress that from fiscal years 2013 through 2017, it had recovered more than $6.6 billion from adjudicated defense contracting fraud cases. For fiscal years 2017 through 2024, DOD reported about $10.8 billion in confirmed fraud via PaymentAccuracy.gov. Recoveries and confirmed fraud reflect only a small fraction of DOD’s potential fraud exposure. Without robust fraud risk management capacity, DOD cannot estimate the extent of fraud in its programs. The lack of a robust fraud risk management program, in addition to 28 agency-wide material weaknesses identified by the DOD Office of Inspector General (OIG), compounds DOD’s failure to establish a strong financial management internal control environment and increases opportunities for fraudulent actions against DOD’s vast resources.
Leadership commitment: met. Since our last update, DOD leadership continued its commitment to financial management improvements by (1) adhering to the agency’s Financial Management Strategy; (2) prioritizing audit remediation efforts; (3) continuing to phase out legacy systems while migrating to newer financial management systems; and (4) conducting governance meetings with senior leadership and working groups to report on audit progress, identify risks and roadblocks, and develop solutions to financial management and audit issues. DOD used advanced tools such as Advanced Data Analytics (Advana), a data analytics platform, to provide leadership with real-time remediation progress.
While DOD leadership has demonstrated a commitment to improving its financial management, it has not yet demonstrated the same level of commitment to managing fraud risk. Although DOD officials stated that they did not believe there was much fraud within the department relative to its overall spending, even a small percentage of DOD’s $1 trillion annual spending lost to fraudsters is significant.
DOD officials also noted that DOD OIG had not indicated fraud as a problem. The Payment Integrity Information Act of 2019 requires the Office of Management and Budget (OMB) to maintain guidelines for agencies, not OIGs, to establish financial and administrative controls to identify and assess fraud risks and incorporate leading practices from our Fraud Risk Framework. OMB Circular A-123, Management’s Responsibility for Enterprise Risk Management and Internal Control, implements this requirement. Given the significant fraud exposure and requirements for managing fraud risk, DOD leadership should give equal consideration to enhancing the department’s fraud risk management efforts throughout its many programs and operations as it does to financial auditability.
Specifically, DOD should determine and document the fraud risk management roles and responsibilities of all oversight officials and the chain of accountability for implementing an effective fraud risk management strategy, as we recommended. Further, DOD should assure that the designated entity for fraud risk management has the necessary authority—not just responsibility—to design and oversee fraud risk management activities, such as data analytics, as we recommended. Until DOD has a comprehensive antifraud strategy in place that effectively aligns with leading practices, assures effective implementation across the department, and balances both financial auditability and fraud risk management, it remains at substantial risk of fraud against its programs.
Capacity: partially met. DOD’s fiscal year 2022–2026 Financial Management Strategy focuses on building and maintaining a premier financial management workforce. The strategy also emphasizes the need to reduce the number of legacy financial management systems and leverage a single enterprise data and analytics platform to assist with fiscally informed decisions and management reporting.
However, we have identified several challenges that adversely affect DOD’s financial management workforce and its efforts to modernize its financial systems. For instance, DOD lacks data on the number and collective functions contractors are performing, and lacks policies and procedures on succession planning. This creates challenges in determining workforce needs and being able to quickly fill gaps. Also, while DOD has taken steps to improve its financial management systems workforce, it lacks a strategic approach to filling workforce gaps.
Additionally, in September 2020, we reported that DOD’s IT strategic plan lacked performance measures for tracking progress in achieving the strategy’s goals. Further, DOD could not identify a complete list of its financial management systems that support the preparation of DOD’s financial statements. DOD has not yet fully addressed these issues. Also, in February 2022, we reported that the Air Force did not have a systems migration plan that followed leading practices for transitioning from its legacy system to its new core accounting system; our recommendations from this work are still open.
In June 2024, we reported that the Marine Corps moved away from its legacy systems and to the Defense Agencies Initiative (DAI), which enables the Marine Corps to strengthen its monitoring of internal controls. The Marine Corps used the DAI program’s established procedures to guide its system migration efforts, but these procedures did not fully incorporate leading practices for data migration and conversion or change management.
DOD has taken some steps to address its fraud risk management challenges, such as filling vacancies on its Fraud Reduction Task Force and establishing a Confirmed Fraud Working Group. However, DOD should also take further and timely action to address fraud risk management capacity deficiencies, including updating its policies and implementing robust data analytics. We recommended DOD determine the roles and responsibilities of all oversight officials and document the chain of accountability in its fraud risk management approach to ensure effective implementation and consistent understanding. In addition, we recommended DOD fully establish its fraud-related data analytics processes to better understand the totality of its fraud risk exposure and implement controls to readily prevent and detect fraud. In September and December 2024, DOD officials told us it continues to update its fraud risk management strategy and related policies in response to these recommendations. We continue to monitor DOD's progress on this recommendation.
Action plan: partially met. DOD and its components continue to prioritize audit remediation efforts and develop corrective action plans to address findings from its external auditors report. To this end, the Secretary of Defense has targeted four priority areas in fiscal year 2024 to improve financial statement audit results: (1) establishing processes and controls to more timely record cash collections and disbursements, (2) enhancing security of critical IT systems, (3) compiling and validating transactions from all accounting systems, and (4) developing alternatives to valuing assets.
However, in the recently completed fiscal year 2024 financial statement audits, material weaknesses remain for three of these four priority areas. Additionally, DOD has not yet fully addressed key deficiencies we reported in October 2020 pertaining to its corrective action plan process, such as ensuring it performs and documents a root cause analysis.
DOD has also not yet issued detailed implementation plans to carry out the financial management transformation strategies included in its fiscal years 2022–2026 Financial Management Strategy. Also, DOD should develop and document a comprehensive strategy, separate from the financial management strategy, to clearly articulate the detailed DOD-wide efforts to address the Government-Furnished Property material weakness, as we recommended. This comprehensive strategy should document (1) steps to identify and address root causes of deficiencies, (2) an overall planned remediation date with specific interim target dates, and (3) steps to reassess actions after significant target dates so that plans can be adjusted as needed.
DOD has taken initial steps to manage its fraud risks. However, it still must finalize and implement these steps in a timely, strategic fashion. DOD’s fraud risk assessment and management processes should be improved as we recommended, such as planning and conducting regular fraud risk assessments and establishing data analytics as a method for preventing, detecting, and responding to fraud. While DOD has taken some steps to improve its fraud risk assessment guidance and reviewed a wider range of fraud risks, it has not fully ensured that its fraud risk assessments and fraud risk management activities align with leading practices.
Monitoring: partially met. DOD continues to prioritize financial statement audit remediation areas for addressing material weaknesses. In addition, DOD components have developed roadmaps for how they can achieve clean audit opinions. These roadmaps are intended to align material weaknesses, identify timelines, prioritize focus areas, and ensure progress is monitored, and can serve as a way for DOD leadership to monitor the agency’s audit remediation progress. However, we found that these roadmaps do not have sufficient details, such as interim milestone activities and dates to track progress, that are important for achieving a clean audit opinion, and that DOD has faced challenges meeting target remediation dates it had previously established.
We also noted that DOD is using the enterprise data platform Advana to enhance financial data by linking nonfinancial data sources. Through Advana, data are managed centrally and are available for multiple purposes. DOD uses the platform to monitor the progress of corrective action plans and audit remediation efforts in real time, and to visualize data, track the status of corrective actions, and identify areas needing attention.
Demonstrated progress: partially met. DOD continues to make some progress in addressing its financial management challenges. For example, the Marine Corps’ financial audit for fiscal year 2023 resulted in an unmodified opinion (albeit after a 2-year audit cycle), the first clean opinion of a financial statement audit for any military service. Nine other reporting entities also obtained unmodified opinions in fiscal year 2024–including the U.S. Army Corps of Engineers and the Defense Health Agency - Contract Resource Management, which have maintained clean audit opinions for several years. Additionally, in fiscal year 2024, six component-level material weaknesses were downgraded or closed across the military services.
However, the DOD Office of Inspector General reported 28 department-wide material weaknesses in its fiscal year 2024 DOD consolidated audit—the same number reported in the 2023 audit—due to the issuance of newly identified or resolved material weaknesses. DOD has remediated audit deficiencies at a slower rate in recent years as it works to address more complex issues, such as weaknesses in its financial management systems. To achieve a department-wide audit opinion by December 2028, DOD needs to accelerate the pace in which it addresses its long-standing issues.
What Remains to Be Done
We have made over 200 recommendations to DOD focused on financial management, about 100 of which remain open as of January 2025. Additional progress could be made if DOD were to implement open recommendations related to strengthening its information systems, action plans, and monitoring efforts, and improving its fraud risk assessment and management processes. For example, DOD should
· establish specific time frames for developing an enterprise roadmap to implement DOD's financial management systems strategy, continuing efforts to identify a complete inventory of financial management systems, and developing detailed system migration plans where new systems will replace legacy accounting systems;
· improve its corrective action plan review process, including ensuring that (1) data elements missing from corrective action plans are appropriately identified and communicated to DOD’s components and resolved; (2) auditors’ Notices of Findings and Recommendations are appropriately linked to the relevant corrective action plans to address them; and (3) components document their rationale for accepting the risk associated with certain deficiencies and identify such instances in the Notice of Findings and Recommendations Database;
· collaborate with the Navy, Air Force, and Army to develop and document a DOD-wide comprehensive plan that includes a clear vision for how to achieve a clean audit opinion, and complete, detailed procedures for addressing material weaknesses, with interim milestone activities and dates;
· coordinate with DOD components to develop guidance for assessing the capability of current contractor personnel in financial management, and using that assessment to help identify financial management workforce needs and develop written procedures for succession planning;
· revise DOD's Fraud Risk Management Strategy to establish data analytics as a robust method for preventing, detecting, and responding to fraud, and document which entity has the necessary authority to ensure that fraud-related data-analytics activities are planned and implemented;
· plan and conduct regular fraud risk assessments that align with leading practices in GAO’s Fraud Risk Framework as part of the annual statement of assurance process and include all fraud risks;
· collaborate to obtain and analyze relevant information from adjudicated procurement fraud cases to better understand fraud risks facing DOD;
· continue to take steps to mitigate the DOD-wide Government-Furnished Property (GFP) material weakness, including developing a comprehensive strategy that clearly articulates detailed DOD-wide efforts to better position DOD to develop effective and efficient action plans and achievable corrective action dates; and
· continue to take steps to address the DOD-wide F-35 program material weakness, including (1) ensuring that it appropriately categorizes all spare parts in the global spares pool, reviewing all applicable guidance and policies to ensure clarity regarding when an asset is considered GFP, (2) developing and documenting a process for contractors to report government-owned global spares pool losses, and (3) developing and documenting procedures to ensure that disposition instructions are provided consistent with federal regulations.
Benefits
Since this high-risk area was added in 1995, our work has identified about $9.2 billion in financial benefits to the federal government. We have also identified more than 250 other benefits, including enhanced internal controls, improved oversight, and more reliable information to support management decision-making related to this high-risk area. See figure 38 for examples of financial and operational benefits as a result of DOD Financial Statement Audits.
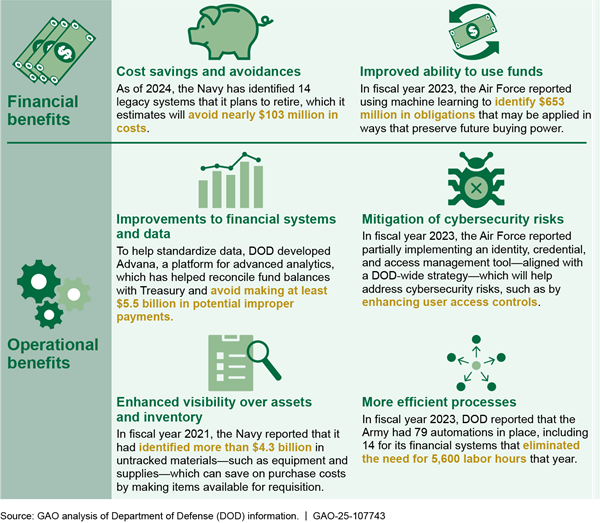
In addition to the examples of benefits noted in the figure above, other improvements stemming from DOD’s financial statement audits include:
· the Defense Finance and Accounting Service eliminated 10 legacy data systems in fiscal years 2021 and 2022, resulting in more than $10 million in savings.
· the Defense Logistics Agency has begun implementing a new warehouse management system that is anticipated to save the agency approximately $12 million per year, beginning in 2026.
· the Navy conducted a complete physical inventory of materials during fiscal years 2019 through 2021; items identified were used to fill more than 12,000 requisitions, totaling nearly $50 million in materials.
Contact Information
For additional information about this high-risk area, contact Asif A. Khan, Director, Financial Management and Assurance, at (202) 512-9869 or KhanA@gao.gov. For questions about our fraud risk management work, contact Seto Bagdoyan, Director, Forensic Audits & Investigative Service, at (202) 512-6722 or BagdoyanS@gao.gov.
Enforcement of Tax Laws
The Internal Revenue Service (IRS) needs to increase its capacity to implement new initiatives, improve ongoing enforcement and taxpayer service programs, and combat identity theft (IDT) refund fraud.
Why Area Is High Risk
This high-risk area comprises two segments representing pressing challenges for IRS: addressing the tax gap and combatting IDT refund fraud. In 2024, IRS projected that the gross tax gap—the difference between taxes owed and taxes paid on time—was $696 billion for tax year 2022. IRS estimated that through late payments and enforcement actions it will collect an additional $90 billion, leaving IRS with an estimated $606 billion net tax gap.
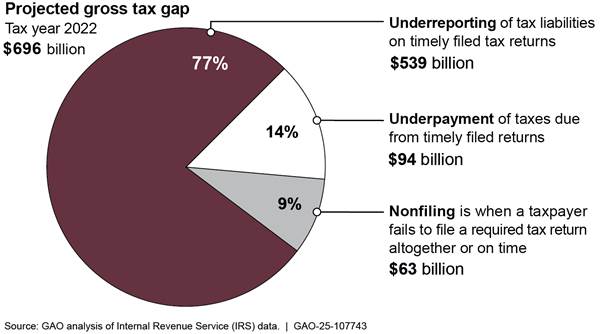
IDT refund fraud occurs when an identity thief files a fraudulent tax return using a legitimate taxpayer’s identifying information and claims a refund. In December 2023, IRS estimated that it prevented the theft of about $15 billion in individual IDT refunds for 2022. However, IRS has a backlog of cases and it is taking over 600 days to resolve identity theft cases.
Overall Area Rating
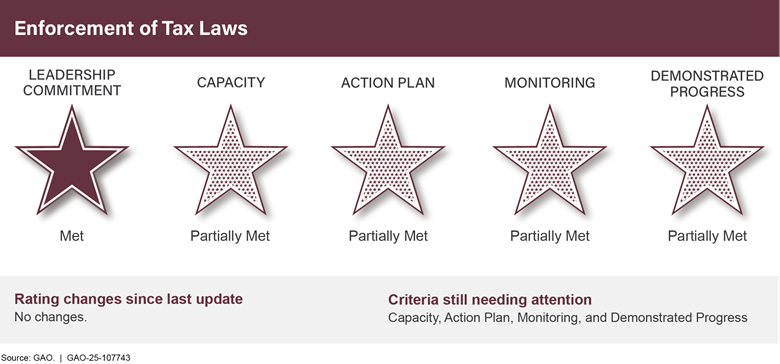
Overall ratings for all five criteria remain unchanged since 2023. The following sections present more detailed information on the two segments summarized in the overall rating, which also remain unchanged since the last update.
Addressing the Tax Gap

Leadership commitment: met. IRS continues to demonstrate strong leadership commitment to estimating and addressing the tax gap. For example, in 2023 IRS began publishing tax gap projections to address the need for more current estimates. IRS continued to update those projections in 2024.
Enacted in August 2022, the Inflation Reduction Act of 2022 (IRA) provided IRS with tens of billions in additional funding over the next decade.[58] According to IRS, these resources will, among other things, help to ensure the fairness of the tax system by addressing the tax gap. However, it is too early to determine if the additional funding has affected the tax gap as it did not become available until fiscal year 2023. It will be years before IRS knows how the funding may have affected the tax gap because of how long it takes IRS to estimate tax compliance based on completed tax return audits.
In September 2022, the Congressional Budget Office estimated that the IRA funding to IRS will result in over $180 billion of additional revenue between fiscal years 2022 and 2031.[59] In February 2024, using a different methodology, IRS estimated that the IRA funding will result in $390 billion to $851 billion of additional revenue between fiscal years 2024 and 2034.[60]
In its April 2023 IRA Strategic Operating Plan, IRS outlined its plans for spending IRA funds. The plan describes a high-level vision for the future of federal tax administration and identifies specific initiatives and projects linked to five objectives (see fig. 40). The plan also noted that implementation will be coordinated by the newly formed Transformation and Strategy Office. In April 2024, IRS released an annual update to the plan containing priorities for fiscal years 2024 and 2025.
Figure 40: Overall Operating Environment and Summary of the Internal Revenue Service’s Transformation Objectives
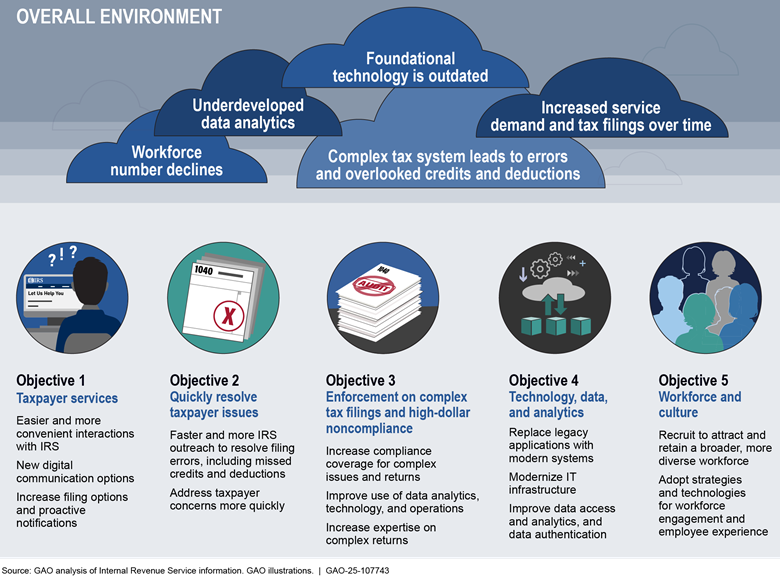
Capacity: not met. IRS continues to face challenges in meeting its objectives, such as with staffing shortages, especially for some key enforcement areas. For example, as we reported in January 2024, IRS officials noted that they have lost a significant number of staff who could audit high-income, high-wealth returns. Officials explained that it takes a minimum of 3 years of on-the-job training to develop the expertise to effectively audit the highest income returns, which can help address the tax gap. As we have recommended, IRS should develop and implement a strategy for hiring and training staff to meet this need.
Additionally, large partnerships continue to grow in number and complexity while the audit rate for large partnerships declined between 2007 and 2019.[61] IRS officials attributed the declining audit rate to resource constraints during that time period. IRS should identify and implement measures for tracking progress toward agency objectives related to large, complex partnerships.
Action plan: partially met. IRS’s plan outlines the areas where it intends to focus its efforts to reduce the tax gap. For example, IRS plans to expand enforcement efforts on taxpayers with complex tax filings and high-dollar noncompliance, where historical audit rates were low.
However, IRS has not demonstrated that it is following relevant leading agency reform practices, such as establishing outcomes and performance measures.
Continuing to implement our open recommendations—particularly those that the agency previously said it lacked resources to implement—would help IRS to prioritize IRA funding. For example, IRS previously did not approve a funding proposal to implement an online signature personal identification number application for business-related returns due to competing IRS priorities, among other things. In November 2024, IRS officials stated they still intend to develop the online application but have not moved forward with it.
In addition, IRS needs to complete planning and improve reporting for its technology, data, and analytics objective, which underpins IRS’s ability to effectively collect taxes, process returns, and secure sensitive taxpayer information. Further, IRS should clearly state agency-wide and business unit performance goals for improvements in the taxpayer experience and specify its related measures with targets.
Monitoring: partially met. IRS continues to use tax gap data to study compliance behaviors and update methods to identify tax returns with a high likelihood of noncompliance. For example, in October 2024, IRS released tax gap projections for tax year 2022 and revised previous projections due to updates in estimation methodologies. However, IRS could strengthen its efforts to assess sole proprietors’ noncompliance risks and improve related third-party information reporting. These efforts could help inform a broader strategy to reduce the tax gap, as sole proprietor noncompliance is the largest portion of the underreporting tax gap.
Demonstrated progress: partially met. IRS implemented some corrective measures to improve compliance with the law and reduce the tax gap. For example, IRS recently improved the systems used to collect information returns, including the 1099 series which helps IRS identify returns that are not complying with tax laws. IRS established new systems and milestones for modernizing its intake, processing, and use of information returns. However, IRS lacks specific quantitative goals to reduce the tax gap or improve voluntary compliance. This makes it more difficult to determine the success of its strategies.
Refund Fraud Related to Identify Theft
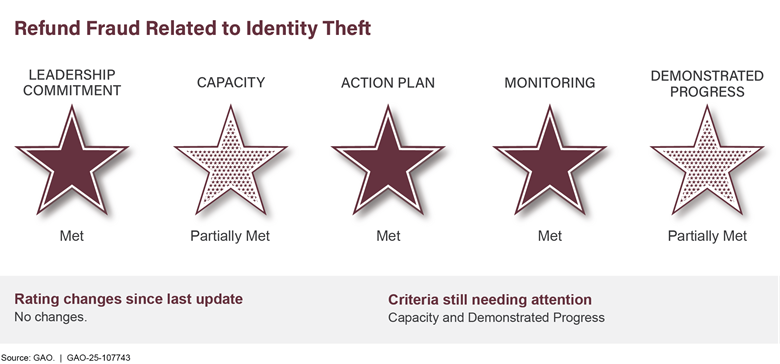
Leadership commitment: met. IRS continues to recognize the evolving challenge of IDT refund fraud in its strategic plans, expand fraud detection activities, and implement agency-wide antifraud efforts. Such efforts include bringing officials together from across the organization to discuss potential fraud risks and working with the private sector to protect taxpayers and the tax system against IDT refund fraud.
Capacity: partially met. IRS has developed a prerefund system, the Return Review Program, that can detect IDT fraud. However, to fully expand IDT refund fraud prevention, IRS needs to digitize information from paper returns at intake. This would allow IRS to reduce processing time, use the prerefund system’s fraud filters on all paper and electronic forms, and allow more prerefund compliance checks or investigations, among other benefits. IRS has begun efforts to scan and digitalize more paper tax returns that taxpayers mail during the annual filing season. As part of these and future planned efforts, IRS intends to capture data from paper-filed returns in a format that would be more useable by IRS’s fraud filters. During the 2024 filing season, IRS received about 11.5 million paper-filed business and individual tax returns.
Additionally, in November 2021, IRS set a new 120-day average time frame standard for processing individual and business IDT cases.[62] In 2024, IRS assisted tens of thousands of taxpayers who were victims of identity theft. However, extenuating circumstances from the COVID-19 pandemic, such as high case inventories, means that IRS faces challenges in resolving all identity theft cases within its time frame standard. As of July 2024, IRS data show that, on average, it is taking 640 days to resolve identity theft cases.
Action plan: met. IRS continues to acknowledge the agency’s responsibility to safeguard taxpayer and IRS data as part of its initiative to ensure data security. For example, in a 2024 update to its Strategic Operating Plan, IRS stated it is focused on advancing cybersecurity monitoring, cyber fraud analytics, and incident response capabilities to reduce risk. IRS also noted it is expanding efforts to protect taxpayers by preventing scams before they happen or identifying them when taxpayers file returns. It also recognizes that technological and security investments help ensure IRS is better positioned to safeguard taxpayer data and proactively combat IDT refund fraud.
Monitoring: met. IRS has improved its ability to monitor IDT fraud. For example, it improved its ability to track outcomes of taxpayer authentication conducted by phone or in person, such as rates and reasons why taxpayers may have difficulty authenticating their identity. IRS also established a policy and schedule to assess risks to phone, in-person, and correspondence authentication channels, which may help identify emerging risks to the tax environment. Additionally, IRS updated its monitoring reports and annual estimates of dollars protected and lost to fraud to include business IDT fraud.
Demonstrated progress: partially met. IRS has demonstrated some progress by developing tools and programs to further detect and prevent IDT refund fraud, such as the Return Review Program. IRS has also conducted business IDT fraud risk assessments to identify and address business tax forms that pose high fraud risk but lack effective controls. In December 2024, IRS estimated that such actions helped IRS protect about $3.3 billion in refunds from business IDT fraudsters in 2023.
However, IRS lacks the governance structure to coordinate all aspects of its efforts to protect taxpayer information held by third-party providers. It also lacks a lead entity with defined responsibilities and authority to oversee business IDT efforts. Establishing these additional oversight structures will help to ensure IRS is better positioned to stay abreast of the evolving threats over time and better protect taxpayer information.
What Remains to Be Done
As of January 2025, 194 recommendations related to the tax gap and IDT refund fraud remained open or partially implemented. Additional progress could be made if IRS were to implement open recommendations related to hiring and training audit staff, following leading agency reform practices, developing performance goals, and establishing oversight structures, among others. For example, IRS should fully implement open high-risk recommendations such as
· assessing IRS’s hiring and training needs for high income, high wealth auditing and developing a strategy to meet those needs;
· identifying and implementing measures for tracking progress toward agency objectives related to large, complex partnerships;
· demonstrating that IRS is following leading agency reform practices when implementing its Inflation Reduction Act Strategic Operating Plan’s objectives and initiatives;
· determining what actions IRS could take to address barriers related to e-filing of business-related returns;
· completing plans and improving reporting for its technology modernization programs;
· finalizing the Service-wide Return Preparer Strategy and identifying the resources needed to implement it;
· identifying agency-wide and business unit performance goals for improvements in the taxpayer experience;
· setting a target to reduce taxpayer burden through the development of new online services;
· coordinating with state revenue agencies to expand taxpayer access to Direct File and, as necessary, taking steps to ensure the availability of the federal Direct File program to eligible taxpayer in all states;
· assessing sole proprietors’ noncompliance risks, including defining objectives and risk tolerances;
· expanding third-party information reporting to improve sole proprietor compliance;
· re-establishing goals for improving voluntary compliance and developing and documenting a strategy for using data to update compliance strategies;
· implementing the most cost-effective method to digitize information provided by taxpayers who file returns on paper;
· expanding IRS’s system for detecting tax fraud, the Return Review Program, to support other enforcement activities;
· developing a centralized governance structure to coordinate all aspects of its efforts to protect taxpayer information;
· developing a lead entity with defined responsibilities and authority to oversee business identify theft efforts; and
· documenting the processes used to address certain compliance risks for COVID-19 employer tax credits and implement additional compliance activities to potentially recapture ineligible claims.
Congressional Actions Needed
While IRS actions are critical to improve compliance with tax laws, there are 28 matters for congressional consideration that are pivotal actions to effectively address the risks in this area. For example, to help IRS address this high-risk area, Congress should consider
· requiring the Secretary of the Treasury to ensure the tax gap strategy includes a segment on improving sole proprietor compliance that is coordinated with broader tax gap reduction efforts;
· expanding third-party information reporting for certain payments that rental real estate owners make to service providers, such as contractors who perform repairs on their rental properties;
· providing IRS with authority—with appropriate safeguards—to correct math errors and discrepancies between information from taxpayers and government databases;
· granting IRS the authority to establish professional requirements for paid tax return preparers;
· requiring that returns prepared electronically but filed on paper include a scannable code printed on the return to better leverage the Return Review Program’s capabilities; and
· providing IRS with explicit authority to establish certain additional security requirements.
Benefits
Progress in this area has led to more than $43.9 billion in financial benefits and more than 350 other benefits since it was designated as high risk in 1990. These benefits include improved research, systems, and delivery of benefits for qualified taxpayers. For example:
· Congress took action to advance the deadline for employers to file W-2s to January 31.[63] By improving its ability to conduct compliance checks before issuing refunds, IRS prevented more than $7 billion in invalid refunds from tax years 2017–2021 after implementing the new W-2 filing deadline.
· IRS began using employee counts from tax forms filed by employers to identify potentially ineligible claims for COVID-19 related sick and family leave credits, as we recommended in 2021. As of March 2024, IRS had assessed additional taxes of about $285.2 million. By using these data to inform compliance actions, IRS helped ensure that sick and family leave credits were claimed in accordance with statutory requirements.
· Congress addressed our recommendation to require more third-party reporting for payments made to online platform workers.[64] The increased reporting will improve tax compliance by providing IRS with better information about platform workers’ incomes and making it easier for certain taxpayers to complete tax returns.
Contact Information
For additional information about this high-risk area, contact James R. McTigue, Jr., or Jessica Lucas-Judy, Directors, Strategic Issues, at (202) 512-6806, McTigueJ@gao.gov, or LucasJudyJ@gao.gov.
Ensuring the Cybersecurity of the Nation
Federal agencies must accelerate the pace of strengthening cybersecurity by fully establishing and implementing a comprehensive national cyber strategy and oversight approach; strengthening protections for federal systems and information; working with the private sector and state, local, tribal, and territorial governments to secure critical infrastructure assets; and protecting privacy and sensitive data.
Why Area Is High Risk
Federal agencies and our nation’s critical infrastructures—such as energy, transportation systems, communications, and financial services—depend on technology systems to carry out operations and process, maintain, and report essential information. The security of these systems and data is vital to protecting individual privacy and ensuring national security, prosperity, and the well-being of Americans.
However, risks to technology systems are increasing. In particular, malicious actors are becoming more willing and capable of carrying out cyberattacks. Such attacks can result in serious harm to human safety, the environment, and the economy. Agencies and critical infrastructure owners and operators must protect the confidentiality, integrity, and availability of their systems and effectively respond to cyberattacks.
We designated information security as a government-wide high-risk area in 1997. We expanded this high-risk area in 2003 to include protecting the cybersecurity of critical infrastructure. In 2015, we expanded it again to include protecting the privacy of personally identifiable information. In June 2024, we identified urgent actions needed to address cybersecurity challenges facing the nation.
Area Rating

The five high-risk criteria ratings remain unchanged since 2023. Although federal agencies have made some improvements, continued issues challenge the federal government’s efforts to ensure the cybersecurity of the nation, including the urgent need for
· a fully established and implemented comprehensive cybersecurity strategy and plan;
· more concerted efforts to implement cybersecurity practices at executive branch agencies;
· more concentrated efforts to encourage the adoption of leading practices to combat ransomware attacks within critical infrastructure sectors; and
· improved efforts to ensure the security and privacy of sensitive data on U.S. residents collected and processed by federal agencies (e.g., taxpayer data).
The federal government is not yet acting with a sense of urgency commensurate with the grave and rapidly evolving threats.
Leadership commitment: met. In January 2021, Congress enacted the William M. (Mac) Thornberry National Defense Authorization Act for Fiscal Year 2021, which established, within the Executive Office of the President, the Office of the National Cyber Director to lead the nation's cybersecurity effort.[65] In December 2023, the Senate confirmed the second National Cyber Director. The presence of this leadership should help facilitate the high-level attention and coordination needed to address cyber threats and challenges facing the nation.
Capacity: partially met. Federal agencies have improved the management of their cybersecurity workforce. For example, 24 agencies have taken steps to identify and categorize all their vacant IT and cyber-related positions. However, federal agencies need to do more to address challenges faced by critical infrastructure entities in hiring, training, and retaining their cybersecurity and privacy workforces. For example:
· The Department of Commerce’s National Institute of Standards and Technology needs to better assess the performance of its National Initiative for Cybersecurity Education program. This partnership among industry, academia, and government is intended to help strengthen cybersecurity education, training, and workforce development.
· The Department of Defense needs to improve how it recruits, trains, and retains a knowledgeable and skilled cyber workforce. This includes tracking specific cyber-related work roles to identify potential staffing gaps.
· The Office of Personnel Management and National Science Foundation need to collect better data to improve the CyberCorps® Scholarship for Service Program. This scholarship program is aimed at students studying certain IT and cybersecurity fields at participating colleges and universities.
Action plan: partially met. In March 2023, the White House released the National Cybersecurity Strategy outlining five pillars and 27 underlying strategic objectives for managing cybersecurity. In July 2023, the White House issued the accompanying implementation plan that described 69 initiatives to achieve the strategy’s objectives.
However, in February 2024, we reported that the National Cybersecurity Strategy and Implementation Plan addressed some, but not all, of the desirable characteristics of a national strategy. Specifically, it did not include outcome-based performance measures to gauge progress in implementing the strategy and estimating costs of key initiatives. Fully establishing and implementing a national strategy to guide the federal government’s cybersecurity activities, including its coordination with the private sector, is a critical component needed to ensure the cybersecurity of the nation.
Monitoring: partially met. Federal agencies continue to monitor progress toward meeting cybersecurity-related targets for administration priorities and implementing effective cybersecurity programs. However, federal agencies need to better measure the performance of their cybersecurity and privacy programs and progress that critical infrastructure organizations are making to manage cyber risk. For example:
· The National Cyber Director needs to establish performance measures for initiatives to share cyber threat information.
· The Office of Management and Budget should improve measures of agencies’ information security programs to provide a more accurate picture of agencies’ information security performance.
Demonstrated progress: partially met. Although agencies have made some improvements, they need to urgently address the 10 critical actions associated with four major cybersecurity challenges that we have identified (see fig. 41).
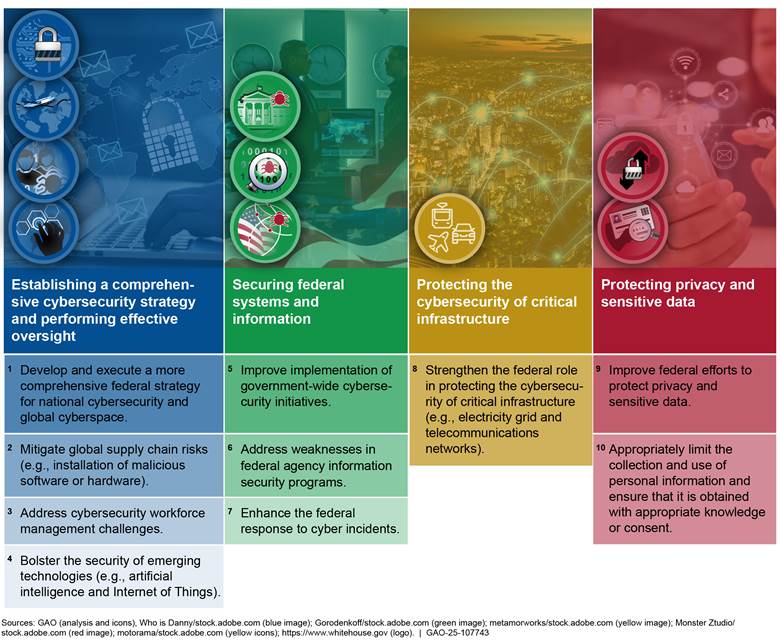
In particular, the federal government needs to
· ensure the responsible use of artificial intelligence and other emerging technologies for cybersecurity;
· mitigate global supply chain risks;
· fully implement incident response requirements;
· address risks to critical infrastructure sectors, such as water and wastewater systems; and
· strengthen programs for ensuring the privacy of sensitive personal information.
What Remains to Be Done
In addition to identifying the issues above, we have made numerous recommendations in this area. Since 2010, we have made 4,387 recommendations to address cybersecurity weaknesses. More than 277 of these recommendations were made since the last high-risk update. As of January 2025, 764 of these recommendations had not been fully implemented, including 56 of 170 priority recommendations, which we believe warrant priority attention from heads of key departments and agencies.
We have made recommendations to address the four cybersecurity challenges facing the nation and ways to improve the security of federal and critical infrastructure systems. For example, federal agencies need to
· fully establish and implement the National Cybersecurity Strategy;
· fully implement programs for responding to cybersecurity incidents;
· enhance oversight of ransomware practices and assess the effectiveness of federal support to critical infrastructure sectors designed to reduce ransomware risk; and
· address privacy requirements for law enforcement agencies’ use of facial recognition technologies.
Congressional Actions Needed
In addition, we recommend that Congress consider the following legislative matters related to protecting digital privacy:
· provide IRS with direct statutory authority to inspect receiving agencies' safeguards for taxpayer information shared under subsection 6103(c) of the Internal Revenue Code;
· require agencies to designate a senior privacy official—a position with the organizational placement necessary to coordinate with other agencies and the authority to ensure that privacy requirements are implemented—at agencies that currently lack such a position;
· provide the Federal Trade Commission with civil penalty authority to enforce the privacy and safeguarding provisions of the Gramm-Leach-Bliley Act to help ensure the agency can most effectively act against data privacy and security violations; and
· strengthen the consumer privacy framework to reflect the effects of changes in technology and the marketplace related to privacy controls and review consumers’ ability to access, correct, and control their personal information.
Benefits
Progress to address this high-risk issue has resulted in more than 4,000 benefits since it was added in 1997. For example:
· In 2023, we reported that four selected agencies had not implemented key practices for securing cloud-based computing resources.[66] Fully implementing the selected key practices will support agencies’ efforts to ensure the confidentiality, integrity, and availability of information in their cloud systems. In response, the selected agencies have implemented 17 of 35 recommendations to improve their cloud security practices.
· In 2022, we reported that 24 selected agencies had not fully implemented key elements of their privacy programs. Fully establishing such programs is critical to protecting personally identifiable information collected for government programs and processed by federal IT systems. In response, the selected agencies have implemented 26 of 62 recommendations to fully establish their privacy programs.
· In December 2021, we reported numerous deficiencies in the National Institutes of Health's cybersecurity program and controls that placed sensitive information at risk of unauthorized disclosure and modification. In response, the National Institutes of Health implemented 216 of 219 recommendations we previously made in a limited distribution report to strengthen its cybersecurity controls.
Contact Information
For additional information about this high-risk area, contact Marisol Cruz Cain, Director, Information Technology and Cybersecurity, at (202) 512-5017 or CruzCainM@gao.gov.
Improving and Modernizing Federal Disability Programs
Sustained attention and efforts are needed to ensure that federal disability programs provide accurate benefits in a timely manner, reflect current research about disability, and achieve positive employment outcomes.
Why Area Is High Risk
Three of the largest federal disability programs—managed by the Social Security Administration (SSA) and the Department of Veterans Affairs (VA)—paid about $360 billion in cash benefits through the programs in fiscal year 2023 to nearly 20 million individuals. However, SSA and VA struggle to manage their workloads and make timely decisions on benefit claims.
In addition, both agencies rely on outdated criteria to decide whether individuals qualify for benefits. They also experienced delays in their efforts to update these criteria. Beyond these benefit programs, we reported in June 2012 that the government has a patchwork of more than 40 employment support programs, which lack a unified vision, strategy, or set of goals to guide their outcomes.
Overall Area Rating
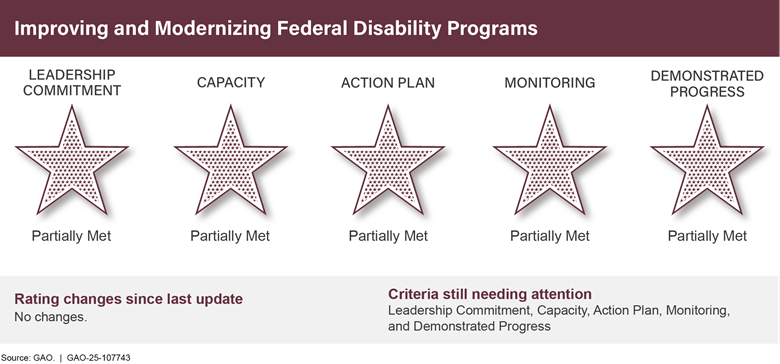
Overall ratings for all five criteria remain unchanged since 2023. However, ratings for the segments that comprise this high-risk area show mixed progress. One criterion increased for Updating Disability Benefit Eligibility Criteria (VA), but two criteria decreased for Updating Disability Benefit Eligibility Criteria (SSA) and one criterion decreased for Programs with Unified Strategies and Goals (Office of Management and Budget).
The following sections present more information on the five segments summarized in the overall rating.
Managing Disability Claims Workload (SSA)

Leadership commitment: met. SSA maintained its leadership focus on disability claims workloads. For example, SSA named improving average processing time for disability claims initially processed at local SSA field officials and state agencies as one of the top priorities in its fiscal year 2025 annual performance plan. Additionally, in February 2024, SSA launched a performance management program and tracking tool that allows leadership to view data in real time and adjust resources or strategies as needed.
Capacity: partially met. SSA has taken steps to increase staff and other resources available to process initial claims and decide appeals. For example, to facilitate quicker disability decisions, SSA updated its electronic decision support tool and provided more training to claims processors on how to use the tool.
However, SSA has experienced challenges achieving its desired number of staff for both initial claims and appeals. In fiscal year 2023, SSA increased its total staff by about 3,200 employees after receiving direct-hiring authority from the Office of Personnel Management for direct public service positions and increasing outreach to colleges and universities to identify candidates.
In contrast, SSA experienced a decrease of about 1,000 employees in fiscal year 2024 due to both attrition and limited hiring. In particular, SSA officials stated that the agency has experienced challenges hiring and retaining entry-level legal assistants to help process appeals, in part because of higher compensation offered by private sector employers and other federal agencies. Additionally, SSA funds the state agency staff who process initial claims, and SSA officials said SSA experienced setbacks in its efforts to help these agencies increase staffing levels due to SSA budget constraints that limited new hiring in fiscal year 2024.
Action plan: partially met. In our previous High-Risk List update, we reported that SSA lacked a detailed plan to address workload management challenges. We also recommended in November 2022 that SSA develop a plan for managing anticipated increases in disability workloads due to COVID-19-related illnesses and other factors. Over the past 2 years, SSA has strengthened its planning by identifying root causes of workload management challenges and developing corrective actions to address them. By collecting more than 5,000 recommendations from employees and other stakeholders, SSA identified communication, process, and technology issues affecting claims processors’ ability to perform efficiently and effectively. SSA developed an action plan with 27 high-level goals and related corrective actions to address these issues. However, SSA’s action plan lacks timelines for completing these actions as well as metrics for monitoring progress on achieving its goals.
Monitoring: partially met. SSA continues to monitor and report on its progress toward achieving goals for timely processing of initial disability claims and appeals. Additionally, SSA developed an online tool showing the agency’s progress on addressing some challenges, including some related to managing disability claims workloads. However, SSA lacks metrics for monitoring progress on all corrective actions within its action plan, such as its initiatives to improve employees’ experiences with workload management tools and career development opportunities intended to help decrease employee attrition. Without these, SSA will be unable to determine whether these actions are helping the agency achieve its goals.
Demonstrated progress: partially met. SSA has demonstrated mixed progress managing initial disability claims and appeals. SSA’s average processing time for initial disability claims increased by about 26 percent from 184 days in fiscal year 2022 to 231 days in fiscal year 2024. Accordingly, SSA’s pending initial claims increased from about 941,000 at the end of fiscal year 2022 to about 1.2 million claims at the end of fiscal year 2024. This growth continues an upward trend that started at the beginning of the COVID-19 pandemic and peaked in May 2024 (see fig. 42). In contrast, SSA’s inventory of pending appeals decreased from about 347,000 to 262,000 over the same period. However, without continued improvements to processing times, disability claimants will continue to face long wait times for SSA decisions on benefits that could be critical to their financial and physical well-being.
Figure 42. Social Security Administration Initial Disability Claims Processing, October 2018–September 2024
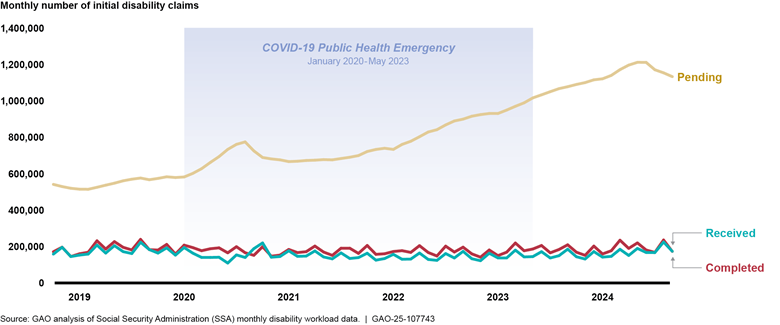
Managing Disability Claims Workload (VA)
Leadership commitment: met. VA leaders continued focusing on initiatives and reforms to improve processing of veterans’ claims for disability compensation. These efforts include reducing the department’s backlog of initial claims and appeals of claims decisions. For example, VA has continued to refine its action plan through changes in leadership and designated a team to coordinate its initiatives to address this high-risk area.
Capacity: partially met. VA has built capacity to meet the increasing number of veterans’ claims; however, it is unclear whether these efforts will be sustainable over the long term. VA data show that the increase in claims, driven partly by the Honoring our PACT Act of 2022 (PACT Act),[67] added to VA’s already considerable workload and contributed to a significant VA-projected budget shortfall, after which Congress appropriated additional funding.[68] VA has initiatives and reforms to help improve capacity for processing initial claims and appeals workloads, such as enhancing its ability to predict workloads, improving information technology (IT), and hiring and training thousands of staff.
However, it is too early to tell whether these efforts will improve VA’s long-term ability to manage its disability workloads. Further, VA should improve its training program for disability claims processors as we recommended, including documenting plans for incorporating stakeholder feedback to improve training.
Action plan: met. VA has continued enhancing its action plan to manage its workload, including refining metrics and milestones needed to track progress. For example, VA uses a metric to determine if it is achieving its staffing goal to address surges in disability workloads.
Monitoring: met. VA monitors and reports on the timeliness of initial claims and appeals, among other performance metrics, used to gauge progress toward managing workloads. This includes using monitoring tools, such as metric dashboards, to track progress on efforts in the action plan. For example, VA regularly reports on whether it is reducing various errors, including errors identified by the Board of Veterans’ Appeals, that are sent back (remanded) to the Veterans Benefits Administration for correction.
Demonstrated progress: partially met. VA has realized gains in deciding initial disability claims and appeals amid spikes in these workloads. For example, VA’s backlog improved from a high of over 600,000 in March 2013 to about 244,000 claims as of December 2024.
However, progress has been mixed for certain workloads. For PACT Act claims, average processing times and the percentage of claims not meeting established timeliness goals have climbed since last year, according to VA data.
· As of November 2024, average days to complete PACT Act claims reached about 168 days compared to about 155 days in August 2023. And 37 percent of claims completed the process within VA’s goal of 125 days, down from 47 percent in September 2023.
· In contrast, VA completed non-PACT Act claims in 129 days on average and 59 percent within VA’s 125-day timeliness goal, as of November 2024. For all initial claims, VA completed disability-related claims in about 139 days on average in November 2024.
For appeals, VA has also made progress in decreasing its inventory from nearly 475,000 6 years ago to about 200,000 as of 2024. However, the average number of days for VA to decide certain appeals in its modernized process has increased, according to VA data. For example, the average days to complete the hearing option at the Board of Veterans’ Appeals reached 1,089 days as of June 2024 compared to a goal of 730 days. VA also continues to contend with the inventory of about 42,000 appeals remaining in its legacy process.
In addition, VA’s processes to maintain the quality of claims decisions and appeals, predict resource needs, and implement new initiatives and reforms face ongoing challenges. Many challenges facing VA stem from its leaders not fully leveraging leading management practices to improve the disability compensation program. For example, VA leadership has not developed and implemented a policy that describes the leading reform practices that VA should follow to improve its planning and management of disability compensation program reforms, as we recommended.
Updating Disability Benefit Eligibility Criteria (SSA)

Leadership commitment: decreased to partially met. Since 2023, this rating decreased from met to partially met. SSA has efforts underway to update the medical and occupational criteria it uses to determine claims for disability benefits, such as replacing outdated job definitions that have not been revised in decades. While SSA includes these efforts in its annual performance plan, SSA leadership has not prioritized the rule and policy changes SSA says are needed to use updated occupational criteria. The agency withdrew its prior proposed rule for this effort in January 2021 before publishing a Notice of Proposed Rulemaking, and SSA now expects to submit a proposed rule for Office of Management and Budget (OMB) review in June 2025. SSA is unable to state when it expects to stop using outdated job definitions. Further, the agency has not submitted congressionally-requested annual reports to Congress about its progress updating occupational criteria since April 2022.
Capacity: decreased to partially met. Since 2023, this rating decreased from met to partially met. SSA has maintained consistent levels of staff tasked with (1) monitoring advances in medical diagnosis and treatment, and (2) developing proposed updates to medical criteria used in disability determinations. SSA has maintained its partnership with the Bureau of Labor Statistics (BLS) to collect updated occupational data. However, the lack of progress in making rule and policy changes has impacted SSA’s capacity to complete IT systems that will be needed to work with the new occupational criteria. According to SSA, all IT work related to this effort has been on hold since fiscal year 2022 pending the rule and policy changes.
The agencies are now considering cost-saving measures to the data collection effort that could include reducing sample sizes or refreshing data less frequently. SSA states that any changes to the survey will prioritize the preservation of data quality.
Action plan: partially met. SSA has plans for updating the medical criteria for diseases and disorders in each part of the body—known as the body systems—used when determining eligibility for disability benefits. For example, it has contracted for studies on emerging medical conditions that are of concern. According to SSA, the agency needs to implement rule and policy changes before it can use BLS data on occupational requirements for disability determinations. Further, the agency plans to develop an IT system which staff will use to access updated occupational criteria.
However, SSA does not have an action plan with goals, metrics, and timelines for updating its occupational criteria, nor does it have a target date for using the BLS data. SSA officials said the agency’s goal is to submit a proposed rule on its occupational criteria for OMB review in June 2025.
Monitoring: partially met. SSA’s process for monitoring medical advances, such as reviewing body system rules for potential updates on a 3-to 5-year cycle, helps it regularly update its medical criteria. However, the agency has limited ability to monitor its progress on developing occupational rules, policies, and IT development without a timeline or detailed plan for these efforts.
Demonstrated progress: partially met. SSA is revising its rule for the cardiovascular system and expects to finalize it in summer 2025. According to SSA, once that rule is complete, SSA will have revised all 15 of its body system rules since 2011—a substantial improvement since 2012, when we reported that some rules had not been updated in more than 25 years.
Following our testimony in June 2024 on challenges SSA faces in its disability programs, SSA announced policy changes that limit the use of certain outdated jobs in its disability determinations. Additionally, SSA published a ruling in December 2024 that makes it easier for vocational experts to cite more recent job definitions. However, SSA’s disability determination process generally continues to rely on job definitions that have not been updated in more than 30 years, making it more challenging for the agency to provide claimants with decisions that reflect jobs available in today’s economy.
Updating Disability Benefit Eligibility Criteria (VA)
Leadership commitment: met. VA maintained leadership focus on updating its eligibility criteria for disability compensation. VA uses the VA Schedule for Rating Disabilities criteria to assign a degree of disability for veterans with service-connected injuries or conditions. The degree of a veteran’s injury or condition is a basis for calculating a compensation level. The Veterans Benefits Administration and VA leadership meet monthly to review progress updating these criteria.
Capacity: partially met. VA has established a program office to oversee a comprehensive update of its disabilities rating criteria. Specifically, this office created a process for making routine improvements and updates to the criteria based on new medical information. It also developed a pilot program to test the feasibility for using data on the loss of job earnings associated with specific disabilities from studies conducted by VA. However, the procedures have not been fully tested and this effort is complex. Also, VA has not fully articulated the level of resources needed to incorporate information from the earnings loss studies into future VA Schedule for Rating Disabilities updates.
Action plan: met. VA continued to update its action plan that defines corrective actions for updating its disabilities rating criteria, including metrics and milestones to track and achieve its stated goals. For example, VA’s action plan describes its progress in establishing and maintaining sufficient staffing to update criteria on a continual basis.
Monitoring: increased to met. This rating increased from partially met to met. VA continued to use its project management plan to monitor and evaluate variances between actual and expected time frames for updating medical information in its criteria. VA also continued to monitor efforts on whether earnings loss information can be used to update the criteria. Specifically, for its pilot or “proof of concept” program, VA has implemented a process for tracking, evaluating, and reporting on progress toward determining if the earnings loss data can be used to update the criteria.
Demonstrated progress: partially met. VA continued to face delays in fully completing its initial update of the criteria. VA’s August 2024 action plan stated that the department had updated the medical information covering 11 of the 15 body systems and made progress in studying earnings loss as a potential source for future updates. However, in January 2025, VA officials also stated the remaining four body systems are still being updated, in part due to VA’s lengthy internal and external review period. VA has extended the timeline to complete its comprehensive updates to fiscal year 2026, which is more than 10 years beyond VA’s initial goal. VA also continues to test the efficacy of procedures for producing earnings loss information but has not updated the criteria with this information.
Programs with Unified Strategies and Goals (OMB)
Leadership commitment: decreased to not met. This rating decreased from partially met in 2023 to not met. OMB staff stated that there are no plans to establish government-wide goals for the employment of people with disabilities, citing the difficulty of setting goals for more than 40 programs with different designs and target populations. Establishing government-wide goals could enhance coordination across disparate federal programs and help improve employment rates for people with disabilities, which remain lower than those for people without disabilities.
Instead, to enhance federal coordination, OMB staff told us that the Department of Labor's (DOL) Office of Disability Employment Policy led an interagency subcommittee on employment of people with disabilities. This subcommittee was established in 2021 under the Domestic Policy Council and took some actions to encourage collaboration across federal agencies and programs. However, in April 2024, OMB staff said the subcommittee had stopped meeting. As of September 2024, DOL staff reported no immediate plans to reconvene, although they said employment of people with disabilities was a key component of more recent interagency committees. As of January 2025, OMB provided no further updates in this area.
Capacity: partially met. OMB staff reported that the agency would continue supporting federal agencies on demonstration projects related to the employment of people with disabilities and on several interagency working groups, including the DOL-led subcommittee discussed previously. However, the subcommittee has not met since July 2023 and has no immediate plans to reconvene.
Action plan: not met. Neither OMB nor the subcommittee has established long-term priorities and plans to set goals for the overall employment of people with disabilities. Such a plan would provide OMB and relevant agencies a roadmap for achieving progress in this area.
Monitoring: partially met. Neither OMB nor the subcommittee reported monitoring progress toward a goal for employment for people with disabilities beyond the federal sector. However, DOL oversees progress in one area: the federal government’s existing goal for individuals with disabilities to comprise 7 percent of the workforce for federal contractors and subcontractors. DOL reported in September 2024 that 18 percent of contractors, who provided data by job group as part of a compliance review in fiscal year 2023, met the 7 percent goal. In addition, the federal government exceeded a prior goal for hiring an additional 100,000 people with disabilities by 2015.
Demonstrated progress: partially met. The DOL-led subcommittee previously collaborated on several efforts—including a website that launched in March 2024 with consolidated resources for people with disabilities, service providers, employers, and others—on ways to increase competitive integrated employment. However, as previously noted, it is not clear when or if the subcommittee will meet again.
What Remains to Be Done
Attention is needed to address these issues, including improving processing times of initial disability claims and appeals, improving training programs for disability claims processors, prioritizing rule and policy changes needed to use updated occupational criteria, and creating government-wide goals for the employment of people with disabilities.
As of January 2025, 20 related recommendations remain open. SSA, VA, and OMB should implement our recommendations related to improving the process of claiming benefits and coordinating between programs that support employment for people with disabilities. For example:
· SSA should continue refining its plans to address workload management challenges, including anticipated increases in disability workloads.
· VA should improve its training program for disability claims processors as we recommended, such as fully developing and documenting an integrated and comprehensive training plan as well as a policy and related processes for collecting and incorporating stakeholder feedback to improve training.
· VA should develop and implement a policy that describes the leading practices for government reforms that VA should follow to help ensure planning and implementation is consistent across its efforts. This would better position VA to achieve the intended results of its reforms, such as improving services to veterans.
· VA should develop and implement an evidence-based decision-making process that includes a plan outlining how it will build evidence to assess the underlying causes for the most common Board of Veterans’ Appeals (Board) errors and reasons for remands. The Board should use this evidence to better target its interventions and assess their results.
· OMB should establish a set of measurable, government-wide goals to help ensure that federal programs make progress toward increasing employment levels for people with disabilities.
Benefits
Since the area was added to the High-Risk List in 2003, more than $13.9 billion in financial benefits and more than 100 other benefits have been realized due to progress in modernizing and improving disability programs, including:
· In June 2024, we testified that SSA relied on outdated occupational data when making disability award decisions, citing cases where obsolete jobs—such as pneumatic tube operator—were used to deny benefits. The agency subsequently published new guidance and identified 114 occupations that it would no longer cite when denying a disability application. This will help SSA make more informed disability award decisions.
· VA took steps to assess and mitigate risks to its implementation of the Veterans Appeals Improvement and Modernization Act of 2017. Specifically, it articulated key goals and measures, such as the quality of appeals decisions. In addition, VA identified risks by estimating their significance, likelihood of occurrence, and needed actions to manage those risks. These efforts will help VA respond to risks that may impede the timeliness and quality of decisions in the new appeals process.
Contact Information
For additional information about this high-risk area, contact Elizabeth H. Curda, Director, Education, Workforce, and Income Security, at (202) 512-7215 or CurdaE@gao.gov.
Improving Federal Management of Programs That Serve Tribes and Their Members
Several federal agencies need to take additional actions to improve tribal health care and education programs and facilitate Tribes’ and their members’ access to their assets held in trust, including trust and restricted fee assets such as land and energy resources.
Why Area Is High Risk
The federal government faces challenges administering health care and education programs and managing assets (such as land and energy resources) held in trust for Tribes and their members. We added this area to our High-Risk List in 2017 because of these concerns. The United States has undertaken these trust responsibilities—through treaties, statutes, and historical relations—to protect and support Tribes and their members as part of the government-to-government relationship between the U.S. and Tribes.
Overall Area Rating
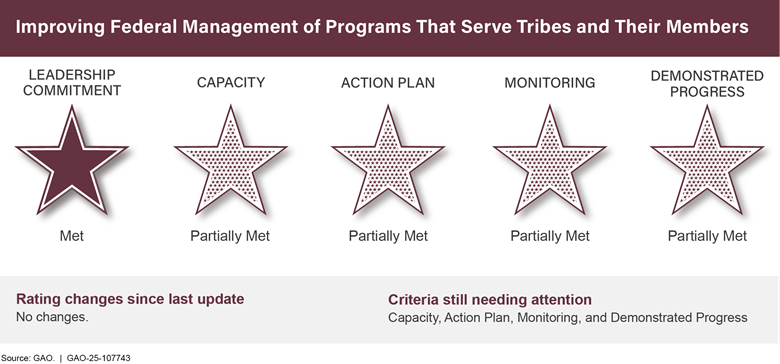
Since our 2023 update, the ratings for all five criteria remain unchanged. In addition, we have reframed our prior segment related to tribal energy service delivery to focus on activities to facilitate Tribes’ and their members’ access to their assets held in trust (e.g., land and energy resources). We made this change, in part, because of recent work that identified challenges with the Department of the Interior’s Office of the Assistant Secretary-Indian Affairs’ (Indian Affairs) workforce practices and Interior’s Bureau of Indian Affairs’ (BIA) timely delivery of real estate services and shortages in real estate staff.
The following sections present more detailed information on the three segments summarized in the overall rating.
Education. The Bureau of Indian Education (BIE)—within Interior’s Indian Affairs—has limited capacity to support schools and insufficient monitoring of schools’ use of federal funds.
Health Care. The Indian Health Service’s (IHS)—within the Department of Health and Human Services—inadequate oversight of federally operated facilities hindered its ability to ensure American Indian and Alaska Native communities have timely access to quality health care.
Assets Held in Trust. Management challenges at BIA—also within Indian Affairs—include slow real estate and energy service processing, and challenges at Indian Affairs include insufficient staff with appropriate skills to facilitate access to trust assets.
In addition to the management challenges we identified across these three areas, federal agencies, tribal organizations, and others have reported variability and shortfalls in funding that may adversely affect federal agencies’ ability to support Tribes and their members. For example, in 2018, the U.S. Commission on Civil Rights found that federal funding for certain programs and services for Tribes and their members continued to be disproportionately lower than federal funding for similar programs and services to non-Native populations.
Education
Leadership commitment: met. BIE continues to show commitment to addressing key management weaknesses by maintaining stability in the director position (see fig. 43). In addition, BIE assigned permanent leadership to the office responsible for overseeing the agency’s performance toward its strategic goals and addressing management weaknesses.
Capacity: partially met. BIE has taken preliminary steps to update and expand its workforce plan agency-wide, including additional offices that support and oversee schools. However, it continues to lack the staff capacity for certain key functions. We have found that a shortage of staff with the requisite skills and knowledge has affected BIE’s ability to oversee and support schools. These shortages include staff responsible for monitoring schools’ use of federal funds and supporting their operation of special education programs.
While BIE’s ability to hire new staff is affected by its budget and what officials described as a lengthy and complex hiring process, BIE can do more to build staff capacity. For example, BIE can complete and implement an updated workforce plan, including recruiting and retention strategies, and ensure that staff resources are aligned with its strategic plan goals.
Action plan: met. BIE continues to develop plans for corrective actions to address a variety of challenges we have raised for this high-risk area. For example, in 2024, BIE developed a plan to expand digital connectivity for schools and provide comprehensive guidance to support their distance learning programs as we recommended.
Monitoring: partially met. BIE established a process to monitor schools’ technology needs and ensure students and teachers have the necessary devices and internet bandwidth for distance learning. However, BIE has not taken the necessary steps to address other monitoring deficiencies. For example, it has not yet established adequate controls to ensure BIE staff overseeing purchase card transactions at BIE-operated schools consistently use Interior’s required tools and procedures to identify potential fraud and misuse of federal funds.
Demonstrated progress: partially met. Since 2023, BIE and related Interior offices improved special education, distance learning, and school construction. For example, BIE provided schools with comprehensive guidance on distance education in response to our finding that not all of its schools had the needed guidance to establish and operate distance learning programs.
However, significant work remains. Specifically, we have recommended that BIE strengthen oversight of schools’ federal COVID-19 spending and special education. BIE also must focus on building staff capacity, especially in offices that support and oversee schools. Demonstrating progress in addressing management weaknesses will depend on the sustained support of senior agency leaders.
Health Care

Leadership commitment: met. IHS is working to centralize its management structure to enhance senior leadership visibility across the organization, according to agency officials. For example, according to agency officials, the IHS executive leadership team, which includes Area and Headquarters leaders, meet quarterly to provide governance for the agency, plan strategically, and monitor progress of priorities to achieve quality results. Furthermore, to ensure more consistent oversight, IHS recently standardized governing body bylaws and agendas. IHS officials have also continued demonstrating leadership commitment by proactively meeting with us to discuss agency progress in addressing this high-risk area.
Capacity: partially met. Since 2023, IHS has taken some steps to enhance its capacity to resolve key risks. For example, agency officials reported developing and deploying a leadership training initiative that aims to develop selected managers and supervisors. IHS officials told us they improved training for current senior executives. IHS officials also reported developing a new mechanism to deploy skilled staff to the field to help address urgent patient safety needs.
While these are positive steps, concerns remain about IHS’s capacity to consistently deliver high-quality health care. Senior IHS officials have called for more adequate and stable funding for the agency, including by noting estimates that it is funded at approximately 49 percent of its level of need. IHS officials recently told us that funding constraints and a lack of staff hampered the agency’s ability to understand and address its facility and medical equipment needs. In 2024, we reported that many of IHS’s buildings were in poor or fair condition, and IHS’s equipment is aging—which can affect the agency’s ability to provide quality care (see fig. 44).
In addition, for fiscal year 2024, IHS reported a 30 percent overall vacancy rate for health care providers, with even higher vacancy rates in certain provider categories such as physicians (38 percent), nurses (34 percent), dentists (37 percent), and mental health professionals (43 percent).
Action plan: partially met. Since our 2023 update, IHS has shifted focus away from its previously drafted action plan that outlined long-term priorities to address selected areas of concern. Instead, it developed annual workplans that identify priorities for IHS improvement during a specific calendar year. The agency has also established a process to track and review progress toward its annual goals.
Although these workplans help identify priorities and track progress on a variety of agency efforts, the workplan does not reflect a longer-term vision for addressing the root causes of IHS management weaknesses. IHS officials told us the agency plans to draft a longer-term plan that would more fully address the root causes of its challenges but did not have a time frame for completing this effort.
Monitoring: partially met. IHS has implemented a process to monitor progress toward its annual workplan goals. As part of that process, IHS identified officials responsible for each goal who are to submit a report, at least quarterly, to agency executives on progress made, using a standard template.
However, we continue to report on problems stemming from IHS’s inadequate monitoring, including on adverse events, facility and medical equipment needs, and provider screening, that put patient safety and quality of care at risk. For example, we recently reported that a lack of consistent oversight places IHS at risk of hiring or retaining clinicians with performance, health, or other issues, potentially affecting the quality of care provided to patients. We also recently reported that IHS’s aging facilities and medical equipment can lead to delays in care—potentially exacerbating patients’ medical conditions.
Demonstrated progress: partially met. Since our last update, IHS has implemented four of our recommendations, including creating a standardized approach for documenting oversight related to provider misconduct. These actions have helped IHS to make progress toward creating a more consistent overall oversight approach. IHS has also made progress implementing its annual work plan priorities. As noted above, IHS needs to enhance its capacity to consistently deliver high-quality care. It also must develop an action plan and related mechanisms to ensure progress on longer-term goals and use this information to demonstrate improvement.
Assets Held in Trust

Leadership commitment: met. BIA continues to demonstrate leadership commitment to addressing key management weaknesses. For example, BIA updated procedures and documented the role of multiple agencies for the approval of certain agreements between Tribes and private parties. These agreements encompass leasing trust or restricted fee land for mineral development, including oil and gas. BIA is also identifying potential changes to its minerals, oil and gas, and other energy leasing regulations that would allow online lease sales and potentially decrease lease processing times. Additionally, BIA consulted with eight Tribes on resource needs to support renewable development and, subsequently, developed recommendations to support Tribes’ renewable development goals.
Capacity: partially met. To improve staff knowledge in providing energy and real estate services, BIA held numerous training opportunities including a national, in-person training for realty and energy staff, the first in 7 years. Additionally, BIA hired seven new realty specialists to address vacancies in its central office. In 2024, we reported that Indian Affairs had also taken some actions to improve capacity, such as expanding outreach to recruit new talent, but had not tracked vacancy data centrally.
However, BIA did not complete a planned workforce assessment for its energy and realty programs or implement a comprehensive workforce planning system. Indian Affairs’ leadership told us their most pressing challenge is additional funding and adequate staff to carry out their mission. By tracking vacancy data and conducting workforce assessments, its leadership can better identify the staff needed to manage energy and realty functions.
Action plan: partially met. The Indian Energy Service Center—funded by Indian Affairs and staffed by BIA and other agencies—has an active strategic plan for fiscal years 2022 through 2026 that includes goals for reducing processing times for energy-related documents and streamlining policies. However, BIA has not developed a comprehensive action plan for assessing these energy processing times, nor does it have an action plan to address the realty and workforce challenges we have identified.
To meet this criterion, Indian Affairs should develop an action plan that (1) identifies the root causes of the specific energy, realty, and workforce challenges we identified (e.g., slow processing times, staffing limitations, and limitations with data and tools); and (2) describes the corrective actions needed to address each challenge. The action plan should also identify the resources needed and measurable targets with clear time frames, both interim and full completions.
Monitoring: partially met. For energy development activities, BIA staff developed a list of pending and recently approved leases and the amount of time its field offices took to approve these leases. However, Indian Energy Service Center officials said the data system does not facilitate real time monitoring of energy transactions and data quality issues limit its utility. Additionally, in 2023, BIA initiated updates to its realty transaction tracking system to collect additional data needed to measure processing times.
To make additional progress, agency staff should more fully develop the data needed for a baseline understanding of BIA’s timeliness in processing energy and real estate transactions. BIA staff should also use these data to identify areas needing improvement and routinely monitor whether corrective actions are having the desired effect.
Demonstrated progress: partially met. The Indian Energy Service Center assisted several field offices with leasing and permitting work for energy development. It also coordinated meetings of seven regional groups of federal agencies to identify and resolve energy development issues.
However, BIA needs to develop quality data on review and response times for energy and realty transactions. Where timeliness concerns are evident, it needs to demonstrate improvement. BIA also needs to complete an assessment of its energy and realty workforce composition and implement a comprehensive workforce planning system. This is needed to document the specific funding and staff needs that Indian Affairs leadership told us exist.
What Remains to Be Done
We added this area to our High-Risk List in 2017. Attention is needed to address persistent management issues, including workforce planning, potential purchase card fraud, oversight of COVID-19 spending, limited facility and medical equipment, and timely processing of energy and real estate transactions. It will be important to address these issues and ensure a sustained focus on implementing our recommendations. There are 29 recommendations that remain open as of January 2025.
For BIE, there are 10 open recommendations related to education, including
· establishing training requirements for agency staff responsible for supporting and overseeing schools’ special education programs;
· developing controls to ensure agency staff consistently follow standard procedures when schools and other BIE grantees do not submit timely financial audit reports; and
· ensuring relevant staff consistently use Interior’s required tools and procedures to monitor schools’ purchase card transactions.
BIE also must focus on building staff capacity, especially in offices that support and oversee schools, and monitor agency actions to ensure sustained progress in these areas.
For IHS, there are eight open recommendations regarding health care, including
· taking steps to implement any needed improvements or disseminate best practices to address IHS trends in adverse health events;
· assessing the extent of the medical equipment data problems across all IHS areas and service units with federally operated facilities, and developing and implementing a plan to address any problems identified; and
· implementing regular monitoring of areas’ and facilities’ adherence to IHS's provider screening process.
In addition, IHS must develop and implement an action plan to address the root causes of its management weaknesses and monitor agency actions to ensure sustained progress in these areas.
There are 11 open recommendations for Indian Affairs and BIA related to assets held in trust, including
· conducting an initial assessment of processing times and compliance with regulatory and internal deadlines in delivering real estate services;
· developing performance goals and accompanying measures for monitoring real estate processing times;
· tracking vacancy data across Indian Affairs in a systematic and centralized manner; and
· identifying skills, knowledge, and competency gaps in mission-critical occupations across Indian Affairs.
In addition, Indian Affairs and BIA also must develop and implement an action plan to address the root causes of management weaknesses and monitor agency actions to ensure sustained progress in these areas.
Benefits
There have been more than 50 benefits realized due to progress in this high-risk area since it was added to the list in 2017. For example:
· BIE developed and provided schools with comprehensive guidance on a variety of areas related to developing and operating distance learning programs as we recommended.
· IHS took steps to improve the likelihood that the professional qualifications of clinicians employed at its federally-operated facilities were verified by publishing a standard operating procedure outlining the screening requirements. The agency developed a process to review training and policies related to provider quality and conduct, and established a standardized approach to monitoring provider quality of care. IHS also developed standards for patient wait times for primary care and urgent care appointments.
Contact Information
For additional information about this high-risk area and our Indian Affairs work, contact Anna Maria Ortiz, Director, Natural Resources and Environment, at (202) 512-3841 or OrtizA@gao.gov. For specific questions about our Bureau of Indian Education work, contact Melissa Emrey-Arras, Director, Education, Workforce, and Income Security, at (202) 512-7215 or EmreyArrasM@gao.gov. For our Indian Health Service work, contact Michelle Rosenberg, Director, Health Care, at (202) 512-7114 or RosenbergM@gao.gov.
Improving Federal Oversight of Food Safety
A government-wide approach is needed to address fragmentation—including inconsistent agency oversight—in the federal food safety oversight system.
Why Area Is High Risk
The safety and quality of the U.S. food supply, both domestic and imported, are governed by at least 30 federal laws collectively administered by 15 federal agencies. This federal oversight system is supplemented by states, localities, Tribes, and territories, which may have their own laws and agencies to address the safety and quality of food. Moreover, federal agencies responsible for carrying out similar food safety activities—such as inspecting food facilities and testing food for pathogens—may take different approaches to these activities due to differing authorities and regulations. This fragmentation has caused inconsistent oversight, ineffective coordination, and inefficient use of resources. We designated federal oversight of food safety as a high-risk issue in 2007.
Strengthening the food safety oversight system is critical to protecting Americans. Each year, six common foodborne pathogens sicken about 10 million Americans, according to a forthcoming study by the Department of Health and Human Services’ (HHS) Centers for Disease Control and Prevention (CDC). While many cases are mild, some cases can result in hospitalization, long-lasting symptoms and complications, or even death.
Common pathogens that can cause foodborne illness, hospitalizations, or death include Salmonella, Listeria monocytogenes, and Campylobacter, among others. Such pathogens can contaminate all types of foods, including meat, vegetables, dairy, and more. Foodborne illness also has widespread economic consequences, costing Americans an estimated $75 billion (in 2023 dollars) annually in medical care, productivity lost, and premature deaths, including those associated with secondary chronic illnesses and conditions that develop after the initial illness, according to a study by researchers from U.S. Department of Agriculture’s (USDA) Economic Research Service and collaborators.
According to CDC data, there were over 9,000 reported foodborne illness outbreaks between 2011 and 2022 across all 50 states. Some recent outbreaks include:
· In November 2024, HHS’s Food and Drug Administration (FDA) recalled 10,800 packages of eggs discovered to have come from a facility that tested positive for Salmonella. Around the same time, FDA recalled cucumbers linked to a Salmonella outbreak across 23 states, and which led to 25 known hospitalizations, as of December 17, 2024. FDA designated these recalls “Class I,” meaning there is a reasonable probability that use of the product will cause serious adverse health consequences or death.
· In November 2024, the CDC announced 10 deaths and 60 hospitalizations related to an outbreak of Listeria monocytogenes bacteria in deli meat products. The outbreak led to a recall of 7 million pounds of meat and poultry and an ongoing federal investigation by USDA’s Food Safety and Inspection Service (FSIS) in cooperation with the CDC.
· In January 2024, FSIS issued a public health alert due to a Salmonella outbreak attributed to charcuterie meats. The outbreak resulted in 104 confirmed illnesses and 27 hospitalizations across 33 states, according to CDC.
· In 2024, FDA and CDC investigated an outbreak of Listeria monocytogenes in queso fresco and cotija cheese that resulted in 26 identified illnesses, 23 hospitalizations, and two deaths across 11 states. This outbreak also resulted in a pregnancy loss and two newborns with Listeria monocytogenes infections.
· In 2018, an outbreak of E. coli in romaine lettuce impacted consumers across 36 states and was associated with 210 reported illnesses, 96 hospitalizations, 27 cases of hemolytic uremic syndrome, and five deaths, according to CDC.
· Zoonotic diseases—diseases transmitted to humans from animals, including livestock—are also an ongoing food safety concern. For example, raw (unpasteurized) milk and any products made from raw milk, including cheese, ice cream, and yogurt, can be contaminated with avian influenza (“bird flu”). CDC confirmed 915 cases of bird flu in cattle across 16 states from March 2024 through January 2025. CDC confirmed 66 human cases of bird flu over roughly the same period, 40 of which came from contact with dairy cows, and in January 2025, confirmed the first bird flu-related death in the United States. FDA recently began sampling raw cow’s milk cheese as part of an FDA, CDC, and USDA investigation into a recent outbreak of bird flu in poultry, dairy cows, and people across multiple states.[69]
FSIS and FDA are the primary agencies that ensure the safety of food products sold in the U.S. FSIS oversees the safety of meat, poultry, catfish, and processed egg products. States with programs that are “at least equal to” the federal program as determined by FSIS can conduct their own inspections of meat and poultry plants. FDA is responsible for virtually all other food, with nonfederal regulatory partners often conducting inspections under contract with FDA. These agencies conduct inspections, sample products for pathogens, and respond to outbreaks of foodborne illness, among other things. CDC investigates outbreaks of foodborne illnesses in conjunction with USDA and FDA to determine the source of contamination, the extent of related illness, and how to stop an outbreak.
Other federal agencies also have responsibilities for food safety. For example, the National Marine Fisheries Service provides voluntary fee-for-service examinations of seafood for safety and quality. The Environmental Protection Agency establishes tolerance levels for pesticides in food. U.S. Customs and Border Protection inspects imported food products, plants, and live animals for compliance with U.S. law and federal regulations.
Area Rating

All five criteria ratings remain unchanged since 2023.
Leadership commitment: partially met. USDA and FDA have continued to include crosscutting food safety efforts in their strategic and planning documents, a focus of multiple recommendations we have made since 2014. For example, in 2021, FDA issued a plan to improve its response to foodborne outbreaks, such as by collaborating with the CDC and USDA to detect and identify pathogens. In addition, as of October 2024, FDA had implemented a reorganization to unify its Human Foods Program. This program combines the functions of three FDA offices to provide clear, authoritative leadership to address food safety, including implementing the 2011 FDA Food Safety Modernization Act (FSMA).
There also has been some progress on the Healthy People initiative. Started in 1979, Healthy People identifies public health priorities with 10-year, measurable public health objectives. The latest iteration, Healthy People 2030, identifies specific objectives related to the goal of reducing foodborne illness, developed by a working group comprising officials from CDC, FDA, and FSIS. However, we found that the agencies were still developing six additional objectives related to reducing foodborne illness in the U.S. over the next decade.
While the agencies have taken promising steps, these actions do not provide an authoritative national strategy that establishes government-wide goals and performance measures. The Food Safety Working Group (FSWG), established by the President in March 2009 to coordinate federal efforts and develop goals to make food safer, previously provided a mechanism for a government-wide strategic approach. However, the group has not met since 2011 and is no longer active, as of January 2025, according to CDC officials.
Senior officials from USDA, FDA, and CDC told us that they were committed to improving the federal food safety system, and that collaboration between the agencies—while ad hoc in some cases—is consistent and has improved since our last High-Risk update in 2023. Office of Management and Budget (OMB) officials also agreed, but stated that the office does not plan to develop a government-wide performance plan or national strategy for food safety, as we recommended. While we acknowledge agencies’ improvements in specific areas, these efforts have not addressed the core issue of fragmentation across the federal food safety system.
Capacity: partially met. Federal food safety agencies would benefit from a centralized collaborative mechanism on food safety. USDA, FDA, and others have engaged in specific collaborative activities, including a workgroup that FDA and USDA convened in 2022 to collaborate on produce safety activities. However, these efforts do not include key elements for interagency collaboration that the FSWG previously provided, such as broad-based collaboration and discussion of resources.
Identifying the resources agencies need to carry out their food safety missions is an important part of a government-wide performance plan or, alternatively, a national strategy for food safety. Doing so can help address agency resource challenges. For example, according to FDA documentation, as of March 2023, the U.S. imported about 15 percent of its overall food supply from more than 200 countries or territories. This includes approximately 32 percent of the fresh vegetables, 55 percent of the fresh fruit, and 94 percent of the seafood, according to FDA (see fig.45). The proportion of food derived from imports has also increased over time. For example, fresh fruit is up from 50 percent and fresh vegetables up from 20 percent since 2007, according to USDA’s Economic Research Service.
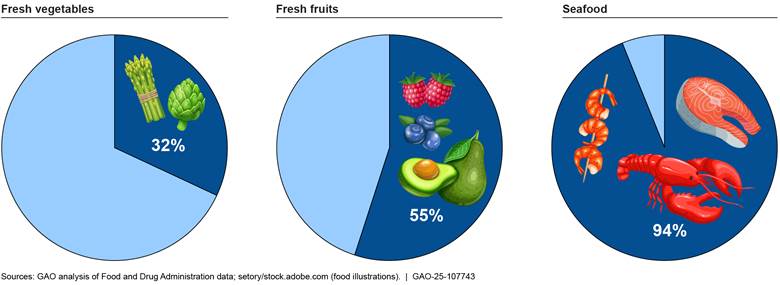
However, FDA officials recently acknowledged that, given the agency’s workforce capacity and resources, it was not capable of meeting its inspection targets for foreign or domestic food facilities. For example, according to FDA data, FDA conducted an average of 917 foreign food safety inspections each year from fiscal years 2018 through 2023—about 5 percent of its target of 19,200 inspections for this period (see fig. 46).
Figure 46: Food and Drug Administration’s (FDA) Performance in Meeting Annual Targets for Foreign Food Facility Inspections according to FDA Data, Fiscal Years 2018–2023
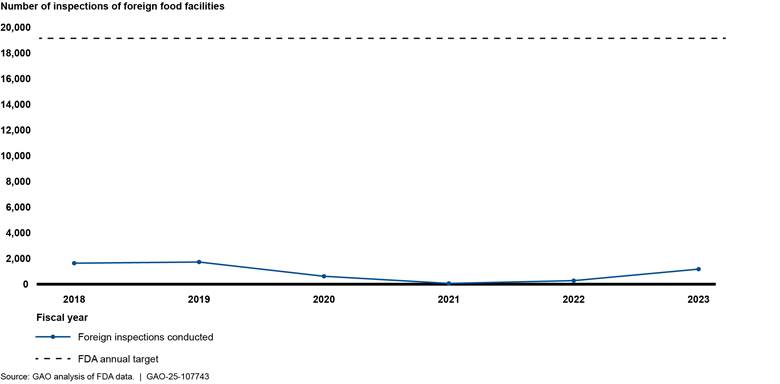
Note: FDA has interpreted the FDA Food Safety Modernization Act to require that, beginning in 2016, the agency inspect 19,200 foreign facilities per year. FDA includes both completed and attempted inspections in its fiscal year totals to track its progress covering foreign food facilities in FDA’s inventory that are due for inspection. Attempted inspections occur when FDA investigators attempt to conduct an inspection of a food facility, but the inspection cannot be completed.
We also found that FDA had not identified the staff and resources it needs to meet foreign inspection targets. Taking steps to determine the appropriate size and workload of its foreign inspector cadre will help FDA ensure it can safeguard imported food. Taking similar steps may also help FDA identify the resources the agency and nonfederal regulatory partners need to implement FDA’s 2022 food traceability rule to help identify the source of outbreaks of foodborne illness.
Moreover, a centralized collaborative mechanism on food safety as well as a national strategy for food safety could provide agencies responsible for carrying out similar activities—such as food facility inspections, which either FDA or FSIS may conduct based on the type of food—to learn from each other’s approaches to achieving their mission within resource constraints and leveraging resources from key stakeholders and foreign partners. A national strategy could also provide the framework for stakeholders to identify food safety laws and regulations that may need to be updated and food inspection processes that could be modernized.
For example, FSMA, which was signed into law in 2011, presents a risk-based approach by requiring FDA to allocate inspection resources to food facilities based on known risks. By contrast, the Federal Meat Inspection Act and Poultry Products Inspection Acts—under which FSIS inspects and regulates meat and poultry products—have not been substantively overhauled in decades and still require USDA to inspect each FSIS-regulated animal carcass. A senior USDA official with whom we spoke in December 2024 stated that FSIS’s carcass-by-carcass approach may merit revision—as well as benefit from the incorporation of more modern technologies—to better economize FSIS’s efforts while still providing for reasonable assurance of food safety. By helping agencies align their approaches, a national strategy could allow for more effective and efficient oversight of the nation’s food supply.
Action plan: not met. Without a government-wide performance plan or a national strategy for food safety, decision-makers are hampered in setting priorities, allocating resources, and restructuring federal efforts, as needed, to achieve long-term goals. According to officials, FDA intends to develop a comprehensive plan in fiscal year 2025 that would focus on its food safety inspection efforts.
FDA should take steps to ensure the plan includes specific performance targets and associated measures for monitoring FDA’s performance, as we recommended. Doing so will help FDA ensure its food safety inspections achieve its primary goal of protecting U.S. consumers. However, without a government-wide action plan, federal food safety agencies are limited in their ability to develop broad-based food safety goals and objectives.
Monitoring: not met. We have not seen significant progress in developing a government-wide strategy or plan that would help align agencies’ respective monitoring efforts. Individual agency efforts to track progress on addressing foodborne illnesses and related outbreaks have been mixed. For example, in 2023, the CDC finalized an internal dashboard with performance indicators for tracking and responding to outbreaks, as we recommended.
However, we recently found that USDA has not finalized updates to existing pathogen standards—the level at which the presence of a pathogen in a food item is considered unsafe, according to FSIS—or any new standards for meat and poultry products. For example, some pathogen standards (e.g., Salmonella in ground beef) have not been updated since 1996, and other products—such as ground pork—continue to have no pathogen standards. Keeping pathogen standards current, such as by ensuring they reflect what is known about emerging food safety risks, is important for reducing foodborne illness associated with meat and poultry products. We also have ongoing work evaluating challenges FDA has faced implementing key FSMA rules. These include those related to tracing the sources of foodborne illness outbreaks and establishing and monitoring controls—including facility sanitation requirements, for example—to minimize hazards in human food.
A government-wide performance plan or national strategy for food safety is needed to facilitate effective monitoring of federal food safety efforts, such as which areas need corrective measures. Such a plan or strategy could also better inform Congress and the public about these efforts.
Demonstrated progress: partially met. FDA and USDA continue to collaborate on food safety through joint working groups and information sharing practices, such as the Interagency Risk Assessment Consortium and a working group supporting the Healthy People 2030 Initiative. While such collaboration can help the federal government move toward developing a government-wide performance plan for food safety, the current agency-by-agency focus does not provide the integrated perspective necessary to guide decision-making and inform the public.
A government-wide performance plan or national strategy could enhance collaboration among agencies that have a food safety role, such as CDC, the National Marine Fisheries Service, and Customs and Border Protection. Formalizing the FSWG would also help ensure sustained leadership across food safety agencies over time.
What Remains to Be Done
There has been limited progress in this area since our last update. Specifically, no entity has assumed leadership responsibility for coordinating food safety efforts across the federal government.
Since we added food safety to our High-Risk List in 2007, we have made numerous recommendations to address fragmentation, enhance collaboration, and identify capacity needs among agencies with food safety responsibilities. For this area to be removed from our list, progress needs to be made, in particular, on implementing those food safety recommendations we have designated as high-risk. As of January 2025, six of these high-risk recommendations remain open, including:
· The appropriate entities within the Executive Office of the President should develop, in consultation with relevant federal agencies and other stakeholders, a national strategy for food safety that, among other things, establishes high-level sustained leadership, identifies resource requirements, and monitors progress.
· FDA should develop and implement a performance management process that includes defining the desired results of FDA’s food safety inspection efforts, collecting performance information on these efforts, and using this information to assess performance, inform FDA decision-making, and communicate to Congress and the public about results. Specific elements of this process could include, but not be limited to, data and information on FDA’s progress in recruiting and retaining food safety investigators and in minimizing incidences of attempted inspections.
· FDA should complete an analysis to determine the annual number of foreign food inspections that is sufficient to ensure comparable safety of imported and domestic food. If the inspection numbers from that evaluation are different from the inspection targets mandated in FSMA, FDA should report the results to Congress and recommend appropriate legislative changes.
· FDA should take steps to determine the appropriate size and workload of its foreign investigator cadre for the purpose of meeting FDA’s foreign inspection goals and ensuring FDA’s ability to safeguard imported food.
· FDA and USDA should more fully incorporate the seven leading practices for effective collaboration in the agencies' interagency agreement for the joint oversight of cell-cultured meat (this comprises two recommendations, one to each agency).
· FDA should direct the Center for Food Safety and Applied Nutrition to finalize and document an implementation plan to help the agency achieve its regulatory goal of compliance with the food traceability rule by January 20, 2026. Such a plan should include FDA's resource needs, strategies for facilitating compliance with the rule, and detailed plans for communicating with and educating regulated entities, nonfederal regulatory partners, and FDA regulatory staff about the rule's requirements.
Congressional Actions Needed
In July 2024, companion bills were introduced in the House and Senate that proposed establishing a Federal Food Administration—a new agency that would take over food safety responsibilities from other federal agencies.[70] No further action was taken on either bill, and as of January 2025, no similar legislation has been introduced in the 119th Congress. As of January 2025, five matters for congressional consideration remain open and are significant for removing this area from the High-Risk List. Four of these matters request that Congress consider
· directing OMB to develop a government-wide performance plan for food safety that includes results-oriented goals and performance measures and a discussion of strategies and resources; and
· formalizing the FSWG through statute to help ensure sustained leadership across food safety agencies over time.
· directing FDA to conduct an analysis to determine the annual number of foreign food facility inspections sufficient to ensure the safety of imported food, and communicate this number and FDA’s underlying analysis to Congress; and
· upon receiving the relevant information and analysis from FDA, updating the annual target for the number of foreign food facility inspections FDA should conduct to ensure the safety of imported food.
If weaknesses in food safety oversight persist, Congress may wish to consider
· commissioning the National Academy of Sciences or a blue ribbon panel to conduct a detailed analysis of alternative organizational food safety structures and report the results of such an analysis to Congress.
Benefits
Since we added this area to our list in 2007, implementation of our recommendations has led to more than 70 benefits to the federal government, including the following:
· In 2023, CDC set performance goals and objectives related to managing foodborne, waterborne, and environmentally transmitted infections and incorporated them into its strategic plan, which will help CDC to evaluate the overall health of multistate outbreak response and identify changes in response effectiveness.
· In 2023, we found that USDA and FDA had more fully incorporated leading practices for collaboration in their working groups on cell-cultured meat, such as by assessing and sharing resources. As a result, USDA and FDA will help minimize potential fragmentation in oversight, ensure more efficient use of resources, and provide clarity to stakeholders.
· In 2020, FDA and USDA began ongoing discussions of relevant food safety research, including detection methods of contaminants in food. These discussions will help FDA and USDA enhance their ability to coordinate their research on such methods, use their resources efficiently, and avoid potentially duplicative efforts.
Contact Information
For additional information about this high-risk area, contact Steve Morris, Director, Natural Resources and Environment, at (202) 512-3841 or MorrisS@gao.gov.
Limiting the Federal Government’s Fiscal Exposure by Better Managing Climate Change Risks
To reduce its fiscal exposure to climate change, the federal government needs a cohesive, strategic approach with strong leadership and the ability to manage risks across the entire range of related federal activities.
Why Area Is High Risk
Numerous studies have concluded that climate change poses risks to many environmental and economic systems and creates a significant fiscal risk to the federal government.[71] Between fiscal years 2015 and 2024, selected appropriations for disaster assistance totaled about $448 billion.[72] Even with efforts to reduce greenhouse gas emissions, costs are likely to rise—in part because greenhouse gases already in the atmosphere will continue altering the climate for decades. We found that the federal government is currently not as well positioned as possible to manage this reality.
As we have stated since we designated this area as high risk in 2013, the federal government needs to take government-wide action to reduce its fiscal exposure, including, but not limited to, its roles in five areas: (1) providing disaster aid, (2) insuring property and crops, (3) owning or operating infrastructure, (4) leading a strategic plan to coordinate federal efforts, and (5) providing data and technical assistance to decision-makers. The federal government can limit its fiscal exposure to climate change by enhancing climate resilience—that is, taking actions to reduce potential future losses by planning and preparing for potential climate hazards. Congress should also consider better assigning responsibility within the federal government to prioritize climate resilience projects for investment, among other things.
The increased frequency and intensity of certain extreme weather events across the country—such as the flooding caused by Hurricanes Helene and Milton—have focused greater attention on federal disaster recovery efforts. The efforts are spread across more than 30 agencies, making it difficult for communities to figure out whom to turn to for help. Due to significant and long-standing challenges with federal disaster recovery efforts, we are adding it as a new high-risk area in 2025. This new Improving the Delivery of Federal Disaster Assistance high-risk area elevates the topic for significant attention and removes it as a component of this area.
Overall Area Rating
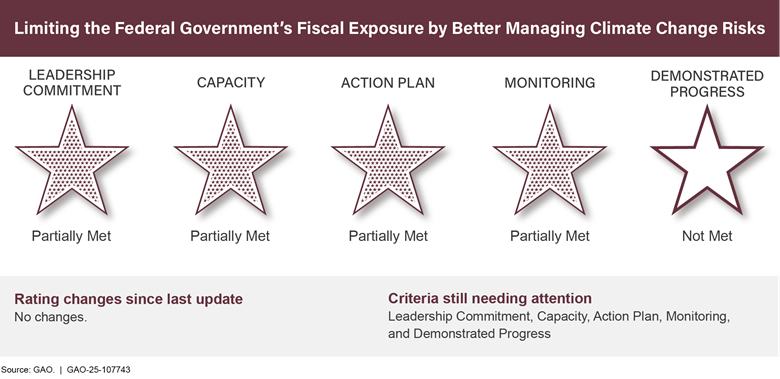
Overall ratings for all five criteria remain unchanged since 2023. Executive Orders (E.O.) 14008 on Tackling the Climate Crisis at Home and Abroad, E.O. 14030 on Climate-Related Financial Risk, and E.O. 14057 on Catalyzing Clean Energy Industries and Jobs Through Federal Sustainability, all of which were issued in 2021, directed agencies to plan, implement, and report on climate resilience activities. [73] These executive orders were revoked in January 2025 by E.O. 14148 on Initial Rescissions of Harmful Executive Orders and Actions.
The following sections present more detailed information on the four areas summarized in the overall rating.
Federal Insurance Programs

Leadership commitment: partially met. The Inflation Reduction Act of 2022 included $24.4 billion in appropriations to the U.S. Department of Agriculture (USDA) related to agricultural conservation and forest restoration, including for hazardous fuels reduction, climate mitigation, resilience, and conservation programs.[74] This funding is intended to help farmers and foresters adopt conservation practices that improve climate resilience, potentially lowering costs of disasters and crop insurance. However, Congress should consider comprehensive reform to improve the National Flood Insurance Program’s solvency and enhance the nation’s resilience to flood risk.
Capacity: partially met. USDA’s network of 10 regional Climate Hubs in the U.S. provides technical support and information that can help agricultural producers manage climate change impacts and potentially reduce crop losses covered by the federal crop insurance program. However, to help increase capacity further, USDA needs to analyze options for enhancing climate resilience of agricultural producers. This includes expanding technical assistance provided by USDA and other key partners to prioritize and promote practices that enhance climate resilience.
Action plan: partially met. In June 2024, USDA and the Department of Homeland Security—which includes the Federal Emergency Management Agency—released updated climate adaptation plans to better integrate climate risk across their missions, operations, and asset management. However, we recommended that USDA needs to, as appropriate, increase its annual adjustments of federal crop insurance premium rates in areas with higher crop production risks.
Monitoring: partially met. USDA and the Department of Homeland Security’s June 2024 adaptation plans describe the progress they made since implementing their 2021 climate adaptation and resilience plans. However, it is too early to determine the effectiveness of these plans as a monitoring mechanism. The executive order that directed agencies to implement and update these plans, E.O. 14057 on Catalyzing Clean Energy Industries and Jobs Through Federal Sustainability, was revoked in January 2025 by E.O. 14148 on Initial Rescissions of Harmful Executive Orders and Actions.
Demonstrated progress: not met. The federal government should improve the resilience of federally insured property or address structural weaknesses, as we recommended. This includes analyzing options to help enhance agricultural producers’ climate resilience and incorporating them, as appropriate, into ongoing climate resilience prioritization and planning.
Federal Government as Property Owner
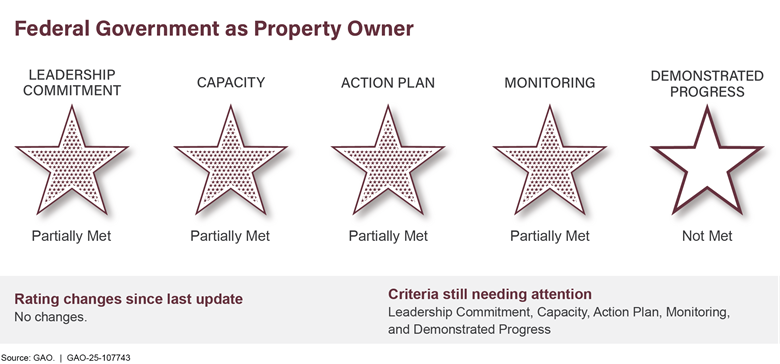
Leadership commitment: partially met. The National Defense Authorization Act for Fiscal Year 2024 directed the Department of Defense (DOD) to include the impact of military installation resilience into certain guidance documents, particularly those governing installation master planning.[75] However, DOD needs to further integrate climate change adaptation into its overseas installations.
Capacity: partially met. Federal agencies have made mixed progress in increasing their capacity to protect federal property from climate-related risks. In 2023, the U.S. Postal Service updated its facility investment process to include climate change risk data as part of its preliminary reviews, as we recommended.
However, opportunities remain for agencies to increase capacity. For example, DOD needs to clarify instructions for considering climate change adaptation when comparing proposed construction projects. Additionally, the Department of State needs to ensure that its Bureau of Overseas Buildings Operations adjusts its Climate Security and Resilience program plans to reflect department decisions on program staffing levels. The federal government also needs to further increase capacity by providing the best available forward-looking climate information for standards-developing organizations to consider when developing design standards, building codes, and voluntary certifications.
Action plan: partially met. In June 2024, 28 federal agencies released updated adaptation and resilience plans to better integrate climate risk across their missions, operations, and asset management. In 2023, the Federal Highway Administration provided documentation of how it is implementing options—such as administering grants for resilience activities and implementing the Department of Transportation’s resilience guidance—to enhance the climate resilience of federally funded roads, as we recommended.
However, the Army Corps of Engineers has yet to implement options we identified to enhance the climate resilience of federally funded flood risk management infrastructure.
Monitoring: partially met. The federal government has made some progress in monitoring climate risks to federal property. For example, in 2023, DOD developed performance measures for its community grant programs that support community coordination with local military installations on climate change, as we recommended. Additionally, the June 2024 adaptation and resilience plans updated progress on agencies’ efforts. However, it is too early to determine the effectiveness of these monitoring mechanisms. The executive order that directed agencies to implement and update these plans, E.O. 14057 on Catalyzing Clean Energy Industries and Jobs Through Federal Sustainability, was revoked in January 2025 by E.O. 14148 on Initial Rescissions of Harmful Executive Orders and Actions.
Demonstrated progress: not met. The federal government needs a comprehensive approach to improve the resilience of facilities it owns and operates and land it manages, as we recommended.
Federal Government as Leader of National Climate Strategic Plan
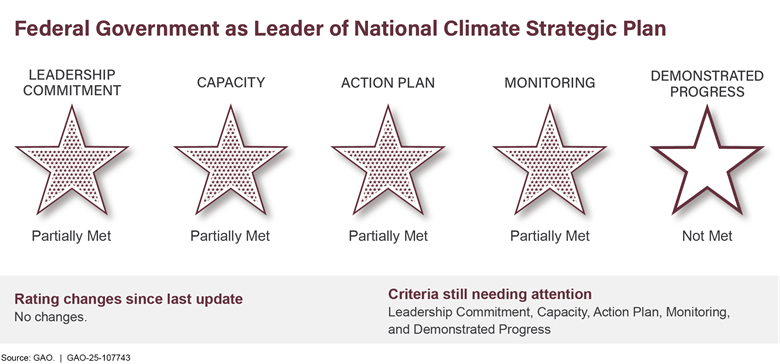
Leadership commitment: partially met. Two federal guidance documents identified climate resilience-related objectives and opportunities for federal action: the 2023 National Climate Resilience Framework and the 2024 Climate Resilience Game Changers Assessment. For example, one objective of the National Climate Resilience Framework is to embed climate resilience into planning and management. In addition, the U.S. Global Change Research Program established the Federal Adaptation and Resilience Group with members from federal agencies to foster interagency collaboration and increase resilience to climate variability and change. Finally, on January 10, 2025, the Department of State announced the release of the National Adaptation and Resilience Planning Strategy, which provides details on the U.S. approach to climate resilience and adaptation.
However, the federal government has not established an organizational arrangement with a climate resilience strategic plan to target federal resources toward high-priority projects that manage some of the nation’s most significant climate risks, including a climate migration pilot program. For example, in the fall of 2024, Newtok, Alaska became one of the first Alaska Native villages to fully relocate its population to a new site because of climate change and work remains to complete important infrastructure and permanent housing. It took over 30 years to begin relocating Newtok, in part because no federal entity has the authority to coordinate assistance.
Capacity: partially met. The President’s budgets for fiscal years 2024 and 2025 continued to account for some fiscal risks of climate change, such as flood risk at federal facilities. The Office of Management and Budget also revised its financial reporting requirements for federal agencies in May 2024 to clarify how climate-related risk could be discussed in agency annual financial statements.[76] However, none of these efforts include clear priorities for climate-related activities of key federal entities.
Action plan: partially met. The climate and resilience plans updated by federal agencies in June 2024 also help address this segment of the high-risk area. However, the federal government has not developed a strategic plan—with clear priorities and roles and responsibilities for key federal entities—to guide the nation’s efforts to adapt to climate change. In addition, the Department of Energy has yet to release a final department-wide strategy to coordinate its efforts to enhance the resilience of the electricity grid to the risks of climate change.
Monitoring: partially met. It is too early to determine if the June 2024 federal climate adaptation plans will support effective monitoring. The executive order that directed agencies to implement and update these plans, E.O. 14057 on Catalyzing Clean Energy Industries and Jobs Through Federal Sustainability, was revoked in January 2025 by E.O. 14148 on Initial Rescissions of Harmful Executive Orders and Actions.
Demonstrated progress: not met. The federal government needs to develop a national strategic plan with clear roles and responsibilities to better enhance climate resilience.
Technical Assistance to Federal, Tribal, State, Local, and Private-Sector Decision-Makers

Leadership commitment: partially met. Published in 2023, the Federal Framework and Action Plan for Climate Services calls for a more coherent strategy for providing information and products that enhance knowledge and understanding about the impacts of climate change for decision-making. In addition, in January 2024, the National Science and Technology Council established a Subcommittee on Climate Services.
However, the federal government has not led the development of a government-wide approach for providing decision-makers with the best available climate-related information and assistance with translating such information. The Environmental Protection Agency also has not developed and provided training and technical assistance on using existing authorities and requirements to manage climate risks to hazardous waste treatment, storage, and disposal facilities.
Capacity: partially met. Progress has been mixed across the federal government on developing the capacity to share climate information across different sectors. For example, the U.S. Global Change Research Program is developing the Climate Resilience Information System to enable more consistent development of regionally and locally tailored climate information. To help advance climate-informed decision-making, the National Marine Fisheries Service published updated regional action plans to guide the agency’s ongoing implementation of its Climate Science Strategy, as we recommended. In addition, the Tennessee Valley Authority developed a climate adaptation plan and the Western Area and Southeastern Power Administrations issued climate vulnerability assessments and resilience plans, as we recommended.
However, the federal government has not developed a government-wide approach for providing decision-makers with the best available climate-related information and assistance with translating climate-related data into accessible information. In addition, the Nuclear Regulatory Commission has yet to assess whether its existing processes adequately address climate risks to nuclear power plants and develop and implement a plan to address any gaps identified.
Action plan: not met. The federal government has not developed a plan to implement a system to provide the best available information to decision-makers to support climate resilience.
Monitoring: not met. There are neither programs nor mechanisms to monitor government-wide progress addressing the challenges we have identified providing climate-related technical assistance.
Demonstrated progress: not met. The federal government needs to demonstrate long-term improvement in its climate-related technical assistance to decision-makers, as we recommended.
What Remains to Be Done
As of January 2025, 44 recommendations remain open since this area was designated as high-risk in 2013. These recommendations address each of the four segments that compose this high-risk area as follows:
· Federal Insurance Programs. The federal government should incentivize climate resilience by incorporating it into the requirements for receiving payments from federal flood and crop insurance programs. For example, USDA should further analyze the 13 options identified to enhance agricultural producers’ climate resilience and integrate them, as appropriate, into its ongoing climate resilience planning.
· Federal Government as Property Owner. The federal government needs a comprehensive approach to improve the climate resilience of facilities it owns and operates and land it manages. For example,
· The Army Corps of Engineers should analyze the 14 options identified to enhance the climate resilience of federally funded flood risk management infrastructure and integrate them, as appropriate, into its future climate resilience planning.
· Department of State should ensure the Bureau of Overseas Buildings Operations adjust its Climate Security and Resilience program plans to reflect department decisions on program staffing levels.
· DOD should require overseas installations to systematically track costs associated with climate impacts and include climate change adaptation coordination in agreements between DOD installations and the surrounding host nation communities, among other things.
· The Department of Commerce should convene federal agencies for an ongoing effort to provide the best available forward-looking climate information to standards-developing organizations for their consideration in the development of design standards, building codes, and voluntary certifications.
· Federal Government as Leader of a National Climate Strategic Plan. The federal government could better reduce its fiscal exposure if federal efforts were coordinated and directed toward common goals, such as improving climate resilience. For example,
· Department of Energy should develop a department-wide strategy to enhance electricity grid resilience to climate change, and the Federal Energy Regulatory Commission should identify and assess climate change risks to the electricity grid and plan a response.
· Entities within the Executive Office of the President should use information on the potential economic effects of climate change to help identify significant climate risks and craft appropriate federal responses.
· Technical Assistance to Federal, Tribal, State, Local, and Private-Sector Decision-Makers. The federal government needs a government-wide approach for providing federal, tribal, state, local, and private-sector decision-makers with the best available climate-related information and assistance with translating climate-related data into accessible information. For example,
· Environmental Protection Agency should provide training and technical assistance and assess issuing regulations to clarify requirements and provide direction on managing climate risks at hazardous waste treatment, storage, and disposal facilities, among other things.
· Nuclear Regulatory Commission should assess whether its existing processes adequately address climate risks to nuclear power plants and develop and implement a plan to address any gaps identified.
· Environmental Protection Agency should identify and engage technical assistance providers to help water utilities incorporate climate resilience into infrastructure projects.
· The Executive Office of the President should direct a federal entity to develop a set of authoritative climate change projections and observations and create a national climate information system with defined roles for federal agencies and nonfederal entities.
Congressional Actions Needed
There are 10 open matters for Congress to consider, including:
· developing an organizational arrangement with five key elements to prioritize climate resilience investments: (1) a national climate resilience strategic plan, (2) a national climate information system, (3) expanded usage of climate economics information, (4) a consistent approach for prioritizing federal climate resilience investments, and (5) a community-driven climate migration pilot program.
· providing direction or authority to the Army Corps of Engineers to further enhance the climate resilience of federally funded flood risk management infrastructure.
· establishing a coordinating entity to strategically target federal investments to Alaska Native villages facing significant environmental threats.
· requiring that climate resilience be incorporated in the planning of all drinking water and wastewater projects that receive federal financial assistance.
· comprehensive reform to the National Flood Insurance Program to improve its solvency and enhance the nation’s resilience to flood risk.
Benefits
Since we designated this area as high-risk in 2013, the federal government has recognized more than 40 benefits of limiting the federal government’s fiscal exposure by better managing climate change risks, including:
· DOD developed performance measures for its community grant programs that support community coordination with local military installations on climate change.
· The National Marine Fisheries Service worked with fisheries managers to discuss and identify priorities that advance the climate resilience of their fisheries.
· The U.S. Postal Service incorporated climate information into its process for making facility investments.
Contact Information
For additional information about this high-risk area, contact J. Alfredo Gómez, Director, Natural Resources and Environment, at (202) 512-3841 or GomezJ@gao.gov.
Management of Federal Oil and Gas Resources
To enhance its oversight of oil and gas development on federal lands and waters, the Department of the Interior needs to accurately determine and collect revenue and address human capital challenges.
Why Area Is High Risk
Interior collected almost $15 billion in oil and gas revenues in fiscal year 2024. However, it may not be collecting the government’s fair share of revenues from oil and gas produced on federal lands and waters. It also continues to face strategic challenges with managing its workforce. This high-risk area comprises two segments representing these ongoing challenges.
Specifically, Interior faces challenges related to the compliance data systems to support the collection, accounting, and verification of revenues—including royalties paid by companies—from oil and gas production at federal lease sites. Interior also faces challenges with filling vacancies and maintaining the workforce it needs to manage oil and gas resources and verify their production and royalties. These and other issues hamper Interior’s ability to ensure the public receives a fair return for resources extracted from federal lands and waters.
Overall Area Rating
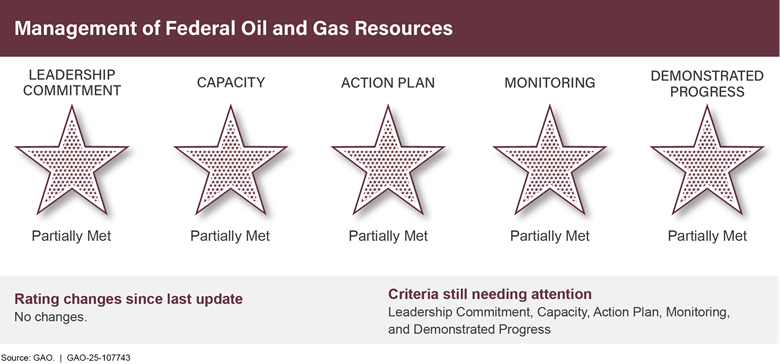
Overall and segment ratings for all five criteria remain unchanged since 2023. The following sections present more detailed information on actions taken for the two segments summarized in the overall rating.
Revenue Determination and Collection
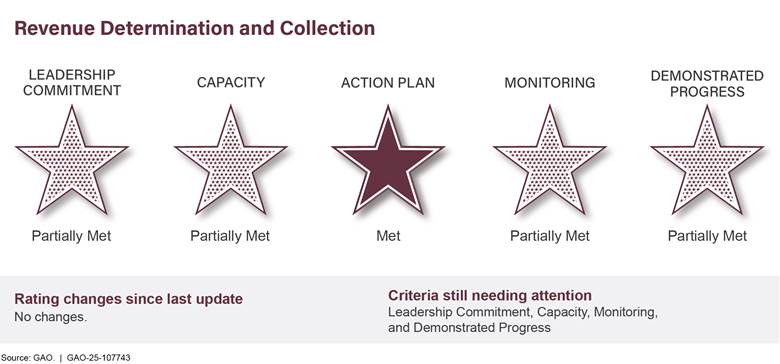
Leadership commitment: partially met. In April 2024, Interior’s Bureau of Land Management (BLM) published its Final Waste Prevention, Production Subject to Royalties, and Resources Conservation Rule.[77] The final rule requires that companies pay royalties on flared (or burned) gas above certain volumes or in other circumstances.[78]
However, management in Interior’s Office of Natural Resources Revenue (ONRR) stopped efforts to estimate an annual royalty gap—the difference between the royalties ONRR received for oil and gas produced on federal lands and what it should collect—and could not provide documentation to explain why. Periodically estimating the royalty gap would help inform ONRR leadership’s decision-making and strategic planning of compliance efforts (see fig. 47).
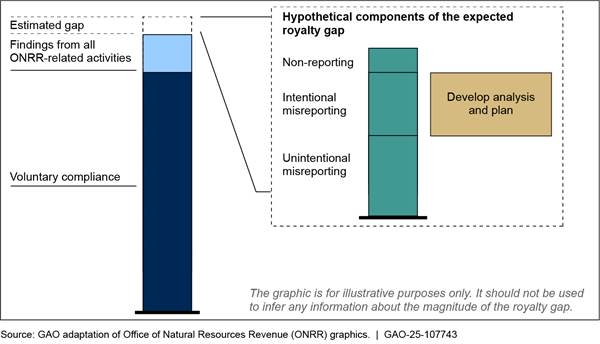
Note: The royalty gap is the estimated amount of royalty revenues that are not collected. ONRR developed this preliminary model, which it last used in 2011.
We also found that Interior and BLM’s lack of effective leadership contributed to a failed modernization of an IT system central to managing inspections, including those that verify oil and gas production volumes—a key component for determining royalties. For example, Interior officials who oversee IT projects did not know about the system’s failure until we brought it to their attention. Interior urgently needs effective leadership and oversight to address the department’s IT governance weaknesses, especially as BLM begins a new initiative to replace the failed system.
Capacity: partially met. In May 2023, Interior took steps to address some of the deficiencies in its oil and gas IT systems that we identified. Specifically, Interior issued a new data sharing policy that establishes mandatory data sharing requirements and responsibilities, such as requiring that all new systems provide automated data sharing capabilities. However, Interior continues to experience challenges with its IT systems. For example, we found that BLM reverted to relying on paper records to manage permitting and inspections after the failed IT system modernization.
We also reported that ONRR does not have consistent and complete data to assess historical performance for its compliance program. As ONRR retired one IT system and implemented another, it did not transfer the legacy compliance data. As a result, compliance data were stored in an inconsistent manner across two data systems, making it difficult to accurately assess historical trends. Assessing the need for a consistent and complete set of compliance data would enable ONRR to be better informed about its ability to assess compliance program performance and whether such data could inform its compliance strategy.
Action plan: met. Interior has taken steps, or shared with us its plans to take steps, to address various deficiencies we have identified. For example, Interior told us that it had established regular reviews of its IT portfolio and was working to update a key policy to help it ensure oversight of IT projects. In addition, Interior tracks our open recommendations, and officials periodically meet with us to discuss them.
Monitoring: partially met. In July 2023, ONRR established an accuracy goal based on payor coverage (the percentage of payors subject to data mining, compliance review, or audits) that aligns with its mission of collecting, accounting for, and verifying royalty payments. ONRR also developed a performance measure for tracking compliance cases that find noncompliance, helping ONRR align its compliance activities with its compliance goals.
However, ONRR has been unable to fully assess the effectiveness of its risk models for compliance case selection in part because it does not use a methodology that employs a random sample to select compliance cases. A random sample is important to the development of risk models because it serves as a proxy for the overall universe of all companies, properties, or products, including those that have never been subject to compliance activities. Access to this proxy is essential for determining the indicators that predict risk. ONRR should assess the benefits of incorporating randomly selected compliance activities into its workplans, which would give it better information to validate its methodology for compliance review case selection.
Demonstrated progress: partially met. Interior has taken various actions since our last update. For example, as described above, BLM published a final rule in April 2024 to govern natural gas venting and flaring and established an accuracy goal related to revenue determination and collection. Interior needs to continue its efforts to address the issues we have identified related to its oversight of royalty collection—including data quality issues—and management of IT projects.
Human Capital Challenges

Leadership commitment: partially met. BLM has completed a strategic workforce plan and begun its implementation as of January 2025, according to an agency official. However, Interior has not yet resumed efforts to ensure bureau leadership incorporates key practices for effective agency reforms before undertaking reorganization activities at Interior bureaus. It paused these efforts in July 2024. These key practices include strategic workforce planning, such as assessing how a reform will affect the workforce, including staff recruitment.
We also found that ONRR leadership did not always prioritize efforts to hire data analysts or statisticians. Instead, leadership relied on a vendor to develop data systems and drive progress in certain parts of its compliance program. In part because it allocated resources elsewhere within the agency, ONRR became overly reliant on its vendor to understand its own data. ONRR should determine the number of staff it needs in this area, so it can better ensure it has the necessary staff with the skills to understand its compliance data systems and analyze its data.
Capacity: partially met. The relocation of BLM’s headquarters from Washington, D.C., to Grand Junction, Colorado, announced in July 2019, resulted in a high number of vacancies. The relocation also contributed to challenges such as a widespread loss of experienced staff with institutional knowledge, as well as delays in creating or clarifying guidance or policy. Implementing its agency-wide strategic workforce plan will help the bureau better address these and related challenges.
In addition, ONRR’s staffing gaps have affected its compliance efforts. For example, while ONRR officials told us that they recently hired two data scientist staff, they also said the office still has skills gaps. These gaps hamper ONRR’s effective oversight of royalty payments. By using OPM’s Intergovernmental Personnel Act Mobility Program, which helps agencies address mission critical skills gaps with temporary assignments, ONRR could bring in the additional skills it needs to enhance its compliance data analysis and improve its compliance efforts.
Action plan: partially met. We found that BLM’s mechanism for strategic workforce planning was a memorandum that did not address two critical needs: aligning BLM’s human capital program with emerging mission goals and developing long-term strategies for acquiring, developing, and retaining staff. BLM has taken steps to address these issues. According to BLM, as of January 2025 it had finalized a strategic workforce plan and was beginning its implementation. Implementing this plan will help BLM ensure it has the workforce it needs to manage millions of acres of public lands.
Monitoring: partially met. We previously found that BLM was not tracking data on vacancies across the agency, which limited its ability to make informed decisions about staffing. BLM has since developed a process to manually track vacancies. However, BLM officials said this process is flawed and that the agency continues to look for a better process. Completing and implementing an accurate vacancy tracking process will enable BLM to gain a complete picture of its staffing needs.
Demonstrated progress: partially met. Interior is taking steps to improve workforce planning and mitigating the effects of recent staff vacancies. For example, BLM is looking for a more accurate vacancy tracking system and an official told us it has begun implementing its strategic workforce plan. However, Interior needs to resume its efforts to ensure bureau leadership incorporates key practices for effective agency reforms before undertaking reorganization activities at Interior bureaus. Doing so will help ensure any future reorganizations are well positioned to achieve goals and that Interior’s agencies continue to deliver important services to the taxpayer.
What Remains to Be Done
Attention is needed to estimate the royalty gap, IT governance weaknesses, incomplete compliance data, strategic workforce planning, recruiting staff with critical skills, agency reforms, and financial liability related to decommissioning infrastructure to make progress in this high-risk area. Specifically, 29 high-risk recommendations to Interior remain open as of January 2025. Of these, 17 recommendations relate to royalty determination and collection, and IT, including the following:
· ONRR should assess the need to develop a consistent and complete dataset from ONNR’s multiple compliance data systems to better analyze historical compliance performance and inform its compliance strategy.
· ONRR should assess the costs and benefits of developing a plan and implementation timeline to create a royalty gap model of adequate rigor, including the collection of additional data, as needed to inform decision-making and strategic planning of royalty compliance efforts.
· Interior leadership urgently needs to address the department's IT governance weaknesses by implementing leading practices in executive-level IT governance for major IT investments.
· Interior should establish policy that meets OMB requirements and strengthen its internal controls to ensure that the cost, schedule, and performance of its IT projects are approved by appropriate milestones.
· BLM should ensure that policies are in place for completing root cause analyses and corrective action plans for projects that exceed established cost, schedule, and performance thresholds.
Interior should also implement six recommendations related to human capital management, including the following:
· Interior should ensure bureau leadership incorporates key practices for effective agency reforms prior to implementing reorganization activities at Interior bureaus.
· BLM should fully implement an agency-wide strategic workforce plan that aligns the agency's human capital program with emerging mission goals and includes long-term strategies for acquiring, developing, and retaining staff to achieve programmatic goals.
· ONRR should determine the number of staff ONRR needs to better assure it has the necessary staff with the skills to both understand ONRR’s compliance data systems and analyze its data.
Benefits
Since this area was added to our High-Risk List in 2011, Interior and its bureaus’ implementation of our recommendations have resulted in more than $160 million in financial benefits and more than 90 other benefits to the federal government, including the following:
· BLM increased royalty rates for new onshore federal oil and gas leases from 12.5 percent to 16.67 percent, effective June 2024, to match changes from the Inflation Reduction Act.[79] These changes are expected to generate revenues from onshore federal leases, better assuring a fair return for U.S. taxpayers for resources extracted from federal lands.
· BLM finalized its strategic workforce plan and began implementing it as of January 2025, according to an agency official. Implementing this strategic workforce plan will help BLM ensure it has the workforce it needs to achieve its mission and goals. When we review the plan, we will determine if it fully addresses our recommendations.
Contact Information
For additional information about this high-risk area, contact Frank Rusco, Director, Natural Resources and Environment, at (202) 512-3841 or RuscoF@gao.gov.
Managing Risks and Improving VA Health Care
The Department of Veterans Affairs (VA) needs to continue to make progress in all high-risk areas of concern to address veterans’ critical health care needs.
Why Area Is High Risk
VA operates one of the largest health care systems in the nation. It provides services to more than 9 million veterans who generally have greater health care needs than the broader population. We have identified challenges with VA’s ability to provide timely, cost-effective, and quality care. We added VA health care to the High-Risk List in 2015 with five areas of concern: (1) ambiguous policies and inconsistent processes, (2) inadequate oversight and accountability, (3) information technology (IT) challenges, (4) inadequate training for VA staff, and (5) unclear resource needs and allocation priorities.
Since our last high-risk update, VA has continued to face system-wide challenges in overseeing patient safety and access to care, hiring critical staff, and meeting future infrastructure needs. VA had a number of major modernization initiatives that were still under way, including those related to financial management and electronic health records. As it continued growing its workforce and delivering health care services to newly enrolled veterans, VA also faced challenges estimating its budget for fiscal year 2025.
VA and its Veterans Health Administration (VHA) are both responsible for making progress in this area. VHA is responsible for addressing policies, oversight, training, and resources. VHA has also been responsible for developing an action plan addressing all VA health care concerns, which it last updated in fiscal year 2024. VA leads efforts related to IT issues.
Overall Area Rating
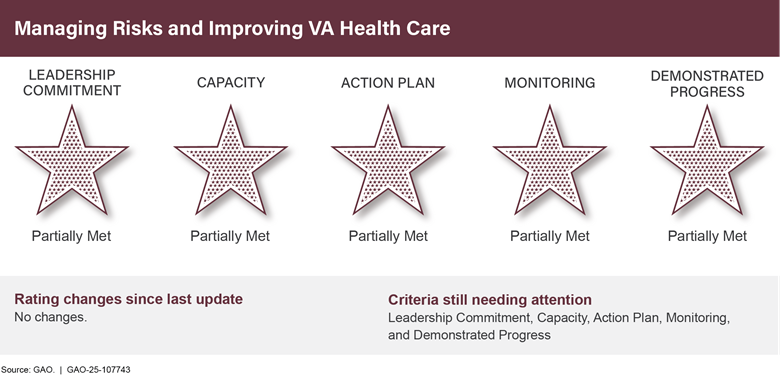
Overall ratings for all five criteria remain unchanged since 2023. The following sections present more detailed information on the five segments summarized in the overall rating. There has been further progress in two of the five areas of concern, or segments, described below and summarized in the overall rating. In the policies area, the rating for the monitoring criterion increased to met. In the training area, the rating for the capacity criterion increased to met.
Ambiguous Policies and Inconsistent Processes
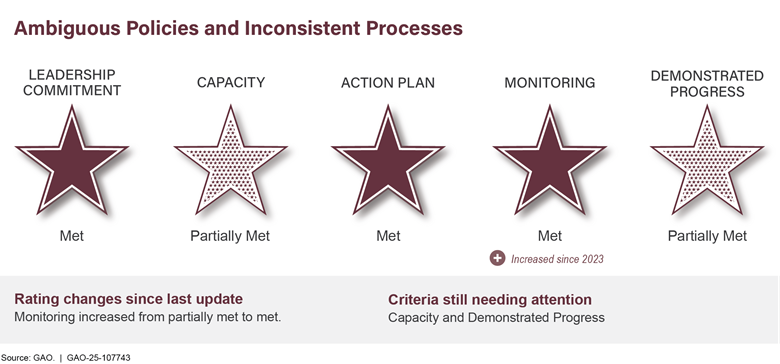
Leadership commitment: met. VHA maintained the processes set out in its March 2022 revised policy management directive. These included monitoring local medical facility policy documents to ensure consistency with national policy. In spring 2024, VHA refined the role of a key senior leadership committee it uses to obtain feedback on its policy management processes. In June 2024, VHA’s field advisory committee recommended eliminating local policy mandates stemming from 12 outdated national policies, which VHA estimates gives 60 hours of staff time back to each facility per policy.
Capacity: partially met. VHA reported that it maintained existing staff responsible for carrying out its policy management initiatives and hired additional staff, including two policy writers. In January 2024, VHA developed a policy review guide to train new staff on the policy management processes it established. VHA also had relied on contracted staff to support its capacity needs through 2024, with the goal of hiring full-time equivalent staff positions to replace these contracted staff going forward. VHA reports that its capacity will decrease beginning in fiscal year 2025 until it can carry out hiring plans to convert contracted staff to full-time equivalent staff positions.
Action plan: met. In its updated fiscal year 2024 high-risk action plan, VHA refined its road map for addressing the root causes of ambiguous policies and inconsistent processes. For example, by addressing a root cause related to unclear policy definitions, VHA reduced the number of redundant local policies by 51 percent at the end of fiscal year 2023, exceeding its goal of 25 percent by that time. By July 2024, VHA reported that it had further reduced the number of redundant policies by 54 percent.
Monitoring: increased to met. VHA is tracking metrics it identified to show progress on policy management and reporting on them at quarterly senior leadership meetings. VHA’s senior leadership committee reviews a list of high-priority policies under development and monitors progress in reducing the number of overdue national policies. For example, the committee discussed VHA’s progress in reaching its target of 30 percent overdue policies for fiscal year 2023 and recommended a target of 26 percent overdue policies for fiscal year 2024. VHA further reported that 28 percent of its policies were overdue by the end of fiscal year 2024. VHA reported it planned to maintain a target of 28 percent overdue policies for fiscal year 2025, adjusted for its decreased capacity.
Demonstrated progress: partially met. VHA has shown some progress in improving its policy management processes. In fiscal year 2023, VHA reported saving approximately 1 million labor hours by reducing redundant local policies. As a result, VHA officials said that staff would have more time to devote to direct patient care or quality improvement.
It will be important for VA to continue tracking its metrics to demonstrate that root causes are being addressed and progress is sustained over time. VA should also implement 23 policy-related recommendations. For example, we found the following:
· VHA’s regional networks and local facilities lacked a national policy for implementing the Referral Coordination Initiative that aims to streamline scheduling for specialty care appointments. VHA should define the Referral Coordination Initiative’s strategic goals, roles and responsibilities, standards for consistent implementation, and oversight and accountability.
· VHA did not always document employee background investigations as required. We recommended that VHA develop and implement policies that establish who is responsible for documenting these investigations.
· VHA is not able to ensure that all non-biological medical devices are effectively tracked to individual patients.[80] We recommended that VHA include requirements in its policies that these devices be effectively tracked to the patient level and ensure that VHA national-level offices have access to the information from the tracking systems for oversight.
Inadequate Oversight and Accountability
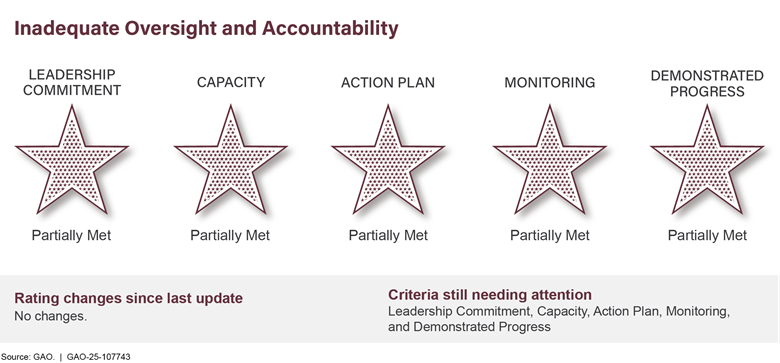
Leadership commitment: partially met. VHA has maintained stability in key leadership roles, including the Under Secretary for Health and senior VHA executives leading high-risk oversight and accountability initiatives. In August 2024, VHA updated its policy directive describing broad roles and responsibilities for oversight at each level of the organization, including its regional networks and facilities. However, VHA’s steps to implement organizational initiatives are in the early stages, such as developing an overarching oversight policy directive.
Capacity: partially met. In 2024, VHA further reorganized the structure of its oversight offices responsible for compliance, risk management, internal audit, and medical investigations. VHA reported that this reorganization would streamline its oversight. However, we recommended that VHA develop a workforce plan for its oversight offices based on evaluating the staff needed to effectively conduct compliance, risk management, internal audit, and medical investigations functions. VHA agreed with our November 2024 recommendation and said it would assess the resources and associated workloads for its oversight offices, estimated to be complete by the end of 2025.
Action plan: partially met. In its updated fiscal year 2024 action plan, VHA continued to address root causes of oversight and accountability concerns. For example, VHA described its efforts to develop a new oversight model that provides a framework for conducting and coordinating oversight of its health care system. However, VHA does not yet have a clear roadmap with performance measures to assess progress for all outcomes in this area. For example, VHA identified steps in its action plan related to risk management and internal control activities but not metrics to assess whether these activities helped hold the organization accountable.
Monitoring: partially met. VHA included some monitoring activities in its action plan, such as reporting to various governance bodies made up of VHA leadership, such as the Audit, Risk, and Compliance Committee. However, we found that this committee did not review relevant oversight findings, such as those from its medical investigations. VHA should take action to ensure the Audit, Risk, and Compliance Committee monitors relevant oversight findings and provides recommendations to VHA leadership to help inform potential system-wide improvements, as appropriate.
Demonstrated progress: partially met. VHA has begun to take important steps to improve oversight of its health care system, such as obtaining a better overview of clinical and nonclinical risks, instead of considering these risks in silos.
To continue its progress, VHA must further refine its action plan to provide a clearer roadmap that demonstrates how root causes are being addressed. VA also must continue implementing our 37 recommendations to address continued oversight and accountability issues. For example, we recommended that VHA take the following actions:
· Take steps to fully meet leading practices for managing risk, such as by comprehensively identifying risks across VHA’s health care system.
· Ensure that its Office of the Medical Inspector establish performance measures and collect relevant information to measure progress toward established performance goals. Doing so would better position the office to assess its ability to meet its mission of independently investigating health care concerns in order to monitor and improve the quality of care provided to veterans.
· Capture the reasons for community care appointment scheduling challenges, including for mental health, and use the information to address those challenges.
Information Technology Challenges

Leadership commitment: met. VA has maintained leadership stability in the Chief Information Officer position responsible for prioritizing and meeting VHA’s IT needs. As of December 2024, VA also designated senior executives in VHA’s Office of Digital Health and Strategic Investment Management with co-leading high-risk IT initiatives.
Capacity: partially met. VA has continued to provide significant funding and staff resources for electronic health record (EHR) modernization. In April 2023, VA halted future EHR system deployment to make improvements at five locations currently using the system. In March 2024, VA deployed its EHR system at a sixth location and there are over 160 remaining locations for EHR implementation. In December 2024, VA announced that it had restarted pre-deployment planning activities and selected four additional locations to deploy its EHR system in mid-2026. This effort to deploy its new EHR system remains in the early stages.
Action plan: partially met. In its updated fiscal year 2024 action plan, VA continued to address root causes of IT concerns we identified in our 2015 update. For example, VA reported that it had completed steps to address two of the three root causes related to its ability to integrate health care information electronically, such as viewing health care information from DOD’s EHR system. However, VA has not included any corrective actions, milestones, or performance measures related to deploying its new EHR system, which has cost about $12.7 billion.
Monitoring: partially met. VA has described monitoring activities in its action plan. The monitoring includes various scorecards and dashboards, such as health information exchange metrics VA reports quarterly to Congress. These metrics include the number of active VA users logged into sharing tools and the number of private-sector partners (e.g., hospitals and clinics) sharing access to their patient records. However, VA did not describe metrics for monitoring major IT initiatives, such as deployment of its new EHR system.
Demonstrated progress: partially met. VA has demonstrated some progress by halting EHR system deployment in April 2023 and subsequently revising its budget estimate. As a result, VA reduced the cost of EHR modernization by over $528 million while it made improvements to the system. To continue its progress, it will be important for VA to further refine its action plan to provide a clearer roadmap that demonstrates how root causes are being addressed.
VA also must continue implementing our 17 recommendations to address continued IT issues. For example, VA should use leading practices for change management and establish related targets for VA’s EHR Modernization program. VA should also establish user satisfaction targets to help ensure that future systems are not deployed prematurely and do not pose unnecessary risks to patient health and safety.
Inadequate Training for VA Staff

Leadership commitment: partially met. VHA maintained stability in the Chief Learning Officer position and the governance structures it previously established, such as learning councils made up of program office training staff. VHA continues to establish training processes to develop an enterprise-wide training policy by fiscal year 2026.
Capacity: increased to met. VHA established training working groups, which it reports comprise over 450 VHA staff across 16 integrated project teams. VHA stated that these teams are each responsible for specific training initiatives and have, as of fiscal year 2024, developed 11 training functions, 23 training standards, and 38 training processes. Using the work conducted with these resources, VHA plans to develop a comprehensive framework for its training program.
Action plan: met. In its updated fiscal year 2024 action plan, VHA described the progress its 16 integrated project teams made in developing different training components, such as skill-set standards. VHA continues to measure its quarterly progress toward completing each training component. VHA plans to use information from its established processes to develop outcome measures, including baseline measurement to occur in fiscal year 2025.
Monitoring: partially met. VHA continues making progress by tracking its training goals and outcomes, such as through various dashboards to monitor efforts to develop training processes. According to VA’s updated action plan, VHA will begin collecting and reporting data on training development and compliance in fiscal year 2025.
Demonstrated progress: partially met. In its action plan, VHA describes the progress VHA is making through its 16 integrated project teams, such as developing a systematic approach to competency assessment. It will be important for VHA to further develop its metrics to show how the actions taken are addressing root causes and whether progress is sustained over time. VA should also implement our two recommendations to address continued training issues.
Unclear Resource Needs and Allocation Priorities

Leadership commitment: partially met. VA maintained stability in the Chief Financial Officer position through August 2024. VHA also has taken steps to implement a number of workforce initiatives required by the Honoring our PACT Act of 2022 (PACT Act), such as developing a new approach to apply critical skills incentive payments. However, in May 2024, VA’s Office of Inspector General found that the millions of dollars in critical skill incentive payments VA awarded to senior executives at its central office lacked adequate justification and were inconsistent with the PACT Act and VA policy. The Inspector General noted that this was due, in part, to breakdowns in leadership and controls at multiple levels of VA.
Capacity: partially met. VHA took steps to increase its capacity in this area, such as by dedicating additional contracts to support a 2024 reorganization of its central office. VHA plans to further increase its capacity using additional authorities provided by Congress through the PACT Act, such as incentives for recruiting and retaining certain staff. However, VHA has faced challenges estimating its budget for 2025 in part due to higher-than-expected staffing levels needed to provide care to newly eligible veterans under the PACT Act. As a result, VHA may not have a clear picture of its capacity needs.
Action plan: partially met. In its updated action plan, VHA made improvements for how it will address certain resource-related concerns. For example, VHA set targets through fiscal year 2025 to improve human resources service delivery of various functions, such as personnel security. However, not all sections of VA’s action plan are complete. For example, VHA’s financial management modernization effort is under development and, as a result, it does not yet have associated timelines and performance measures.
Monitoring: partially met. VHA continued the monitoring activities in its action plan and reported on its progress. For example, in 2024, VHA used data to measure “time-to-fill” metrics for hiring staff and published a dashboard with trends across its regional networks. However, VHA does not yet have monitoring activities that can measure progress in all outcomes for the resources area of concern.
Demonstrated progress: partially met. VHA provided a clearer roadmap for how it will address resource-related concerns, such as implementing workforce initiatives required by the PACT Act. However, VHA needs to further refine its action plan to address root causes in light of significant resource-related concerns that factored into its budget estimation challenges for 2025. For example, VHA now estimates that community care will grow by 16.5 percent in fiscal year 2025 to meet anticipated veterans’ needs, compared to the estimated 12 percent growth included in its fiscal year 2025 budget submission. Figure 48 depicts the model VHA uses to estimate the resources needed to provide its health care services, the Enrollee Health Care Projection Model.
Figure 48: Basic Components of the Department of Veterans Affairs’ (VA) Enrollee Health Care Projection Model
Note: The Enrollee Health Care Projection Model makes a number of complex adjustments to projections for VA’s health care services to account for the characteristics of VA health care and enrolled veterans. For example, the model includes adjustments to account for reliance on VA health care—that is, the extent to which enrolled veterans will choose to access health care services through VA as opposed to other health care services. Unit costs are the costs to VA of providing a unit of service, such as a 30-day supply of a prescription or a day of care at a medical facility.
VA should also continue implementing our 23 recommendations to address resource allocation issues. For example, VA should enhance its analytical modeling capacity to better enable VHA to estimate the funding needed to respond to potential future health emergencies, such as pandemics, natural disasters, and terrorist acts.
What Remains to Be Done
As of January 2025, 102 recommendations related to this high-risk area remained open. Additional progress could be made if VA were to implement open recommendations related to our high-risk area concerns, including those that would help improve VHA’s ability to provide timely, cost-effective, and quality care. For example, VA should
· assess the impact of data limitations affecting its veteran population model and take steps to address those limitations for veterans located in U.S. territories and freely associated states, as well as clearly communicate the appropriate uses of its new database capabilities that generate utilization and timeliness of care data by veteran location;
· establish a metric for its Veterans Community Care Program that will permit VHA to monitor whether veterans are receiving community care within time frames comparable to those at VA facilities;
· implement a systematic process to compile and review data on maternal care coordinators’ screening of veterans for mental health conditions on an ongoing basis;
· identify and use additional performance metrics to determine the extent to which the department's IT systems support performance of VHA's mission and ensure that unmet IT needs identified by key program areas—pharmacy benefits management, scheduling, and community care—are addressed appropriately;
· develop a process that would accurately count all physicians providing care to veterans at each medical center to help ensure VA’s workforce planning process sufficiently addresses any gaps in physician staffing;
· improve the data, planning, and communication for modernizing and realigning facility infrastructure across its 96 health care markets nationwide; and
· collect and assess information on veterans' use of the mileage reimbursement benefit by subpopulation (e.g., rural veterans) and collect additional information on veterans' travel costs and assess costs by subpopulations to inform resource decisions.
Benefits
Since we added this area to the list in 2015, financial benefits to the federal government due to progress in this high-risk area totaled more than $1 billion, largely due to reduced VA expenditures from pausing the deployment of its new EHR system. In addition, there were more than 200 other benefits. For example:
· VA established a timeliness standard for the average number of days within which veterans' medical appointments with VA facility providers should occur. Specifically, the average number of days for a new patient appointment to occur from the date of the request should be no more than 20 days for primary care and mental health and 28 days for specialty care. This will help ensure that veterans have more timely access to care.
· VA updated its funding guidelines to target veterans with serious mental illnesses that live in rural areas to ensure that funding and programs better consider where veterans live. These efforts will help ensure veterans in rural areas have access to the mental health care they need.
· VA developed a plan to ensure its data system for monitoring state veterans homes had capabilities to aggregate and analyze data by multiple measures, including by state and home, and across survey years. This will help VA be more efficient in performing oversight of state veterans homes, which provide nursing home care to roughly 14,500 veterans.
Contact Information
For additional information about this high-risk area, contact Sharon Silas, Director, Health Care, at (202) 512-7114 or SilasS@gao.gov.
Medicare Program and Improper Payments
The Centers for Medicare & Medicaid Services (CMS) has taken some action to reduce improper payments but needs to do more to address Medicare’s financial and oversight challenges.
Why Area Is High Risk
Medicare—which is administered and overseen by CMS—was designated as high risk in 1990 due to its size, complexity, and effect on the federal budget and health care sector, and susceptibility to mismanagement and improper payments.
The Medicare program is complex, with more than 1.4 million providers and more than 20 different payment systems. In fiscal year 2024, the Medicare program spent around $1 trillion—about 15 percent of all federal spending—to provide health care services for approximately 68 million beneficiaries. Spending is expected to increase significantly over the next decade as the U.S. population ages and more individuals begin receiving Medicare benefits.
Medicare also faces a significant risk for improper payments—those made in an incorrect amount, that should not have been made at all, or that lack sufficient documentation—which reached an estimated $54.3 billion in fiscal year 2024.
Area Rating
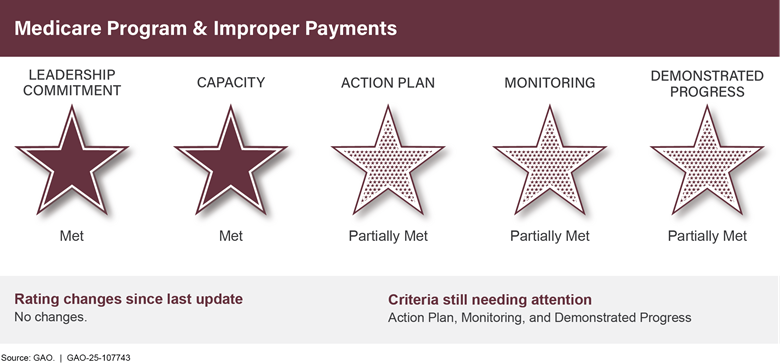
Overall ratings for all five criteria remain unchanged since 2023. The following sections present more detailed information about Medicare improper payments plus three additional broad segments: (1) payments, provider incentives, and program management under Medicare fee-for-service; (2) Medicare Advantage and other Medicare health plans; and (3) design and oversight of the Medicare program and the effects on beneficiaries.
Although we are rating Medicare’s progress on improper payments, we continue to not rate CMS’s progress for the three other segments, which cover the entirety of the Medicare program, for the following two reasons:
· Many vital financial and regulatory factors are outside of the agency’s control due to frequent legislative updates to Medicare provider payments and other policies; and
· The Medicare program is in a profound state of transition from the following:
· a payment system that rewards providers based on the volume and complexity of health care services they deliver to one that ties payments to the quality and efficiency of care; and
· a program where beneficiaries were primarily enrolled in the fee-for-service program to one where, as of 2024, over half of beneficiaries (54 percent) are enrolled in Medicare Advantage plans, which are private plans under contract with CMS to provide health care coverage to Medicare beneficiaries.
Medicare Improper Payments
Leadership commitment: met. CMS has continued to demonstrate the leadership commitment needed to ensure the integrity of the Medicare program. For example, one of the six pillars of CMS’s 2023 strategic plan, called “protect programs,” includes program integrity activities intended to address Medicare improper payments. In 2023, CMS also finalized rules for identifying and recovering excess payments—instances where Medicare pays more than they should—made to Medicare Advantage plans.[81]
Capacity: met. CMS maintained its met rating for capacity by increasing resources for its Center for Program Integrity (CPI)—CMS’s centralized entity for Medicare and Medicaid program integrity issues. For example, CPI’s full-time equivalent positions increased from 177 in fiscal year 2011 to about 556 in fiscal year 2024, according to CMS officials. CPI employs its Fraud Prevention System—a data analytic system—to screen fee-for-service claims prior to payment to help identify and prevent improper and potentially fraudulent payments. CMS estimated its program integrity activities saved Medicare $14.9 billion in fiscal year 2023.
Action plan: partially met. CMS continues to identify and report progress on corrective actions related to Medicare improper payments. CMS reported this progress in the Department of Health and Human Services fiscal year 2024 Agency Financial Report, and CMS officials said the report reflected the agency’s record on its action plan. However, more work needs to be done to fully meet this criterion. For example, although the improper payment rate for hospital outpatient claims decreased from 5.2 percent in fiscal year 2023 to 3.2 percent in fiscal year 2024, the rate for skilled nursing facility claims increased from 13.8 percent to 17.2 percent.
Also, while the annual financial report includes targets for reducing Medicare improper payments and highlights corrective actions taken to address root causes of payment errors, it does not identify clear metrics to assess progress or time frames and resources needed to implement corrective actions.
Monitoring: partially met. CMS continues to make progress in monitoring some areas. For example, in November 2023, CMS finalized regulations to conduct fingerprint-based criminal background checks when revalidating the enrollment of providers who pose a high risk of fraud, waste, and abuse.[82]
However, CMS needs to prioritize and implement provider enrollment revalidations of moderate- and high-risk provider types who enrolled under a waiver during the COVID-19 pandemic. CMS also should take steps to routinely assess how variations in the documentation requirements between Medicare and Medicaid may affect estimates of improper payment rates. Further, CMS needs to improve the timeliness of Medicare Advantage plan audits to recover significant improper payments.
Demonstrated progress: partially met. Estimated improper payment rates for Medicare fee-for-service increased slightly by three-tenths of a percentage point from fiscal years 2023 to 2024, to 7.7 percent (see fig. 49). For Medicare Advantage in fiscal year 2024, CMS reported a slight decrease by about four-tenths of a percentage point to 5.6 percent. The improper payment rate for Medicare Part D prescription drug coverage remained unchanged from 2023 to 2024 at 3.7 percent. In total, Medicare improper payments were estimated to be about $54.3 billion in fiscal year 2024. Continued emphasis on reducing improper payments in Medicare is critical to safeguarding federal funds. As of January 2025, we have seven open recommendations related to Medicare improper payments. For example, we recommended that CMS should institute a process to routinely assess, and take steps to ensure, as appropriate, that Medicare documentation requirements are necessary and effective at demonstrating compliance with coverage policies while appropriately addressing program risks.
Figure 49: Medicare Fee-for-Service, Medicare Advantage, and Medicare Part D Improper Payment Rates, Fiscal Years 2014–2024
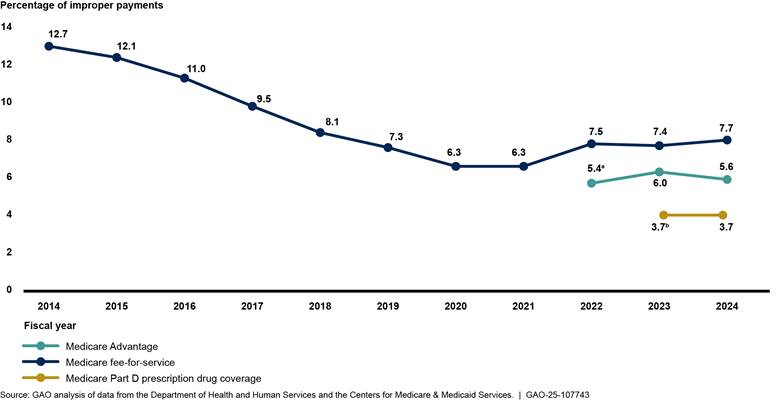
aAccording to the Centers for Medicare & Medicaid Services (CMS), the agency refined its Medicare Advantage improper payment rate methodology for fiscal year 2022 and, as a result, it should not be compared with prior years.
bAccording to CMS, the agency implemented numerous methodology changes in the fiscal year 2023 reporting period and, as a result, it should not be compared with prior years.
Payments, Provider Incentives, and Program Management under Medicare Fee-for-Service
CMS continues to move toward full implementation of its value-based payment systems in its Medicare fee-for-service program. The value-based payment systems are intended to reward health care providers for resource use and quality, rather than volume of services. It will be important for the agency to pay providers appropriately and to use reliable quality measures and methodological approaches, as highlighted in the following two areas.
Hospital-Physician Consolidation. We have reported that after hospitals acquire a practice or hire physicians to work as salaried employees—a financial arrangement known as vertical consolidation—certain physician services can be classified as being performed in hospital outpatient departments and receive higher payment rates. Such excess payments are inconsistent with Medicare's role as an efficient purchaser. We recommended that Congress direct CMS to equalize payments between hospital outpatient departments and physician offices to lower Medicare costs. While Congress has taken actions to limit certain hospital outpatient departments from billing at higher rates, Medicare could realize additional savings if Congress applied this limitation to additional outpatient departments and services.[83] For example, the Congressional Budget Office estimated that paying hospital outpatient departments the same as physician offices would save almost $157 billion from 2025 through 2034.
Merit-Based Incentive Payment System. Under Medicare’s Merit-Based Incentive Payment System, doctors and other providers’ Medicare fee-for-service payments may change based on such factors as the cost and quality of care provided. We found that, from 2017 to 2019, more than 90 percent of providers earned a small increase (less than 2 percent) to their Medicare payments. Providers we interviewed noted some strengths and challenges of the incentive payment system. For example, some said certain design aspects of the system encouraged the participation of providers in certain specialties or in smaller practices. Others raised concerns that the performance feedback given to providers was not timely or meaningful.
Medicare Advantage and Other Medicare Health Plans
As enrollment in the Medicare Advantage program continues to increase and exceeds half of all eligible Medicare beneficiaries, it is important for CMS to pay plans accurately. Further, it should collect and analyze data necessary to oversee the program, as highlighted by the following areas:
Medicare Advantage plan payment adjustments. The limitations of CMS’s adjustments to Medicare Advantage plan payment rates—which account for differences between fee-for-service and Medicare Advantage providers’ coding of medical diagnoses—resulted in an estimated $50 billion in excess payments in 2024, according to the Medicare Payment Advisory Commission. We recommended that CMS improve the accuracy of these adjustments by, for example, identifying and accounting for all years of coding differences that could affect the payments to Medicare Advantage plans in a given year.
Encounter data. CMS used encounter data—claims-like data submitted by the sponsors of Medicare Advantage plans—in its methodology for risk adjusting payments to Medicare Advantage plans. Yet, it has not fully validated encounter data for completeness and accuracy, as we recommended. Specifically, CMS has not yet demonstrated that it verifies encounter data by systematically reviewing medical records in a timely manner.
Medicare Part D rebates. CMS does not use rebate data provided by pharmaceutical manufactures to Part D plan sponsors to oversee plan formularies, which are lists of covered drugs. CMS should monitor the effect of rebates on formulary design by plan sponsors and on Medicare and beneficiary spending.
Design and Oversight of the Medicare Program and the Effects on Beneficiaries
Medicare fee-for-service’s benefit design and CMS’s oversight of it affect beneficiaries’ out-of-pocket costs. Medicare fee-for-service beneficiary premiums for calendar year 2025 increased and are expected to continue increasing in the long term. Medicare premiums are based, in part, on changes to federal Medicare spending. In 2024, the Medicare Trustees estimated that federal Medicare spending will grow at a faster rate than workers’ earnings and the economy overall in the long term. This could significantly burden Medicare beneficiaries facing these higher premiums.
CMS must also ensure the quality and safety of care that beneficiaries receive. As noted below, CMS has made progress in certain areas, but we identified gaps in oversight of other areas.
Skilled nursing facilities. CMS should report more information on its Care Compare website, a web-based tool that allows consumers to compare health care providers. CMS has made progress—for example, it included information on weekend decreases in nurse staffing levels along with minimum staffing thresholds needed to ensure quality of care as we recommended. This improves beneficiaries’ ability to make informed choices when choosing a skilled nursing facility for their care.
Hospice provider oversight. CMS’s oversight of hospice providers can be improved. For example, it did not complete standard surveys—inspections to ensure compliance with Medicare’s quality standards—of all hospices or make hospice survey results publicly available in a prominent, easily accessible, and readily understandable manner. We recommended that CMS complete these surveys and publicly disseminate survey results. We also recommended that CMS address gaps in requirements for reporting allegations of abuse or neglect for individuals in hospice care.
What Remains to Be Done
As of January 2025, we have 64 open recommendations for CMS to strengthen aspects of the Medicare program. Additional progress could be made if CMS were to implement open recommendations related to validating Medicare Advantage encounter data for completeness and accuracy, improving adjustments to Medicare Advantage plan payment rates, assessing documentation requirements, and ensuring the quality of care that beneficiaries receive. For example, the Administrator of CMS should:
· seek legislative authority to permit payment for recovery auditors to conduct prepayment claims reviews to deny improper claims and prevent overpayments consistent with CMS’s goal to pay claims correctly the first time;
· complete all of the steps necessary to validate Medicare Advantage encounter data, including systematically reviewing medical records in a timely manner;
· take steps to improve the accuracy of Medicare Advantage plan payment adjustments to reflect coding differences between fee-for-service and Medicare Advantage providers’ coding of medical diagnoses by, for example, including the most current data available and accounting for additional beneficiary characteristics such as sex and health status;
· enhance the timeliness of audits to identify and recover improper payments to Medicare Advantage organizations. As of January 2025, CMS had not yet released findings for Medicare Advantage plan audits for 2018 or subsequent years to recover improper payments;
· monitor the effect of rebates on Part D plan sponsor formulary design and on Medicare and beneficiary spending;
· require, for individuals in hospice care, immediate reporting of all abuse and neglect allegations involving all perpetrators to the hospice administrator, a state survey agency, and other appropriate authorities;
· comprehensively assess the quality of Medicare services, including audio-only services, delivered using telehealth during the public health emergency;
· prioritize and implement provider enrollment revalidations of moderate- and high-risk provider types who enrolled under a waiver during the COVID-19 pandemic; and
· assess and ensure the documentation requirements for Medicare and Medicaid are necessary and effective at demonstrating compliance with coverage policies while appropriately addressing program risk.
Congressional Actions Needed
There are six open recommendations for congressional consideration as of January 2025, including that Congress consider:
· Equalizing payment rates that are higher for certain types of services provided in hospital outpatient departments rather than physicians’ offices. Fully addressing this matter for all hospital outpatient departments could yield billions of dollars in savings to the Medicare program.
· Directing the Secretary of Health and Human Services to implement additional reductions in payments to skilled nursing facilities that generate Medicare spending on potentially preventable critical incidents, such as hospital readmissions and emergency room visits. We estimated that in 2018 Medicare spent over $5 billion on critical incidents occurring within 30 days of the skilled nursing facility admission. Under current law, CMS is directed to make reductions of up to 2 percent to certain skilled nursing facilities’ payments to incentivize them to improve care.[84] However, additional reductions are not authorized. Authorizing additional reductions could reduce the billions in spending on potentially preventable critical incidents or the patient harm that can occur from them.
Benefits
CMS actions to implement our recommendations and Congress’s actions in this area have resulted in more than $72.1 billion in financial benefits and more than 200 other benefits over the last 19 years. For example:
· In February 2024, CMS issued guidance to Medicare Advantage plans clarifying that utilization of supplemental benefits, such as vision and dental, are required to be reported. This will allow CMS to collect more complete information on enrollees' use of supplemental benefits.
· In May 2024, CMS issued guidance for surveyors to assist and promote consistency in applying remedies for hospices that are determined to be out of compliance with Medicare requirements as we recommended. Because of this, the agency is fully prepared to carry out its obligation to ensure hospices that are out of compliance with quality standards face appropriate consequences.
· In November 2019, CMS issued a final rule with comment period that completed the phase in of reduced payments for specific hospital outpatient services to more closely align with the payments for the same services provided in physician practices, which our previous work supports.[85] CMS estimated the change saved the Medicare program about $864 million in fiscal year 2023.
· In May 2024, CMS established minimum nurse staffing standards in long-term care facilities, including skilled nursing facilities, which addressed our previous recommendation.[86] These staffing standards were intended to, among other things, reduce the risk of nursing home residents receiving unsafe and low-quality care. CMS will display determinations of facility compliance with the minimum staffing standards on its Care Compare website. As a result, beneficiaries have the improved opportunity to receive safe and quality care and make more informed choices when choosing a facility for their care.
Contact Information
For additional information about this high-risk area, contact Leslie V. Gordon, Director, Health Care, at (202) 512-7114 or GordonLV@gao.gov.
Modernizing the U.S. Financial Regulatory System
Financial regulators need to strengthen oversight of financial institutions and systemic risk. Congress may want to consider options to address regulatory fragmentation and gaps that hamper the financial regulatory system.
Why Area Is High Risk
The U.S. financial regulatory structure remains complex, with responsibilities fragmented among multiple regulators that have overlapping authorities.
We added this area to the High-Risk List because of weaknesses in the financial regulatory system highlighted during the 2007–2009 financial crisis. In particular, no single regulator was tasked with monitoring and assessing risks posed by the activities of large, interconnected financial companies across the entire financial system. Additionally, entities that played key roles in the financial markets were not subject to sufficiently comprehensive oversight by the regulators. Further, the regulatory system did not effectively provide consumers and investors with key protections from new, complex financial products.
Recent events and the rapid adoption of emerging technologies in the marketplace have highlighted continued challenges in the regulatory system. In March 2023, bank failures and regulators’ emergency responses raised concerns about the effectiveness of bank supervision. Further, financial products powered by blockchain and other innovative technologies have tested regulators’ abilities to appropriately oversee the use of these products and address their risks to the financial system.
Area Rating
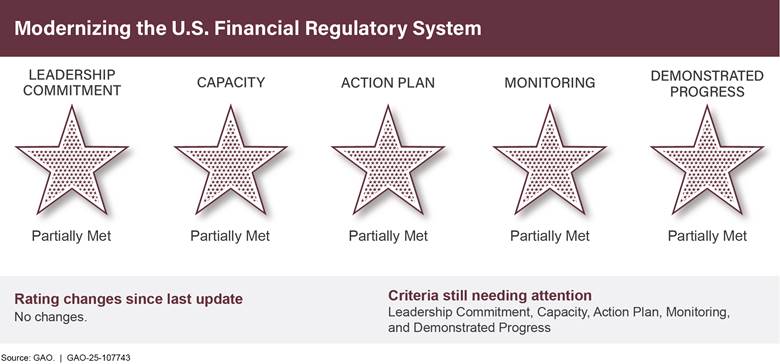
Since our 2023 High-Risk Report, ratings for all five high-risk criteria remain unchanged. Actions are needed by financial regulators and the Congress to address this high-risk area.
Leadership commitment: partially met. The Dodd-Frank Wall Street Reform and Consumer Protection Act (Dodd-Frank Act) was enacted in July 2010 and included provisions to better position the financial regulatory system to identify and address financial stability risks.[87] Federal financial regulators have finalized rules to reform the system by implementing the act’s rulemaking requirements. However, the act generally left the financial regulatory structure unchanged, maintaining a system with multiple regulators that have fragmented responsibilities and overlapping authorities. We found that this fragmentation and overlap in the structure have created inefficiencies in regulatory processes and inconsistencies in how regulators oversee similar types of institutions.
As part of our work reviewing the regulators’ supervision of banks that failed in March 2023, we found that the Board of Governors of the Federal Reserve System (Federal Reserve) had not finalized a Dodd-Frank Act rulemaking to establish early remediation standards for certain financial institutions.[88] Such standards would require the Federal Reserve to intervene quickly, rather than wait until a financial institution is about to fail. Finalizing the rulemaking could help lessen the risk of insolvency among certain institutions and protect financial stability.
We also found that the Federal Reserve’s unclear procedures to escalate supervisory concerns could have contributed to delays in implementing corrective actions at one of the banks that failed in March 2023. Further, the Federal Deposit Insurance Corporation lacked a process for managers to formally consult the entire examination team and other relevant stakeholders when they decide whether to escalate concerns and take more forceful supervisory actions against a bank to correct identified problems. As a result, escalation decisions may not be fully independent and grounded in evidence gathered during examinations.
Capacity: partially met. The Dodd-Frank Act created the Financial Stability Oversight Council (FSOC) to help identify risks and respond to emerging threats to the stability of the nation’s financial system. See fig. 50 below for FSOC’s membership. The act also included other provisions to increase the financial regulatory system’s capacity to identify and address risks to the nation’s financial stability, such as stress testing for large financial institutions. Most of these reforms have been implemented.
We have repeatedly reported that FSOC’s legal authorities are limited with respect to risks that arise from financial activities spanning multiple entities. Because FSOC recommendations are nonbinding, it can recommend but not compel regulatory action, even with broad consensus among its members. As a result, FSOC may lack the tools needed to comprehensively respond to systemic risks.
We also reported on gaps in federal financial regulators’ oversight authorities over certain crypto assets and trading platforms. These gaps limit regulators’ abilities to address risks related to investor and consumer protection, market integrity, and financial stability.
Action plan: partially met. FSOC’s annual report has served as its key accountability document. Each report discusses the progress regulators have made in implementing reforms, identifies newly emerging threats, and includes recommendations to address them.
Federal banking regulators may have to conduct regulatory analyses as part of their rulemakings and are required to conduct certain retrospective analyses, which can help agencies understand how regulations have worked and whether changes are warranted. We found that federal financial regulators’ policies and procedures did not always reflect leading practices for regulatory analysis, such as including requirements for a benefit-cost assessment or a retrospective review. These practices would help regulators determine the extent to which a rule achieved its intended effects and help ensure the safety and soundness of the U.S. financial system.
Monitoring: partially met. FSOC monitors and reports on potential emerging threats to financial stability. In addition, in 2018, the Federal Reserve began publishing an annual financial stability report that includes its assessment of the U.S. financial system. The Federal Reserve’s stress test programs have also played a key role in supervisory efforts to evaluate and maintain financial stability.
However, we found that FSOC does not regularly assess the effectiveness of its policies and governance structure, potentially missing opportunities to improve its response to systemic risks. FSOC should conduct regular and comprehensive reviews of its policies and procedures, as we recommend, to determine whether they are sufficient to respond to financial stability threats, particularly in light of the bank failures that occurred in March 2023.
Demonstrated progress: partially met. The agencies and oversight bodies created under the Dodd-Frank Act have taken actions toward carrying out their missions and coordinating efforts. For example, in March 2024, the Federal Reserve took steps to improve its model risk management and help ensure that decisions based on supervisory stress tests would be based on more complete information.
Further, in March 2023, federal financial regulators formalized coordination efforts to address risks posed by crypto assets and other blockchain-based products and services. In particular, these regulators have used FSOC’s Digital Asset Working Group to identify risks and promote information sharing. As of January 2025, the regulators have yet to jointly develop processes for responding to those risks in a timely manner, particularly those that span multiple regulatory jurisdictions.
What Remains to Be Done
Attention by federal financial regulators is needed in several areas, including improving procedures for escalating supervisory concerns, incorporating leading practices for regulatory analysis, and jointly developing processes for responding to risks posed by crypto assets and other blockchain-based products and services. Specifically, there are 23 open recommendations to various regulators as of January 2025 to make progress in this high-risk area. Examples include the following:
· FSOC should establish a process for conducting regular and comprehensive reviews of its effectiveness, including the extent to which its policies, procedures, and governance structure facilitate its ability to respond to financial stability risks.
· The Federal Reserve and the Office of the Comptroller of the Currency should develop and implement policies and procedures for systematically performing retrospective reviews of regulations.
· The Federal Reserve should revise its procedures on when to escalate supervisory concerns to informal or formal enforcement actions to be clearer and more specific and to include measurable criteria.
· The Federal Reserve should issue a regulation to implement remaining open portions of section 166 of the Dodd-Frank Act to establish early remediation standards for certain financial institutions.
· The Federal Deposit Insurance Corporation should establish procedures, such as vetting meetings, to ensure that managers formally consult with the examination team and relevant stakeholders before making substantive changes to examination findings.
· The Consumer Financial Protection Bureau, Commodity Futures Trading Commission, Federal Deposit Insurance Corporation, Federal Reserve, National Credit Union Administration, Office of the Comptroller of the Currency, and Securities and Exchange Commission should jointly establish or adapt an existing formal coordination mechanism for collectively identifying risks posed by blockchain-related products and services and formulating a timely regulatory response.
Congressional Actions Needed
As of January 2025, five matters for congressional consideration remain open. Examples include the following:
· Congress should consider whether legislative changes are necessary to align FSOC’s authorities with its mission to respond to systematic risks. Congress could do so by changing FSOC’s mission, its authorities, or both, or the missions and authorities of one or more of the FSOC member agencies.
· Congress should consider legislation that designates a federal regulator to provide for comprehensive regulatory oversight of certain crypto asset markets, including requirements intended to protect investors from fraud and market manipulation and to promote market integrity.
· Congress should consider requiring the adoption of noncapital triggers that require early and forceful regulatory actions tied to unsafe banking practices before they impair capital, such as by amending the Federal Deposit Insurance Act to incorporate noncapital triggers into the prompt corrective action framework.
Benefits
There have been more than 50 benefits to the federal government due to progress in this high-risk area since we added it to our list in 2009. These include improvements to
· collaboration among FSOC and its member agencies on identifying and addressing threats to financial stability;
· the implementation of key financial stability reforms under the Dodd-Frank Act, such as stress testing for large financial institutions; and
· financial regulators’ efforts to assess the effectiveness of Dodd-Frank Act reforms, including steps taken to strengthen their regulatory analyses.
Contact Information
For additional information about this high-risk area, contact Michael Clements, Director, Financial Markets and Community Investment, at (202) 512-8678 or ClementsM@gao.gov.
NASA Acquisition Management
The National Aeronautics and Space Administration (NASA) needs to continue making progress on reducing acquisition risk and improving project cost and schedule performance for its most expensive and complex projects.
Why Area Is High Risk
NASA plans to invest billions of dollars in the coming years to explore space and conduct aeronautics research, among other things. We designated NASA’s acquisition management as high risk in 1990 due to NASA’s history of persistent cost growth and schedule delays in most major projects, which are programs or projects with estimated life-cycle costs greater than $250 million.
Area Rating
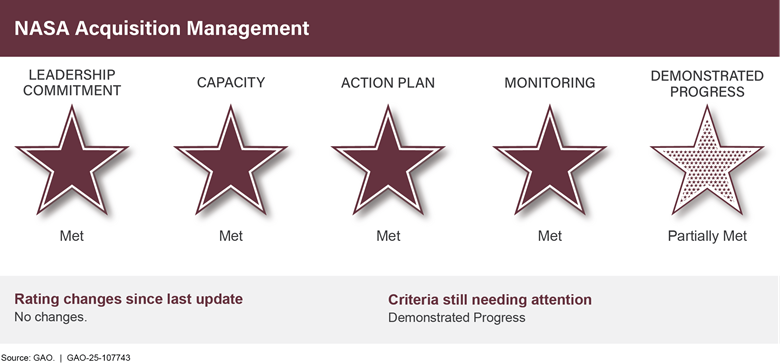
Overall ratings for all five criteria remain unchanged since 2023.
NASA has implemented efforts to improve the oversight and transparency of its major projects’ costs and schedules, including the long-term costs of human space exploration programs. However, NASA continues to face challenges controlling cost growth and schedule delays for its category 1 projects, which exceed $2 billion in life-cycle costs. These include projects needed to conduct the Artemis missions that will return astronauts to the moon, build a sustainable lunar presence, and ultimately bring humans to Mars. Category 1 projects have an outsized effect on NASA’s portfolio if they experience cost and schedule growth.
Leadership commitment: met. NASA leadership continues to demonstrate its commitment to improving acquisition management by improving oversight of its projects. For example, NASA updated policy and guidance to clarify that agency decision-makers should review the results of an analysis of alternatives prior to making acquisition strategy decisions and before a program manager is authorized to begin planning a new program.
NASA also established cost and schedule baselines for several Artemis projects. These baselines are the commitments against which NASA measures project performance. They also provide decision-makers transparency into costs and enable them to assess long-term affordability and progress. The agency’s new project baselines are for capability upgrades, such as the upgraded version of the Space Launch System rocket and the structure used to launch the rocket, the Mobile Launcher 2, and the first two pieces of the Gateway, a small space station planned for lunar orbit. NASA officials said that they plan to focus on tracking how the newly established Moon to Mars program manages those baselines and project performance.
Capacity: met. NASA continues to demonstrate its capacity to reduce acquisition risk. This includes taking steps to improve independent assessments of major projects and determine whether to engage review boards at additional points in project life cycles. Independent assessments examine project performance and readiness to proceed to the next phase of development. NASA plans to further develop independent assessment processes and execution and officials said they also plan to measure the outcomes stemming from prior improvements.
NASA has used independent assessments to try to improve project outcomes. For example, NASA conducted an additional independent review of Mars Sample Return, a category 1 project with a potential life-cycle cost of $8 billion to $11 billion that is facing funding, schedule, technical, and architectural challenges. Following the review, NASA is investigating options to lower costs and reduce mission complexity and risk prior to setting the project’s cost and schedule baselines.
Action plan: met. NASA continues to update and implement a corrective action plan. As of October 2024, the agency completed or closed three of six 2022 plan initiatives. In October 2024, NASA updated its action plan and began five new initiatives. Three of these new initiatives build on prior efforts to improve scheduling and increase insight into use of firm-fixed-price contracts and their outcomes.
Monitoring: met. NASA continues to monitor progress against its corrective action plan. This process includes tracking and briefing senior leaders on the progress made on action plan initiatives. It also reports progress against its other cost and schedule performance metrics to us and NASA senior leadership semiannually.
Demonstrated progress: partially met. NASA’s cumulative cost performance improved since our 2023 update. This is largely because NASA launched or demonstrated the initial capabilities of some large category 1 projects—the James Webb Space Telescope, Space Launch System, and Exploration Ground Systems—and therefore they left the project portfolio. For example, in June 2024, we found that cumulative cost overruns decreased from approximately $12 billion in 2022 to $7.6 billion and $4.4 billion in 2023 and 2024, respectively.
Despite this progress, category 1 projects continue to drive NASA’s cumulative cost performance. In 2024, they accounted for 81 percent of the portfolio’s total cumulative baseline overrun. One of these projects, the Orion Multi-Purpose Crew Vehicle, accounted for 65 percent of the portfolio’s total cumulative baseline cost overrun.
NASA officials described the agency’s overall goal of 70 percent of projects performing within their development cost and schedule baselines. As of early 2024, NASA reported that 29 percent of all major projects were within their original cost baselines. Later in the year, it subsequently reported an improvement to 63 percent of major projects performing within their cost baselines. NASA attributed the improvement to changes to the portfolio—removing some projects with cost growth because they were canceled and adding several new projects—and to no change in performance for the remaining projects.
To assess progress against its goal, NASA uses a metric that is based on its policy of setting baselines for projects with a 70 percent confidence of achieving joint cost and schedule agency-level commitments. NASA officials said this metric might be too strict. For example, a project that only had a small amount of cost growth might be considered a success but would not count toward this goal. While the metric may be difficult to achieve, it provides a measurement as to whether NASA is demonstrating progress over time.
NASA has eight category 1 projects in development. Four of them were executing within their cost baseline and five were within their schedule baseline as of mid-2024 (see fig. 51).
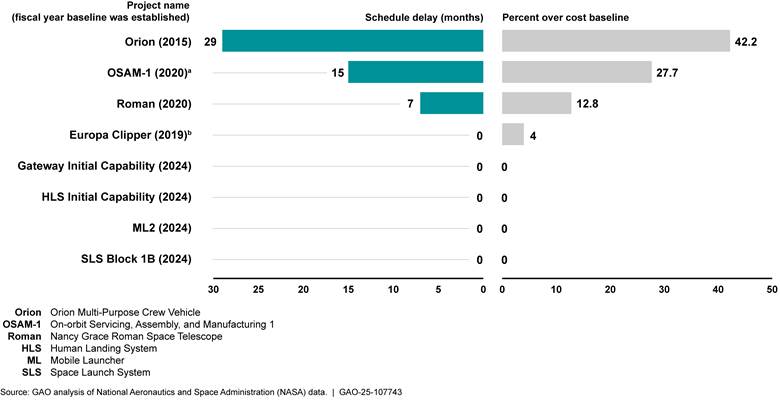
Note: Data are as of July 2024. We excluded the Commercial Crew Program, which is also a category 1 project, from this analysis because it has a tailored project life cycle and project management requirements and did not establish a baseline.
aNASA announced in March 2024 that it planned to discontinue OSAM-1 due to continued technical, cost, and schedule challenges, among other reasons. As of October 1, 2024, NASA was in the process of shutting down the project.
bThe Europa Clipper project launched 11 months ahead of its schedule baseline in October 2024.
Artemis-related category 1 projects are positioned to shape NASA’s cumulative cost performance in the coming years. For example, NASA established cost and schedule baselines for four new Artemis-related projects between December 2023 and June 2024. We also found that each of these new Artemis projects have experienced challenges. Further, all four are in, or are approaching, the final design and fabrication phase of the development process, which often reveals unforeseen challenges leading to cost growth and schedule delays. Controlling costs for these projects over the next 2 years could help NASA demonstrate sustained improvement for the portfolio and get closer to its goal.
According to NASA senior leaders, corrective action plan initiatives and other agency actions should help control project cost and schedule growth over time. In 2024, NASA’s Chief Acquisition Officer identified risk management—particularly during projects’ early stages—as an agency priority to strengthen acquisition efforts and outcomes.
NASA subsequently began several efforts in support of this priority. For example, the agency plans to generate more realistic cost and schedule estimates while projects are still early in their life cycles, particularly for category 1 projects. NASA expects that this will improve its ability to make risk-informed decisions prior to starting a project and determining an acquisition strategy.
NASA also took actions to try to control cost and schedule growth for individual projects. For example, senior NASA officials said they delayed setting the baseline for the SLS Block 1B project until the agency was more confident that requirements for the project would not change. As a result, they are confident they can execute the project within the established cost and schedule baseline commitments.
What Remains to Be Done
NASA will need to continue to identify ways to improve management of the most expensive and complex major projects, such as category 1 projects. This will be critically important as NASA plans to spend a total of more than $31 billion on five category 1 projects to support its goal to return humans to the lunar surface.
Specifically, 12 recommendations remain open as of January 2025. To reduce acquisition risk, NASA should improve
· transparency into Artemis mission and major project costs, including by establishing a life-cycle cost estimate for the Artemis III mission and measuring production costs for the Space Launch System program; and
· management of its lunar missions, including documenting plans describing the lunar Gateway program’s mass reduction approach and priorities for key trade-off decisions and completing a schedule risk analysis for Exploration Ground Systems and Mobile Launcher 2 ahead of Artemis IV.
Benefits
Financial benefits since this area was added to the list in 1990 have totaled more than $10 billion. There were also more than 70 other benefits. For example:
· In spring 2023, NASA provided a rationale for its current lunar architecture and lunar programs. It also conducted two Architecture Concept Reviews to map its high-level Moon to Mars exploration goals to the elements that are needed to achieve them and plans to hold future reviews on an annual basis.
· NASA improved schedule management and workforce planning guidance for the Artemis missions, which are planned through the 2030s. Schedule management guidance for these multiprogram missions will help ensure that senior NASA leaders have quality, risk-informed schedule information for decision-making.
Contact Information
For additional information about this high-risk area, contact William Russell, Director, Contracting and National Security Acquisitions, at (202) 512-4841 or RussellW@gao.gov.
Protecting Public Health Through Enhanced Oversight of Medical Products
The Food and Drug Administration (FDA) needs to take additional actions to oversee the quality of global medical product supply chains and ensure drug availability.
Why Area Is High Risk
FDA has the vital mission of protecting the public health by overseeing the safety and effectiveness of medical products—drugs, biologics, and medical devices—marketed in the U.S. These products are used in health care settings and at home. FDA faces multiple challenges in this role, including (1) globalization; (2) an extensive workload; (3) rapid changes in science and technology; and (4) unpredictable public health crises, such as the COVID-19 pandemic.
Area Rating
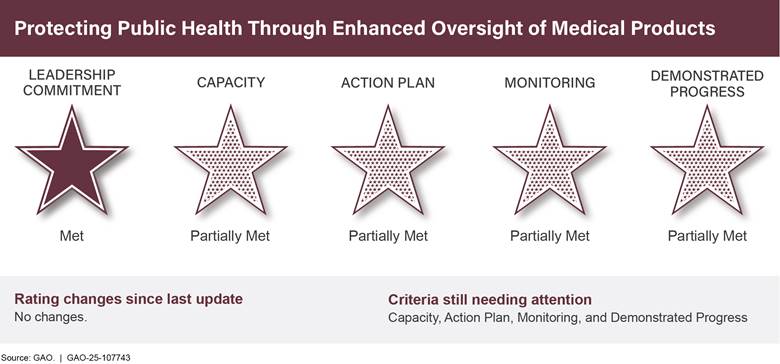
Overall ratings for all five criteria remain unchanged since our last High-Risk Report in 2023. The following sections present more detailed information on actions that FDA has taken since then to address the oversight of medical products.
Leadership commitment: met. FDA has remained committed to ensuring stable leadership over this area in the last few years. For example, it has maintained Senate-confirmed leadership at the commissioner level and FDA promptly filled vacancies at two of the centers that oversee medical products over the last several years when long-time leadership left the agency. However, the new administration has nominated a new FDA commissioner pending Senate confirmation, and other senior FDA leadership have recently left FDA, including the director for the center that oversees drugs. A Senate-confirmed commissioner, as well as stable senior FDA and center leadership, remains of vital importance to the agency and this high-risk area.
In addition, in October 2024, FDA implemented a structural reorganization, including of the staff who conduct inspections necessary for overseeing medical products. According to FDA, its efforts are intended to modernize and strengthen the agency to work together more collaboratively to meet the agency’s public health mission.
FDA has also identified drug shortages as a top priority risk for the agency given the persistent public health challenge this has posed for over 20 years. We have previously reported that drug shortages can significantly affect patient care by causing treatment delays and, ultimately, having potential adverse health outcomes for patients. In addition, the White House directed the Department of Health and Human Services to create a leadership position to coordinate medical product supply chain resilience efforts across the department, including FDA and other agencies, and to address drug shortages.
We will continue to monitor the effects of these leadership and organizational changes on the agency’s ability to conduct its medical product oversight responsibilities, including to prevent and mitigate drug shortages.
Capacity: partially met. FDA took some steps to address its recruitment and retention challenges. For example, in January 2024, FDA issued an agency-wide workforce plan, as we recommended, and plans to refine it on an annual basis. FDA also developed tailored strategies to recruit and retain drug investigators who conduct inspections in foreign countries, as we recommended. Further, it is implementing a workgroup to address long-standing challenges recruiting investigators to work in its offices in China and India.
While FDA has made these efforts, its capacity to conduct inspections remains challenged. FDA continues to face significant vacancies among investigators critical to ensuring the safety of the drug supply. Specifically, FDA faces vacancies among those who inspect entities conducting clinical research as well as those who inspect drug manufacturers (see fig. 52).
Figure 52: Vacancies of Food and Drug Administration Drug Manufacturing Investigators, November 2021–June 2024
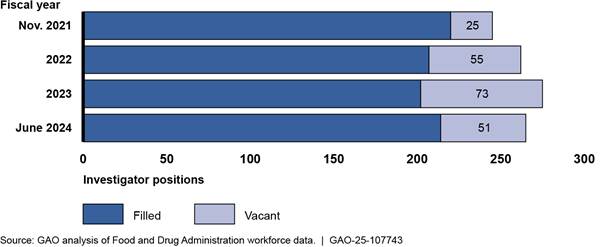
Agency officials noted that the investigator position has the highest levels of attrition within FDA. This has hindered its ability to resume inspections at rates comparable to the rate prior to the COVID-19 pandemic (see fig. 53).
Figure 53: Food and Drug Administration Foreign and Domestic Drug Manufacturing Inspections, Fiscal Years 2016-2023
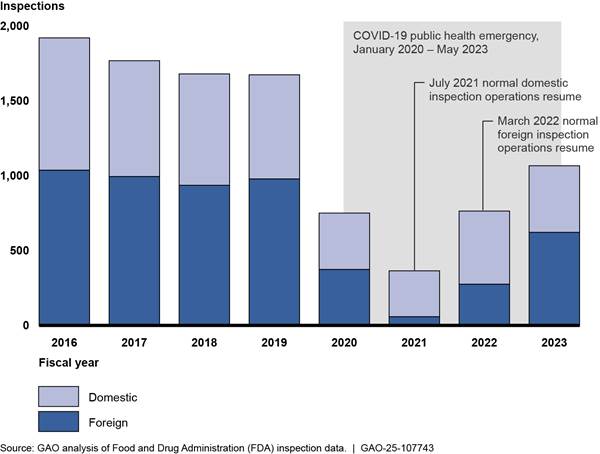
Note: FDA paused all inspections except those deemed mission critical in March 2020 due to the COVID-19 pandemic. The agency resumed normal operations for domestic inspections in July 2021 and began resuming normal operations for foreign inspections in March 2022, according to FDA officials.
To address these significant investigator vacancies and help increase the number of inspections, FDA should develop and implement plans to address the causes of attrition for investigators who inspect drug manufacturers. FDA should also evaluate its recruitment and retention efforts for investigators who conduct clinical research inspections. Given these recurring challenges, we are continuing to assess the actions FDA takes more broadly to ensure it has the capacity to carry out its oversight responsibilities.
Action plan: partially met. FDA outlined plans for fiscal years 2023 and 2024 to address the inspection backlog caused by the COVID-19 pandemic, as we recommended. For example, in fiscal year 2024, FDA began its planned increase of risk-driven, routine inspections of drug manufacturers for the first time since the pandemic.
However, FDA needs to do more to define its oversight approaches and evaluate them to ensure progress. Specifically, FDA should assess annually whether it is conducting an adequate number of inspections of the institutional review boards that help ensure human subjects are protected during clinical trials and other research, as we recommended.
Monitoring: partially met. FDA continued to take steps to monitor the effectiveness of its efforts to improve its oversight of medical products manufactured in foreign countries. For example, it took steps toward assessing the effectiveness of its foreign offices in the regulation of imported products and tracking the offices’ contributions. As of January 2025, the agency plans to finalize the system for tracking this effectiveness by June 2025.
Moreover, it continues to work to improve its visibility of the supply chain to help ensure a sufficient supply of medical products. In February 2024, FDA finalized guidance for how drug manufacturers report certain required supply chain information to help the agency mitigate supply chain vulnerabilities, consistent with our recommendation. FDA officials said that this reporting will help enhance the agency’s supply chain oversight and may help to mitigate drug shortages.
However, the agency has not been able to use the information to conduct comprehensive analyses because many manufacturers still have not submitted the required information to FDA, according to agency officials. These data also have gaps and lags in reporting, which officials said may limit their usefulness in preventing drug shortages. As a result, the agency continues to seek additional authority from Congress to collect more complete drug manufacturing information that will be more useful to the agency.
FDA also continued to develop data systems that could be used to proactively identify signals that may lead to drug shortages, as we recommended. Doing so could potentially help FDA to recognize trends, clarify causes, and resolve problems before drugs go in shortage.
Demonstrated progress: partially met. FDA continues to demonstrate progress in this area, but much work remains. For example, FDA has highlighted advanced manufacturing—innovative technologies that improve product quality and process performance—as a way to enhance supply chain resiliency, but few drugs have been made using these techniques.
As of April 2024, FDA had started to develop performance measures and goals to monitor the use and effectiveness of advanced manufacturing, as we recommended. Such steps would help FDA make informed program management decisions, including the allocation of finite resources.
What Remains to Be Done
As of January 2025, 17 recommendations to FDA remain open. To make progress in this high-risk area, attention is needed to address vacancies in specialized positions, identify and manage risks, and assess the effectiveness of FDA inspections and foreign offices. Specifically, FDA should implement the following recommendations:
· ensure FDA has the appropriate workforce in place to conduct inspections, including by
· developing tailored strategies to recruit and retain investigators to conduct foreign inspections,
· evaluating its recruitment and retention efforts for clinical research investigators for effectiveness, and
· developing and implementing action plans that address the causes of attrition.
· complete an annual risk assessment to determine whether the agency is conducting the appropriate number of routine inspections of institutional review boards.
· ensure FDA obtains complete and accessible information to help the agency identify and mitigate drug supply chain vulnerabilities, including those that may lead to drug shortages.
· develop a set of performance goals and measures that can be used to demonstrate foreign office contributions to outcomes related to the regulation of imported products.
Benefits
There have been nearly 50 benefits to the federal government due to progress in this high-risk area since it was added to the List in 2009. For example:
· In January 2024, FDA released an agency-wide strategic workforce plan for fiscal years 2023 through 2027 that describes the agency’s human capital goals, strategies to achieve those goals, and a roadmap for evaluating progress and refining the plan on an annual basis. We recommended and federal law required FDA to release such a plan.
· FDA implemented improvements to its postmarket data system, as we recommended. These changes included adding new templates, forms, and codes to identify specific submissions, as well as review goal notifications, dashboards, and reports to provide staff with user-friendly access to metrics and statuses of postmarket studies. According to FDA, these database enhancements will ensure continued, accurate oversight of postmarket studies.
· FDA is conducting a pilot program to evaluate the effectiveness and efficiency of unannounced inspections to decide if this approach should be applied more broadly. In implementing this pilot, FDA incorporated leading practices for designing a well-developed and documented pilot program, as we recommended. As of January 2025, FDA is in the process of evaluating interim results of the unannounced inspection pilot.
Contact Information
For additional information about this high-risk area, contact Mary Denigan-Macauley, or John E. Dicken, Directors, Health Care, at (202) 512-7114, DeniganMacauleyM@gao.gov or DickenJ@gao.gov.
Protecting Technologies Critical to U.S. National Security
Agencies have made progress protecting critical programs and technologies to maintain U.S. military superiority; however, several areas need more attention. This includes monitoring the effectiveness of measures taken to protect critical technologies.
Why Area Is High Risk
The Department of Defense (DOD) spends billions of dollars each year to develop and acquire technologies that provide an advantage for the warfighter. Many of these technologies are sold or transferred to promote U.S. economic, foreign policy, and national security interests. Foreign entities may also target these technologies for unauthorized transfer through theft, espionage, reverse engineering, and illegal export.
This high-risk area involves DOD’s actions to protect its critical programs and technologies, the Department of the Treasury’s efforts as the chair of the Committee on Foreign Investment in the United States (CFIUS) to mitigate the risk of foreign investment in the U.S., and other agencies’ actions to enforce export control regulations.
Area Rating

Since our 2023 High-Risk Report, the ratings for all five categories remain unchanged. The following sections present more detailed information on actions that DOD and other federal agencies have taken and need to take to address this high-risk area.
Leadership commitment: met. Agencies have maintained leadership commitment in this high-risk area. For example, DOD continues to create an annual list of critical programs and technologies. A senior DOD official said the department shares the list with other agencies that engage with DOD on technology protection efforts, as necessary. The list facilitates information sharing across the government to support efforts to protect critical DOD technologies.
Capacity: partially met. DOD has increased staffing resources within the Office of the Under Secretary of Defense for Research and Engineering to complete protection tasks, but officials said they have still not determined the cost of resources needed to implement protection measures. Therefore, DOD does not know the extent to which it needs to obtain additional funding for protection efforts.
Treasury plans to double its staffing to better manage its CFIUS workload and has taken steps to define its staffing goals, as we recommended. However, Treasury has not yet coordinated with CFIUS member agencies to establish a committee-wide process to coordinate staffing for monitoring and enforcing mitigation agreements, which we also recommended. We are currently evaluating the workload and resources Commerce dedicates to implementing and enforcing export controls.
Action plan: partially met. DOD is continuing to implement a four-step process to identify and protect critical programs and technologies (see fig. 54). As of January 2025, DOD has begun implementing the first three steps for identifying and protecting its critical programs and technologies. DOD is also assigning protection measures for each program and technology on the list. However, DOD officials said they have yet to identify metrics to assess the effectiveness of protection measures used. We are reviewing how the CFIUS member agencies implemented an expansion of the committee’s jurisdiction over foreign investments, including for certain critical technology investments.
Figure 54: Overview of DOD’s Process to Identify and Protect Programs and Technologies Supporting Critical Military Capability
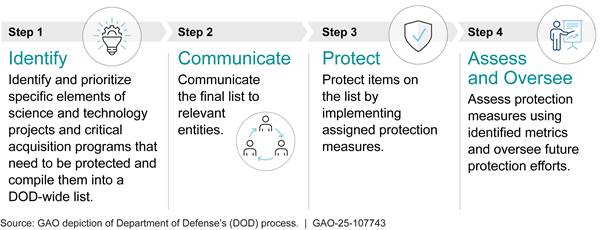
Monitoring: partially met. Agencies made limited progress to improve monitoring efforts under their control. For example, DOD has not completed its efforts to develop metrics for assessing protection measures (the fourth step of the process in fig. 54), as we recommended. Similarly, Treasury has issued public guidelines for levying penalties on companies that violate a CFIUS mitigation agreement. However, Treasury has not completed work with other CFIUS member agencies to document processes for certain committee-wide decisions, such as enforcement actions, as we recommended.
Demonstrated progress: partially met. Agencies took some steps to improve their efforts to protect critical programs and technologies by implementing 11 of our recommendations in the 2 years since our last update. For example, the FBI and Commerce established mechanisms to periodically assess the relevance and sufficiency of the risk factors they consider in identifying universities at greater risk for sensitive technology transfers, including unauthorized deemed exports, as we recommended. However, DOD has not yet developed metrics to assess the effectiveness of protection measures.
What Remains to Be Done
To make progress in this high-risk area, agencies need to improve workforce planning, identify metrics to assess program effectiveness, and assess new and evolving threats. As of January 2025, there are eight open recommendations related to this high-risk area which would better protect critical programs and technologies. For example:
· DOD should identify, develop, and periodically review appropriate metrics to assess the implementation and sufficiency of the assigned protection measures.
· Treasury should establish procedures to help ensure CFIUS responds in a timely manner to violations and focuses resources on mitigation agreements that remain relevant.
· Treasury should coordinate with CFIUS member agencies to establish a committee-wide process to coordinate staffing for monitoring and enforcing mitigation agreements.
Benefits
There were more than 70 benefits to the federal government due to progress since this area was added to the High-Risk Report in 2007. For example, over the last several years:
· DOD formalized a process to share its list of critical technologies with other federal agencies and ensure consistent protection across the government.
· CFIUS, with Treasury as chair, improved its staffing resources, identifying and reviewing covered transactions of certain foreign acquisitions and mergers.
· FBI and Commerce implemented mechanisms to periodically assess the relevance and sufficiency of risk factors they use to prioritize universities for outreach to address new or evolving threats to U.S. university research.
Contact Information
For additional information about this high-risk area, contact William Russell, Director, Contracting and National Security Acquisitions, at (202) 512-4841 or RussellW@gao.gov.
Strategic Human Capital Management
Federal agencies and the Office of Personnel Management (OPM) need to address skills gaps within the federal workforce by improving workforce planning, training, and recruitment and retention efforts.
Why Area Is High Risk
A highly skilled federal workforce is critical to the nation’s ability to address complex social, economic, and security challenges. However, the government faces long-standing challenges in strategically managing its workforce. This area was added to the High-Risk List in 2001.
Skills gaps, both within federal agencies and across the federal workforce, pose a high risk to the nation because they impede the government from cost effectively serving the public and achieving desired results. Agencies experience skills gaps when they have an insufficient number of individuals or individuals without the appropriate skills or abilities to successfully perform their work. OPM serves as the federal government’s chief human resources agency and personnel policy manager. This role includes providing guidance to federal agencies on closing skills gaps. However, OPM still needs to address skills gaps within its own workforce.
Area Rating

Since our 2023 high-risk update, the ratings for all five criteria remain unchanged.[89]
Leadership commitment: met. OPM continues to provide leadership to address skills gaps within the federal workforce. In particular, in April 2024, OPM released an artificial intelligence (AI) classification policy and guidance to respond to the AI in Government Act of 2020. This act requires OPM to establish or update an occupational series for AI positions. A consistent definition of AI work across government will enable agencies to identify the skills and competencies needed to attract, hire, and retain a highly skilled AI workforce. To develop this policy and guidance, OPM analyzed data from industry and academia and gathered input from numerous agencies. These include the Department of Defense, Department of Homeland Security, and Office of Management and Budget, as well as the Chief Human Capital Officers Council.
In addition, in 2023, OPM conducted an analysis to identify common hiring needs across multiple agencies. OPM’s analysis helped establish a pooled hiring strategy that saves time and resources through a centralized coordination of federal government hiring to address skills gaps within the IT and human capital management workforce.
Capacity: partially met. In addition to taking steps to close skills gaps across the federal government, OPM reported taking initial steps to address skills gaps within its own workforce. These steps included targeting early career talent through an internship program and providing employees with on-demand training through an e-learning content library.
OPM needs to continue to close its internal skills gaps in areas such as project management, organizational performance, leadership development, and data analytics. By closing these gaps, OPM could improve capacity to provide human capital services and guidance to agencies and address government-wide skills gaps.
Action plan: partially met. According to OPM’s regulation, agencies should develop a human capital operating plan that describes agency-specific skill and competency gaps that must be closed through the use of agency-selected human capital strategies.[90] However, OPM has not yet developed an action plan—whether as part of its human capital operating plan or as a separate effort—that addresses skills gaps within its own workforce, as we recommended. This action plan should include key information, such as a list of mission-critical occupations, which occupations have skills gaps, and how OPM will measure progress toward closing these skills gaps. This plan would help OPM implement, measure, and monitor its activities aimed at closing its skills gaps.
Other agencies are implementing plans to address their skills gaps. For example, according to agency officials, the Bureau of Land Management has begun to implement an agencywide strategic workforce plan as of January 2025, as we recommended. The plan includes long-term strategies for acquiring, developing, and retaining staff to achieve programmatic goals.
Monitoring: partially met. In June 2024, OPM identified the risks and mitigating strategies associated with its skills gaps, as we recommended. As a result, OPM is better positioned to monitor skills gaps across the agency and determine if risk mitigation strategies are successful. Nevertheless, additional work is needed, such as issuing an action plan, to improve OPM’s ability to monitor its efforts to close skills gaps in its own workforce.
Other agencies face similar struggles in monitoring their progress toward closing skills gaps. For example, we reported that the Department of Health and Human Services’ Administration for Strategic Preparedness and Response had taken steps to assess its workforce needs but did not have performance measures to help monitor progress in addressing hiring concerns. Likewise, we found that the National Nuclear Security Administration needs to monitor whether its recruitment and retention efforts have addressed related challenges.
Demonstrated progress: not met. For fiscal years 2022–2023, OPM developed agency priority goals directly related to recruitment and hiring government-wide. OPM met the goal supporting critical and urgent recruitment and hiring by helping agencies fill 75 percent of surge hiring positions identified in the first quarter of fiscal year 2022 in support of the Infrastructure Investment and Jobs Act. On the other hand, OPM did not meet its goal related to capitalizing on new workplace flexibilities to recruit and retain talent.
Moving forward, OPM needs to demonstrate progress in meeting its goals, including its goal to streamline the hiring process through pooled or shared hiring actions. These actions include sharing lists of qualified candidates among different agencies and reducing the number of different hiring actions for similar positions.
In addition to OPM, individual agencies need to demonstrate improvement in their capacity to perform workforce planning, train staff effectively, and recruit and retain the appropriate number of staff with the necessary skills. Multiple agencies face challenges in these areas of human capital management. As outlined in table 10, these challenges have contributed to our designating 20 of the other 37 areas currently on the List as high risk. These areas are in addition to the need for OPM to better manage skills gaps within its own workforce.
|
High-risk area |
Examples of skills gaps |
|
Staffing: The Federal Emergency Management Agency has fallen short of its annual staffing target between 2019 and 2022. Staffing gaps have limited the agency’s capacity to administer assistance to state and local governments, manage risk to create safer communities, and coordinate all aspects of resource planning and movement during a disaster. |
|
|
HHS Leadership and Coordination of Public Health Emergencies |
Staffing and workforce planning: The Department of Health and Human Services (HHS) has not completed the key workforce planning practice of developing strategies to fill staffing gaps. As a result, it does not have the number of medical emergency responders, such as doctors, nurses, and paramedics, it anticipates needing to effectively respond to disasters and public health emergencies. |
|
Staffing and workforce planning: Despite recent success with recruiting, the Bureau of Prisons (BOP) still faces staffing shortages. In addition, BOP’s use of overtime has increased annually since 2021. These workforce challenges may be resulting in officer fatigue and increasing risks to staff, incarcerated individuals, and facility security. |
|
|
Skills and workforce planning: The Department of Defense’s (DOD) Offices of the Director of Administration and Management and Chief Information Officer need to leverage their 2020 human capital analysis to determine next steps for identifying skills gaps and other resource gaps associated with its efforts to manage DOD’s portfolio of business systems. |
|
|
Staffing: The Office of Environmental Management within the Department of Energy continues to be understaffed, notably in two mission-critical positions—contract specialists and facility representatives who monitor site operations and safety. Staffing shortages have caused project failures, schedule delays, cost overruns, and workplace accidents. |
|
|
Skills and staffing: DOD continues to be challenged in establishing the necessary expertise and a sufficient workforce to effectively oversee acquisition processes and modernize software development. This workforce includes software systems architects and engineers, as well as acquisition professionals with expertise in procuring, managing, or developing software. In addition, workforce readiness in the defense industrial base remains a top challenge. |
|
|
Workforce planning: Four of the 24 major federal agencies have yet to fully implement our prior IT workforce recommendations, such as recommendations addressing key IT workforce planning activities, including establishing a workforce planning process, assessing gaps in competency and staffing needs, and implementing activities to address any such gaps. |
|
|
Skills and staffing: The Federal Protective Service, which is responsible for protecting thousands of federal facilities, continues to experience staffing shortages in areas such as law enforcement. The agency also needs to collect and analyze data to improve its contract guards’ capabilities to detect prohibited items and prevent them from entering federal facilities. |
|
|
Staffing and workforce planning: The Department of Energy’s (DOE) Office of Environmental Management (EM) faces staffing shortages. In particular, EM is understaffed in high-risk, mission-critical occupations, such as nuclear safety specialists and electrical engineers. It has also experienced difficulties with hiring and retaining staff at certain sites. In addition, EM does not have a forward-looking workforce plan to prepare for and manage current and future workforce needs, as we recommended. |
|
|
Workforce planning: DOD needs to assess the collective capability of current contractor personnel in financial management, use that assessment to help identify workforce needs, and develop written procedures for succession planning for DOD’s financial management workforce. |
|
|
Skills, training, and workforce planning: The Internal Revenue Service (IRS) faces challenges in addressing mission-critical skills gaps in its workforce, such as hiring and retaining revenue agents, revenue officers, and special agents who enforce the tax law and identify and collect taxes owed. IRS needs to develop and implement a strategy for hiring and training staff to meet this need. |
|
|
Training and workforce planning: Federal agencies have taken steps to identify and categorize all their vacant IT and cyber-related positions. However, they need to better identify staffing gaps and assess the effectiveness of their efforts to hire, train, and retain their cybersecurity and privacy workforces. |
|
|
Staffing and training: The Social Security Administration (SSA) has experienced challenges achieving its desired number of staff for both initial disability claims and appeals. For example, SSA officials stated that the agency has experienced challenges hiring and retaining entry-level legal assistants to help process appeals. The Department of Veterans Affairs (VA) has initiatives to improve its capacity to process initial claims and decide appeals but needs to develop plans to evaluate its training program for claims processors. |
|
|
Improving Federal Management of Programs that Serve Tribes and Their Members |
Skills, staffing, and workforce planning: The Bureau of Indian Education needs to establish training requirements for special education program staff, update its strategic workforce plan, and reduce staff vacancies, especially in offices that support and oversee schools. Indian Affairs needs to identify skills, knowledge, and competency gaps in mission-critical occupations, such as realty officers and certain specialists and assistants, across the agency. |
|
Workforce planning: The Food and Drug Administration (FDA) has not identified the investigators it needs to meet foreign inspection targets and thus safeguard imported food. |
|
|
Staffing and workforce planning: The Bureau of Land Management has not yet fully implemented an agencywide strategic workforce plan that includes long-term strategies for acquiring, developing, and retaining staff to achieve programmatic goals, such as managing energy development on public lands. Also, the Department of the Interior's Office of Natural Resources Revenue (ONRR) did not always prioritize efforts to hire data analysts or statisticians. Doing so could help ONRR better understand its own data and ensure the public receives a fair return for resources extracted from federal lands and waters. |
|
|
Staffing and training: The VA’s Veterans Health Administration (VHA) has yet to develop a comprehensive training framework. Further, the agency faces staffing challenges in certain areas, such as hiring psychologists and psychiatrists. VHA also needs to continue monitoring its efforts to hire staff across its health care system, such as determining the number of staff needed for VA’s community care program area. |
|
|
Protecting Public Health Through Enhanced Oversight of Medical Products |
Staffing: The FDA has significant vacancies among investigators who inspect clinical research entities and drug manufacturers. |
|
Transforming EPA’s Process for Assessing and Managing Chemical Risks |
Workforce planning: Workforce planning challenges hinder the Environmental Protection Agency's (EPA) efforts to recruit, develop, and retain the workforce needed to assess and manage chemical risks. This workforce requires scientific and technical expertise across mission-critical occupations (e.g., toxicologists, biologists, economists, and information technology specialists), which the agency considers core to carrying out its mission. |
|
Workforce planning: The VA has not conducted strategic workforce planning to ensure its acquisition workforce is of sufficient size and capability to oversee service contracts that need heightened management attention. |
Source: GAO analysis of prior work. | GAO-25-107743
What Remains to Be Done
Of the many recommendations focused on human capital issues to OPM and other federal agencies, 60 remain open as of January 2025. Thirty-three of these focus on OPM and 27 focus on other federal agencies. Additional progress could be made if agencies were to implement open recommendations related to closing skills gaps, monitoring the effects of recruitment and retention efforts, and preparing for and managing current and future staffing needs. For example:
· OPM should establish an action plan to address OPM’s skills gaps identified in its workforce assessment. This action plan should include a list of mission-critical occupations, which occupations have skills gaps, and how the agency will measure progress toward closing these skills gaps. Similarly, OPM should implement the two remaining key IT workforce planning activities—assessing competency needs and finalizing a workforce plan—to help ensure that it has the IT staff with the necessary knowledge, skills, and abilities to support its mission and goals.
· The Administration for Strategic Preparedness and Response within the Department of Health and Human Services should tailor its recruitment and hiring strategies to meet its unique workforce needs, such as hiring intermittent emergency responders and scientific staff, and account for government-wide shortages of human capital staff.
· The Department of Transportation should assess skill gaps in key occupations, such as attorneys, engineers, data analysts, and cybersecurity-related positions, that are involved in overseeing the safety of automated technologies. This analysis will help it understand its existing expertise to address any staffing gaps.
Congressional Actions Needed
Congressional action would be helpful to resolve skills gaps. For example, the Department of Energy's Office of Environmental Management relies on federal staff to oversee its nuclear waste cleanup from decades of nuclear weapons production and research at locations across the country. At the end of fiscal year 2023, it had 263 vacant positions, including engineers and management staff. Further, 44 percent of its staff will be eligible for retirement by 2030. Congress should consider requiring this office to report annually on its efforts to address recurring workforce problems.
Benefits
Since this area was added to the High-Risk List in 2001, progress to address strategic human capital management issues government-wide has resulted in about $920 million in financial benefits and more than 200 other benefits. For example:
· The Department of the Army converted military positions to civilian positions to make military personnel available to meet other Army needs, such as addressing staffing shortfalls in its warfighting force. Replacing higher-cost military personnel with lower-cost civilian employees and reallocating service members instead of increasing military personnel levels resulted in a financial benefit of over $915 million.
· The Global Markets unit in the Department of Commerce addressed human capital office vacancies to help small- and medium-sized U.S. businesses enter and expand into international markets, as we recommended. In February 2024, it hired more staff to decrease the open vacancies from 7 to 2 out of 30 positions and worked to decrease staff turnover. These changes will better position Commerce to deliver human capital services to its personnel working and living overseas and help ensure that employees can effectively carry out their mission.
· In June 2023, the Department of Defense completed a skills gap analysis of the department's cybersecurity and cyber IT personnel. The department mapped current workforce resources to future skill and position requirements needed for an enterprise-wide cloud environment. The analysis will place the department in a better position to anticipate and respond to changing IT staffing needs and to control human capital risks.
· In December 2021, the Army Corps of Engineers finalized its strategic human capital plan for fiscal years 2022–2023. This plan serves as the agency’s primary organization-wide civilian workforce planning document and includes its primary human capital goals, key initiatives, and associated performance metrics. As a result, the Corps is better positioned to address its workforce challenges, such as attracting top talent, hiring them quickly at competitive rates, and retaining them after they are trained. The updated human capital plan also helps the Corps manage its specialized workforce, which includes various types of engineers and other occupations requiring science and technical education, training, and experience, according to Corps officials.
Contact Information
For additional information about this high-risk area, contact Dawn G. Locke, Director, Strategic Issues, at (202) 512-6806 or LockeD@gao.gov.
Strengthening Department of Homeland Security IT and Financial Management Functions
The Department of Homeland Security (DHS) has made progress but needs to address remaining challenges in IT security controls, IT information systems, and its financial management systems and controls.
Why Area Is High Risk
DHS began operations in 2003. It had to transform 22 agencies—several with major management challenges—into one department. This high-risk area has evolved over time to reflect DHS’s progress in addressing these challenges.
In 2011, we reported that DHS needed to focus its efforts on five areas: human capital, acquisitions, IT, financial, and management functions. Since then, DHS has made sustained progress in some, but not all, of these areas. In 2023, we narrowed this high-risk area to focus on DHS’s remaining work in two areas that continue to experience significant challenges: IT and financial management.
DHS manages an annual budget of about $60 billion, but it has faced difficulties securing federal IT systems and information. It continues to face significant challenges with its financial management systems, processes, controls, and reporting. DHS needs to do more to address these pressing management challenges.
Area Rating
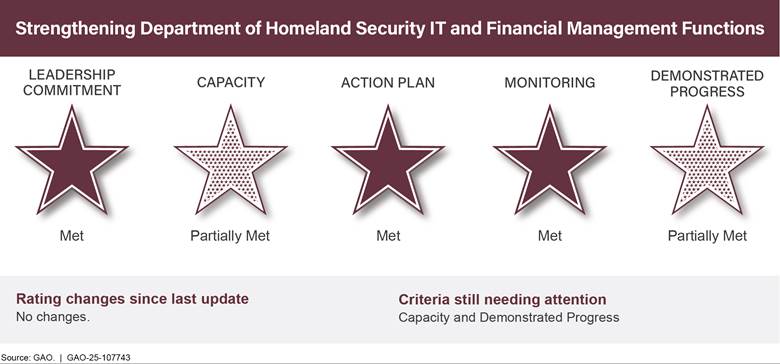
Since the 2023 High-Risk List, the high-risk criteria ratings are unchanged.
Leadership commitment: met. DHS’s top leaders have continued to demonstrate commitment and support for addressing the department’s management challenges. For instance, the Secretary of Homeland Security continued to prioritize addressing IT and financial management weaknesses as part of a department-wide initiative in 2024, thus helping to sustain focus on these areas.
Capacity: partially met. DHS is in the process of implementing its multiyear strategy to modernize its financial systems across its agencies but needs to continue addressing capacity-related issues. For example, Coast Guard completed rebaselining efforts of its financial system modernization in May 2024. However, it needs more capacity to address the serious findings and issues identified by system testing to declare full operational capability by October 2025, as planned.
The Federal Emergency Management Agency’s (FEMA) modernization efforts will also need additional attention and resources in its initial stages of implementing a new system. Further, U.S. Immigration and Customs Enforcement needs to develop cost and schedule estimates to determine needed resources as it plans to modernize its financial system.
Action plan: met. DHS has continued to update its Integrated Strategy for High-Risk Management every 6 months. The most recent update, from September 2024, includes outcome action plans that describe DHS’s progress and planned actions to further strengthen its management functions.
Monitoring: met. DHS’s latest strategy includes status updates and plans for actions that are in progress. For example, DHS has delayed obtaining a clean opinion on internal controls over financial reporting to fiscal year 2028 because of ongoing and planned system modernization efforts.
Demonstrated progress: partially met. In 2010, we identified actions that are critical for addressing DHS’s management challenges. DHS agreed with these actions, which we refer to as outcomes. DHS has since fully addressed seven of 14 outcomes in the areas of IT and financial management, but progress has been limited on the remaining seven (see fig. 55).
Figure 55: Management Outcomes Fully Addressed by the Department of Homeland Security as of September 2024
· IT management. DHS has addressed five of the six IT management outcomes and made progress implementing recommendations from DHS's Office of Inspector General (OIG) related to IT security weaknesses. However, more work remains for DHS to strengthen its information security program. It needs to mitigate the vulnerabilities identified by its OIG and financial statement auditor.
In fiscal year 2023, the DHS OIG reported six deficiencies in the information security program. For example, the OIG reported that not all vulnerabilities were promptly mitigated, nor did DHS create the plans of action and milestones for all information security weaknesses. These actions include enforcing requirements for components to obtain authority to operate, resolving critical and high-risk vulnerabilities, and applying sufficient resources to mitigate security weaknesses.
Further, in 2024, DHS's financial statement auditor continued to designate deficiencies in IT controls and information systems as a material weakness for financial reporting purposes. These deficiencies included ineffective design and implementation of controls to address areas such as system changes and access controls at several DHS components. It has identified planned steps and projects and will achieve and sustain at least a significant deficiency status for 2 consecutive years in November 2029.
Until DHS addresses these deficiencies, the data and systems will continue to remain at risk of disruption. Ineffective security controls to protect these systems and data could significantly affect a broad array of agency operations and assets.
· Financial management. DHS has received an unmodified (clean) audit opinion on its consolidated financial statements for 12 consecutive years, from fiscal years 2013 through 2024. However, during those same 12 years, DHS did not receive a clean opinion on its internal controls over financial reporting because it did not design and fully implement control activities to provide reasonable assurance that its systems will reliably report financial information. Specifically, the fiscal year 2024 financial statement auditor reported two long-standing material weaknesses related to financial reporting systems and controls.
· The financial statement auditor found that DHS did not design, implement, or effectively operate information technology general controls to help prevent unauthorized access to programs and data; document, authorize, or monitor system changes; and control access to systems that were commensurate with job responsibilities.
· Further, DHS did not effectively design, implement, or operate controls over the financial reporting process in the following areas: appropriate level of supervisory review of journal entries and preparation of disclosures; monitoring of automated and manual control environments, including service providers; and establishing an organizational structure and internal communication to plan and execute controls at Coast Guard.
Much work also remains to modernize DHS components’ financial management systems and business processes. For example, FEMA currently uses six segregated systems for financial management and procurement. FEMA plans to include the functionality of these systems under one financial system modernization effort. This modernization effort is critical given the significant amount of money FEMA manages for disasters as well as recent COVID-19 programs.
DHS’s financial statement auditor also continued to report that agency financial management systems did not comply with requirements of the Federal Financial Management Improvement Act of 1996. Specifically, DHS does not comply with applicable federal accounting standards in certain instances, federal financial management system requirements, and the U.S. Standard General Ledger at the transaction level. Without implementing modernized systems with fully effective controls that comply substantially with these requirements, DHS is at an increased risk of errors and inconsistent or incomplete financial information.
· Management integration. To fully address the remaining management integration outcome, DHS must continue to demonstrate sustainable progress integrating its management functions within and across the department. Most notably this includes integrating its financial management and IT systems. DHS must also address the remaining seven outcomes in financial and IT management.
What Remains to Be Done
As of January 2025, there were five open recommendations related to DHS financial management. These include continuing to modernize its financial system and to remediate known issues, fully incorporating leading practices into strategic documents, and fully incorporating the key elements of effective independent verification and validation into systems engineering guidance.
In addition to addressing our recommendations, DHS’s progress depends on addressing its remaining challenges identified by its OIG and its financial statement auditor including:
· continuing efforts to mitigate vulnerabilities to its IT security program identified by DHS's OIG;
· continuing efforts to ensure key controls are in place to address material weaknesses identified by the financial statement auditor; and
· obtaining an unmodified (clean) opinion on internal controls for 2 consecutive years.
Benefits
Since we designated implementing and transforming DHS as a high-risk area in 2003, there have been more than $2.4 billion in financial benefits. Some of the most significant benefits come from reductions in improper overpayments in DHS programs such as the Homeland Security Grant Program and National Flood Insurance Program and the increase in air carrier fees to help pay for aviation security services. More than 200 other benefits have also been realized. For example:
· In September 2023, FEMA provided an updated Grants Management Modernization system security plan and a high-level report of the security control test results. By taking these steps to test these security controls, FEMA reduced the risk of exposing the system to potential exploits.
· In November 2023, the Coast Guard updated its guidance on developing corrective action plans for IT and financial system weaknesses.
Contact Information
For additional information about this high-risk area, contact Chris Currie, Director, Homeland Security and Justice, at (404) 679-1875 or CurrieC@gao.gov; Paula Rascona, Director, Financial Management and Assurance, at (202) 512-9816 or RasconaP@gao.gov; or David (Dave) Hinchman, Director, Information Technology and Cybersecurity, at (214) 777-5719 or HinchmanD@gao.gov.
Strengthening Medicaid Program Integrity
The Centers for Medicare & Medicaid Services (CMS) needs to reduce billions in Medicaid improper payments, ensure the appropriate use of program dollars, and improve the quality of program data to better manage quality of care and efficiency of payments for services.
Why Area Is High Risk
In fiscal year 2024, the Medicaid program served approximately 73 million low-income and medically needy individuals at the cost of about $611 billion. This area is on our High-Risk List because of (1) improper payments, estimated to be over $31 billion in fiscal year 2024; (2) limitations in CMS efforts to ensure states use Medicaid funds in accordance with federal requirements; and (3) limited CMS oversight of states’ Medicaid data, including on expenditure and utilization.
Medicaid enrollment increased more than 30 percent (22.4 million individuals) between February 2020 and February 2023. The law required states to keep beneficiaries continuously enrolled in Medicaid throughout the COVID-19 public health emergency as a condition for receiving a temporary increase in federal funds.[91] This condition ended effective March 2023, and states resumed full eligibility redeterminations, including disenrollments. This process, which was still ongoing as of January 2025, is known as Medicaid “unwinding.” During the public health emergency, CMS also allowed states flexibility in rules for screening and enrolling Medicaid providers.
Overall Area Rating

Overall ratings for all five criteria have not changed since 2023 and are all partially met. The following sections present more-detailed information on the three segments that comprise the overall high-risk area: improper payments, appropriate use of program dollars, and program data. The ratings for these segments also remain unchanged since 2023.
Improper Payments

Leadership commitment: met. To strengthen its oversight of improper payments, CMS has leveraged the work of state auditors to begin using national trends in findings the auditors identified to improve audit processes, as we recommended in September 2023. Additionally, in late 2023, CMS initiated a series of audits to help states identify and correct compliance issues to minimize improper payments. Also, in July 2024, we reported that CMS identified key lessons from the “unwinding” to improve oversight of states’ compliance with federal eligibility redetermination requirements. CMS had taken initial steps toward embedding these lessons, consistent with our recommendation. For example, CMS issued guidance in May 2024 extending requirements for states to report data used by the agency to monitor compliance during unwinding.
Capacity: partially met. CMS is working with states and audit contractors to increase its investigations of managed care plans, which have previously identified millions in provider overpayments and other unallowable costs. CMS efforts resulted in a significant increase in the number of managed care investigations opened by audit contractors from 16 in fiscal years 2016 to 2018 to 893 in fiscal years 2019 to 2021. Further, CMS reinstated collaborative efforts, which had been paused during the COVID-19 pandemic, with state auditors to identify updates to guidance for conducting federally required single audits. CMS should strengthen its collaborations with state auditors, who are uniquely positioned to help CMS with Medicaid oversight. Providing state auditors with information on program risks and agency actions taken to address single audit findings could help them better target their reviews and address gaps in CMS’s oversight activities.
Action plan: partially met. CMS took some actions to reduce improper payments but could strengthen oversight. About a third of Medicaid improper payments in fiscal year 2019 related to states’ noncompliance with provider screening and enrollment requirements. In September 2024, CMS contracted with an entity to assess states’ current compliance with these requirements and to help states develop and implement action plans to address areas of noncompliance. This contract, in combination with CMS’s targeted assistance to states and other activities, addresses our October 2019 recommendation that CMS expand its efforts to assess state compliance with these requirements. However, CMS still needs to assess states’ progress toward addressing areas of noncompliance with provider screening and enrollment requirements for states with corrective action plans.
Monitoring: partially met. CMS improved its monitoring efforts to address improper payments but could take additional steps to identify more. To address CMS’s weak oversight of Medicaid procurements in states and U.S. territories, CMS assessed Puerto Rico’s reformed procurement process for risk in February 2023. It also helped the territory implement a competitive procurement for external reviews of Medicaid managed care organizations in March 2023.
However, CMS should continue taking steps to enhance the effectiveness of recovery audit efforts, which involve reviews of claims for improper payments, as we recommended in June 2023. CMS issued procedures in October 2023 specifying that the agency will grant exemptions from recovery audit efforts for a 2-year period and will communicate an expiration date to states when approving such exemptions. Yet, CMS could identify additional improper payments by studying whether states’ recovery audit efforts should include payments to managed care organizations.
Demonstrated progress: partially met. CMS estimated the overall Medicaid improper payment rate in fiscal year 2024 to be 5.09 percent, or $31.1 billion. This rate reflects a decline from 8.6 percent in fiscal year 2023 and from 15.6 percent in fiscal year 2022. The Department of Health and Human Services (HHS) attributed the decline in part to certain flexibilities granted to states during the COVID-19 public health emergency, including postponed eligibility redeterminations and reduced provider enrollment requirements. The improper payment rate is likely to increase as Medicaid unwinds and states continue to resume standard processes for eligibility determinations and provider enrollment through early 2027. Additionally, while CMS significantly increased the number of managed care investigations in fiscal years 2019 to 2021, the managed care component of the error rate continues to not account for all program risks and may not be a good indicator of improper payments in managed care.
Appropriate Use of Medicaid Dollars
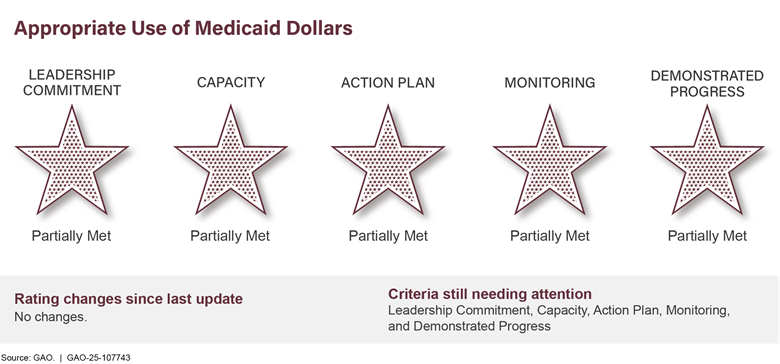
Leadership commitment: partially met. In May 2024, CMS issued a final rule that will enhance fiscal oversight of state directed payments, which states use to direct how Medicaid managed care plans pay providers.[92] The rule established limits for certain state directed payments. Further, the rule and the supplemental guidance issued in April 2024 help ensure that states use appropriate sources of funds to finance the nonfederal share of Medicaid payments. However, CMS has not taken steps to ensure that payments are economical and efficient at the provider level, which we recommended in April 2015. Implementing this recommendation could help ensure that providers do not receive payments that exceed their cost.
In September 2022 CMS revised its policies aimed at ensuring Medicaid demonstrations are budget neutral—meaning that the demonstrations do not increase federal costs. Certain changes were consistent with our recommendation to use valid methods when setting demonstration spending limits and are estimated to reduce federal fiscal liabilities by billions of dollars. Other changes, however, may lead to increased federal costs. As such, the overall effect of the September 2022 policies on the federal costs of demonstrations is unclear.
Capacity: partially met. CMS has worked toward enhancing its oversight capacity for spending under state directed payments, which has grown rapidly to at least $38.5 billion in 2022, the sixth year of state use. In a final rule issued in May 2024, CMS established a state reporting requirement for actual state directed payment expenditures at the provider level, although the requirement will not be in effect until 1 year after CMS issues reporting instructions.[93] Until then, CMS continues to rely on state estimates of spending when deciding whether to renew approval for a state directed payment. In December 2023, we reported that actual spending for state directed payments sometimes far exceeded approved state estimates (see fig. 56).
In February 2024, CMS told us that a reorganization allowed the agency to devote additional resources to completing certain reviews of state expenditure reporting. While this has reduced its review backlog, we maintain that CMS should conduct a national assessment to ensure resources are adequate and appropriately targeted, as we recommended in 2018. The agency suspended its plan to conduct such an assessment in 2019 given its reorganization plans.
Action plan: partially met. CMS took steps to improve state reporting on separate payments that are made to certain providers and may offset the cost of care, known as supplemental payments. CMS issued guidance in December 2021 that required states to report supplemental payments made beginning in fiscal year 2022. As of January 2025, CMS had made fiscal year 2022 and 2023 supplemental payment data publicly available. CMS noted challenges with the accuracy and reliability of the reported data, and is working to fix some of the data issues. CMS also increased transparency around state directed payments by publicly posting certain approval documents in July 2023. In December 2023, we recommended that CMS post all relevant approval documents. As of December 2024, the agency had delayed efforts to do so, citing competing priorities.
Monitoring: partially met. CMS has taken steps to improve its ability to monitor state directed payments but continues to lack data needed to monitor others, such as supplemental payments. In 2023, CMS formalized procedures for completing an enhanced review of applications for certain types of state directed payments, which we found exceeded $1 billion in some states. For supplemental payments, however, CMS still does not have a strategy for ensuring complete, consistent, and sufficiently documented provider-specific information about sources of funding for the nonfederal share of these payments, as we recommended. Further, CMS efforts remain ongoing to develop standard operating procedures for monitoring spending under Medicaid demonstrations.
Demonstrated progress: partially met. CMS’s May 2024 final rule for state directed payments enhances the requirements for state evaluation of directed payments. It also increases accountability by clarifying CMS’s authority to disapprove payments that are based on impermissible financing or do not comply with all federal requirements. However, CMS will not take enforcement actions for about 3 years, so it is too soon to determine the extent to which CMS’s new requirements will better ensure the appropriate use of Medicaid dollars.
Medicaid Data

Leadership commitment: met. CMS continues to demonstrate leadership commitment through its efforts to improve the availability and quality of Medicaid data. These efforts include ensuring that all 50 states, the District of Columbia, and three U.S. territories submit data monthly to the Transformed Medicaid Statistical Information System (T-MSIS). T-MSIS includes data on a variety of Medicaid topics. This includes enrollment, enrollee demographics, and utilization to help support program oversight and research. CMS also continues to set targets for critical and high-priority T-MSIS data and works with states to improve the quality of their data and to help states meet these targets. Further, CMS issued final rules establishing time frames for states to report Medicaid payments for certain home and community-based services and requiring states to report the annual amounts of state directed payments to individual providers.[94]
Capacity: partially met. CMS increased its capacity to report Medicaid data by releasing additional T-MSIS data for oversight. Additionally, the agency also began making states’ managed care data publicly available in 2024, and officials told us that they plan to continue to do so. However, the usefulness of the managed care data is limited as CMS officials told us that they are continuing to address data quality issues, such as incomplete reporting across certain data elements.
Action plan: partially met. CMS has used available data to inform its oversight of the program but further attention is needed. CMS shared examples of how the agency used T-MSIS data for oversight and its plan to release, on an ongoing basis, additional T-MSIS data for program research and oversight. However, CMS has been assessing whether to use T-MSIS data to calculate certain quality measures to inform benefit oversight instead of requiring states to report them. Relying on T-MSIS for these measures would streamline state reporting, as we recommended. Additionally, CMS should analyze states’ managed care appeals and grievances data and implement the agency’s plan for how to use these data for oversight.
Monitoring: partially met. CMS used T-MSIS data to monitor the effects of the COVID-19 public health emergency on Medicaid enrollment and whether eligible enrollees received appropriate screening services. Since our last update, CMS has begun collecting states’ eligibility redetermination data, which it uses to monitor state compliance with federal requirements. According to agency officials, CMS continues to assess how it can leverage lessons learned during the “unwinding” to ensure state compliance with redetermination requirements.
Demonstrated progress: partially met. CMS continues to improve the usefulness and quality of data available for oversight, yet issues persist. For example, in September 2023, CMS issued clarifying guidance aimed at improving the reliability of states’ managed care encounter data. Further, in September 2024, CMS also revised its template for managed care annual reports to collect information on the outcomes of enrollee appeals of service denials, as we recommended. However, CMS should also collect additional information on the number of managed care denials, which would further improve the usefulness of these reports. Additionally, some states still do not meet T-MSIS quality standards, such as unreliable data on the race and ethnicity of adults with intellectual and developmental disabilities.
What Remains to Be Done
As of January 2025, 65 recommendations related to strengthening Medicaid program integrity remain open. To strengthen Medicaid program integrity, CMS should fully implement our recommendations related to reducing billions in Medicaid improper payments, ensuring the appropriate use of program dollars, and improving the quality of program data. For example, CMS should
· strengthen collaboration with state auditors and leverage state auditor work to inform oversight activities and audit processes;
· document and implement the oversight practices the agency learned during the unwinding period that were needed to prevent and detect state compliance issues with federal eligibility redetermination requirements;
· annually monitor states’ progress toward addressing areas of noncompliance with provider screening and enrollment requirements;
· assess the cost effectiveness of requiring states to expand recovery audit efforts to include managed care;
· enhance fiscal oversight of state directed payments in managed care and make publicly available all approval documents related to these payments;
· develop a policy establishing criteria to ensure that Medicaid payments at the provider level are economical and efficient and collect and document provider-specific information about Medicaid payments to providers;
· conduct a national risk assessment to ensure resources to oversee states’ Medicaid expenditures are adequate and allocated based on areas of highest risk;
· use valid methods to ensure demonstrations are budget neutral and develop and document standard operating procedures for monitoring demonstration spending;
· implement its planned actions for appeals and grievances data to oversee Medicaid managed care programs; and
· continue to improve T-MSIS data quality and use these data to improve oversight of Medicaid benefits for children and streamline state reporting.
Congressional Actions Needed
Congressional action could also improve oversight of the Medicaid program. As of January 2025, three matters for congressional consideration related to Medicaid program integrity remained open. Specifically, we recommended that Congress consider
· establishing statutory requirements for HHS to improve the demonstration review process to better ensure valid methods are used to demonstrate budget neutrality;
· addressing whether demonstrations that allow states to operate public managed care organizations and retain excessive revenue to support programs previously funded by the state are within the scope of the Secretary of HHS’s authority; and
· establishing a requirement for CMS to improve the transparency and accountability of certain Medicaid supplemental payments made to hospitals or other providers serving, for example, high-cost enrollees.
Benefits
Financial benefits due to progress made strengthening Medicaid program integrity totaled about $154.7 billion and resulted in more than 100 benefits to the federal government since it was added to the list in 2003. For example:
· In multiple reports since the 1990s, we reported that HHS allowed states to use questionable methods that resulted in inflated demonstration spending limits and increased the federal government’s fiscal liability. Beginning with demonstrations approved in September 2022, CMS implemented a policy change to better ensure demonstration projects are budget neutral. CMS estimated that these changes would further reduce spending limits by about $106 billion in fiscal years 2023 through 2027, of which we estimated the federal share would be more than $60 billion.
· The Medicaid Extenders Act of 2019 included a provision that essentially reduced federal funds to states that had not implemented an electronic asset verification system for determining eligibility for certain individuals applying for Medicaid.[95] This policy change addresses our findings showing states’ noncompliance with program requirements. This provision is projected to result in about $55 million in savings to the federal government for fiscal years 2021 through 2024.
· In October 2018, we recommended that CMS provide states with information on how to fulfill requirements that could improve the reliability of managed care encounter data, which are critical for overseeing managed care and the Medicaid program. In September 2023, CMS issued guidance and tools that provide states with information to conduct and report on required encounter data assessments. These assessments will provide CMS with information to address encounter data weaknesses.
Contact Information
For additional information about this high-risk area, contact Michelle B. Rosenberg, Director, Health Care, at (202) 512-7114 or RosenbergM@gao.gov
Transforming EPA’s Process for Assessing and Managing Chemical Risks
The U.S. Environmental Protection Agency (EPA) needs to address capacity issues to more effectively assess and manage chemicals posing risks to human health and the environment.
Why Area Is High Risk
Chemicals in commerce (existing chemicals) and those that have yet to enter commerce (new chemicals) may pose risks to human health and the environment. Offices and programs across EPA work to assess and manage those risks in a scientifically sound and timely manner:
· The Office of Chemical Safety and Pollution Prevention (OCSPP) implements the Toxic Substances Control Act, as amended (TSCA). The amended law expanded EPA’s authority and responsibility to regulate new and existing chemicals. For example, it directs EPA to make formal determinations on all new chemicals before they can be manufactured—generally within a 90-day review period.
· The Office of Research and Development (ORD) produces a variety of chemical assessment products including Integrated Risk Information System (IRIS) assessments. These assessments identify and characterize the health hazards of chemicals.
· Other EPA offices are involved in the agency’s work on chemical risk assessment or management.
We added this issue to the High-Risk List in 2009 because EPA had not developed sufficient risk information to limit exposure to many chemicals that may pose substantial health risks. Since then, EPA’s approach to assessing and managing chemicals has changed significantly. For example, EPA was given greater responsibility for regulating existing and new chemicals when TSCA was amended in 2016, partly in response to concerns about the pace of the agency’s work under the law.
Similarly, the IRIS Program’s approach to meeting user needs for chemical assessments changed considerably as ORD improved its program. For example, ORD is more effectively using its portfolio of toxic chemical assessment products—which include IRIS and other chemical assessments like Provisional Peer-Reviewed Toxicity Values—to provide a range of risk assessments informing EPA’s decision-making on the protection of public health and the environment. Topics such as the assessment of per- and polyfluoroalkyl substances (PFAS) —a group of thousands of chemicals used in a wide range of consumer and other products that can persist in the environment and cause adverse health effects—have been prominent in the program’s recent efforts, as well as across EPA.
Given the changes to these programs, we are evaluating EPA’s work managing chemical risks through a single combined rating in this update. We will no longer assess the IRIS Program and TSCA implementation separately as we did in 2023.
Area Rating
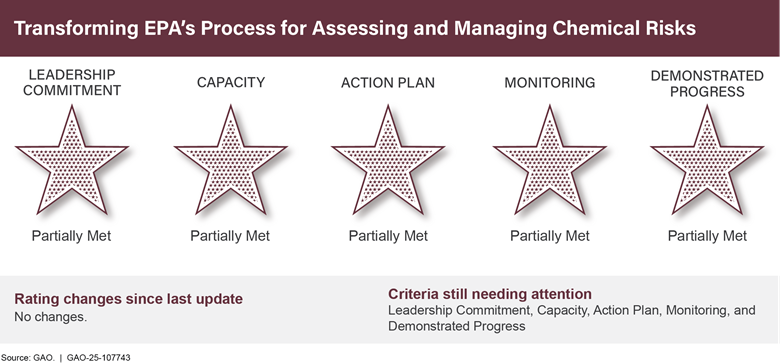
Overall ratings for all five criteria remain unchanged since 2023. The following sections present more detailed information on actions EPA has taken under each criterion.[96]
Leadership commitment: partially met. Since 2023, EPA leadership has continued to demonstrate a strong commitment to implementing its TSCA responsibilities, including seeking resources to address outstanding program needs. For example, EPA’s budget request to implement TSCA increased annually from fiscal year 2023 through fiscal year 2025: approximately $124.2 million in fiscal year 2023, $130.7 million in fiscal year 2024, and $131.9 million in fiscal year 2025. However, EPA’s final actual budget authority for fiscal year 2023 was about $91.2 million.[97] According to the fiscal year 2025 request, these additional resources are essential for EPA to complete existing chemical risk evaluations within the statutory time frame and modernize IT systems supporting the TSCA program.
Further, EPA has shown leadership commitment focusing on the challenges associated with persistent chemicals. For example, in April 2021, EPA established a council charged with creating a multi-year, agencywide strategy for addressing risks posed by PFAS. EPA has taken some actions to restrict PFAS and to provide additional information to the public.
However, EPA leadership and officials in ORD overseeing the IRIS Program have not increased resources or examined workforce needs for either the program or across EPA. The budget for the Health and Environmental Risk Assessment (HERA) research program, of which IRIS is a part, has remained about the same since fiscal year 2009—approximately $45 million in fiscal year 2023.
Since resources have remained static, the IRIS Program has been unable to increase the number of assessments in development at any one time despite high demand. For example, despite receiving 43 nominations for chemical assessments from EPA offices in 2022, the program was unable to accept 27 of them due to staffing constraints. In addition, the program’s current pace of finalizing one or two IRIS assessments a year likely cannot increase without more resources. ORD and EPA leadership have not responded to a February 2023 resource analysis IRIS Program officials completed identifying the Program’s needed workforce for completing IRIS assessments as well as other assessment efforts.
Capacity: partially met. OCSPP and IRIS Program officials reported a lack of capacity to effectively carry out their work, but both have taken some steps to identify needed resources. For example, in February 2024, OCSPP developed a Workforce Action Plan with goals to address hiring delays and retention challenges and to summarize its planning activities on an annual basis. However, in January 2024, the Assistant Administrator for OCSPP testified that, due to budgetary constraints, EPA has struggled to meet TSCA’s requirements to ensure that new chemicals can be used safely and quickly enter commerce.
According to EPA, among the 1,163 pre-manufacture notice reviews completed between 2017 and 2022, the agency typically made its determination within the initial 90-day review period less than 10 percent of the time. See table 11. Specifically, EPA completed these reviews in 181 days or more between 53 and 90 percent of the time. EPA provides information related to new chemical reviews (such as cases completed and submissions received since TSCA was amended in 2016 including fiscal year 2024) on an agency public webpage but does not publicly report how long it takes to complete reviews.
Table 11: U.S. Environmental Protection Agency (EPA) Review Times for Pre-Manufacture Notice Reviews, Calendar Years 2017-2022
|
2017 |
2018 |
2019 |
2020 |
2021 |
2022 |
|
|
Percentage of reviews completed in 90 days or less |
7 |
3 |
14 |
8 |
6 |
0 |
|
Percentage of reviews completed between 91 days and 180 days |
40 |
8 |
17 |
22 |
24 |
10 |
|
Percentage of reviews completed in 181 days or more |
53 |
89 |
69 |
7% |
71 |
90 |
Source: EPA. | GAO-25-107743
Note: Counts are based on the calendar year in which EPA completed the review. EPA review time reflects the calendar days between the date of receipt of the pre-manufacture notice and the date of completion. Counts for 2022 are incomplete and include reviews from January 1, 2022, through May 16, 2022, the most recent information available for our review. Review time percentages may not add to 100 due to rounding. TSCA, as amended, directs EPA to make formal determinations on all new chemicals before they can be manufactured—generally within a 90-day review period.
The Assistant Administrator for OCSPP stated that although EPA has prioritized resources for its new chemicals program, the agency will continue to struggle for as long as the budgetary constraints persist. Moreover, senior managers in OCSPP’s New Chemicals Division told us the division lacks expertise and resources to assess the sufficiency of its existing evidence-building capacity or to identify actions to maintain or enhance that capacity.
In February 2023 and again in April 2024, IRIS Program staff reported they need 26 additional staff across various scientific specialties to meet current demand for chemical assessments. IRIS Program staff also reported they had spent about 33,000 hours from fiscal years 2018 through 2023—or the equivalent of 16 full-time staff years—on mostly unplanned technical assistance to various EPA offices and other entities, which reduced staff time to prepare planned chemical assessments.
Action plan: partially met. The IRIS Program and OCSPP’s New Chemicals Division have conducted strategic planning activities. IRIS Program staff included in their April 2024 resource analysis the Program’s plans for preparing various types of chemical assessments relying on current budget and human resources.
In November 2024, EPA provided its third-year progress report on the PFAS Strategic Roadmap, which lays out EPA’s agencywide approach to addressing risks. This strategy is intended to further science and research to allow EPA to manage risks from persistent chemicals; for example, in April 2024, the agency updated its guidance for managing the destruction and disposal of PFAS-containing materials.
Moreover, in January 2025, EPA published its most recent annual plan identifying existing chemical substances for which it expects to initiate or complete risk evaluations that year, along with needed resources, as required by TSCA.[98] Additionally, the New Chemicals Division drafted a strategic plan in August 2024. This draft plan includes five goals related to the New Chemicals Program and identifies metrics and strategies for achieving each goal. However, as we discuss below, we found that the division did not follow key practices for effectively assessing, building, or using evidence for its planning activities.
Monitoring: partially met. The IRIS Program’s April 2024 resource analysis included metrics to track the Program’s progress in meeting user needs for chemical assessments. The IRIS Program improved its monitoring processes by implementing changes to the Program’s chemical nomination surveys in 2022 and to the way that survey was carried out.
However, we found that OCSPP’s New Chemicals Division did not follow key practices for effectively assessing, building, or using evidence for its activities (see fig. 57). We found the division had not completed foundational planning actions, such as finalizing its draft strategic plan. Finalizing the plan consistent with relevant key practices will better position the division to identify and prioritize the evidence it needs and use that evidence to monitor progress toward achieving its goals, such as to “deliver scientifically sound risk-based assessments for new chemical substances with improved timeliness.”
Figure 57: Extent to Which EPA Follows Key Management and Assessment Practices for Its New Chemicals Program
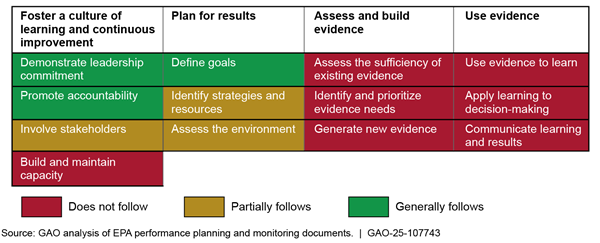
Demonstrated progress: partially met. The IRIS Program has made progress in carrying out its chemical assessment activities. Since February 2023, the Program has released four final IRIS assessments—including the assessment for formaldehyde—and seven Provisional Peer-Reviewed Toxicity Value assessments. The Program continues to make progress on other assessments in its work plan.
EPA has made progress in implementing its PFAS Strategic Roadmap, as well. For example, EPA finalized the PFAS National Primary Drinking Water Regulation in April 2024. Further, we reported in September 2024 that to address a key action in the roadmap, EPA had posted a PFAS Communications Toolkit on its website with information public water systems can share with customers about health risks posed by PFAS in drinking water.
However, OCSPP continues to face challenges in carrying out its responsibility to make determinations on new chemical reviews within the 90-day review period as shown in table 11 above. EPA stated that it is committed to improving the efficiency and transparency of its New Chemicals Program and has launched related process improvements, such as finalizing updates to the regulations that govern new chemical reviews.
What Remains to Be Done
Attention is needed to resources (budgetary and staffing), strategic planning, and monitoring to make progress in this high-risk area. Specifically, as of January 2025, three recommendations related to assessing and managing chemical risks remain open, including the following focused on OCSPP’s planning and assessment efforts:
· OCSPP should develop a process and timeline to fully align its workforce planning efforts for implementing TSCA chemical review responsibilities with workforce planning principles.
· OCSPP’s New Chemicals Division should, as it finalizes its strategic plan, address relevant key practices for managing and assessing the New Chemicals Program including involving stakeholders and identifying resources.
· OCSPP’s New Chemicals Division should implement a systematic process for aligning the division’s performance management approach with key management and assessment practices.
Benefits
This area has realized more than 10 benefits since it was added to the High-Risk List in 2009, including the following in response to our recommendations:
· To inform future budget and human capital planning efforts, Health and Environmental Risk Assessment (HERA) staff delivered an analysis of resources needed to produce various chemical assessments for EPA’s program and regional offices, for fiscal year 2023 and 2024.
· HERA staff identified ORD products beyond IRIS assessments that could better serve EPA user needs through their portfolio and efforts to create fit-for-purpose solutions for EPA program and regional offices.
· The IRIS Program made changes to its website and its communication to EPA offices about the status of chemical assessments in progress, allowing EPA offices who rely on these assessments to better understand when they may be available.
Contact Information
For additional information about this high-risk area, contact J. Alfredo Gómez, Director, Natural Resources and Environment, at (202) 512-3841 or GomezJ@gao.gov
VA Acquisition Management
The Department of Veterans Affairs (VA) should improve its acquisition function, by completing a supply-chain strategy and implementing an acquisition framework to increase its efficiency and effectiveness.
Why Area Is High Risk
VA has among the highest contract obligations in the federal government and has increasingly relied on contractors to perform some key tasks. Our reporting over the past 10 years has shown that VA’s total contract obligations increased substantially, rising over 150 percent. In fiscal year 2023, VA obligated about $61 billion for goods and services.
Our work continues to identify VA acquisition management challenges including (1) developing adequate strategies and policies, (2) managing its supply chain, (3) managing its acquisition workforce, and (4) providing consistent leadership and execution of management priorities. VA made some progress addressing these issues; however, several substantial challenges remain. We added this area to the High-Risk List in 2019.
Area Rating
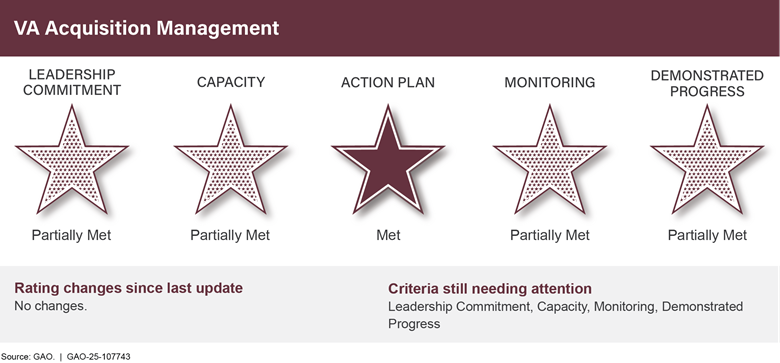
Since 2023, ratings for all criteria remain unchanged. The following sections present more detailed information on the overall rating.
Leadership commitment: partially met. VA’s acquisition leaders, including the Chief Acquisition Officer and Senior Procurement Executive, continue to demonstrate commitment to addressing acquisition management challenges. In its September 2024 update to its high-risk action plan, VA formally identified executive and senior leaders responsible for addressing corrective actions.
For example, VA leadership designated the Office of Acquisition and Logistics as the lead for developing acquisition program management capacity. As part of this effort, the office is establishing strategies and activities to implement its major acquisition framework. VA leadership also gave the Logistics Redesign Program Management Office responsibility for developing and implementing a supply chain management strategy to include governance, strategy, policy, operations, training, and program management.
However, VA needs sustained leadership commitment and accountability across the agency to fully implement its action plan and demonstrate progress. Specifically, the plan requires ongoing efforts by different individuals and organizations across the agency—many of which do not report directly to the Chief Acquisition Officer or Senior Procurement Executive. These include the Assistant Under Secretary for Health in the Veterans Health Administration; the Executive Director, Programming, Analysis, and Evaluation in the Office of Management; and the Executive Director in the Office of Small and Disadvantaged Business Utilization, among others.
In addition, VA needs to establish clear accountability mechanisms to ensure consistent execution. For example, VA acquisition leaders are still working to fully implement its framework for managing major acquisitions. VA also needs to demonstrate sustained leadership commitment to develop a comprehensive supply chain strategy. In July 2024, the Veterans Health Administration canceled a solicitation for an IT platform to support supply chain management transformation due to budget constraints and changing leadership priorities. VA is in the process of determining next steps for this effort.
Capacity: partially met. VA continues to build capacity to address its acquisition management challenges. For example, in August 2023, VA deployed an automated tool that helped improve the accuracy of its acquisition workforce records to help it make data-driven decisions. However, VA needs to develop additional capacity to manage its major acquisitions and oversee its service contracts. For example:
· VA could face challenges implementing its framework for managing major acquisitions because of information gaps on program cost and workforce needs.
· VA had not conducted strategic workforce planning to ensure sufficient personnel are available to oversee service contracts that need heightened management attention. We recommended that VA determine whether its acquisition workforce is of sufficient size and capability.
· VA eliminated the program manager position for its Community Care contracts, which allow veterans to receive medical care from community providers instead of VA facilities, without reassigning contract oversight responsibilities. Given the cost and scope of these contracts, we recommended that VA assess whether these oversight responsibilities are being effectively fulfilled.
Action plan: met. VA continued to update its high-risk action plan to address ongoing acquisition management challenges. These challenges include management of contracting officer workload, lack of reliable contracting and financial data systems, and supply chain modernization, among other things. VA’s September 2024 plan identified root causes of these issues, corrective actions, and included additional metrics intended to track progress. VA also developed outcome tables for each acquisition management area of concern that we identified. These tables identify more specific initiatives to address the root causes.
Monitoring: partially met. VA continues to make some progress in improving its monitoring efforts; however, VA has yet to fully develop a monitoring program to validate the effectiveness of its corrective actions. For example, VA’s September 2024 action plan includes performance measures aligned with broader initiatives and identifies expected completion dates, but many of the plan’s metrics measure interim steps, rather than VA’s desired outcomes. VA continues to refine the metrics to measure outcomes where possible and is also working to implement a dashboard to assist with monitoring progress against the plan.
Also, VA reported that it took steps to reduce the number of drop-shipped items (supplies shipped directly from manufacturers instead of local warehouses) in its new version of the Medical-Surgical Prime Vendor program. We found that drop shipments often result in late deliveries. VA increased the monitoring and oversight of backorders that can lead to drop shipments. The new version of the program will include additional automated reporting of transaction data that will enable more detailed monitoring of backorders and drop shipments.
We also recently highlighted other areas where VA could improve monitoring. For example:
· VA has unreliable and incomplete data on its service contracts, which accounted for $42 billion in contracting obligations in fiscal year 2022 and provided limited oversight of them. We recommended that VA take steps to improve the completeness of its service contract data and issue additional oversight guidance.
· VA had yet to develop a monitoring approach for an initiative to centralize the contracting and distribution of positive airway pressure devices that help veterans with sleep apnea. We recommended that VA develop metrics and objectives to track performance of its initiative for centralizing distribution of devices and supplies to treat sleep apnea with appropriate, reliable data sources, and routinely share this information with relevant stakeholders.
· VA’s contract oversight guidance was incomplete for the five large contracts that are central to its Community Care Program and accounted for almost 40 percent of all of VA’s total contract obligations (fig. 58). For example, the guidance contained information on specific tasks, such as how to track receipt of contract deliverables and reports, but limited information on overall roles and responsibilities for VA officials overseeing these contracts. We recommended that VA establish a complete set of guidance, including identifying clear and complete procedures as well as roles and responsibilities.
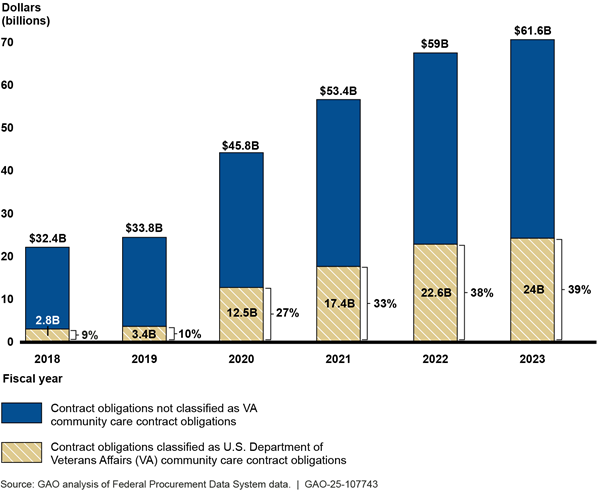
Demonstrated progress: partially met. VA demonstrated some progress by implementing measures to improve acquisition management. However, VA still needs to address remaining steps that will take substantial effort and require obtaining broad buy-in from leaders and organizations across the department. For example:
· In March 2024, VA officially rescinded its previous acquisition management framework and replaced it with its Acquisition Lifecycle Framework. VA is working to implement a program management structure to help ensure the success of the Acquisition Lifecyle Framework. VA recognizes this is a longer-term effort. To implement this framework, VA needs to address gaps in program management for managing its major acquisitions.
· VA developed an initial draft of a comprehensive supply chain management strategy. After review, VA leadership determined that additional changes were needed to ensure stakeholder input and industry best practices were reflected. VA said a new strategy would be completed in 2025. VA still needs a comprehensive supply chain strategy to address its acquisition management root causes.
As VA continues to develop desired outcomes and measures to improve acquisition management, it also needs to demonstrate sustained progress.
What Remains to Be Done
To make progress in this high-risk area, VA needs to establish clear accountability for carrying out its action plan, improve strategic workforce planning, strengthen oversight of service contracts, and fully implement its strategy and framework for acquisition management. There are 21 recommendations to improve VA acquisition management that remain open as of January 2025. These include
· developing a comprehensive supply chain strategy;
· addressing obstacles to implementing a framework to provide oversight of its major acquisitions; and
· developing policies and procedures for planning and conducting oversight of contracts that involve functions needing heightened management attention, including its Community Care contracts.
Benefits
More than 20 benefits have been achieved since we added this area to the High-Risk List in 2019. For example, VA
· deployed an automated data tool that helped improve the accuracy of its acquisition workforce records;
· developed performance metrics for procurement organizations; and
· developed a report and procedures for reducing drop shipments from its Medical-Surgical Prime Vendor program, and improved quarterly data reporting and analysis for purchases made outside of the program.
Contact Information
For additional information about this high-risk area, contact Shelby S. Oakley, Director, Contracting and National Security Acquisitions, at (202) 512-4841 or OakleyS@gao.gov.
High-risk area
|
Improving the Delivery of Federal Disaster Assistancea,b (new) |
|
Funding the Nation’s Surface Transportation Systema |
|
HHS Leadership and Coordination of Public Health Emergenciesb |
|
Strengthening Management of the Federal Prison System |
|
Unemployment Insurance Systema,b |
|
DOD Approach to Business Transformation |
|
DOD Business Systems Modernization |
|
DOD Contract Management |
|
Emergency Loans for Small Businesses |
|
Government-wide Personnel Security Clearance Processa,b |
|
National Efforts to Prevent, Respond to, and Recover from Drug Misuseb |
|
National Flood Insurance Programa |
|
Resolving the Federal Role in Housing Financea,b |
|
U.S. Government’s Environmental Liabilitya,b |
|
USPS Financial Viabilitya |
|
DOD Weapon Systems Acquisitiona |
|
Improving IT Acquisitions and Managementa,b |
|
Managing Federal Real Propertyb |
|
Acquisition and Program Management for DOE’s National Nuclear Security Administration and Office of Environmental Managementa |
|
DOD Financial Management |
|
Enforcement of Tax Lawsa |
|
Ensuring the Cybersecurity of the Nationa,b |
|
Improving and Modernizing Federal Disability Programsb |
|
Improving Federal Management of Programs that Serve Tribes and Their Membersb |
|
Improving Federal Oversight of Food Safetya,b |
|
Limiting the Federal Government’s Fiscal Exposure by Better Managing Climate Change Risksa,b |
|
Management of Federal Oil and Gas Resources |
|
Managing Risks and Improving VA Health Care |
|
Medicare Program and Improper Paymentsa |
|
Modernizing the U.S. Financial Regulatory Systema,b |
|
NASA Acquisition Management |
|
Protecting Public Health Through Enhanced Oversight of Medical Products |
|
Protecting Technologies Critical to U.S. National Securityb |
|
Strategic Human Capital Managementb |
|
Strengthening Department of Homeland Security IT and Financial Management Functions |
|
Strengthening Medicaid Program Integritya,b |
|
Transforming EPA’s Process for Assessing and Managing Chemical Risks |
|
VA Acquisition Management |
Source: GAO. | GAO‑25‑107743
aLegislation is likely to be necessary to effectively address this high-risk area.
bCoordinated efforts across multiple entities are necessary to effectively address this high-risk area.
This appendix contains credit, copyright, and other source information for images, tables, or figures in this product when that information was not listed adjacent to the image, table, or figure.
Highlights Page Icons
GAO is the source for the following icons used in the Highlights page.
![]()
![]()
United States Postal Service is the source for the following icons used in the Highlights page.
![]()
Icons-Studio/stock.adobe.com is the source for the following icons used in the Highlights page.
![]()
![]()
![]()
![]()
![]()
![]()
![]()
Executive Summary Icons
GAO is the source for the following icons used in the Executive Summary.
![]()
![]()
United States Postal Service is the source for the following icons used in the Executive Summary.
![]()
Icons-Studio/stock.adobe.com is the source for the following icons used in the Executive Summary.
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
The following GAO reports reflect our High-Risk Series reports issued since 2000. For additional GAO products specific to each of the 38 high-risk areas on our updated list, see our High-Risk List website, https://www.gao.gov/high-risk-list.
High-Risk Series: Efforts Made to Achieve Progress Need to Be Maintained and Expanded to Fully Address All Areas. GAO-23-106203. Washington, D.C.: Apr. 20, 2023.
High-Risk Series: Key Practices to Successfully Address High-Risk Areas and Remove Them from the List. GAO-22-105184. Washington, D.C.: Mar. 3, 2022.
High-Risk Series: Dedicated Leadership Needed to Address Limited Progress in Most High-Risk Areas. GAO-21-119SP. Washington, D.C.: Mar. 2, 2021.
High-Risk Series: Substantial Efforts Needed to Achieve Greater Progress on High-Risk Areas. GAO-19-157SP. Washington, D.C.: Mar. 6, 2019.
High-Risk Series: Progress on Many High-Risk Areas, While Substantial Efforts Needed on Others. GAO-17-317. Washington, D.C.: Feb. 15, 2017.
High-Risk Series: Key Actions to Make Progress Addressing High-Risk Issues. GAO-16-480R. Washington, D.C.: Apr. 25, 2016.
High-Risk Series: An Update. GAO-15-290. Washington, D.C.: Feb. 11, 2015.
High-Risk Series: An Update. GAO-13-283. Washington, D.C.: Feb. 14, 2013.
High-Risk Series: An Update. GAO-11-278. Washington, D.C.: Feb. 16, 2011.
High-Risk Series: An Update. GAO-09-271. Washington, D.C.: Jan. 22, 2009.
High-Risk Series: An Update. GAO-07-310. Washington, D.C.: Jan. 31, 2007.
High-Risk Series: An Update. GAO-05-207. Washington, D.C.: Jan. 1, 2005.
High-Risk Series: An Update. GAO-03-119. Washington, D.C.: Jan. 1, 2003.
High-Risk Series: An Update. GAO-01-263. Washington, D.C.: Jan. 1, 2001.
Determining Performance and Accountability Challenges and High Risks. GAO-01-159SP. Washington, D.C.: Nov. 1, 2000.
This is a work of the U.S. government and is not subject to copyright protection in the United States. The published product may be reproduced and distributed in its entirety without further permission from GAO. However, because this work may contain copyrighted images or other material, permission from the copyright holder may be necessary if you wish to reproduce this material separately.
The Government Accountability Office, the audit, evaluation, and investigative arm of Congress, exists to support Congress in meeting its constitutional responsibilities and to help improve the performance and accountability of the federal government for the American people. GAO examines the use of public funds; evaluates federal programs and policies; and provides analyses, recommendations, and other assistance to help Congress make informed oversight, policy, and funding decisions. GAO’s commitment to good government is reflected in its core values of accountability, integrity, and reliability.
Obtaining Copies of GAO Reports and Testimony
The fastest and easiest way to obtain copies of GAO documents at no cost is through our website. Each weekday afternoon, GAO posts on its website newly released reports, testimony, and correspondence. You can also subscribe to GAO’s email updates to receive notification of newly posted products.
Order by Phone
The price of each GAO publication reflects GAO’s actual cost of production and distribution and depends on the number of pages in the publication and whether the publication is printed in color or black and white. Pricing and ordering information is posted on GAO’s website, https://www.gao.gov/ordering.htm.
Place orders by calling (202) 512-6000, toll free (866) 801-7077,
or
TDD (202) 512-2537.
Orders may be paid for using American Express, Discover Card, MasterCard, Visa, check, or money order. Call for additional information.
Connect with GAO
Connect with GAO on Facebook, Flickr, X, and YouTube.
Subscribe to our RSS Feeds or Email Updates. Listen to our Podcasts.
Visit GAO on the web at https://www.gao.gov.
To Report Fraud, Waste, and Abuse in Federal Programs
Contact FraudNet:
Website: https://www.gao.gov/about/what-gao-does/fraudnet
Automated answering system: (800) 424-5454 or (202) 512-7700
Congressional Relations
A. Nicole Clowers, Managing Director, ClowersA@gao.gov, (202) 512-4400, U.S. Government Accountability Office, 441 G Street NW, Room 7125, Washington, DC 20548
Public Affairs
Sarah Kaczmarek, Managing Director, KaczmarekS@gao.gov, (202) 512-4800, U.S.
Government Accountability Office, 441 G Street NW, Room 7149
Washington, DC 20548
Strategic Planning and External Liaison
Stephen J. Sanford, Managing
Director, spel@gao.gov, (202) 512-4707
U.S. Government Accountability Office, 441 G Street NW, Room 7814, Washington,
DC 20548
[1]This total includes $312 billion in selected supplemental appropriations to federal agencies for disaster assistance and approximately $136 billion in annual appropriations to the Disaster Relief Fund for fiscal years 2015 through 2024. It does not include other annual appropriations to federal agencies for disaster assistance. Of the supplemental appropriations, $97 billion was included in supplemental appropriations acts that were enacted primarily in response to the COVID-19 pandemic.
[2]Pub. L. No. 118-158, div. B, 138 Stat. 1722 (2024).
[3]Improper payments are payments made in an incorrect amount or that should not have been made or that lack sufficient documentation and include both over- and underpayments. 31 U.S.C. §§ 3351(4), 3352.
[4]Under the Payment Integrity Information Act of 2019 (PIIA), an agency is required to report an annual estimate when the agency’s risk assessment determines that a program may be susceptible to significant improper payments. PIIA defines significant improper payments as those that, in the preceding fiscal year, may have exceeded either (1) $100 million or (2) $10 million plus 1.5 percent of the total amount of program outlays.
[5]89 Fed. Reg. 64,538 (Aug. 7, 2024). This rule is scheduled to take effect October 1, 2025.
[6]Pub. L. No. 115-391, 132 Stat. 5194.
[7]GAO, High-Risk Series: Efforts Made to Achieve Progress Need to Be Maintained and Expanded to Fully Address All Areas, GAO‑23‑106203 (Washington, D.C.: Apr. 20, 2023).
[8]GAO, Government Performance Management: Leading Practices to Enhance Interagency Collaboration and Address Crosscutting Challenges, GAO-23-105520 (Washington, D.C.: May 24, 2023).
[9]31 U.S.C. § 503(c)(1)(F).
[10]GAO, Determining Performance and Accountability Challenges and High Risks, GAO‑01‑159SP (Washington, D.C.: November 2000).
[11]GAO, High-Risk Series: Efforts Made to Achieve Progress Need to Be Maintained and Expanded to Fully Address All Areas, GAO-23-106203 (Washington, D.C.: Apr. 20, 2023).
[12]GAO, High-Risk Series: Key Practices to Successfully Address High-Risk Areas and Remove Them from the List, GAO-22-105184 (Washington, D.C.: Mar. 3, 2022).
[13]This total includes $312 billion in selected supplemental appropriations to federal agencies for disaster assistance and approximately $136 billion in annual appropriations to the Disaster Relief Fund for fiscal years 2015 through 2024. It does not include other annual appropriations to federal agencies for disaster assistance. Of the supplemental appropriations, $97 billion was included in supplemental appropriations acts that were enacted primarily in response to the COVID-19 pandemic. Additionally, in December 2024, the Disaster Relief Supplemental Appropriations Act, 2025, appropriated $110 billion in supplemental appropriations for disaster assistance. Pub. L. No. 118-158, div. B, 138 Stat. 1722 (2024).
[14]Pub. L. No. 117-249, § 2, 136 Stat. 2350 (2022) (codified at 15 U.S.C. § 636(b)(16)). See also at 13 C.F.R. § 123.3(a)(6).
[15]Pub. L. No. 117-58, §§ 70201-07, 135 Stat. 429, 1250-58 (2021).
[16]Pub. L. No. 117-58, 135 Stat. 429, 1386-88 (2021).
[17]Pub. L. No. 116-284, 134 Stat. 4869 (2021) (codified at 42 U.S.C. § 5135).
[18]FEMA’s Individual Assistance program provides financial assistance and direct services to eligible individuals and households who have uninsured or underinsured necessary expenses and serious needs as a result of a disaster. FEMA has also made other regulatory changes to the Individual Assistance program intended to improve access to assistance for survivors. 89 Fed. Reg. 3990 (Jan. 22, 2024). See also FEMA, Biden-Harris Administration Reforms Disaster Assistance Program to Help Survivors Recover Faster, (Washington, D.C.: 2024) for more information.
[19]Pub. L. No. 117‑58, 135 Stat. 429 (2021).
[20]Pub L. No. 112-141, § 1203(a), 126 Stat. 405, 524 (2012) (codified as amended at 23 U.S.C. § 150).
[21]Pub. L. No. 115-391, 132 Stat. 5194. The Act, among other things, directs BOP to deliver programs that may lower incarcerated individuals’ risk of recidivism. It also provides certain incarcerated individuals with opportunities to earn time credits that may allow them to reduce the amount of time they spend in a BOP facility.
[22]National Defense Authorization Act for Fiscal Year 2025, Pub. L. No. 118-159, § 902 (2024).
[23]DOD’s Office of Inspector General has announced a review assessing the effectiveness of internal controls to ensure that the data in Advana is reliable for making informed decisions on DOD operations and performance.
[24]31 U.S.C. §§ 1115(b), 1116.
[25]10 U.S.C. § 125a(e).
[26]William M. (Mac) Thornberry National Defense Authorization Act for Fiscal Year 2021, Pub. L. No. 116-283, § 901, 134 Stat. 3388, 3794 (2021).
[27]21 U.S.C. § 1705(h)(1).
[28]21 U.S.C. § 1705(c)(1)(G)(iii).
[29]In our 2023 update, we reported that the CDC reported nearly 107,000 predicted provisional drug overdose deaths during the 12-month period ending in September 2022. In February 2025, the CDC updated its estimate for the 12-month period ending in September 2022 to be 110,550 predicted provisional drug overdose deaths. We used the most recent CDC data in our estimates.
[30]21 U.S.C. § 1705(a)(2). For the 2024 National Drug Control Strategy, ONDCP notified Congress in accordance with 21 U.S.C. § 1705(e) that the strategy would be late and specified the date by which it would be submitted. However, ONDCP missed this date as well due to its interagency clearance process. ONDCP issued the strategy in May 2024, but did not release all of the accompanying documents, such as the Performance System Review report, until December 2024.
[31]In October 2018, the Substance Use-Disorder Prevention that Promotes Opioid Recovery and Treatment for Patients and Communities Act, Pub. L. No. 115-271, § 8202, 132 Stat. 3894, 4110, reauthorized ONDCP. In addition, section 8221 of the Act, 132 Stat. at 4134-42 (codified at 21 U.S.C. § 1705(a)), requires the Director to release a statement of drug control policy priorities in the calendar year of a presidential inauguration (but not later than April 1) and the President to submit to Congress a strategy not later than the first Monday in February following the year in which the term of the President commences, and every 2 years thereafter. Pursuant to 21 U.S.C. § 1705(b)(1), the strategy is to set forth a comprehensive plan to reduce illicit drug use and the consequences of such illicit drug use in the U.S. by limiting the availability of, and reducing the demand for, illegal drugs.
[32]Consolidated Appropriations Act, 2023, Pub. L. No. 117-328, § 1262, 136 Stat. 4459, 5681 (2022) (codified at 21 U.S.C. § 823(h)).
[33]21 U.S.C. § 1705(c)(1)(N)(iii).
[34]21 U.S.C. § 1705(c)(1)(C).
[35]21 U.S.C. § 1705(g).
[36]21 U.S.C. § 1705(h).
[37]In our 2023 update, we reported that the CDC reported nearly 107,000 predicted provisional drug overdose deaths during the 12-month period ending in September 2022. In February 2025, the CDC updated its estimate for the 12-month period ending in September 2022 to be 110,550 predicted provisional drug overdose deaths. We used the most recent CDC data in our estimates.
[38]CDC National Center for Health Statistics, Drug Overdose Deaths in the United States, 2003–2023, (Dec. 2024).
[39]On September 7, 2008, Treasury made commitments of financial support to the enterprises in the form of stock purchase agreements. As of December 2024, the enterprises had collectively received $191.4 billion in support from Treasury. If they were to incur major future losses, they would draw needed amounts from their remaining $254.1 billion in Treasury commitments.
[40]The Housing and Economic Recovery Act of 2008, Pub. L. No. 110–289, 122 Stat. 2654 (July 30, 2008) amended the Federal Housing Enterprises Financial Safety and Soundness Act of 1992, Pub. L. No. 102–550, title XIII, 106 Stat. 3672, 3941–4012 (Oct. 28, 1992) to establish FHFA and give it supervisory and regulatory authority over the enterprises, as well as other entities. Under the act, the Director of FHFA can also appoint the agency as conservator of the enterprises. 12 U.S.C. § 4617(a)(1). When FHFA placed the enterprises in conservatorship on September 6, 2008, it assumed control previously held by management and shareholders. FHFA sets annual priorities for the enterprises using a scorecard.
[41]The 2025 high-risk area rating is based on analysis of agency actions taken up through and including the 118th Congress, before the start of the 119th Congress and the new administration. Therefore, agency plans and policies referenced in this update may have subsequently changed. We will continue to monitor federal government actions, and our future high-risk updates will reflect these and other policy and legal developments.
[42]89 Fed. Reg. 56,028 (July 8, 2024).
[43]We define banks as bank holding companies, financial holding companies, savings and loan holding companies, insured depository institutions, and credit unions, including any subsidiaries or affiliates of these types of institutions. For the purposes of this report, we refer to these entities collectively as “banks.” We define nonbanks as lenders or servicers that are not banks.
[44]89 Fed. Reg. 64,538 (Aug. 7, 2024). The rule is scheduled to take effect October 1, 2025.
[45]James M. Inhofe National Defense Authorization Act for Fiscal Year 2023, Pub. L. No. 117-263, § 326, 136 Stat. 2395, 2518-19 (2022).
[46]The Inflation Reduction Act of 2022 provided USPS with $3 billion to purchase zero-emission vehicles and purchase, design, and install associated infrastructure. Pub. L. No. 117-169, § 70002, 136 Stat. 1818, 2086–87.
[47]Pub. L. No. 117-108, 136 Stat. 1127.
[48]Carl Levin and Howard P. “Buck” McKeon National Defense Authorization Act for Fiscal Year 2015, Pub. L. No. 113-291, div. A, title VIII, subtitle D, 128 Stat. 3292, 3438–3450 (Dec. 19, 2014).
[49]The four agencies that have not yet fully implemented key IT workforce planning activities are the Departments of Agriculture, Labor, and State; and the Office of Personnel Management.
[50]Agencies did not implement 125 of the recommendations we made related to this high-risk area during fiscal years 2010 through 2020. In addition, seven of the recommendations we made during fiscal years 2017 through 2020 are no longer valid; as such, we closed those recommendations.
[51]Thomas R. Carper Water Resources Development Act, Pub. L. No. 118-272, S. 4367, 118th Cong., div. B, tit. III § 2302 (2025) (enacted).
[52]Pub. L. No. 114-287, 130 Stat. 1463.
[53]Thomas R. Carper Water Resources Development Act, Pub. L. No. 118-272, S. 4367, 118th Cong., div. B, tit. III § 2301 (2025) (enacted).
[54]Office of Management and Budget, OMB Memorandum No. 24-01, “Implementation of Occupancy Metrics for Office Space,” (Aug. 16, 2024). The memorandum provides agencies with requirements for design standards and measuring and reporting occupancy for their owned and leased office space.
[55]In January 2025, OPM issued a memo directing agencies to revise telework policies to state that eligible employees must work full time at their respective duty stations, with limited exceptions, which may lead to changes in building utilization rates. Office of Management and Budget, Memorandum, “Guidance on Presidential Memorandum Return to In-Person Work” (Jan. 22, 2025).
[56]Federal Real Property Council, Agency-Level Federal Real Property Profile Data Quality Improvement Program Guidance (August 2024).
[57]Exec Order No. 14111, 88 Fed. Reg. 83,809 (Dec. 1, 2023).
[58]In August 2022, Congress appropriated approximately $79.4 billion to IRS through the Inflation Reduction Act (IRA) of 2022 appropriations. See Pub. L. No. 117-169, tit. I, subtit. A, pt. 3, § 10301, 136 Stat. 1818, 1831-1833 (2022). In June 2023, the Fiscal Responsibility Act of 2023 rescinded about $1.4 billion of the amount appropriated for IRS. See Pub. L. No. 118-5, div. B, tit. II, § 251, 137 Stat. 10, 30-31 (2023). In March 2024, the Further Consolidated Appropriations Act of 2024 rescinded an additional $20.2 billion of the amount appropriated for IRS. See Pub. L. No. 118-47, div. B, tit. VI, § 640, div. D, tit. V, § 530, 138 Stat. 460, 572, 708 (2024). Enacted in September 2024, the Continuing Appropriations and Extensions Act of 2025 prevents IRS from spending an additional $20.2 billion of IRA funding, which is continued by the American Relief Act of 2025 through March 14, 2025. See Pub. L. No. 118-83, div. A, § 115, 138 Stat. 1524, 1527 (2024); Pub. L. No. 118-158, div. A, § 101, H.R. 10545, at 2 (2025).
[59]Congressional Budget Office, Cost Estimate, “Summary Estimated Budgetary Effects of Public Law 117-169, to Provide for Reconciliation Pursuant to Title II of S. Con. Res. 14.” (Washington, D.C.: Sept. 7, 2022).
[60]Internal Revenue Service, Return on Investment: Re-Examining Revenue Estimates for IRS Funding, Publication 5901 (Washington, D.C.: February 2024).
[61]A partnership is generally an unincorporated organization with two or more members that conducts a business and divides the profits.
[62]The Taxpayer First Act required IRS, in collaboration with the National Taxpayer Advocate, to set standards for the management of IDT cases. These standards may include an average time frame for taxpayers to wait to have their respective identity theft victim assistance cases resolved. Pub. L. No. 116-25, § 2008, 133 Stat. 981, 1006–1007 (2019).
[63]Consolidated Appropriations Act, 2016, Pub. L. No. 114-113, Protecting Americans from Tax Hikes Act of 2015, div. Q, § 201(a), 129 Stat. 2242, 3076 (2015), codified at 26 U.S.C. § 6071(c).
[64]American Rescue Plan Act of 2021, Pub. L. No. 117-2, § 9674, 135 Stat 4, 185 (2021), codified at 26 U.S.C. §6050W (e).
[65]Pub. L. No. 116-283, Div. A, Title XVII, § 1752, 134 Stat. 3388, 4144–4149 (Jan. 1, 2021), codified at 6 U.S.C. § 1500.
[66]Cloud computing is a means for enabling on-demand access to shared pools of configurable computing resources (e.g., networks, servers, storage applications, and services) that can be rapidly provisioned and released.
[67]Pub. L. No. 117-168, 136 Stat. 1759.
[68]Pub. L. No. 118-82, 138 Stat. 1521.
[69]Relatedly, we have also reported on the relationship between food and chronic health conditions—such as the link between a diet high in refined grains and type 2 diabetes—and the numerous federal efforts to reduce Americans’ risk of such conditions. See GAO, Chronic Health Conditions: Federal Strategy Needed to Coordinate Diet-Related Efforts, GAO-21-593 (Washington, D.C.: Aug. 17, 2021).
[70]Federal Food Administration Act of 2024, H.R. 9099, 118th Cong. (2024); S. 4745, 118th Cong. (2024).
[71]U.S. Global Change Research Program, Fifth National Climate Assessment, (Washington, D.C.: November 2023).
[72]This total includes $312 billion in selected supplemental appropriations to federal agencies for disaster assistance and approximately $136 billion in annual appropriations to the Disaster Relief Fund for fiscal years 2015 through 2024. It does not include other annual appropriations to federal agencies for disaster assistance. Of the supplemental appropriations, $97 billion was included in supplemental appropriations acts that were enacted primarily in response to the COVID-19 pandemic. Additionally, in December 2024, the Disaster Relief Supplemental Appropriations Act, 2025, appropriated $110 billion in supplemental appropriations for disaster assistance. Pub. L. No. 118-158, div. B, 138 Stat. 1722 (2024).
[73]The 2025 high-risk rating is based on our analysis of federal government actions taken through and including in the 118th Congress, before the start of the new administration. It references executive orders that have been subsequently revoked and federal policy documents that may be rescinded, replaced, or amended. We will continue to monitor federal government actions, and our future high-risk updates will reflect these and other policy and legal developments.
[74]“An Act To provide for reconciliation pursuant to Title II of S. Con. Res. 14,” Pub. L. No. 117-169, §§ 23001-23003, 136 Stat 1818, 2023-2026 (2022) (commonly known as the Inflation Reduction Act).
[75]National Defense Authorization Act for Fiscal Year 2024, Pub. L. No. 118-31, § 2857, 137 Stat. 136, 767 (2023).
[76]Office of Management and Budget, OMB Circular A-136 Revised, Financial Reporting Requirements (Washington, D.C.: May 30, 2024).
[77]89 Fed. Reg. 25,378 (Apr. 10, 2024).
[78]See 89 Fed. Reg. at 25,427–29. As of November 2024, a court order temporarily enjoined enforcement of the rule against several states pending litigation, N. Dakota v. Interior, No. 1:24-cv-00066, 2024 U.S. Dist. LEXIS 164665 (D.N.D. Sept. 12, 2024). Interior has appealed that order. N. Dakota v. Interior, No. 24-3299 (8th Cir.).
[79]89 Fed. Reg. 30916, 30975 (Apr. 23, 2024); “An Act To provide for reconciliation pursuant to Title II of S. Con. Res. 14,” Pub. L. No. 117-169, § 50262(a), 136 Stat. 1818, 2056 (2022) (commonly known as the Inflation Reduction Act).
[80]Implantable medical devices replace, support, or substitute for deformed or weakened anatomical body parts. Some implantable devices are “biological,” that is, made from skin, bone, or other body tissues. Other implantable medical devices are non-biological—made from metal, plastic, ceramic, or other materials—such as pacemakers and hip replacements.
[81]88 Fed. Reg. 6,643 (Feb. 1, 2023).
[82]88 Fed. Reg. 77,676 (Nov. 13, 2023).
[83]Bipartisan Budget Act of 2015, Pub. L. No. 114-74, § 603, 129 Stat. 584, 597.
[84]See 42 U.S.C. § 1395yy(h).
[85]84 Fed. Reg. 61,142 (Nov. 12, 2019).
[86]89 Fed. Reg. 40,876 (May 10, 2024).
[87]Pub. L. No. 111-203, 124 Stat. 1376 (2010).
[88]The rulemaking is required under section 166 of the Dodd-Frank Act. 12 U.S.C. § 5366. The Federal Reserve proposed a rule in 2012 to implement this requirement for large bank holding companies. Enhanced Prudential Standards and Early Remediation Requirements for Covered Companies, 77 Fed. Reg. 594 (Jan. 5, 2012).
[89]The 2025 high-risk area rating is based on analysis of agency actions taken up through and including the 118th Congress, before the start of the 119th Congress and the new administration. Therefore, agency plans and policies referenced in this update may have subsequently changed. We will continue to monitor federal government actions, and our future high-risk updates will reflect these and other policy and legal developments.
[90]5 C.F.R. § 250.205(c).
[91]Families First Coronavirus Response Act, Pub. L. No. 116-127, § 6008, 134 Stat. 178, 208 (2020) (codified, as amended at 42 U.S.C. § 1396d note).
[92]89 Fed. Reg. 41,002 (May 10, 2024).
[93]See 42 C.F.R. § 438.6(c)(4) (2024).
[94]89 Fed. Reg. 40,542 (May 10, 2024); 89 Fed. Reg. 41,002 (May 10, 2024).
[95]Pub. L. No. 116-3, § 4, 138 Stat. 6, 7–8.
[96]The 2025 high-risk rating is based on our analysis of federal government actions taken through and including in the 118th Congress, before the start of the new administration. It references federal policy documents that may be rescinded, replaced, or amended. We will continue to monitor federal government actions, and our future high-risk updates will reflect policy and legal developments.
[97]According to EPA, final actual amounts include obligations made in a specific fiscal year as well as funds carried over from the previous fiscal year and obligated in the specific fiscal year. The final actual amount for fiscal year 2024 was not included in EPA’s fiscal year 2025 budget justification.
[98]15 U.S.C. § 2625(n).